Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Your Source of Truth for All Things AutoRABIT
The Knowledge Base is your centralized, always-evolving source for technical documentation, product guidance, release notes, FAQs, and operational support across the AutoRABIT ecosystem. Whether you’re leading enterprise-scale transformation or optimizing daily flows, this is where insight meets action.
AutoRABIT is not just a toolset—it’s a system. Our enterprise-grade DevSecOps platform is purpose-built for Salesforce, enabling controlled speed, secure scalability, and intelligent automation across development, compliance, and data management workflows.
Our ecosystem includes:
— Structured CI/CD pipelines for Salesforce. Aligns governance with acceleration.
— Industry leading static analysis to enforce quality and secure code before it ships.
— Resilient, compliant backup and recovery tailored for complex Salesforce data models.
— Real-time permission intelligence and compliance automation. Prevents access risk before it becomes exposure.
Together, these products form the industry’s most complete DevSecOps solution for Salesforce, trusted by the most security-conscious and performance-driven teams in the world.
Precision answers, fast. Use our embedded AI assistant to extract exact steps, explanations, and insights from our full documentation library.
Stay informed. Track feature updates, patch releases, and roadmap-aligned improvements—built for enterprise-readiness.
From initial configuration to advanced workflows—our user guides provide structured clarity for every role and function.
Self-serve solutions to unblock your team and reduce downtime.
(Recommended)
Have a clarification, correction, or improvement in mind? Every page in this Knowledge Base includes an “Edit on GitHub” button in the right-hand sidebar. This opens a GitHub Pull Request pre-linked to the exact page, so you can propose updates directly—whether it’s adding missing context, flagging outdated content, or refining explanations.
Your suggestions help us evolve the documentation in real time—driven by the people who use it most.
If there’s a concept, use case, or integration we haven’t covered yet, let us know. Our documentation team partners closely with product and support to continuously expand coverage based on real-world needs.
How-To Tutorials Get practical. Resolve common challenges, optimize configurations, and apply best practices confidently.
Stay informed — this page is your go-to destination for all organization-wide announcements.
Welcome to the AutoRABIT Release Notes page! This is your go-to resource for the latest updates and changes to all of our key products, including ARM, CodeScan, Vault, and nCino Integration.
Here, you'll find detailed release notes that provide insights into new features, enhancements, and bug fixes for each product update. Our goal is to keep you informed and equipped with the knowledge to make the most of our products.
By staying tuned to this page, you'll gain a deeper understanding of how our products are evolving to meet your needs and the changing landscape of software development. From small adjustments to major overhauls, every update is documented here to ensure you have all the information you need at your fingertips.
Whether you're a new user learning the ropes or an experienced customer seeking to optimize your use of our products, our Release Notes page is an invaluable tool for staying up-to-date with AutoRABIT's dynamic suite of solutions.
19 July 2024
Rule enhancement for Misuse of Assert Class Included the ability to configure parameters for the "Misuse of Assert Class" rule, specifically for the Assert methods Assert.isFalse, Assert.isNotNull, hard-coded values, and Assert.areEqual, so that user can customize the rule to better fit the coding standards and practices of their project.
Rule Enhancement for “Avoid Using Test.isRunningTest()” {APEX Rule}: Previously, this rule was flagging violations when finding methods written as Test.isRunningTest(). This rule has been enhanced to also flag violations when finding methods written as System.Test.isRunningTest().
Decrease False Positives reported for Rule “sf:FixDuplicateMethods” Summary: CodeScan recognizes that methods should not share the same implementations. As such, the scope of the rule will be limited to methods with actual implementations, rather than including interface method declarations. This means the rule will now focus solely on detecting and addressing duplicate implementations within concrete classes, ensuring that only methods containing executable code are evaluated. Violations reported by this rule will now include details of all duplicate methods affected. This means each violation will list every instance of a method that shares the same implementation, making it easier to identify and resolve duplicated code. These updates will make the rule more precise, and its violation reports more comprehensive, enhancing its effectiveness.
Enhancement to Rule "Field-Level Security" (FLS): CodeScan’s FLS rule did not detect DML methods called when syntax is insert (record), update (record), etc. Instead, FLS was only detecting when “insert record;” syntax was used. We made a parser update within CodeScan and an enhancement to the rule was applied, which corrected the syntax detection.
Enhancement to Rule "Cyclomatic Complexity" Summary: Several enhancements were applied to the rule cyclomatic complexity, including adding the decision points '?', '&&', '||', and 'catch'.
New Rules: CodeScan Polyfill Protection We are excited to announce that CodeScan has been updated with crucial enhancements to address recent security concerns related to polyfills. Recent advisories have highlighted significant threats stemming from polyfills, particularly those distributed via the CDN polyfill.io, which are linked to malware. This update introduces advanced protection mechanisms to ensure your Salesforce environment remains secure.
Here’s how CodeScan is advancing your security:
Configuration Scanning: Our enhanced system now scans the configuration settings of Salesforce components, including Salesforce Sites, Salesforce CORS (Cross-Origin Resource Sharing), and Salesforce CSP (Content Security Policy), to detect any unauthorized calls to polyfill.io domains.
Component Scanning: We are scanning the core Salesforce components that enable developers to build sophisticated, custom user interfaces including Visualforce, Aura, Lightning, and other web components
Package Scanning: Our updated scanning mechanism checks downloaded packages from Salesforce AppExchange to ensure they do not contain insecure calls to polyfill.io domains
Activate the Polyfill rules, Avoid Script References to Polyfill.io, and Avoid Configuration References to to your custom quality profile to begin using them.
The 'Hard-Coded Credentials' rule name has been changed to 'Use Named Credentials' for clarity.
'Use Named Credentials' and 'Field-Level Security' rules have updated descriptions highlighting Salesforce best practices and better paths to resolution.
Fixed a false positive in the rule 'Avoid using methods getDescribe and getMap inside Loops' when using custom methods with similar names.
CodeScan Release 23.1
23 April 2023 Release Date
(CodeScan v 23.1.0)
The complete CodeScan rules list can be accessed .
New interactive and appearance have been introduced to the CodeScan Welcome screen. Two new options, Application Security Testing and Policy Management are offered when you first log in to CodeScan. If you select Application Security Testing, you will be directed to the Projects page, which is now your default homepage. As a result, when you log in to CodeScan the next time, you will be immediately redirected to the Projects page. Similarly, if you choose Policy Management, you will be navigated to the Policy Results screen, now set as your default homepage.
This release includes minor stability fixes and improvements for the CodeScan platform.
(CodeScan v.23.1.6)
This update included minor improvements.
(CodeScan v.23.1.5)
The following was updated:
(CodeScan v23.1.4)
The following rules were updated for release 23.1:
(CodeScan v23.1.3)
What's New:
CodeScan Self-Hosted version 23.1.3 (now compatible with SonarQube™ version 10).
(CodeScan v23.1.2)
This is a maintenance release. The following items were fixed and/or added:
Starting from version 23.1.2, CodeScan supports integration to GIT with SSH Keys and supports ssh:// protocol. Connecting to GIT repository using the Secure Shell Protocol (SSH) provides a secure channel over an unsecured network. )
Salesforce Spring '23 (API version 57.0) Support: To keep our product up to current with the most recent Salesforce upgrades, CodeScan supports the most recent API 57.0 version in this release.
This release also includes insecure dependent libraries upgrade and other significant security improvements.
(CodeScan v23.1.1)
CodeScan self-hosted has been upgraded from 22.8 to 23.1.1 version.
This release includes Apex-pmd dependency upgrade and significant security improvements. Updating is strongly recommended.
PermissionSet - Flows Policy
PermissionSet - Flows Policy gives visibility on access permissions related to Run Flows, Flows Policy, Manage Flow. This violation means that this Permission Set conflicts with your policy for these settings.
5
Profile - API Admin Policy
Profile - API Admin Policy gives visibility on API Admin permissions.
6
Profile - Security Settings Policy
Profile - Security Settings Policy gives visibility on access permissions related to IP Restrict Requests,Manage Certificates,Manage IP Addresses,Manage Encryption Keys,View Threat Detection Events,Profile allows Manage Security Center.
7
PermissionSet - Packages Admin Policy
PermissionSet - Packages Admin Policy gives visibility on access permissions related to Create and Update Second-Generation Packages, Delete Second-Generation Packages, Manage Package Licenses, Download AppExchange Packages, Create AppExchange Packages, Upload AppExchange Packages.
8
PermissionSet - Platform Admin Policy
PermissionSet - Platform Admin Policy gives visibility on Platform Admin permissions.
9
PermissionSet - User Management Policy
PermissionSet - User Management Policy gives visibility on access permissions related to Manage Users, Manage Roles, Assign Permission Sets, Reset Passwords and Manage Internal Users.
10
Profile - Packages Admin Policy
Profile - Packages Admin Policy gives visibility on access permissions related to Packaging2, Packaging2Delete, ManagePackageLicenses, InstallPackaging, CreatePackaging, PublishPackaging.
11
PermissionSet - Data Admin Policy
PermissionSet - Data Admin Policy gives visibility on access permissions related to Manage Data Categories, View All Data, Manage Data Integrations, ModifyAllData , View Encrypted Data, Weekly Data Export, Edit Read Only Fields.
12
PermissionSet - Developer Policy
PermissionSet - Developer Policy gives visibility on access permissions related to Author APEX, Import Custom Objects.
13
Profile - Data Admin Policy
Profile - Data Admin Policy gives visibility on access permissions related to Manage Data Categories, View All Data, Manage Data Integrations, ModifyAllData , View Encrypted Data, Weekly Data Export, Edit Read Only Fields.
14
PermissionSet - Files and Content Policy
PermissionSet - Files and Content Policy gives visibility on access permissions related to Files Connect Cloud.
15
Profile - Platform Admin Policy
Profile - Platform Admin Policy gives visibility on Platform Admin permissions.
16
Profile - Reports and Dashboards Admin Policy
Profile - Reports and Dashboards Admin Policy gives visibility on access permissions related to Create Report Folders, Manage All Private Reports and Dashboards, Create and Customize Reports, Manage Reports in Public Folders, Manage Dashboards in Public Folders, Manage Custom Report Types, Report Builder, Report Builder (Lightning Experience), Run Reports, Create and Customize Dashboards, Manage Dynamic Dashboards, Export Reports.
17
PermissionSet - Permissions Admin Policy
PermissionSet - Permissions Admin Policy gives visibility on access permissions related to Manage Profiles and Permission Sets, Manage Sharing, Multi-Factor Authentication for User Interface Logins, Manage Auth. Providers, Manage Custom Permissions, Manage Login Access Policies, Manage Password Policies, Allow Password Never Expires, Manage Session Permission Set Activations, Exempt from Transaction Security, Waive Multi-Factor Authentication for Exempt Users.
18
PermissionSet - Reports And Dashboards Admin Policy
PermissionSet - Reports And Dashboards Admin Policy gives visibility on access permissions related to Manage All Private Reports and Dashboards, Create and Customize Reports, Manage Reports in Public Folders, Manage Dashboards in Public Folders, Manage Custom Report Types, Report Builder, Report Builder (Lightning Experience), Run Reports, Create and Customize Dashboards, Manage Dynamic Dashboards, Export Reports.
19
Organization - Session Policy
Organization - Session Policy gives visibility on access permissions related to Session Timeout, Enforce login IP ranges on every request.
20
Profile - Flows Policy
Profile - Flows Policy gives visibility on access permissions related to Run Flows, Flows Policy, Manage Flow.
21
Organization - Password Policy
Organization - Password Policy gives visibility on access permissions related to Passwords Expiry, Enforce password History, Minimum Password Length, Password Complexity Requirement, Password Question Requirement, Maximum Invalid Login Attempts, Lockout Effective period, Obscure answer for password resets, Require minimum One Day password lifetime.
22
Profile - Session Policy
Profile - Session Policy gives visibility on access permissions related to Required Session Level and Session Timeout Limit.
23
Profile - Files and Content Policy
Profile - Files and Content Policy gives visibility on access permissions related to Query All Files, Files Connect Cloud, Manage Salesforce CRM Content, Manage Content Permissions, Manage Content Properties.
24
Profile - Permissions Admin Policy
Profile - Permissions Admin Policy gives visibility on access permissions related to Manage Profiles and Permission Sets, Manage Sharing, Multi-Factor Authentication for User Interface Logins, Manage Auth. Providers, Manage Custom Permissions, Manage Login Access Policies, Manage Password Policies, Allow Password Never Expires, Manage Session Permission Set Activations, Exempt from Transaction Security, Waive Multi-Factor Authentication for Exempt Users.
25
PermissionSet - API Admin Policy
PermissionSet - API Admin Policy gives visibility on access permissions related to Modify Metadata Through Metadata API Functions, Bulk API Hard Delete, API Enabled, Multi-Factor Authentication for API Logins, Manage Multifactor Auth - API, Apex REST Services, Access Customer Asset Lifecycle Management APIs, Update Consent Preferences Using REST API.
26
Profile - User Management Policy
Profile - User Management Policy gives visibility on access permissions related to Manage Users, Manage Roles, Assign Permission Sets, Reset Passwords and Manage Internal Users.
1
Profile - Developer Policy
Profile - Developer Policy gives visibility on access permissions related to Author APEX, Import Custom Objects. This violation means that this Profile conflicts with your policy for these settings.
2
Profile - Password Policy
Profile - Password Policy gives visibility on access permissions related to Passwords Expiry, Enforce password History, Minimum Password Length, Password Complexity Requirement, Password Question Requirement, Maximum Invalid Login Attempts, Lockout Effective period, Obscure answer for password resets, Require minimum One Day password lifetime, Don't Immediately expire links in forgot password emails.
3
PermissionSet - Security Settings Policy
PermissionSet - Security Settings Policy gives visibility on access permissions related to Manage Certificates,Manage IP Addresses,Manage Encryption Keys,View Threat Detection Events,Profile allows Manage Security Center.
sf:AvoidPublicFields
Class Variable Fields should not have Public Accessibility
sf:AvoidUsingHardCodedId
Avoid Using Hard Coded Salesforce Id
sf:InsecureEndpoint
Avoid Cleartext Transmission of Sensitive Information
sf:SOQLInjection
Avoid Untrusted/Unescaped Variables in DML Query
4

Release Date: 3 December 2025
A new in-product chatbot that provides real-time guidance on product features, navigation, troubleshooting, and best practices.
Includes:
Floating in-app widget
Natural language Q&A
Documentation-backed responses
Smart fallback and escalation to Support
Permission History
A new Permission History feature allows users to select one or multiple permissions and view history of all modification events across profiles, permission sets, and permission set groups. Results are auto sorted by permission name for streamlined review.
Alternative View by Profile/Permission Set
A new view selector supports switching between:
Matching Users (default)
Matching Profiles
Matching Permission Sets
Matching Permission Set Groups
Available in both Permissions Explorer and Explore Object Access.
Selecting a Salesforce org in any feature now auto-selects it across all features for the duration of the session. Logging out clears the selection.
Salesforce orgs are now directly accessible from the main navigation menu, improving discoverability and reducing navigation steps.
Users can now see their tenant's name next to the Release version in the bottom-left corner of the interface, providing better environment awareness.
The platform has been upgraded to Spring Boot 4.0 for enhanced performance, security, and framework stability.
User Activity Monitoring now works even in orgs missing the User.LastPasswordChangeDate field, preventing GQL errors.
Multiple issues have been fixed, including:
Incomplete Risk Assessment results
Failure to refresh after Permission Explorer errors
Errors parsing Salesforce API usage statistics
Release Date: 26 November 2025
Added Change Monitoring and Data Classification widgets to the Salesforce Org Dashboard.
Widgets link directly to their respective feature pages.
Updated the Executive Report to include Change Monitoring and Data Classification insights.
Added clear password requirement hints to the New Password screen.
Helps users understand the strict password criteria and successfully set up their account.
Fixed the formatting of certificate details.
Shows “No certificate created” when no certificates are available.
Fixed an issue with the Sync to Salesforce button appearing multiple times in Data Classification.
Improved placeholder text shown in the Permission Explorer.
The placeholder now displays the intended guidance.
Release Date: 29 October 2025
Gain deeper insight into your connected apps and organizational exposure with the enhanced API Security Dashboard.
View key risk metrics, filter results by org, explore detailed app information, and export data for further analysis — all from a responsive, easy-to-use interface.
The Permissions Explorer now automatically supports all available Salesforce permissions, giving you a complete view of your org’s access setup.
A new “Other” category dynamically lists uncategorized permissions, ensuring nothing is missed and reducing manual effort.
You can now save custom Object Permission queries with names and descriptions, making it easy to revisit important configurations without rebuilding them each time.
Access to support resources is now simpler. The Help menu has been redesigned to include quick links to the Support Portal, Guard Product Guide, and Support Login Access.
The Guard home page now features interactive cards that highlight recently added features. Each card links directly to its feature page for quick navigation, and the updated Change Monitoring card reflects the latest functionality for easier discovery.
Fixed an issue where the “Approve Uninstalled Connected Apps” permission caused an error indicating that the field PermissionsCanApproveUninstalledApps did not exist in the PermissionSet entity.
Resolved an issue where some permissions were not displaying correctly in the Custom Explorer view for some environments. Permissions now load correctly under their respective categories.
Release Date: 15 October 2025
We’re thrilled to announce that users can now sync Data Classification results directly back to their Salesforce org. This closes the loop between AutoRABIT Guard and Salesforce, keeping compliance data consistent and up to date.
Highlights:
Push Data Classification results (compliance categorizations and relevant regulations) back to Salesforce.
New table view with field selectors, compliance and regulation columns, and sync status.
“Sync to Salesforce” button for bulk or individual field syncs.
Field detail view enhanced with Compliance and Sync options.
Impact: Automates alignment between Guard and Salesforce for compliance data — reducing manual effort, errors, and audit risk.
A brand-new Org Summary Dashboard provides a unified overview of an org’s health, compliance, and risk posture.
Highlights:
Aggregates data from multiple modules:
Risk Assessment
API Security
Permissions Explorer
Impact: Gives customers an executive-level view of org performance and compliance in one place.
We’re introducing Support Login Access—a secure, auditable way for AutoRABIT Support Engineers to access Guard instances with customer approval and full transparency.
Highlights:
Dedicated “Grant temporary Support access” screen.
Customers approve access by providing case details, support representative email, and preferred access duration (7, 15, or 30 days).
Support users are created as read-only accounts; activity is fully logged and auditable.
Customers can revoke access at any time.
Impact: Faster issue resolution with complete transparency, security, and customer control.
We’ve added a “Reauthenticate” button to simplify reconnecting Salesforce orgs without deleting them.
Impact: No more data loss when tokens expire—orgs, access controls, and rules stay intact.
Module: Change Monitoring Risk levels (Low, Medium, High) are now visually displayed for each change.
Impact: Greater visibility into risky activities and faster prioritization of security review.
Change Monitoring now records granular details when user permissions change on Profiles, aligning with existing tracking for Permission Sets.
Impact: Improved traceability and audit accuracy, enabling downstream features.
Introduced an alternative table view for displaying risks, complete with sorting and filtering by name or properties.
Impact: Simplifies navigation and analysis, especially for large number of orgs.
The previous single “Status” field was split into two:
Status: Unresolved, Resolved
Severity: Warning, Critical
Impact: Improves clarity, ensuring severity and progress are tracked distinctly.
Added the ability to change the org directly from the main detail page, streamlining workflows.
Impact: Saves time for admins managing multiple orgs.
Added a new “Show Frozen Users” checkbox in Custom Explorer.
Unchecked (default): frozen users excluded.
Checked: frozen users included.
Impact: Provides clarity and control in results interpretation.
Fixed an issue where the Delete Org confirmation modal displayed unrelated notification rules.
Impact: Now shows only items tied to the org being deleted, eliminating confusion.
Release Date: 24 September 2025
A new User Activity Monitoring section is now available under Compliance, giving admins real-time visibility into Salesforce users' activity.
Highlights
Real-time monitoring
Accessible via the standard org switcher
Data sourced from Salesforce
Why it matters: Strengthens compliance visibility and enables proactive security monitoring of user behavior.
We’ve introduced a dedicated Real-time Change Notifications section with pre-built notification templates, making it easier to detect and respond to critical security-related changes.
Highlights
Pre-built templates for key events, including:
Profile created
Password policy modified
User assigned to new profile
Why it matters: Helps enforce Compliance requirements and ensures visibility into high-impact configuration changes.
Tenant data now has a mandatory expiration time to enforce lifecycle management.
Highlights
Mandatory expiration is set at tenant creation.
Automated tenant deletion is triggered on the expiration date.
Advance notice: Tenant managers receive an email 5 days before deletion.
Why it matters: Ensures consistent data lifecycle management and enforces retention limits.
The platform now provides comprehensive event logging to strengthen accountability and monitoring.
Highlights
Audit records for key events.
Logs safeguarded against unauthorized modification or deletion.
Supports audit reduction, correlation, and reporting for easier compliance review.
Why it matters: Provides robust traceability and supports effective security investigations.
Salesforce Org Registration OAuth Error: Fixed an issue preventing new Salesforce Orgs from being registered due to OAuth flow failures.
Password Reset Flow: Password policy error messages now clearly display complete requirements
Permission Explorer – User Metadata: “User Created By” displays details properly
Permission Explorer – Custom Objects: Object access results are displayed correctly for custom objects.
Release Date: 15 September 2025
Change Monitoring Export
Users can now export the Change Monitoring Changes table into CSV file.
Export includes all columns available in the UI, as well as detail and modifiedProperty fields for improved auditing and analysis.
Copy as JSON
A new “Copy as JSON” button has been added to the Permissions Explorer.
This feature allows users to copy the entire JSON response, which simplifies troubleshooting, data sharing, and downstream analysis.
Implemented additional APIs and added extended logs for deeper insights during troubleshooting, improving visibility into system operations.
Release Date: 10 September 2025
We’re launching API Security in Guard to help customers identify and mitigate risks from third-party apps connected to Salesforce. As attacks on Salesforce orgs increase, including from unverified or over-permissive apps, this feature gives teams visibility into which apps are connected, how they’re being used, and whether they pose a risk.
AutoRABIT Guard introduces a new API Security tab under the Risk section. From here, users can inspect API activity for a specific Salesforce org in real time.
Value to Users:
Increased security visibility: Spot risky or shadow apps that might otherwise go unnoticed.
Proactive defense: Prevent over-permissive apps from giving unauthorized users access to critical data.
Multi-org management: Quickly assess and compare API risks across all Salesforce orgs.
User Details at a Glance Admins can now view detailed user information directly within Permissions Explorer, including:
Full name, active/inactive status, and last login.
Creator details and their current status.
This makes it faster to investigate suspicious permissions and strengthens overall security posture.
Object-Level Access Insights A New Object Access Mode makes it easy to see who can perform actions (Read, Create, Edit, Delete) on both standard and custom Salesforce objects. With filtering by Profile, Role, or Email, compliance audits and security reviews are now faster and more accurate.
New Filters in Permissions Explorer Permissions Explorer now offers additional Super Admin permission filters, including:
Setup & Configuration access.
AppExchange package downloads.
Approval of uninstalled connected apps.
These updates give admins greater visibility into high-risk privileges.
Business-Oriented Risk Labels: Risks are now described in simple, more understandable terms. Once resolved, risks display positive compliance outcomes to reinforce progress.
Navigation Enhancements: Users can browse between risks with new “Previous” and “Next” buttons, cycling through seamlessly.
Dedicated Risk Detail Page: Clicking on a specific risk now opens a full detail page, providing richer context and better usability.
Certificate Settings Clarity: Updated UI labels make certificate key sizes and expiration values easier to understand and configure correctly.
These changes make Risk Assessment more accessible for both technical and non-technical stakeholders, while streamlining the review process.
Information Hierarchy: Organizations are now grouped into clear priority categories (Critical, Quick Wins, Compliant), making it easier to focus remediation efforts.
Improved Icon Visibility: Table header icons are now larger and easier to read, improving accessibility and UI consistency.
Data Classification Transparency: A new “Non-Started” state prevents confusion and allows users to trigger analysis manually when needed.
Data Classification Export: Email notifications correctly include attached exports.
Permissions Explorer: Accurate Access visibility ensured.
User Management: Enforced validation for mandatory fields and added clear toast messages for success/error feedback.
Database Cleanup: Removed legacy tables for improved performance and maintainability.
Tenant Deletion API: A new API introduced to enable safe and auditable tenant removal.
Release Date: 20 August 2025
Creating new users is now faster and more flexible. Admins can set up accounts with just an email address and role. Other details (username, first name, and last name) are optional and hidden by default but can be filled out as needed.
The system now automatically handles username conflicts by suggesting available alternatives.
The user list view and user icons have been updated to reflect these enhancements.
To enhance security and prevent accidental or malicious account removals:
Admins can no longer delete or deactivate their own accounts but still can manage Standard User accounts.
Standard Users cannot delete or deactivate their own or any other accounts.
This change helps maintain system stability and protects privileged accounts.
We’ve introduced new safeguards to reduce the risk of privilege loss or escalation:
Admins can no longer downgrade themselves to Standard User.
Admins can still promote Standard Users to Admin.
Standard Users cannot change anyone’s role.
All role changes are now logged for better auditing and compliance.
Guard now supports Single Sign-On (SSO) using encrypted SAML assertions. This ensures:
Sensitive authentication data is securely transmitted.
Reduced risk of data interception or tampering.
Compliance with federal security standards.
User Unlocking: Resolved an issue with locked accounts that couldn’t be unlocked from the Settings page. Admins can now restore users' access without any errors.
Security & Compliance: We have strengthened our platform’s security by implementing targeted improvements that meet stringent federal standards. These updates reduce potential attack surfaces and further enhance data protection.
Implemented a few back-end optimizations to enhance system stability and ensure long-term maintainability, supporting a smoother and more reliable user experience.
Release Date: 23 July 2025
Risk Assessment is goal-oriented now!
We have grouped risks under four key Security Goals:
Goal 1: Establish Secure Access & Identity
Ensuring only authorized users access Salesforce, their identities are verified, and highly privileged access is governed.
Goal 2: Harden Application & Session Security
Protecting the Salesforce application from common web vulnerabilities, ensuring secure communication, and maintaining user session integrity.
Goal 3: Safeguard Data & Control Exposure
Protecting data confidentiality and integrity by managing sharing settings, controlling access to sensitive information, and limiting guest user access.
Goal 4: Ensure Foundational Platform Integrity
Maintaining the core security of the Salesforce platform via valid configurations for certificates, encryption, and secure external connections.
Users can see their progress towards achieving each Goal and remediate the associated risks accordingly.
Custom Permission Explorer queries can be saved
Just give your query a name and definitive description, and it will be saved for your future revisits:
New home page
To help navigate and get instant value, we are happy to introduce a brand-new home page:
Instance version details are available now in the bottom left corner of the expanded page:
New menu
To improve application navigation, in this release we have added a new menu:
While we enhance its performance and functionality, we have temporarily removed the Field usage (data) tab from Data Classification UI:
1. Zoho desk link now works as expected.
2. User menu is no longer cut off by browser window.
“Export Executive Report” is available for easy reporting
Onboarding flow updated to include a dashboard overview.
Sharing rules updated
Login IP ranges created/modified, or deleted
External credentials modified
Remote site settings updated
Multi-org support for applying templates across environments
Enhanced detail pages
Access Controls – User Dropdown Limit: Fixed limitation where only 2,000 users were displayed in the “Define Allowed Users” dropdown; now supports all users in large Salesforce Orgs.
The Data Classification Export now includes a new rationale column for each field in the CSV output.
Provides better context and justification for field classifications, improving clarity and audit readiness.
Risk Assessment Export
A new “Export Assessment” button is now available in Risk Assessment.
Users can export the entire assessment as a CSV file.
API Security Export
Customers can now export all data from the API Security page into a CSV file.
This export provides a complete view of connected applications and their security posture.









Frequently Asked Questions (FAQs) have been integrated within the product documentation for easier reference. Please refer to the information for FAQs on AutoRABIT ARM.
Custom rules using XPath: With this added capability, CodeScan Cloud users can now be able to define their own XPath based rules aligning with their organizational standards.
Fast Scan Mode: CodeScan’s pull-request analysis is now going to be more efficient with the added capability of CodeScan to scan only the changed files in the pull request instead of scanning through the entire branch.
New Compliance rules for Salesforce Metadata: We made our Salesforce Metadata Ruleset be more powerful with the addition of two new rules that helps minimize and prevent the Salesforce users from being provided with unnecessary privileges.
Limit number of System Administrators: In Salesforce Metadata ruleset, we added a new rule "Limit number of System Administrators" which helps to limit the number of users with System administrator profiles to a defined minimum.
Limit number of Custom Profiles with Modify All Data Permission: In the Salesforce Metadata ruleset, we added a new rule "Limit number of Custom Profiles with Modify All Data Permission" which helps to limit the number of users with 'Modify all Data' permission to a defined minimum.
Release Date: 16 June 2024
nCino 24.1 is a major release that encompasses the following release items:
nCino Compare Functionality
Enhanced Data Loader Pro Job Configuration
Exclude the OwnerID from Automapping in nCino CI jobs
Data Loader Pro Job Run Options in Configuration
nCino Compare Functionality
Overview: This provides users with enhanced control and insight into the deployment of nCino Record-Based Configurations (RBC). Application: The nCino RBC Comparison Tool allows users to effortlessly compare RBC configurations between those ready for deployment and those already existing in the target environment. This comparison ensures that users can identify discrepancies, confirm consistency, and make informed decisions before finalizing deployments. Benefit: This tool addresses the need for a reliable method to ensure consistency and accuracy in RBC deployments, reducing the risk of configuration errors and streamlining the configuration management process. Further documentation: For more detailed information, please refer to our
Enhanced Data Loader Pro Job Configuration Overview: To provide users with greater flexibility and control over the data loading process by allowing the users to enable and disable the validation rules, workflow rules, and triggers.
Exclude the OwnerID from Automapping in nCino CI jobs
Overview: Users can now disable the auto-mapping of ownerIDs between environments within the application.
Application: This new option allows users to prevent the automatic mapping of ownerIDs during record-based configuration migration. This is particularly useful in scenarios where developers in lower environments, such as a development sandbox, have the necessary privileges to own configuration records but lack similar access in higher environments like QA or production. By disabling auto-mapping, users can manually set appropriate ownerIDs, ensuring a smoother and more controlled migration process.
Benefit: Helps avoid issues encountered during record-based configuration migration due to limited access to record owners in higher environments. This enhancement ensures that migrations do not fail or cause access-related issues, improving the reliability and consistency of deployments across different environments.
Further documentation: For more detailed information, please refer to our .
Triggering nCino CI Jobs Using REST API
Select external unique identifier During nCino Feature Deployment
Benefit: Enhances flexibility and control over the data loading process, enabling users to customize job configurations to meet their unique needs and reducing the risk of unintended rule or trigger executions.
Further documentation: For more detailed information, please refer to our Knowledge Base.
Triggering nCino CI Jobs Using REST API Overview: Customers can now trigger nCino CI (Continuous Integration) jobs using the provided API endpoints.
Application: This enhancement simplifies and automates the Continuous Integration (CI) process for nCino users by allowing them to trigger CI jobs through REST API calls. With this capability, users can integrate CI job execution seamlessly into their existing automation workflows or CI/CD pipelines. By leveraging API endpoints, users gain greater flexibility and control over the CI process, enabling efficient and consistent integration testing and deployment.
Benefit: Addresses the need for streamlined and automated CI processes by providing customers with the ability to trigger nCino CI jobs via API endpoints. This enhancement improves efficiency, reduces manual intervention, and enhances the overall CI experience for users.
Further documentation: For more detailed information, please refer to our Knowledge Base.
Data Loader Pro Job Run Options in Configuration
Overview: All job run options can now be configured when creating a job in Data Loader Pro.
Application: This enhancement allows users to set all desired job run options at the time of job creation, providing greater customization and control over Data Loader Pro job executions. These configurations are preserved for the scheduled execution of the jobs, ensuring that each job runs with the specified settings without the need for manual adjustments before each execution.
Benefit: Enhances customization and control over Data Loader Pro job executions and ensures that job settings are consistently applied during scheduled runs, reducing the risk of errors and improving efficiency.
Further documentation: For more detailed information, please refer to our Knowledge Base.
Select External Unique Identifier During nCino Feature Deployment
Overview: Users now have the option to select the external unique identifier instead of AutoRABIT external ID for deployments.
Application: This enhancement provides users with the flexibility to choose an external unique identifier for deployments, rather than relying solely on AutoRABIT's external ID. This feature ensures accurate data transfer and eliminates the risk of record duplication by allowing users to select an identifier specific to their environment or requirements, such as an external system ID or a custom unique identifier. Users can now confidently deploy data outside of AutoRABIT or in refreshed sandboxes without encountering issues related to record duplication.
Benefit: Addresses the potential for record duplication when transferring data outside of AutoRABIT or deploying default data in refreshed sandboxes. By enabling users to select an external unique identifier, this enhancement mitigates the risk of duplication and ensures data integrity during deployments.
Further documentation: For more detailed information, please refer to our Knowledge Base.
Frequently Asked Questions (FAQs) have been integrated within the product documentation for easier reference. Please refer to the information here for FAQs on Vault.
We are thrilled to announce that you can easily change your Super Admin with our new 23.1 release.
With the new 23.1 release, we’ve consolidated the roles of Super Admin and Registered Admin into a single empowered Admin role. But also with the new 23.1 release, we have added a new feature so you can assign the ex-Super Admin from your login.
Please follow the simple steps below, making sure you are on the latest 23.1 build.
Log in with your Admin credentials. Go to the Users section in the Admin panel.
From the User tab, you will see the * symbol next to the current Super Admin name. Click on the Edit icon.
Edit the previous Super Admin user, remove the Admin access by pressing the 'Deactivate' button on the right.
Once the deactivation is completed, you will see the other Admin being promoted to Super Admin.
Once you're finished, save the changes. You will get a confirmation pop-up window about the new Super Admin on the next page. Log out and log in again.
New Apex Security Hotspots
Deserializing JSON Is Security-Sensitive: Deserializing an object from an untrusted source is security-sensitive. An attacker could modify the content of the data.
Encrypting Data Is Security-Sensitive: Encrypting data is security-sensitive. Although most encryption problems are solved or managed by Salesforce, care must be taken when relying on encryption.
Type Reflection Is Security Sensitive: Dynamically executing code is security-sensitive. If the code comes from an untrusted source, the untrusted source may be able to choose which code to run.
Using Cookies Is Security-Sensitive: Attackers can use widely available tools to view the cookie and read the sensitive information. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.
Using UserInfo.GetSessionId() Is Security-Sensitive: The use of UserInfo.GetSessionId() is security-sensitive. Ensure that you need to do this.
New Visualforce Security Hotspots
Using GETSESSIONID() and $API.Session_Id is security-sensitive: The use of GETSESSIONID() and $API.Session_Id is security-sensitive. Ensure that you need to do this.
Quality Profiles
Removed Unescaped Source rule from default Apex profile (v4.3.12).
Removed deprecated rule javascript: S2228 from Salesforce Lightning Quality Profile (v4.3.9).
SonarQube™ Ant task has been updated to 2.6.0.1
SOQL Injection Rule updated and improved.(v4.3.11)
Open Redirect Rule updated and improved. (v4.3.11, v4.3.12)
Bug fixed in RightLineBracesPositions rule.
Bug fixed in Field Level Security Vulnerabilities rule. (v4.3.10)
Bug fixed in Preserve Stack Trace Rule (v4.3.12)
Bug fixed in Unescaped Source Rule (
New compliance rules added for Apex Class:
Long Class Names: In the Apex class ruleset, we have added a new rule “Long Class Name” You can now configure an Apex Class with a class name that is longer than 40 characters.
Long Trigger Names: In the Apex class ruleset, we have added a new rule “Long Trigger Name”. You can now configure an apex trigger with a trigger name that contains more characters than the set limit.
Long Method Name: In the Apex class ruleset, we have added a new rule “Long Method Name”. This rule helps to create an apex class rule with a method name that contains more characters than a set limit.
New compliance rules added for Salesforce Metadata:
Avoid Excess Workflow Rules in Org: In the Salesforce metadata ruleset, we have added a new rule “Avoid Excess Workflow Rules in Org”. This rule helps to limit the number of workflow rules in your salesforce org.
Project Analysis Log Report: We've added a new feature that allows users to view their project analysis report by clicking on a link from their VC project. As a result, the user can now view the detailed log report.
Log4j Version: Updated the latest version of log4j to 2.17.1 to address the Apache Log4j security vulnerabilities.
Scheduled project reports: Users with Administrator permission either at the project level or organization level can configure the scheduled project reports. Earlier, this option was available only to the owners of the organization.
Analyze salesforce packages: Users can now analyze the contents of salesforce packages. This will help to keep track of issues in files packages. This feature is especially helpful when the packages are developed and maintained by the user.
There was an issue with project reports not being triggered when they were scheduled; this has now been fixed.





Standard User
A Standard User is an individual authorized by the Customer to log in to and fully utilize AutoRABIT’s subscribed products. Standard Users have access to all product functionalities, including the Web UI, IDE plugins, APIs, and other interfaces.
Platform Owners/Admins are included in the Standard User class, ensuring administrative rights without affecting licensing terms.
Platform Integration User
A Platform Integration User is an individual authorized by the Customer to perform actions that trigger the execution of AutoRABIT products (directly or indirectly).
This includes, but is not limited to:
Analyzing reports or data from AutoRABIT to identify and resolve code quality, security, compliance, or system performance issues.
Agents, bots, or systems executing actions via AutoRABIT to automate testing, deployments, or compliance checks.
Using AutoRABIT IDE plugins
Triggering AutoRABIT APIs
Key Points:
Automation (e.g., bots, agents) utilizing AutoRABIT for testing, deployment, or monitoring must be licensed appropriately.
Any person who commits code to a Source Code Management (SCM) system, where the commit directly or indirectly triggers a job in AutoRABIT, requires a Platform Integration License.
If a service account is used to trigger automation or integrate with AutoRABIT, the person or team responsible for the actual code commit must still hold a Platform Integration License. This ensures that each individual whose actions contribute to triggering AutoRABIT processes is appropriately licensed.
Example: In Git, multiple commits pushed simultaneously are counted individually toward user licensing.
Platform Integration Users are included in licensing with view-only permissions.
Additional Notes:
The number of licensed users represents the total unique users of the products throughout the Subscription Term.
Directly changing Salesforce org configurations
Committing changes to a source code repository
This release incorporates new features, enhancements, and resolved issues from all previous significant releases. If you're upgrading from an earlier version of Vault, check the release notes for any interim versions or details about additional improvements in this release over your current release.
August 2023
What's New?
The archival capabilities of Vault are now enhanced further to create a connection between Salesforce and the storage environment (AWS S3 bucket), leveraging Salesforce Connect with OData 4.0 adapter to display the archived records directly within Salesforce without having to perform complex data loading operations.
Salesforce Connect OData 4.0 adapter license
Reach out to [email protected] to express your interest in participating in the beta program.
Please reach out to your respective Customer Success Manager or Account Executive for more details on the pricing of this capability.
OData protocol is an open and platform-independent protocol that can be integrated with the system of the user’s choice (along with Salesforce) as it exposes REST APIs for consuming and querying data from the underlying archives.
External objects support most of the capabilities that standard and custom objects have in Salesforce.
No need to install any managed packages or write custom scripts in Salesforce.
Files and attachments are not supported for viewing through external objects in Salesforce. This will be supported in the upcoming version of Vault Connect scheduled for the end of Q4 ’23.
Salesforce OData 4.0 adapter has a limitation on the number of callouts per hour. This is going to be addressed with the support for the Salesforce OData 4.01 adapter in the subsequent versions of the capability.
Relationships between external objects and Salesforce objects need to be established manually (like if cases are archived and they are related to accounts that are not archived, the reference to accounts that are in the Salesforce object will be available in the external object but will not be reflected as a lookup relationship). The plan is to support the automated recreation of these references by the end of Q4 2023.
For details on how to configure Vault Connect, please click here to access our .
January 2023
Currently, Vault allows usernames and passwords or SSO-based authentication to grant users access to the Vault application; however, most of our customers requested the implementation of an additional layer of protection to prevent the misuse of their credentials if user credentials were compromised. With MFA now supported, it will allow our users to add Google, Salesforce, or other comparable authenticator apps to provide an authentication code at login.
With this update, we've added the capability to assign a unique identification to each object, preventing the generation of duplicate records. The mapping between source and destination records was not previously available with Vault when records were available in a sandbox, making it impossible to uniquely identify the records in the destination.
Thanks to this capability, every entity in the Salesforce org can now have a unique identifier configured. You can now restore or replicate data without recreating duplicate records.
With the most recent Vault 23.1 release, we improved the schema representation by showing one level of the child/parent objects at a time. The tree can now be expanded based on your selection rather than the entire tree, which speeds up the download of the schema data and improves the UI.
The significant improvements are:
Shows the user one level of the child/parent objects at a time.
Expand the tree based on user selection instead of expanding the entire tree.
The schema is easily searchable, and objects are easily selectable.
We have now made it possible to search backups for records selectively using a term that partially matches them. Users can now search backup records with partially matching values instead of using the whole value as the search keyword.
Users need to understand the details of the config created, and it is helpful for any new member to understand the configs setup and why they were created. As a result, we included the Description box on the Configuration page so that you may describe why you created the backup and archiving configurations. This description field can also be seen on the Config Summary screen.
Improved pagination to reduce page load times across the modules.
Minor performance, bug fixes, and security improvements can also be observed in the Vault portal.
3 Jan 2024
Vault v23.2.14
Backup Delay: The backup is taking longer because FeedItem and EmailMessages are processing for over an hour.
Suggested Workaround: A workaround was suggested to exclude Total Price and Unit Price to resolve the issue.
Policy Level Verification: Verification revealed issues with multiple policies when selecting policy-level changes.
Vault v23.1.11
This is a maintenance release. The following items were fixed and/or added:
An issue was resolved where users were experiencing a problem replicating records from production to a developer sandbox with the backup with hierarchy option. In this issue, when attempting to replicate over 1100 records, no records were being populated in the developer sandbox.
An issue has been resolved that affected manual backups. Users were unable to obtain all the objects in the backup, even when using the correct configuration settings.
An issue has been addressed where users were archiving jobs with a configuration set to limit to 1 million records, but more than 1 million records were being archived. This issue has been fixed.
Vault v23.1.10
This is a maintenance release. The following items were fixed and/or added:
Vault now supports Single Sign-On (SSO) capability through its auto-login function.
Vault v23.1.9
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue for the Restore/Replicate operation where the Person accounts restoration/replication failed when the backup got triggered with Person contacts.
Vault v23.1.8
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the Vault archival failed with "No Records Archived" status in the Vault UI.
Fixed an issue where replicating the Assest records from the source to the destination org ran for a few hours, but no records were picked up.
Fixed an issue where the scheduled backups failed for production orgs.
Vault v23.1.7
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the scheduled Archival jobs ran even after the Config was deleted.
Fixed a bug where users had issues downloading the Label Names report in the Replicate section.
Vault v23.1.6
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue when replicating records from the production to a developer sandbox (1100+ records); no records were populated in the developer sandbox.
Fixed an issue where the archive job kept running after data were processed.
Fixed an issue with the Vault's data storage and management where the archive process failed as it could not write a backup to the Amazon S3 bucket.
Vault v23.1.5
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users could not archive the ContentDocument files ().
Fixed an issue where the users could not edit or delete masking rules in the Replicate module (internal ticket).
Fixed an issue where the Archival jobs did not show all children's details in the Archive config info section (internal ticket).
Vault v23.1.4
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue when the archive jobs got stuck, and the following error was thrown java.util.concurrent.ExecutionException: [UnexpectedErrorFault [ApiFault exceptionCode='TXN_SECURITY_RUNTIME_ERROR'. Additionally, when multiple archive jobs were initiated in the Salesforce environment, the count of the archive records fluctuated. Now that the issue has been rectified, everything works as it should.
Fixed an issue where the Salesforce API limit for the backup triggered using the Bulk API differed from the limit displayed inside the Vault application.
Fixed an issue that stopped the replication jobs from migrating the Case and related objects to the production environment, including the Content Document, ContentVersion, and ContentDocument link
Vault v23.1.3
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where users were trying to map case records which were eventually restored but not properly mapped.
Fixed an issue where the users could not use the SSO feature to log in to their Vault account.
Fixed an issue where users, while changing the password, the users were unable to see the Save button.
Vault v23.1.2
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the restore operation was stuck for hours, and in the end, the status threw as failed.
Fixed an issue where the replicate job failed with no error in the log.
Fixed an issue where the replicate Job is not replicating ContentVersion and ContentDocumentLink objects.
Vault v23.1.1
This is a maintenance release. The following items were fixed and/or added:
Handling Salesforce session timeout in restore/replicate improved and performance improvement in the updateOldIdsWithNewIds method.
All the limitations of Salesforce external objects are applicable as mentioned in this article: Help and Training Community.
The solution supports only the customers configured with AWS S3 as a storage option in Vault.
There is a max limit of 5GB of archived data per customer supported for connecting to Salesforce external data source as part of the beta program. This can be extended to a higher limit by raising a request with [email protected].
An issue has been resolved where users encountered a problem while searching for a specific set of objects using the filter option during restoration or replication. Instead of selecting only those specific objects, all the objects were selected. This issue has been fixed.
Fixed an issue where the hierarchical and archival-child objects were not processed using EZ-restore and EZ-replicate.
Fixed an issue for the EZ- Replicate, where the file upload count was incorrect.
Release Date: September 28, 2025
Enhanced multi-bucket handling to ensure records are processed without creating duplicate entries.
Fixed an issue preventing users from viewing record differences when multiple templates were committed to the repository. Diff counts now display accurately.
Resolved a deployment failure scenario where templates containing multiple buckets caused object deployment errors.
Fixed a defect where builds failed because of null entry objects. Builds now complete successfully.
Improved stability of data uploads to S3 to ensure seamless and reliable transfers.
Implemented safeguards to prevent failures in multi-object set templates during execution.
Release Date: September 21, 2025
Enhanced rollback functionality to ensure that inserted records are deleted and updated records are accurately reverted to their previous state.
Resolved an issue where duplicate objects were displayed when working with multiple buckets..
Fixed an issue where optional fields were incorrectly considered during delete operations — now only record IDs are considered for deleting the records.
Addressed duplication issues when using the same branch with the VC Revision Range option including both commits. Objects are no longer duplicated.
Introduced support for multi-bucket functionality in templates, enabling better CI/CD data migration deployments and commits..
Release Date: September 14, 2025
Resolved an issue where the ID and Status/Error fields were displayed in an incorrect order when viewing success or failure results in the Data Loader modules.
Enhanced the log display for bulk operations to present users with optimized, clear, and relevant information for better troubleshooting and analysis.
Release Date: September 10, 2025
A fix has been provided to address a null pointer exception occurring in instances with AuditLog enabled, ensuring stable and consistent execution.
Release Date: August 31, 2025
Resolved an issue caused by an unwanted forward slash that disrupted the complete data migration flow in both nCino and Data Loader. Customers must re-run the affected jobs to process data successfully.
Release Date: August 24, 2025
The dependency on the uber jar has been removed. Bulk data operations are now handled programmatically in the backend, improving efficiency, stability, and maintainability of the system.
A Salesforce discrepancy previously prevented source IDs from being fetched correctly. This issue has been resolved with a code fix, ensuring accurate retrieval and consistency of source IDs.
A code fix has been applied to enforce correct permission requirements:
Source ORGs now only require read access.
Destination ORGs require write access.
Release Date: August 17, 2025
A fix has been implemented to ensure that Record Types are now correctly assigned to records during processing. This resolves issues where records were previously created or updated without the appropriate Record Type association.
A fix has been rolled out to ensure that, during data deployment, the deployment status is fetched accurately, resulting in a more reliable and successful deployment process.
Release Date: Aug 10, 2025
Improved logging capabilities for enhanced tracking and traceability.
Enhanced Data Loader Pro job cloning to ensure accurate replication with all settings retained.
Improved cloning process for Data Loader jobs to maintain configuration integrity.
Resolved issues to ensure reliable upload, insert, and delete operations for files.
Release Date: August 03, 2025
The processing of the commit jobs through the commit workspace has been streamlined.
An issue affecting the reliability of Data Loader Pro job execution has been resolved, ensuring smoother performance under high-load conditions.
An issue that is occurring during the clone operation is rectified
Resolved an issue where the clone functionality did not behave as expected, ensuring cloned jobs retain original configurations accurately.
Release Date: July 27, 2025
CI Job execution via the queue has been streamlined to ensure consistent and reliable processing.
A fix has been implemented to ensure leading and trailing spaces are correctly handled during nCino and DataLoader job executions, improving data accuracy and consistency.
Release Date: July 20, 2025
Resolved an issue impacting feature template functionality to ensure seamless loading, selection, and execution across workflows.
Implemented a fix to ensure reliable data deployment using migration templates, addressing inconsistencies during dataset migration.
Release Date: July 13, 2025
A fix has been implemented to ensure that pagination functions reliably and transitions between pages occur seamlessly without disruptions.
Release Date: 25 June 2025
New Access Controls can now be created from a home page directly.
Release Date: 11 June 2025
The following content provides information and videos on new capabilities associated with Guard.
Permission Set Allow list and Permission-specific Allow list controls are moving to the Access & Permissions module and are referred to as Access Controls.
Users can now Export Data Classification results in the CSV format.
Release Date: 28 May 2025
This release included several bug fixes as well as back-end enhancements designed to optimize processing efficiency and support future feature development.
Release Date: 21 May 2025
AutoRABIT Guard's Automated Data Classification scans and classifies data based on major regulatory standards—PCI, HIPAA, GDPR, COPPA, and more. It provides visibility into sensitive data within your Salesforce environments and helps understand where and how it is used.
Quick Explorer allows users to select one of the pre-built queries to get immediate security and access control insights.
Policy drafts can be created directly from Permissions Explorer now.
Users can now filter risk assessment settings in relation to each of the compliance regulations: GDPR, HIPAA, PCI, PII, etc.
For each risk, the user can see which categories are assigned to it and why.
We have added important information to the email received when a change happens in the monitored Salesforce org.
Release Date: 16 April 16 2025
When users add their first Salesforce org, we automatically create two policies to be used as templates. This can help you understand policies a lot faster and use them as a starting point.
Additional Filters in Permissions Explorer: Users can now add additional filters to the permissions explorer to better understand if there are overprivileged users.
New Metrics in Risk Assessment: We now show an “overview” and “impact” on each risk of the Risk Assessment. This can help you understand more about each risk and how it impacts your org’s security posture.
Offending Changes Added to Monitoring Page: We now show offending changes directly in the Change Monitoring page. Previously, offending changes were only visible from the Policy page.
Search in Permission Explorer: It’s now easier to find permissions in the Permissions Explorer, using free-text search.
Release Date: 21 March 2025
Multi-Factor Authentication (MFA) for Guard: MFA is now implemented for Guard.
User Lockout After Failed Login Attempts: Users will be locked out after three consecutive failed login attempts and notified via email.
New Settings Page: The Admin section has been moved to the profile menu for improved navigation. Users can access Settings from the dropdown menu, which includes Salesforce Orgs and User Management.
Criteria-Based Policies for Permissions: Users can now create criteria-based policies for permission-specific policies, extending the existing capability for permission set policies.
Removal of Clickjack Protection Setting from Risk Assessment: The Enable Clickjack Protection for Setup pages setting has been removed from Risk Assessment due to Salesforce limitations.
Rebranding of SPM to Guard in Emails: All customer-facing emails now display "Guard" instead of "SPM."
Identification of Sandbox Type Upon Login: Guard now determines and stores the sandbox type for usage tracking when a sandbox org is registered.
Move Management Console to Settings Page: The Management Console is now integrated into the Settings page, and the Delete User button has been relocated to the User Detail page.
October 2022 - New Features, Enhancements, Improvements, and Bugs Fixed
You can easily log in to CodeScan Cloud by setting up a Single Sign-On (SSO) through SAML-based third-party identity providers such as Okta, PingOne, and Microsoft Azure.
For more information, see .
The ability to download a CSV file containing the issues has now been added. The CodeScan CSV issue export option can be found in the More menu. Prior to this release, this functionality was only accessible to CodeScan Self-Hosted users; however, we have now enabled support for Cloud users as well.
For more information, see
CodeScan now has a new rule added to their Quality Profile called Do not use vulnerable packages, which checks for deprecated and outdated dependencies in the project and highlights the vulnerabilities available.
Previously, project reports were available for download for the main branches. With this update, we now support generating reports manually or by scheduling them for every project branch.
For more information, see
The drop-down list for the entry of Rule Parameters has been introduced to the improved Activate in Quality Profiles page. You could only feed regular text into fields prior to this release.
Fig 1: Old Screen
Fig 2: New Screen
With this update, the Add Member button on the Members page for all CodeScan versions is deleted.
This release includes significant security improvements. Updating is strongly recommended.
The existing metadata rules in CodeScan have been tweaked for SFDX compatibility.
Significant improvements in the ways GitHub is triggered within CodeScan.
Fixed a minor issue where the analysis would start for both branches when merging a feature branch into the master branch. This shouldn't happen as analysis should be initiated only on the master branch and not the feature branch.
Fixed an issue where the target branch's newly added code was not being fetched when the analysis was running.
Fixed an issue where users could view invalid grant type errors while running a pull request analysis.
Added the ability to add comparison branches to a Salesforce project in this release.
Key characteristics to look for:
The comparison of issues
The transfer of issue resolutions to the main branch of the Salesforce project.
For more information, see .
Below are the nCino related rules added to the existing Apex/Salesforce Metadata rule sets and are tagged as “ncino-goldstandard.”
Process Builder Must Reference Product: For general automation and validation best practices, associate actions in the system to a product line, product type, or product feature. Depending on how widespread the automation is, this ensures that follow-on phases for new lines of business have limited rework
Workflow Must Reference Product: For general automation and validation best practices, associate actions in the system to a product line, product type, or product feature
Validation Rule Must Reference Product: For general automation and validation best practices, associate actions in the system to a product line, product type, or product feature
This April's CodeScan cloud release includes the Compute Engine parallel processing capability. The key benefit is that it allows multiple analysis jobs to run in parallel in a fluid manner, reducing analysis job duration during peak usage and thereby improving user experience.
CodeScan self-hosted is now compatible with SonarQube™ 8.9 and SonarJS 6.2+. For more information, see
The log report is now better than before. View your project analysis job's detailed log report, which includes the reasons for failed jobs.
In this release, the CodeScan integration with GitHub actions has been improved. When working on Github actions, the report generation feature has been included, which displays accurate findings based on analysis.
Minor performance, bug fixes, and security improvement can also be observed in the CodeScan portal.
Fixed a minor bug where the scheduled Salesforce jobs were not running in an instance because of several hardcoded values in the product sources.
Fixed an issue where the project analysis job took a long time to accomplish and displayed the "Job took too long" error in some instances.
This release incorporates new features, enhancements, and resolved issues from all previous significant releases. If you're upgrading from an earlier version of Vault, check the release notes for any interim versions or details about additional improvements in this release over your current release.
Release Date: 06 July, 2025
Job Comment Retention
An issue where the Job Label would overwrite the existing Job Comment during job edits has been resolved. The comment field will now retain its original value unless explicitly modified by the user.
RBC Deployment Templates Accuracy
The logic for handling RBC Deployment Templates has been refined. The system now correctly accounts for omitted templates and accurately calculates the count of selected templates, ensuring consistent and reliable template tracking.
Rollback Execution Stability
Enhancements have been made to ensure that rollback operations, even when triggered on the nth iteration, execute seamlessly without disruptions.
Version Control CI Jobs Ordering
The display order of CI Jobs under Version Control has been improved. Jobs are now consistently sorted by their Modified Date, ensuring that the most recently updated jobs appear at the top of the list.
Selected Templates Preservation
In the CI Job configuration, the order of templates within the Selected Templates section is now preserved as per the user’s arrangement. This ensures better clarity and user-defined control over template sequences.
Triggered Date Population
A fix has been applied to ensure that the Triggered Date field is correctly populated whenever a job is initiated. This resolves earlier inconsistencies and supports accurate build history tracking.
Release Date: 29 June 2025
CI Job Failure Resolved an issue causing CI job failures due to improperly rendered template objects. The fix ensures templates are now rendered correctly, allowing jobs to execute successfully.
CI Job Baseline Revision Implemented a fix to ensure the rollback mechanism for CI job baseline revisions functions as expected, maintaining consistency and stability during version changes.
Release Date: 15 June 2025
DL Job Execution Stability
A fix has been implemented to ensure that DL job executions complete without errors, improving overall job reliability and system stability.
Enhanced the tracking mechanism to accurately reflect both cumulative and individual statuses of deployment jobs, including those targeting post-deployment ORGs.
Upgraded the Salesforce integration to use the latest API version 64, ensuring continued compatibility and access to the newest platform features.
Resolved an issue where builds were not reliably triggered upon commit. The trigger-build-on-commit functionality now operates seamlessly and consistently.
Release Date: 08 June 2025
Validation Rules Activation Resolved an issue where enabling validation rules was not functioning consistently.
Rollback Object Configuration Fixed a bug to ensure object configuration data is loaded without discrepancies during rollback.
Job Group Cloning Addressed issues to ensure job group cloning now completes reliably.
CI Job Baseline Revision Corrected an error encountered during CI Job baseline revision selection.
Release Date: 01 June, 2025
API Refactoring
Refactored core APIs to align with industry best practices, enhancing performance, scalability, and maintainability across the platform.
User Permissions
Standardized user permission handling across both nCino and DataLoader. Users now have access strictly based on their assigned roles and permissions, ensuring better access control and security.
DL PRO Job Execution Notifications
Enhanced job execution flow so users will now receive notifications only upon completion of DL PRO jobs, reducing noise and improving clarity in system alerts.
DL PRO Filters Persistence
Addressed an issue where filters were reset after being edited. Filters now persist correctly post-edit, ensuring a seamless user experience during job configuration.
DL PRO Job Execution Stability
Resolved an IndexOutOfBoundsException occurring during DL PRO job execution. The fix ensures more stable and error-free job runs moving forward.
Release Date: 25 May, 2025
Fix on Rollback
A comprehensive fix has been applied to ensure rollback functions correctly across all scenarios without failure.
CI Job Code Fix
Resolved discrepancies in CI job execution. All triggered actions are now accurately reflected, ensuring reliable and traceable job status.
Release Date: 18 May, 2025
Post-Deploy ORGs Selection
Introduced a validation that prevents selecting post-deployment ORGs unless the main ORG is selected, enhancing deployment integrity.
Fixed an issue where rollbacks for parallelly triggered ORGs did not behave as intended.
Resolved a bug ensuring post-deployment ORG statuses are now independently tracked and are not tied to the destination ORG’s status.
CI Job Fixes
Addressed an issue where failed CI jobs remained stuck in the queue.
Applied a fix to prevent CI jobs from staying queued for extended periods, ensuring timely job execution.
Release Date: 10 May, 2025
Rollback Behavior Improved
Rollback operations now skip any undeployed changes introduced after deployment edits, ensuring only successfully deployed components are eligible for rollback.
Release Date: 4 May, 2025
Post-Deployment ORG Rollback
Users can now select specific ORGs used during post-deployment for targeted rollback actions.
Individual Template Rollback
Introduced support for rolling back individual templates, giving users finer control during remediation.
Release Date: 27 April, 2025
Data Transfer Fix
Resolved an issue causing data transfer failures. Uploaded files are now reliably processed without interruption.
Release Date: 20 April, 2025
Template Creation Fix
Implemented a fix to ensure template creation with multiple buckets is stable and error-free.
CI Job Execution Fix
Resolved an issue causing CI jobs to fail. Jobs now execute successfully under all expected conditions.
This update introduces several new rules and bug fixes for current rules. This includes:
Improved the CodeScan parser as it relates to Visual Force. Specifically, the parser had some issues recognizing parts of Aura code (for example, with components (cmp), the parser was unable to recognize divs and spans across multiple lines). With this release, we have corrected these issues and verified that the Visual Force parser for .cmp, vf, xml, and .page files are all parsed properly. Further, CodeScan users can successfully see these issues after analysis.
Fixed a NullPointerException with the Apex rule “Null Coalescing Operator.”
Apex Rules:
Duplicate method implementations: Methods should not share the same implementations. To prevent duplication and confusion, avoid using two methods with identical implementations.
Code length: Lines should not be too long in APEX. Limiting the length of code lines enhances code clarity and readability by reducing complexity and improving quick understanding.
System.runAs to test user permissions: To ensure accurate and realistic testing of user permissions, it is crucial to utilize System.runAs during test execution, ensuring logic is tested in the same context in which it will run.
Relative Salesforce URLs: Salesforce pages should use relative URLs, as code using absolute URLs for Salesforce pages will break in different environments.
“If ... else if” should have “else” case: Include a default case using an "else" statement at the end of "if" and "else if" clauses to handle all conditions and provide code clarity.
Limit case clauses in switch statements: Using a large number of case clauses in switch statements creates complex, difficult-to-read code.
Avoid Identical Expressions on Both Sides of a Binary Operator: When both sides of a binary operator have identical values, the condition will always give the same result.
Avoid Sending Emails in Loops: Avoid using Messaging.sendEmail within loops to prevent exceeding Salesforce governor limits and to enhance application performance.
Avoid duplicate conditions in "if"/"else if" and "switch": When the same conditions are used in statements like "if"/"else if" and "switch", it can lead to duplicate or dead code.
API Versions 7.0 through 20.0 Retirement: The retirement of older Salesforce Platform API versions (7.0 through 20.0) after the Summer '22 release is a critical step to ensure the continued smooth operation of Salesforce applications.
Avoid using methods getDescribe and getMap inside Loops: The ‘getDescribe’ and ‘getMap’ methods typically involve fetching metadata information for objects and fields. Invoking them inside loops can result in unnecessary overhead.
Assertion Rules:
Use Assert.areEqual instead of Assert.isTrue: This rule detects Unit test assertions in object references equality. Instead of using Assert.isTrue as an equality check, these assertions should be made by more specific methods, like Assert.areEqual.
Use Assert.isTrue instead of Assert.areEqual: When asserting a value that is the same as a Boolean literal, use Assert.isTrue, instead of Assert.areEqual.
Use Assert Equals Instead of Boolean Equality Assertion: This rule detects unit test assertions in object references equality. Instead of using Assert.isTrue combined with "==" as an equality operator, these assertions should be made by more specific methods, like Assert.areEqual (expected, actual).
Unit Assertions should include a Message: Unit assertions should include a message. In other words, use the three-argument version of Assert.areEquals(), not the two-argument version.
Unit Test Method Contains Too Many Asserts: Unit tests should not contain too many asserts. Many asserts are indicative of a complex test, for which it is harder to verify correctness. Consider breaking the test scenario into multiple, shorter test scenarios. Customize the maximum number of assertions used by this Rule to suit your needs.
Non-Unit Test Methods Should Not Contain Asserts: Asserts should only be used in test methods.
Misuse of Assert Class: Assert Class can be misused if not applied correctly. To ensure the correctness of our code and avoid common pitfalls, establish best practices for its usage.
Use Messages in Assert Statements: Ensure that messages are included when using the assert method with the message parameter to improve code quality and make it easier to identify the cause of failures during testing and debugging.
Consider Using Assert in place of System.Assert: This new class aims to enhance the readability and maintainability of test code for developers. It is preferable to use Assert in your tests instead of older System.Assert methods.
LWC Rules:
Enable Salesforce Lightning Web Security (LWS): Enabling LWS ensures that the Lightning components within our Salesforce instance are executed in a secure and controlled environment, reducing the risk of potential security vulnerabilities.
SF Meta:
Adopt the ICU Locale Formats instead of JDK locale formats: Salesforce is retiring the JDK locale formats with the Spring ’24 release. ICU is the new standard enforced in API version 45. Make sure your custom code does not use JDK locale formats and instead uses locale-neutral methods.
Set Flows to Auto Layout: Implementing auto-layout for your flows helps designers modify layouts more quickly, allowing them to iterate on their designs with greater speed. It ensures elements are perfectly aligned and evenly spaced, improving readability in complex Flows.
Potential Overuse of Rollup Summaries: Ensure compliance with Salesforce's limit of 25 roll-up summary fields per object to prevent potential issues arising from exceeding Salesforce platform limits.
Improvement was provided on how to fix for the "Deserializing JSON is Security Sensitive" rule.
We provided a fix on the "sf:AvoidUsingHardCodedId" rule not detecting hard-coded IDs as expected.
Wrongly identified violations in specific scenarios were fixed for the "Comments are Required" rule.
The rule "sf:AvoidPublicFields" was updated to exclude public fields with the @InvocableVariable annotation.
We provided a fix for the rule's missing root element in "RuleSet."
We provided a fix for the "Consider removing inactive flows" rule not working correctly.
Uninstalled connected apps restricted — New authorizations will be blocked unless specific permissions are granted.
Note: The existing connections between AutoRABIT and Salesforce are not going to be impacted by this change
OAuth 2.0 Device Flow blocked — Not used by AutoRABIT.
New permissions introduced:
Approve Uninstalled Connected Apps
Use Any API Client
Vault, ARM, and CodeScan Cloud connect to Salesforce via Client Credentials Flow, which creates an uninstalled connected app.
Existing connections (before September 2025): Will continue to work.
New connections (after September 2025): May fail unless permissions are updated by your Salesforce admin.
For existing customers with an already connected Org/s to AutoRABIT No action is required.
Recommended configuration: &#xNAN;For existing customers, adding net new Salesforce Sandbox Orgs
Install Connected App
In your Salesforce Org, Navigate to Setup → type Connected Apps OAuth Usage in the Quick Find box.
Find the AutoRABIT connected app in the list. If it’s not installed, there will be an Install button next to it.
Click Install, then confirm on the subsequent page.
Optional Configuration: &#xNAN;Applies to initial authentications with AutoRABIT made after the connected apps security change made by Salesforce, or net new production orgs (this will be updated, as more information becomes available from Salesforce)
Actions Required
Identify AutoRABIT Connected Apps:
Go to Setup → Connected Apps OAuth Usage in Salesforce.
Locate entries linked to AutoRABIT.
Update User Permissions:
If API Access Control is enabled: Assign “Use Any API Client.”
If API Access Control is not enabled: Assign either “Approve Uninstalled Connected Apps” or “Use Any API Client.”
Grant these permissions only to trusted integration users.
Use a dedicated integration user for AutoRABIT.
Grant only minimum required permissions.
Review unused connected apps regularly and remove them.
Contact AutoRABIT Support ([email protected]).
Refer to Salesforce’s announcement: Prepare for Connected App Usage Restrictions Change.
Refer to the Salesforce documentation below for additional details.
Will my existing AutoRABIT connections stop working? No. If you connected AutoRABIT products (Vault, ARM, CodeScan Cloud) to Salesforce before the enforcement date in September 2025, your existing integrations will continue to work.
What happens if I try to create a new connection after September 2025? New connections may fail unless your Salesforce administrator assigns the new permissions introduced by Salesforce (Approve Uninstalled Connected Apps or Use Any API Client).
Which Salesforce permission should be used? If API Access Control is enabled in your org, assign 'Use Any API Client'. If it is not enabled, you may assign either 'Approve Uninstalled Connected Apps' or 'Use Any API Client'. These should be granted only to trusted integration users.
Does AutoRABIT use the OAuth Device Flow? No. AutoRABIT uses the OAuth 2.0 Client Credentials Flow, which creates an uninstalled connected app in your Salesforce org. The blocked device flow is not used by AutoRABIT.
Is there a long-term solution beyond permissions? Yes. AutoRABIT is actively working on enhancements to move towards installed connected apps for greater security and compliance. Updates will be shared in future product releases.
Do I need to reinstall AutoRABIT in my Salesforce org? No reinstallation is required. You only need to ensure the correct Salesforce permissions are assigned to your integration user for new connections after September 2025.
Where can I read Salesforce’s official announcement? You can view Salesforce’s official article (here)[ https://help.salesforce.com/s/articleView?id=005132365&type=1]
Who should I contact if I face issues? Please contact AutoRABIT Support ([email protected]) for assistance with setup, permissions, or troubleshooting.
There are 19 new rules for Salesforce flows:
Inactive flows should be removed: Inactive flows may cause clutter in the Salesforce org. In extreme cases, they can begin to hit the organization’s limits. These should be removed if not being used.
Avoid Large Flows: Too many nodes can cause your Flow to become complex and unmanageable. Consider using Subflows to make your Flow logic reusable and scalable.
DML statements should not be included in the loops: SOQL and DML in Salesforce are bound by “Governor Limits.” If a large number of SOQL and/or DML calls are made in a short amount of time, you can run into a Governor Limit Exception. This rule minimizes the chances of this happening by letting users know when they are calling these in a loop.
Avoid creating nested loops in Flows: Nested loops within your Flows can cause them to become unreadable, inefficient, and complex. Consider using Invoked Actions to clean up complex Flows.
Document Flows and the Flow components: Flows should have adequate documentation. Any Flow elements without a description should have a violation thrown independently.
Avoid Hard-Coded Values in Flows: Hard-coded values in Flows can lead to unexpected output and make maintenance difficult. Instead, Get Records can be used for the respective object using the DeveloperName. If you’re creating criteria in an entry condition, you can reference DeveloperName (API Name) fields with a formula.
Flows Should Include Fault Paths: Fault paths are a way to handle errors that may occur in your Flow. Depending on the Flow and its purpose, errors can be logged, show an error screen, or send an email of the failure to a group of users. Flows should include Fault paths to ensure that all errors are handled appropriately.
Flow Naming: Standardized naming conventions allow an organization's Flows to be clean, maintainable, and readable. This rule enforces standard naming conventions for Flows and Domains.
Flow Variables & Resources Naming: This rule enforces standard naming conventions for Variables, Formulas, and Choices.
Flow Interaction Naming: This rule enforces standard naming conventions for Screens, Actions, and Emails.
Flow Logic Naming: This rule enforces standard naming conventions for Decisions, Assignments, and Loops.
Flow DML Naming: This rule enforces standard naming conventions for DML operations (Query, Update, Create, Delete).
Migrate Workflows and Processes to Flows: Process Builders and Workflows are being phased out over the coming year. In Winter '23 the ability to create new Workflows is being turned off, in Summer '23 the ability to create new Processes with Process Builder was turned off. It is recommended that these Processes and Workflows be migrated to Flows.
Use Fast Field Updates: If a Flow is only updating the record that triggered it, it should be using the Fast Field Updates option. This can be up to 10 times faster than the more flexible Actions and Related Records Flow.
Get Records Should Be Filtered: This rule mandates the usage of at least one filter in the Data element "Get Records" within Salesforce Flows. Enforcing this rule will encourage flow designers to think critically about their data retrieval needs and apply relevant filters, reducing the risk of performance bottlenecks and unoptimized queries.
Unused Flow Variables: Consider removing unused Flow variables to increase performance and readability.
Missing Null Handler After Get Records in Flow: By implementing a decision element to validate the result of the Get Records operation, you can proactively identify and handle cases where no data is retrieved. This allows you to avoid potential null reference errors and prevent unexpected crashes or data processing issues.
Duplicate DML operations in Flows: This rule aims to avoid potential issues caused by duplicate database operations that might occur if users go back and forth between screens, triggering the same actions multiple times.
Flows API Version Is Too Old: This rule identifies flows that are using older API versions. Consider updating the API versions of any flows found.
Bug Fixes:
Rule Misfire fixed: Corrected Apex code incorrectly detecting TODOs.
Fix provided for the rule “Avoid Using Hard Coded Credentials for Authentication”: Regex updated.
Xpath added for the rule "SOQL Injection possible" to cover the public and class-level variables.
License Key Update: The license has been updated and will now be associated with specified projects.
Parser issue fixed on the rule: “Avoid Untrusted/Unescaped Variables in DML Query."
A new rule parameter, allowList, added to the rule “Track Usage of @SuppressWarnings.”
Apex Parser Update for Null Coalescing Operator: There will be no parsing error when ?? is present in Apex code.
Integrated ZOHO as a ticketing tool for CodeScan support: We've now integrated ZOHO as a way to submit a ticket for any CodeScan-related support. The AutoRABIT Support Portal allows users to submit a support request.
New Compliance rules for Salesforce Metadata: We made our Salesforce Metadata Ruleset more powerful with the addition of two new rules that helps minimize and prevent the Salesforce users from being provided with unnecessary privileges.
Limit number of page layouts per object: In the Salesforce Metadata ruleset, we added a new rule "Limit number of page layouts per object" which helps to restrict the maximum number of page layouts that can be accommodated under a single object.
Limit number of custom fields per object: In the Salesforce Metadata ruleset, we added a new rule "Limit number of custom fields per object" which helps to limit the number of custom fields set for a salesforce object. The rule also allows users to specify object-specific custom field limits.
Log4j2 core and API versions are upgraded to 2.17.0: To address the Apache Log4j Security Vulnerabilities thread, we updated the Apache Log4j version dependencies to 2.17.0.
The user was unable to delete multiple projects from the Manage Projects page due to a bug, which has now been resolved.
After deleting and adding a new repository into the CodeScan, we were getting an 'Unknown error'. It has been fixed now.
There was an issue in CodeScan Cloud where you couldn't create a branching, but it's now fixed and working properly.
When a user attempts to analyze a project by clicking 'Re-run the analysis,' it fails. This problem has now been resolved.
There was an issue with the links from GitHub fork PR and it is not linking to the correct branch. This issue has been fixed now.
CI Job Deletion When a CI job is deleted, the process now ensures that all associated resources are efficiently managed, helping to optimize storage usage.
ExternalID Populated in Single Data Loader The Single Data Loader will automatically populate the ExternalID field, streamlining the data entry process and ensuring consistency.
Disable Delete Button for In-Progress Jobs The delete button will now be grayed out and disabled for any In-Progress CI jobs, preventing accidental deletions during the execution process.
Release Date: 10 September 2024
The following features have been enhanced to facilitate user productivity, simplify tasks, and perform selections more easily.
UI Improvements for VC Baseline Revision The user interface for the VC Baseline Revision has been enhanced to improve usability and navigation.
Download Option for Selected Records A new provision allows users to download selected records directly from the interface, simplifying data management.
"Select All" Option in Feature Type A "Select All" option has been introduced in the Feature Type selection, making it easier to select multiple items at once.
System Bypass Logic - Workflow Rules: This rule is required in custom workflow rules for integration users
System Bypass Logic - Validation Rules: This rule is required in custom validation rules for integration users.
Note regarding the two different CodeScan Self-Hosted editions:
We recognize that our self-hosted customers have different requirements regarding the SonarQube (SQ) versions that are supported/allowed by their organizations. As such, CodeScan is committed to supporting a wide spectrum of versions to accommodate this variance.
Currently, the most recent Long-Term Active version of SonarQube is 2025.1 LTA. Recently, SonarQube released Community Build 25.10, while the latest version for their other editions is 2025 Release 5.
The previous version of SonarQube Long-Term Active was 9.9 LTA. In between, SonarQube released 9 other versions (10.0–10.8).
In order to support a wide range of these SonarQube versions, AutoRABIT decided to provide two versions of CodeScan self-hosted editions to the market to ensure ongoing SonarQube compatibility. Please note that we currently only certify CodeScan on the Community Build. We are working closely with SonarQube to extend our verifications on their other editions as well.
Our Eagle Edition is designed for those customers who run on SonarQube 10.6, 2025.1 LTA, 25.2, 25.3, and 25.4.
Our Tiger Edition is designed for those customers who run on SonarQube 9.9 LTA–10.3.
Please see our corresponding SonarQube Compatibility Matrix for detailed guidance.
We do intend to keep as much feature parity with the editions as possible; however, there will be slight variances. Please review our release notes for detailed information regarding each edition’s respective capabilities.
Additionally, the following diagram provides more detailed information regarding release versioning and release dates.
Regarding earlier CodeScan Versions: Our July 2024 release (24.0.8) fully supports SQ 9.9 LTA as well as SQ 10.0, 10.1, and 10.2.
For customers running newer versions of SonarQube, we encourage you to upgrade to our CodeScan Self-Hosted Eagle Edition v5.0 (25.1.2). This release is generally available as of October 17, 2025, and is compatible with SQ 2025.1 LTA, 25.2, 25.3, 25.4, and SQ 10.6–10.8. Please refer to the release notes for Eagle Edition v5 for complete documentation of features.
For customers running older versions of SonarQube, we encourage you to upgrade to our CodeScan Self-Hosted Tiger Edition v3.0 (25.0.1). This allows customers to have a newer version of the CodeScan plug-in while utilizing older versions of SonarQube™.
Downloads: After identifying your version of SonarQube, refer to the Installing CodeScan Self-Hosted page to view the CodeScan Downloads & Compatibility Chart.
Future SonarQube Releases: We aim to have support for the latest versions of SonarQube approximately 12 weeks after their release date. Each version will be supported for 12 months.
Additional Support: If you have any questions, comments, or concerns, please contact your Account Team directly.


Numerous configuration options are available to users when setting up their profile in ARM. The Profile section allows users to view and update their basic information, personal email settings, etc.
To access user preferences, click your user name in the upper right corner and select Profile.
The Personal Details section displays your full name, ARM user name, email address, phone number, etc. Your personal details will be populated, as the system administrator must enter this information when creating a new user account. In this section, you can update your name, phone number, address, etc., accordingly.
The My Projects section will list all the projects that you have created or have permission to view. Users with admin-level permissions will have access to all projects.
The My Roles displays the list of roles assigned to the user. If you have admin roles and permission, you can perform all the tasks an administrator can perform and access all modules within ARM.
If users maintain an individual version control branch for every release, they must map every branch to Salesforce Org and Version Control branches to keep synchronizing with Salesforce Org. To overcome this daily routine, ARM provides the option to skip the Org Mappings part and directly perform commits.
View the Salesforce Orgs assigned to you, or you have permission to view.
View the Version Control Repositories here based on the Salesforce Orgs selected in the My Salesforce Orgs section. Map the required repositories by choosing the correct Credential from the drop-down field. Click Test Connection to determine whether the connection has been authenticated or not.
Under My ALM Mappings section, you can map your ALM using your credentials or Re-Authenticate Jira ALMs configured with OAuth access.
For ALM type IBMRTC (IBM Rational Team Concert) and JIRA, we have added the filter to fetch specific work items according to the filter applied.
According to the filter set, only specific work items will get fetched. When the developers progress (via EZ-Commit or merge operation in ARM) on updating the ALM status, they are reflected on the corresponding work items. If the user wishes to discard the filter selected, uncheck the Apply My Filter option, and all work items will get fetched.
My Default Page is the first page that appears when you log in to ARM. You can customize ARM to open any page as the default page.
The next step is to map your profile with the Version Control system you will be working with and the associated Salesforce Org.
Go to the Profile section.
Scroll down to My Salesforce Orgs.
Select the Salesforce Org and assign the Salesforce Org User to them.
Next, Scroll down to My Version Control Mappings.
Select the Repository and assign the user.
Click Save.
Go to Admin > SF Org Mgmt, select your org, and scroll down to Salesforce Org - Mappings.
Select the mapping against the version control that you have set up.
Click on Save Mappings.
413: Status Error: Users may encounter a 413-status error in the browser console when trying to upload duplicate profile files that have been resolved after downloading from version control. This occurs when users try to download numerous files at one time. Download one profile file at a time to resolve the error.
Inviting colleagues to AutoRABIT (ARM) lets them run commits, deployments, and CI jobs under their own accounts—so actions are tracked to the right person, and permissions stay aligned with their role. Only Org Administrators can create or modify users.
Log in to ARM.
Hover over Admin and click Users.
Click Add User.
Complete User Details and assign a Role Permission Set that matches the person’s responsibilities.
Choose one of the activation options:
Save & Activate – sends the invitation email immediately.
Save Now & Activate Later – save the profile and activate at a future time.
The new user receives an email to set their password and log in.
Newly created users appear in Admin › Users.
You can edit most profile fields and permissions after creation—except Username and Email (they are immutable).
Go to Admin › Users and locate the user.
Click the Edit icon.
Update fields as needed and click Save.
No. Usernames and emails are locked once the account is created. To correct either field:
Delete the old account (Admins: remove the user from the list).
Create a new account with the correct username/email.
Reassign the same roles and permissions.
You’ve reached your organization’s license limit. Contact your account manager or AutoRABIT support to purchase additional seats or review discrepancies.
09 September 2024
Ability to Download CI Job Backup Snapshot Users can now seamlessly download the entire backup snapshot of CI Jobs, providing quick and easy access to crucial data. Please refer to the Knowledge Base for more information.
Support for Post Deployment ORGs in Rollback We’ve added support for including Post Deployment Orgs in rollback processes. This enhancement ensures seamless rollback operations, maintaining environment consistency and control during deployments. Please refer to the for more information.
Skip Records Functionality Enhancement The Skip Records functionality has been improved by replacing the icon with a checkbox. Please refer to the for reference
Depicting Fields Excluded from Compare and Identifying Record Differences Between Environments Fields excluded from the compare operation are now clearly depicted, helping users focus on relevant data. Differences between records across environments are highlighted for quicker, more accurate assessments.
Option to Delete CI Jobs in Queue Users can now delete CI jobs directly from the queue, giving them greater control over their CI pipelines. This feature optimizes resource usage by allowing the removal of unnecessary or outdated jobs.
A Standard User is an individual authorized by the Customer to log in to and directly use AutoRABIT’s subscribed products.
Platform Owners/Admins are included in the Standard User class, allowing customers to manage admin rights without affecting licensing terms.
The number of licensed users represents the total unique users of the products, calculated throughout the entire course of the Subscription Term.
A Platform Integration User is an individual authorized by the Customer to commit to a Source Code Management (SCM) system, where that external commit is then used in any ARM process. This is primarily intended to represent users who interact with ARM through Git and do not have a Standard User license.
AutoRABIT tracks the usage of ARM as an orchestration engine through version control systems. The unique identifier used is the associated email address. Therefore, it is important that activity be linked to official customer email addresses to avoid double-counting users who may use personal email addresses.
Code Commits and Licensing: Any person who commits code to an SCM system, where that commit is later used in an AutoRABIT function, requires a Platform Integration License (unless the person committing has a active AutoRABIT ARM License). This would include external commits to the SCM System.
Service Accounts: If a service account triggers automation or integrates with AutoRABIT, the individual or team responsible for the actual code commit must still hold a Platform Integration License. This ensures that all contributors whose actions trigger AutoRABIT processes are appropriately licensed.
Commit Count in SCM Systems: For SCM systems such as Git, multiple commits pushed simultaneously are counted separately toward the user license.
Platform Integration Users are sold in blocks of 10. This means any user meeting the criteria above who is not also a licensed Standard User will be counted. These are not “named” users; instead, users are defined by their activity within the quarter. The count is recalculated each quarter.
Calculation:
The average high-water mark of the two highest quarters is used, rounded up to the nearest block of 10, to determine the total Platform Integration User count for the term.
Counts reset each quarter and include both new and recurring users.
Example:
ACME Corp purchases 10 Platform Integration User licenses.
Quarter 1: 15 users
Quarter 2: 8 users
Quarter 3: 17 users
Quarter 4: 5 users
The average of the two highest quarters (15 and 17) is 16. Since licenses are sold in blocks of 10, ACME oversubscribed by 6 users and would need to purchase an additional 10 licenses.
The subscription model aligns with the contract start date, not the fiscal year. For example, if the contract starts in May 2025, the quarterly data points would include: Q1 (May, June, July 2025), Q2 (August, September, October 2025), Q3 (November and December 2025, January 2026) and Q4 (February, March, April 2026).
Licenses are sold in blocks of 10 and always round up. If oversubscribed by 6 licenses, purchase an additional 10. If oversubscribed by 11, purchase an additional 20.
Unique Email IDs: ARM counts users via unique email IDs retrieved from Git. If an individual uses multiple email addresses for commits, they will be counted as separate users. To prevent this, ensure best practices when using Git.
Support for Serial Backups
With this release, we have added the flexibility to enable your backup configs to run in serial mode. This prevents overlap of backups triggered under the same config and helps reduce redundant data storage caused due to overlapping backups.
Access restriction through SSO for non-registered users
We’ve added the capability to Vault administrator to prevent the auto-creation of new users in Vault from SSO ID providers like OKTA and Microsoft Azure AD.
Notifications for Restore/Replicate operations
With this release, we have enhanced the capability of how the users get notified once an operation is performed inside Vault. You will now have a field to add multiple recipients who should receive notifications whenever the action is performed. The currently logged-in recipient will automatically be enabled to receive the notifications.
CodeScan offers three primary deployment options: Cloud, Self-Hosted, and Government. Release notes and information are available for each deployment type.
No Web UI Login Required: A Platform Integration User does not need to log in to the AutoRABIT Web UI to be counted as a user.
Remote Access for Standard Users: Active Standard Users can use ARM remotely without additional license requirements.





Then, the sub-users can view the mapped Salesforce Orgs in the EZ Commit screen once the user is added.














CodeScan for Government
CodeScan for Government is a secure, compliance-focused solution designed to meet the unique needs of public sector Salesforce environments. Built with enhanced security protocols and governance in mind, it empowers agencies to maintain code quality, enforce standards, and reduce risk across their DevOps pipelines.
Please note: Access to CodeScan for Government release notes is currently limited to government license holders only.
Key benefits:
Centralized, encrypted storage managed by ARM.
Role-based sharing (global vs. private).
Eliminates hard-coding credentials in jobs or scripts.
Hover over Admin and click Credentials.
Click Create Credential.
In the pop-up, enter a Credential name and choose a Credential Type:
Username with Password
SSH
HashiCorp Vault
SSH Certificate
Provide the service username and password. Choose a Credential Scope:
Global – share with the team.
Private – visible only to you.
Upload or paste your private key (optionally protected by a passphrase). ARM stores the key and uses it for Git operations over SSH.
Add HashiCorp Vault credentials once; ARM can now generate a new Vault Token automatically via AWS authentication whenever the old token expires.
For details, see the dedicated HashiCorp Vault guide.
SSH certificates pair a public key with a signature from a trusted Certificate Authority (CA). A Git server that trusts the CA accepts any certificate signed by it.
Upload the certificate-signed key while creating the credential.
Supported for GitHub Enterprise Cloud orgs.
Limitation: Available only for GitHub Enterprise Cloud.
Connect ARM to Jira via Personal Access Token (PAT) to meet enterprise compliance.
Select Application Token as Credential Type.
Paste the PAT generated in Jira.
Click Save.
Important Note: The Application Token credential type is not supported for ARM CI Jobs. It is intended only for enterprise Jira integration using a Personal Access Token (PAT). Do not configure Application Token as the credential type for CI Jobs. For CI Jobs, use supported SCM credentials (for example, Username and Password or others) instead.
Need PAT access? Email [email protected]. How to create a PAT in Jira: Atlassian docs.
New Cloud Features
Salesforce Project Branch Types: when adding a sandbox to your Salesforce project as a branch, you are now able to specify the type of branch you would like to add (Long or Short). Find out more here about branches here.
New Metadata Rules
BETA metadata ruleset added: our beta metadata ruleset has been added to this release. Currently, you will find rules covering security settings, custom fields, permissions, and record type ID's. This edition also includes a setting to define the metadata types to be downloaded. Find out more here for CodeScan Cloud and here for a Self Hosted package.xml file.
New Apex Rules
Aura Controller Naming: Aura Controllers should adhere to certain naming conventions. Only classes linked to a page as a controller or extension are considered.
Track Usage of @SuppressWarnings: overuse of the @SupressWarnings annotation can mean issues in your code are not picked up. This rule flags each usage to make sure it is needed.
Track Usage of //NOSONAR: overuse of the //NOSONAR rule suppression can mean issues in your code are not picked up. This rule flags each usage to make sure it is needed.
New Visualforce Rules
Avoid using Tab Characters Check (v4.4.5): checks that there are no tab characters ('\t') in the source code.
Field Level Security now specifies the field it is failing on.
Old Page API Version now specifies the API version in the message (v4.4.4).
Metadata parsing was improved to fix memory errors caused by larger types (v4.4.5).
Excessive Method Length no longer counts comments as lines.
Use Singleton now ignores Aura controllers.
NPath Complexity now calculates correctly around ternary statements.
False-positive fixed in Unnecessary Boolean Assertion.
Frequently Asked Questions (FAQs) have been integrated within the product documentation for easier reference. Please refer to the information for FAQs on CodeScan.
Static can not be used in Inner Class (v4.4.5): Static can only be used on fields, properties, and methods of top-level classes only.
Avoid using Tab Characters Check (v4.4.5): Checks that there are no tab characters ('\t') in the source code.
Avoid Public Fields now ignores Aura fields.
False positive fixed in InlineStyleAttributesCheck for lightning:formattedNumber tag (v4.4.4).
Field Level Security no longer detects WITH_SECURITY_ENFORCED (v4.4.4).
Edge cases of DML parsing fixed (v4.4.4).
Edge cases of Copado parsing fixed (v4.4.4).
Classes extending nested classes parsing fixed (v4.4.4).
General Parser fixes and improvements (v4.4.4).
InsecureEndpointRule throws StackOverflowError while analyzing the attached Apex class (v4.4.5).
Parsing error caused by using "Sharing" as Enum name fixed (v4.4.5).
Parsing error caused by using "import" (Javascript) fixed. BREAKING CHANGE - This will cause new errors to be created on previously unparsed files (v4.4.6).
Error caused by custom fields in SFDX projects fixed (v4.4.6).
Application Token (Enterprise only)







Release Date: 07 December 2025
A fix has been implemented to restore the functionality of the action button next to the download icon in Deployment History. The button now correctly expands the object set view, as intended.
A fix has been implemented to ensure that all jobs are immediately removed from the list after a bulk delete operation. Previously, one job continued to appear until the page was manually refreshed. The job list now updates correctly without requiring a browser refresh.
A fix has been applied to prevent heap-space and restart issues caused by processing objects with complex parent dependencies during initial template creation. The system now skips non-selected standard and non-nCino package objects, ensuring the login screen loads reliably.
Release Date: 30 November 2025
A fix was implemented to correctly handle multi-level parent relationships during DataLoader Pro migrations. An issue where ancestor object failures caused master and parent objects to fail has been resolved. The migration flow now isolates such failures and works reliably, including when Automatic Apply Filter is enabled.
Redundant database calls across DataLoader Pro and Single DataLoader execution flows were removed, including unnecessary process, job, and object lookups. Job execution now fetches only relevant in-progress records, minimizing load. These enhancements significantly reduce DB usage and prevent connection pool shutdown issues.
A fix was implemented to ensure that, when editing a DL Pro job, the child object list correctly displays all available child objects rather than only the previously selected ones. This resolves inconsistencies in object visibility during job configuration.
A fix was applied to ensure only the intended parent objects are included during job execution. The issue occurred when an object acted as both a parent and a child to the master object. The logic has been corrected to prevent additional, unintended parents from being identified and processed.
A fix was implemented to ensure that, after running a DataLoader Pro job, the application correctly redirects back to the same job. Previously, it always loaded the first job in the list. The redirect logic on the DL Pro landing page has now been corrected.
Resolved an issue where an incorrect authentication error was shown for query-related failures. The system now displays the proper error message when a connection exception occurs.
Release Date: 23 November 2025
A fix was implemented to resolve failures in nCino and Data Loader operations when Salesforce connectivity was routed through a proxy. Bulk API requests now establish connections reliably without timing out when the proxy is enabled.
A new option has been added to synchronize schema metadata directly within the Feature Migration Template. Triggering a sync refreshes the latest objects, fields, and attribute changes from Salesforce, ensuring templates remain up-to-date and reducing deployment failures caused by outdated schema definitions.
Release Date: 16 November 2025
Handling User Data
A fix was rolled out to make sure the user data such as jobs are handled properly once the user account is deleted from the Super Admin.
Handling Object Relations
A fix is provided to make sure the circular relations of objects in the buckets with multiple objects will be handled properly.
Release Date: 09 November 2025
Enhanced delta preparation logic to ensure only relevant changes from the selected revisions are included when the source is Version Control (VC). This fix resolves migration failures caused by missing .csv files during deployment.
Resolved an issue where the “Disable Validation Rules” setting was not honored during nCino CI job execution. The fix ensures that destination org details are correctly passed from the Agent to Rabbit, allowing validation rules to be accurately identified and disabled during deployment.
Resolved an issue where audit fields were incorrectly included during data migration, causing deployment failures for specific templates. The fix ensures audit fields are now processed only for objects that support them, preventing similar errors during deployment.
Resolved an issue where nCino RBC feature deployments intermittently failed with authentication errors despite valid credentials. The fix ensures record type data is properly saved during deployment, and additional loggers have been added to help trace any future occurrences.
Salesforce has deprecated the “username + password + security token” authentication method for integrations using the SOAP API starting with version 65. This legacy method will be completely disabled by Summer ’27 for API versions 31–64. Customers using this method in AutoRABIT connections (e.g., {{ConnectionName}}) must migrate to OAuth (JWT Bearer) authentication to ensure uninterrupted connectivity. The migration can be done through Connections → {{ConnectionName}} → Migrate to OAuth, followed by the on-screen steps to confirm the connection status as “OAuth (JWT)”.
Release Date: 2 November 2025
Implemented code changes to ensure parent object references in child records are correctly migrated when both parent and child objects are selected as child objects in a Data Loader Pro job.
A fix was implemented to ensure the sorting field defaults to the lookup key during feature commit creation. The sorting field now switches to “Name” only when a lookup key field does not exist, preventing duplicate lookup keys in pull request file changes.
Resolved an issue where datasets failed to load and got stuck at “Retrieving Iterations...” when the deployment label contained a “#” character. The label handling logic was updated to prevent URL truncation during dataset retrieval.
A fix was implemented to handle attachment names containing commas (,). Previously, deployments failed with an “Invalid Field” error when processing attachments with commas in their filenames.
Release Date: 19 October 2025
Optimized redundant database calls to prevent connection pool shutdown errors. This enhancement ensures stable and consistent connections during data processing, eliminating the “Connection Pool Issue” encountered by users.
Release Date: 15 October 2025
A fix has been implemented to ensure records are processed correctly in environments with Person Account–enabled orgs, preventing migration failures.
Resolved an issue where parent records were incorrectly migrated even when the Automatic Apply Filter option was selected. The system now skips parent records as intended.
Addressed an issue that prevented cloned DataLoader jobs from updating records properly. Cloned jobs now retain and update data accurately.
Implemented a UI enhancement to ensure versioning information displays correctly within the Feature Management section.
Fixed an issue that occurred during job execution when no mappings were provided. The system now handles empty or null mapping values gracefully during job editing and saving.
Introduced a safeguard to handle empty source and destination external ID conditions, preventing circular reference errors during data processing.
Release Date: 5 October 2025
Resolved an issue that caused record failures in environments with Person Account–enabled orgs. The process now supports these orgs seamlessly.
Implemented a fix to ensure that custom queries in DataLoader extractions are parsed and executed correctly, preventing query-related failures.
Addressed an issue with attachment handling in form templates to ensure smooth and reliable processing during uploads and migrations.
Introduced an automatic refresh mechanism to keep job status updates in sync, ensuring that the latest execution status is always displayed in real time.
User Management enables you to manage your account where you can add a new user, edit user roles, remove a user etc.
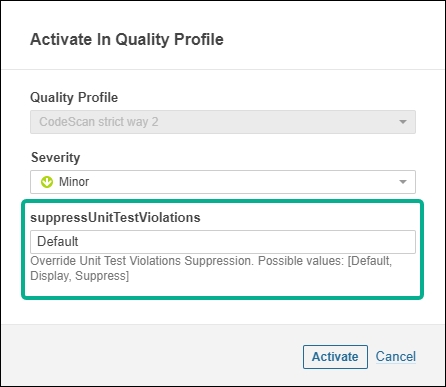
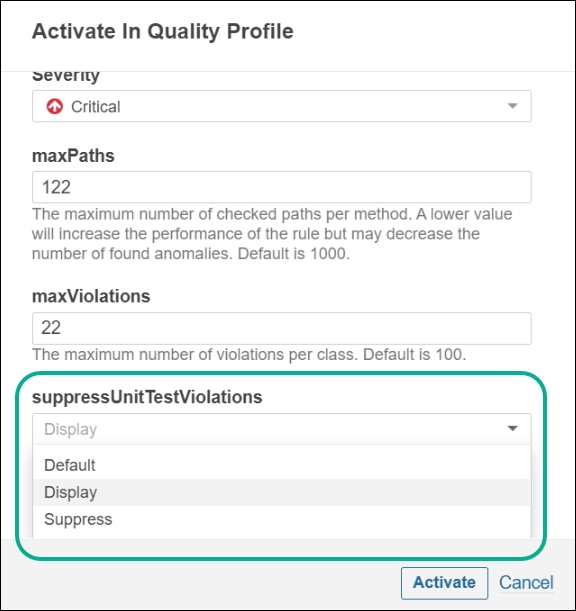
The user registration flow is now enhanced for improved user experience in the CodeScan cloud by updating several options and removing others that no longer apply.
Validate Email address- The CodeScan team to allow users to register for a new CodeScan account using corporate email addresses only.
The users who attempt to sign up using an email domain not registered with us require approval from the CodeScan team. To simplify the approval process, it is recommended that you only invite persons whose email domains already exist with us.
The existing CodeScan rule is now enhanced to verify if SOQL queries are in the loop. With this release, if a SOQL query is called in a loop in another method or class, the rule will now alert the users with information like class name, method name, and the line number of the violation.
The CodeScan IntelliJ plugin has been upgraded to the stable 6.1.4 version. This update improves the connection process with your server.
This release includes minor stability fixes and improvements for the CodeScan platform.
(CodeScan v23.0.6)
This is a maintenance release. The following items were fixed and/or added:
Fixed the following issues with the static code analysis (SCA) report observed in ARM where,
SCA report shows only ApexClass and AuraDefinitionBundle results in ARM, whereas the CodeScan app displays the accurate issues count.
Log file displays the error: Only first 10000 issues can be shown (#48644).
(CodeScan v23.0.5)
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with the Custom Metadata components must have a description field rule. The user added the description field to their quality profile's metadata and implemented the aforementioned rule, yet the problem still persists (#65227).
Fixed an issue where the master scan was failing in the CodeScan application. The multiple scan running for the same environment caused the issue. (#61134).
Fixed an issue where the rule was missing the below case when permissions are checked through a local variable instance:
{noformat}SObject objAcc;
if (objAcc != null && objAcc.getSObjectType().getDescribe().isUpdateable()) {{noformat}
This case is now added to the rule.(#).
(CodeScan v23.0.4)
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the Avoid running Soql and DML inside loops rules were not evaluating properly and throws wrong issue (#62432).
Fixed an issue with the integration of VS Code and CodeScan where, when a user clicked on the quality profile in the project information page, they were sent to a screen that read, The requested Quality Profile was not found (#63569).
(CodeScan v23.0.3)
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the \triggers and \aura folders were not scanned for full code coverage. (#62178).
Added a new column Rull Name to the CSV export report for better issue/rule identification (#53040).
Fixed an issue where the users were not receieving notification for My issues/My new issues/Issues with false positive although the notifications feature was enabled (#).
Fixed an issue where the user when initiated a manual analysis inside CodeScan, the application throws the classes/WSRS_DistributionPartnerDAEventHandler.cls error (#).
Fixed an issue whehre the unit test did not include the System.Assert() Update.
Update the input text on the SSO Login screen from "Your company email" to “Company SSO Domain”.
You'll see this when you log in to your ARM account.
Let's get to know the main areas of the ARM application.
You see a list of icons with the context in the top-right corner.
Let's examine each of these links in detail:
A Create New drop-down is available, which allows users to perform the primary and most used features in ARM, such as creating a CI job or a merge operation, etc., The users can also find the listed Create New operations within the ARM sub-module.
Hover your mouse over the Create New menu and click the drop-down icon. The drop-down field will allow the users to select a value from a predefined set of choices.
Here you can:
Find links to
Know about the ARM version on which you're logged in
ARM Feedback page
Here you can:
View your profile or update your basic information, personal email settings, etc.
Change your current password
Logout from your ARM account
On the left-hand side of the application, you see a list of icons with the context in it. These icons are nothing but the modules or features of ARM. The sub-modules which are part of it will be listed by hovering your mouse over each module.
Let's examine each of these links in detail:
The ARM Dashboards enable you to display multiple performance analytics, reporting, and other widgets on a single screen. ARM includes pre-defined widgets that can be customized and displayed on the Classic Dashboards page. These widgets are displayed as graphs, tables, and text. Each user can choose the widgets to populate their dashboard.
Version control helps you track changes you make in your code over time. Using a version control system, you can create snapshots of your code by creating branches or copies and isolating the codebase from the central repository. Every change made to the source is tracked, along with who made the change, why they made it, and references to problems fixed or enhancements introduced by the change. This makes it easier to make changes and enhances the overall quality of the code. A list of action items related to the Version Control system will get displayed, such as EZ-Commit, Merge, Manage Labels, etc.
ARM's Continuous Integration (CI) is designed to help customers rapidly release code confidently by automating the build, test, and deployment process to accomplish Continuous Delivery for Salesforce. CI encourages developers to share their code and unit tests by merging their changes into a shared version control repository upon completing every task. You can release code faster as it allows you to track application development and metadata modifications.
The Deployment process allows you to quickly and safely transfer new developments from your sandbox instance to a production instance. You can transfer validation rules, custom objects, new fields, apex codes, and many other components from your development environment to a live production environment using the deployment process.
ARM Data Loader allows you to configure your data loading operations in convenient and user-friendly GUI wizards and even allows importing and exporting Salesforce data without typing a line of code. Its powerful and easy-to-understand scheduling settings will enable you to specify almost any schedule quickly. You may schedule any data-loading operation for automatic execution.
Salesforce Developer Experience (DX) is a new set of tools that streamlines the entire development life cycle. It improves team development and collaboration, facilitates automated testing and continuous integration, and makes the release cycle more efficient and agile. It’s a new approach that supports team collaboration, focusing on predictability, quality, and standardized development life-cycle on Salesforce. Salesforce DX enables developers to build and release the latest features in a short period with minimal risk. ARM provides the best Salesforce Developer Experience with continuous integration and helps deliver software rapidly.
ARM allows its users to view all the deployment, merge, and data loader-related information carried out in the Salesforce Org in the form of reports. This information improves productivity, accountability, and insight into your business data in the form of reports.
Environment Provisioning is a unique interface ARM provides to quickly facilitate a Salesforce sandbox with metadata and data requirements that suit specific needs. These can be created as a template and stored in ARM. The same templates can be reused multiple times across various modules in ARM. For example, you can create an Environment Provisioning template to disable validation rules, enable history tracking, anonymous Apex, etc., of a particular object as a post-deployment setup.
Admin-related items are displayed here, such as registering a Salesforce Org, Version Control, adding team members, etc.
nCino-related operations will be displayed in this section, for example, creating a feature migration template, automating nCino deployments, etc.
The ARM signup and activation process has several steps — some on our end and others on yours.
Go to https://www.autorabit.com/ and log in or go directly to https://login.autorabit.com/.
Now, click on the Sign up for a Demo link. The AutoRABIT – New Registration screen appears.
Fill in the registration details, and then click Register.
Wait for an email from us. Next, we review your details to check if they comply with our policies and to set up the rest of your account. When we've completed this process and your account is activated, you will get a confirmation sent to your email address.
The ARM login screen allows you to log in to your instance.
Go to your web browser to your instance's URL (for example, https://instance.autorabit.com).
The ARM login screen appears.
Enter your login credentials (username and password), and then click on Login.
MUST contain at least 10 characters (12+ recommended)
MUST contain at least one uppercase letter (A-Z)
MUST contain at least one lowercase letter (a-z)
MUST contain at least one number (0-9)
When you are done working in ARM and wish to log out of the system, click your username in the upper right corner and click Logout. This will log you out completely from ARM, and you must log in again to access your account.
ARM only allows a username to be logged in under one session, and any additional user sessions started using the same username will be logged out of the previous session. This mechanism is for security, as ARM does not allow multiple sessions for the same username from different machines or browsers. To prevent situations like this, please do not share your login credentials (username and password) with users in your organization.
Another situation where users are automatically logged out is when the user does not perform any actions in ARM for a certain period. Configuration settings in the ARM UI control the security timeout period in ARM.
Users can have multiple tabs of ARM pages open within the same web browser (e.g., Chrome) without getting logged out of the system. For example, this is useful when working with multiple ARM pages or records without navigating away from previous pages.
If you're having trouble logging into your AutoRABIT account, here are some common causes and solutions.
The account is not created: Please check with your admin to create a new account.
The User ID and Password supplied to access the AutoRABIT account were incorrect or invalid: Try resetting the password by following the instructions .
Check if your account subscription has expired or your account is disabled: You'll see a message saying your account is disabled when you try to log in.
If you get the following error
If you requested a new password but didn't receive your reset email:
Check the spam or junk email folder in your email linked to your AutoRABIT account.
Try to reset your password again.
ARM requires you to change your password every 90 days.
Follow the instructions to reset your ARM password.
Release Date: 7 June 2024
Rule Name: “Comment All Hardcoded Values” Category: New APEX rule in CodeScan Purpose: Ensure comments are included when using hardcoded values in Apex classes Detail: Ensures any hard-coded values or strings in the code are accompanied by descriptive comments or, alternatively, use constants. This practice enhances code readability, maintainability, and will make it easier for other developers to understand the purpose of these values.
Rule Name: “Use the null coalescing operator instead of the ternary operator” Category: New APEX rule in CodeScan Purpose: CodeScan recommendation to consider replacing ternary operators (? :) for explicit null checks with the Null Coalescing operator (??) where applicable to enhance code performance and clarity. Detail: In Salesforce's Spring '24 release, the null-coalescing operator has been introduced in Apex. This rule will identify where this operator could be used but isn’t being utilized. For further information, please refer to Salesforce Release Documentation - .
Rule Name: “Avoid JavaScript Scriptlets in Aura Components and Apex Pages” Category: New Aura / Lightning / Visualforce Rule in CodeScan Purpose/Detail: JavaScript scriptlets should not be directly embedded within the markup of Aura components or Apex pages. Instead, utilize Salesforce Static resources for including JavaScript code. Using direct <script> tags in components or pages can pose a security risk, increasing the likelihood of cross-site scripting (XSS) attacks. For further information, please refer to: - - Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
Rule Name: “Exposed Lightning Message Channel” Category: New LWC / Aura / Visualforce rule in CodeScan Purpose: It is recommended to verify instances where the 'isExposed' flag in Lightning Message Channels is set to true. Setting this flag can lead to unintended access to the Lightning Message Service (LMS) API, potentially resulting in unauthorized message publishing and subscribing across components within the Salesforce ecosystem. Detail: This term specifically refers to cases where you have not configured the 'isExposed' flag in Lightning Message Channel to false. Since this provides access to the Lightning Message Service (LMS) API, which lets you publish and subscribe to messages across the DOM and between Aura, Visualforce, and Lightning Web Components, it should be set to false. For further information, please refer to:
Updated the rule “Avoid duplicate conditions in "if"/"else if" and "switch" statements to eliminate dead code." Detail: In the Initial implementation, the "if/else-if" statements and the nested "if/else-if" statements present within them were not allowed to have duplicate conditions. Now only the related "if/else-if" statements are checked for duplicate conditions, without considering the nested "if/else-if" statements present within them. Value: The same conditions can cause duplication and lead to dead code in statements such as "if"/"else if" and "switch." This issue often occurs due to a copy/paste error. In the best-case scenario, it results in dead code that serves no purpose, but in the worst-case scenario, it introduces bugs that may propagate as the code is maintained, potentially leading to unexpected behavior.
Updated the documentation and example on rule “API Version is Too Old” to: “This rule identifies visual force pages which are using older versions of the API. Change the API Version of this visual force page.” Reason for change: The description and example needed to be updated for the rule.
March 2023 - Version 22.3 (nCino)- Key Features and Enhancements
Date of release: 05 March 2023 Article last updated: 05 March 2023
With this nCino release, we've added a new option called Version Control to facilitate deployment. The users will now be able to define a starting point from which commit needs to be picked for the range of revisions to be deployed via Continuous Integration (CI) jobs. The key features are:
The user will be able to trigger builds for new revisions (delta deployments).
The user will be able to select baseline revisions as a starting point for CI jobs.
The user will be able to group all commit revisions together to run dataloader operations at once.
As a post-deployment success activity, we've provided the ability to reuse a package from a single build from a single CI job to deploy the same data in various Salesforce environments.
While using the current nCino implementation, the user must create multiple CI jobs, one for each destination org, in order to build data from the same repository and branch and deploy it to multiple salesforce environments. This results in repeated effort in building from the same source and defining the same job over and over again merely to choose a different destination, making it difficult to manage several CI jobs. With this new functionality, the user can build once and reuse it for deploying to multiple Salesforce orgs using a single build from a CI job.
The key features are:
Reduced effort in redefining the CI jobs with the same source multiple times.
Reduced time to deploy to multiple environments from the same source.
New objects, such as Schedules and Debt Schedules, were introduced with the latest nCino version release.
All of them are part of the Spreads Schedules group. To include all these objects under a single umbrella, we added a new tile called Spreads Schedules Template.
The Spreads Schedules Template template includes the following objects:
LLC_BI__Underwriting_Bundle__c
LLC_BI__Spread_Statement_Type__c
LLC_BI__Spread_Statement_Record__c
LLC_BI__Debt__c
To keep our product up to current with the most recent Salesforce upgrades, AutoRABIT supports the most recent API 57.0 version in this release. The most recent API version is aimed for customising the metadata schema and developing tools to manage it.
With Admin permissions you can download a CSV containing every user in your ARM tenant—handy for audits, license reviews, or compliance reports.
The export includes the following columns:
If you develop on the Salesforce platform, you can use ARM to:
Rapidly compare environments to see the differences
Quickly build deployment packages to get orgs in sync
Integrate version control into your development process
Set up advanced deployment automation
Track changes between environments with detailed change reports
Adopt Salesforce DX without the command line
Reduce risks with rollback and metadata backups
Improve team collaboration and reduce code conflicts
Move data records between production orgs and sandboxes
LLC_BI__Debt_Schedule__c
LLC_BI__Schedule__c
LLC_BI__Schedule_Section__c
LLC_BI__Schedule_Entry__c
Feature Management (visible only for Administrator for both SAAS and On-Premise instances)





MUST contain at least one special character (such as ! @ # $ % ^ & * < >)
MUST NOT include your email address, first, middle or last name, or commonly used passwords
MUST NOT be one of the 5 previously used passwords
Restriction of your IP address: Verify with your network team internally whether there are any issues or restrictions for your IP address from the network side.
If none of the above actions resolve the issue, contact AutoRABIT to raise a Support Ticket.




Released Date: 01 July 2021
Enhanced Reports: CodeScan's weekly reports have been improved, with more scheduling choices, insights into project issue patterns, logs of project configuration changes, and false positives logged.
Enhanced Metadata Ruleset: Before deploying from the developer environment, Salesforce metadata components can now be scanned to ensure that they have an associated description, improving the clarity around their purpose and function.
Rulesets for nCino: In this release, nCino-specific rules have been added. CodeScan can now limit the number of sharing rules, as well as active and inactive workflow rules created on an object in order to prevent performance impact due to system overload caused by extensive calculations when a record is created or updated. Users may customize these rules for their own purposes.
Improved AutoRABIT integration: CodeScan reports generated from AutoRABIT for a project or Salesforce org are now consolidated as individual branches under their respective CodeScan projects rather than in a separate new project. This allows the user to show continuity in the reports and retain history tracking, making the integration more helpful and intuitive.
Salesforce Administrators
Salesforce Administrators who want a faster, more powerful alternative to changesets that is easy to use and helps them quickly move changes without the command line
Salesforce Developers
Salesforce Developers looking for a tool that enables them to adopt modern development practices such as version control, continuous integration, and automated dependency analysis, while removing the need for the manual XML editing of Ant-based development
Release Managers
Release Managers and Technical Architects who want to improve deployment velocity, facilitate team collaboration, and deliver features to their end users quickly and reliable
Consultants and Implementation Partners
Consultants and Implementation Partners who want a way to build, track, and manage changes across multiple clients and organizations and provide detailed reports of their project progress.
September 2023 Version 23.1 – Streamlined CI/CD and Enhanced Control
We're thrilled to introduce a series of exciting enhancements to elevate your nCino experience. Get ready for:
1. Precision Deployment: Define your baseline revisions and effortlessly trigger builds for new revisions, enabling delta deployments. Package multiple commit revisions together for swift Record-Based Configuration (RBC) deployments.
2. Multi-Sandbox Mastery: Seamlessly deploy nCino CI builds to multiple target sandboxes, with the flexibility to choose up to 5 organizations per job. Say goodbye to redundant job creations for the same deployment across multiple Orgs.
3. Effortless Job Management: Our revamped CI job flow guides you directly to the ‘Job List’ page, streamlining your experience. A simple ‘Run’ button on this page empowers you to initiate jobs effortlessly.
4. Rollback Assurance: Take control of your nCino RBC deployments with our rollback feature. Capture snapshots before deployment and confidently revert your Org to its prior state if needed.
5. Access + Validation: We've renamed 'Applied Mappings' to 'External ID Mapping' for clarity. Plus, enjoy peace of mind with automated validation, ensuring your access to objects and essential external ID fields.
6. Post-Deployment Insights: Keep a finger on the pulse of post-deployment activities. The ‘Post Deploy Details' section provides consolidated updates for multiple Orgs. Dive deeper with 'View Details’ to explore Orgs and their records effortlessly.
ARM (Automated Release Management) is total automation for your Salesforce CI/CD (Continuous Integration/Continuous Delivery) pipeline. ARM delivers a unified CI/CD solution purpose-built for Salesforce. The ease of use provided by ARM makes it much easier for Salesforce administrators and developers to leverage an enterprise-class DevOps process and accelerate their journey from defining requirements to deploying code.
ARM is a cloud-based CI/CD that releases an automation suite specifically designed for Salesforce.com. ARM helps Salesforce developers, admins, analysts, and release managers automate version control, deployment, testing, data loading, and sandbox management across multiple Salesforce Orgs.
Rule Name: “Use Accessibility Attributes” Category: New Lightning Web Component Rule in CodeScan Purpose: Updating LWCs with certain attributes makes these components more accessible to users of assistive technology. Detail: Accessibility software such as screen readers interpret the elements on a webpage using the title attribute, so specifying a value for components is very important. Salesforce’s ARIA attributes allow accessibility software to gather more information on the state of the page and align with the ARIA standard. For further information, please refer to: Component Accessibility Attributes Accessible Rich Internet Applications (WAI-ARIA)
Rule Name: “nCino Inactive Workflow Rules” Category: New nCino Gold Standard Rule in CodeScan Purpose: Removing inactive, unmanaged workflow rules in a Salesforce instance allows organizations to maintain an organized workflow environment Detail: Removing inactive UNMANAGED workflow rules will streamline workflow processes, reduce confusion among users, and improve system performance. This action leads to a cleaner and more efficient Salesforce instance. Further, removing inactive UNMANAGED workflow rules helps declutter the Salesforce environment, making it easier for administrators and users to navigate and manage active workflows effectively.
Rule Name: “Utilizing Apex Unit Tests with @IsTest(IsParallel)” Category: New APEX rule in CodeScan Purpose: The annotation “@isTest(isParallel=true/false)” can be set in Apex test classes to indicate whether the particular test can be executed parallelly or sequentially (performance enhancement). Detail: When writing Apex unit tests, ensure that the @IsTest(IsParallel) annotation is set, whether true or false. This keeps the option of running tests in parallel visible through development to optimize test execution times. However, it should only be enabled in scenarios where it adds value without introducing risks or conflicts. Further information: When utilizing Apex unit tests with the annotation @IsTest(IsParallel=true), it's essential to be aware of potential drawbacks to ensure smooth execution and accurate results. Enabling parallel testing with @IsTest(IsParallel=true) may lead to UNABLE_TO_LOCK_ROW errors due to resource competition, which in turn can result in rerunning failed tests in serial mode. Additionally, it's important to note that this setting does not affect change set deployment or package upload processes. By understanding these drawbacks, developers can effectively manage test execution and deployment processes, minimizing errors, and ensuring the reliability of test results.


CodeScan 25.0.3 is comprised of the following 1 component:
Component details are listed in their corresponding sections within this document.
Enhanced rule “Use System.runAs to test user permissions” to ensure that a violation should not be thrown if the variable used is within the class scope. Historically, the CodeScan rule “Use System.runAs to test user permissions” checks for the presence of System.runAs in the test methods and that a local User variable is passed. This enhancement provides an alternative for the rule by adding a parameter to ignore checks for the variable passed to the RunAs method. The implantation of this enhancement is via a parameter which defines an execution:
*Parameter name*: checkRunAsOnly
*Parameter desc*: When true, this parameter tests only if RunAs is used in the method, not the arguments passed to it.\
Note that the parameter default is false.
We have verified that users are now able to see the violation for the following scenarios.
Release Date: 5 February 2025
CodeScan 25.0.2 is comprised of the following 4 components:
Component details are listed in their corresponding sections within this document.
Added “Security Hotspots” in CSV Export We have had a long-standing capability to export issues directly from the CodeScan user interface. However, there was not the ability to export Hotspots. With this new feature, we have added a new page in the CodeScan UI that allows users to directly export Hotspots. And, similar to exporting issues, this can be done at the branch or PR level.
Further, to make navigation clearer and easier for users, we have renamed the existing CSV export page to “CSV Issues Export”, which is separate from the new “CSV Security Hotspots Export” page. Both pages can be opened under the “More” tab (as long as the user has the proper permissions).
Finally, we verified the following scenarios:
Verified that we are able to export security hotspot issues of a selected project.
Verified that all the required fields were included in the exported CSV with correct data.
Verified that the resolutions are visible only when the status Reviewed is selected.
Enhanced rule “Avoid Classes Without Explicit Sharing" to account for interfaces Previously, CodeScan did not consider interfaces when flagging violations. As such, the rule "sf:ClassExplicitSharing" was generating a false positive when applied to interfaces, as the Sharing keyword is not allowed on interfaces in Salesforce. This issue has been remediated. We have updated the rule to exclude interfaces from its check for the Sharing keyword, ensuring accurate validation and preventing incorrect flags. We have verified the rule: "sf:ClassExplicitSharing" for the following scenarios:
Violation is not thrown if we use with/without sharing for classes.
Violation is thrown if we don’t use with/without sharing for classes.
Violation is not thrown for an interface class, not even when used with/without sharing.
Violation is thrown if we only use sharing for classes.
There are no new rules associated with this release.
Fixed issue with “Project Search” in CSV Export (within the CodeScan UI) Recently, we added a search function to the dropdown on the CSV export page to allow users to search for the name of the project they wish to export.
Several customers reported an issue when selecting a project in the new Project Search Window.
This updated fully remediates this reported issue.
Further, we have validated the CodeScan export issue is resolved via the following scenario:
Users are able to select the projects in the Project Search Window (on the CSV export page) as expected.
Fixed an issue with some users being unable to be converted to SAML when not assigned to a SAML org. Some users were receiving the following error:
This was occurring when a user who had previously been either an Auth0 user or an SQ native user was attempting to log in via SAML, but the user is not part of the SAML org. This was occurring because CodeScan had been operating under the assumption that the user had previously logged in to CodeScan at least one time previously.
This assumption, which triggered the issue, has been fully corrected with this fix.
Release Date: 29 January 2025
CodeScan 25.0.1 is comprised of the following 11 components:
Component details are listed in their corresponding sections within this document.
Added nCino module The new nCino module contains rules that scan your metadata and directly query your Salesforce org to find issues and inconsistencies with your nCino configuration. Please note, a portion of these rules are only available for projects created with CodeScan's direct Salesforce integration due to being based on a direct query to a Salesforce Org.
nCino Rules Activation Create a project analysis with the Salesforce Org that includes nCino objects. Select the nCino-specific built-in profile and run the project analysis. Users can choose the built-in nCino Quality Profile consisting of nCino-specific and nCino-goldstandard rules in Apex/Salesforce metadata, or Users can add nCino rules to the CodeScan Quality Profile. Users can extend existing profiles and activate more rules from Apex and Salesforce Metadata using the "nCino-specific" tag. Alternatively, they can add the rules directly to newly created Quality Profiles by selecting the "nCino-specific" tag from the Rules filter, then apply Bulk Change > Activate in > Choose a quality profile. To learn how to create a custom Quality Profile, see this article.
New nCino Specific Rules: The following nCino-related rules have been added to the existing Apex/Salesforce Metadata rule sets and are tagged as "nCino-specific."
Avoid Duplicates in Custom Labels: Maintaining unique labels ensures data accuracy and consistency within the nCino platform. By avoiding the creation of multiple labels with the same value, users can rely on the uniqueness of each label for categorization and analysis purposes.
Collateral Configuration Is Null: The Collateral Configuration Field on the Collateral Type object should not be null. This will reduce the likelihood of missing or incomplete Collateral information.
Duplicate LookupKeys: In the nCino Record-Based Configuration, no two records in the configuration should have duplicate LookupKeys. The LookupKey is a critical identifier for these records, and duplicates could lead to data inconsistency and errors in the system.
Enhanced rule “Avoid Untrusted/Unescaped Variables in DML Query" to account for potential SOQL injections when “queryWithBinds” is used. Historically, CodeScan has offered our “Avoid Untrusted/Unescaped Variables in DML Query” rule to inspect customer’s code and flag where there are SOQL injection possibilities. Recently, one of our customers performed a test and expected this rule to flag an issue in their code, but it did not. We determined that the rule should be enhanced for when “queryWithBinds” is used. Our engineering team utilized specifications within Salesforce documentation (specifically, Help and Training Community) to consider only the query for executed with queryWithBinds() for vulnerability check and violation, avoiding the other parameters such as: (Map, accessLevel) and Database.queryWithBinds (query, bindVariablesMap, accessLevel). Example:
Verified after the rule enhancement was engineered that users are able to see the violation for rule “Avoid Untrusted/Unescaped Variables in DML Query” as expected.
Enhanced IDE to accept email IDs that have up to 255 characters We discovered that certain users could not use the IDE as expected. The root cause was that the CodeScan plug-in was not able to fetch their valid licenses from CodeScan because these users have an email id with more than 40 chars. This enhancement now allows the CodeScan IDE plug-in to accept email IDs with up to 255 characters.
Fixed rule “Require CSRF protection on GET requests” to distinguish Visualforce page settings from Aura components Previously, this rule was flagging violations on .cmp files that are aura:component files. The guidance in the rule suggested to change the Visualforce page setting, but this is not possible on Aura components because they are not Visualforce components. This fix for the rule “Require CSRF protection on GET requests” now enables CodeScan to distinguish Visualforce page settings from Aura components.
Remote Site Settings Description Remote Site Settings should have a description of their functionality to make it easy for others to understand the purpose and functionality of the component, as it may not always be understandable from the name.
Fixed issue with CodeScan plug-ins for VS Code and IntelliJ not working after the 24.0.15 release Recently, we added a search function to the dropdown on the CSV export page to allow users to search for the name of the project they wish to export.
Fixed issue with rule “Flow DML Should Not Be Called In Loops" Recently, we observed that the rule “Flow DML Should Not Be Called In Loops" throws a null pointer exception because of access of parent node without a null check. This fix corrects the issue. We verified the fix by testing and confirming that the rule now throws a violation as expected, and, additionally, we are no longer getting the null pointer exception.
Fixed issue with tracking IDE usage in CodeScan UI Over the last few months, we have made several enhancements that allow admins to track IDE adoption and usage. However, we recently learned that the tokens associated with AutoRABIT ARM users were also being logged in the same report. This fix removes ARM users from the IDE user reports.
Email address
Login Name
Username used to sign in
Role
Highest-privilege role assigned
Job Title
Title from the user profile
Last Login Date
Timestamp of the most recent login
Created Date
Date the account was created
Created By
User who created the account
Last Modified Date
Date the account was last changed
Last Modified By
User who made the last change
Login Type
Standard (username/password) or SSO
Last Login IP
IP address recorded at last login
Last Login Lat/Long
Latitude/longitude obtained at last login
Last Login Location
City, state, and country resolved from the IP
Last Login Browser
Browser string at last login
Deactivated Date
Date the account was deactivated (if any)
Deactivated By
User who deactivated the account
In Admin › Users, click Export All Users in the upper-right corner.
In the pop-up, choose which fields to include, then click Export.
ARM generates the CSV and downloads it to your computer.
First Name
User’s first name
Last Name
User’s last name
Status
Active or Deactivated
When a teammate is on vacation or otherwise unavailable, an administrator can delegate that user’s approvals, scheduled tasks, and repository access to an active colleague. The original account is deactivated, and the delegate steps in with identical permissions.
Log in to AutoRABIT.
Hover over Admin and click Users.
Locate the user whose responsibilities you need to delegate and click Delegate.
At the bottom of the wizard, pick the delegate user from the drop-down list of active users.
Click Release User to finalize the transfer.
After delegation, you’ll find two helpful links next to the user record in Admin › Users:
Log Details – a detailed audit trail of the delegation process (successes, warnings, errors).
User Delegation Report – a summary of all tasks, approvals, and schedules now owned by the delegate.
public void noRunAs(){
// No RunAs will always violate
}public void standardRunAs(){
User newUser = new User();
System.runAs(newUser){
// RunAs User will never violate
}
}public void otherRunAs(){
System.runAs(userFactory.createTestUser()){
// RunAs given a method will violate when checkRunAsOnly parameter is false
}
}Fee Template Record Screen Section: Ensure that every Fee Template record includes a Screen Section data value. This will reduce the likelihood of missing or incomplete Fee information.
Field History Tracking Check: Field History Tracking is limited according to the features in your Salesforce org. By default, Field History Tracking can be used to track a maximum of 20 fields per object.
Null LookupKeys: In the nCino Record-Based Configuration, object records without LookupKeys will cause challenges in data management and processing.
Product Feature Record Does Not Exist: Ensure that for each nCino Product Object, there is a corresponding Product Feature record. Product Object records existing without an associated Product Feature record can lead to potential data inconsistencies.
Product Feature Sharing: Ensure each nCino Product Object record is associated with unique Product Feature records. Shared Product Feature records may lead to data inconsistencies and operational challenges.
nCino Custom Components with Duplicate Names: Avoid naming conflicts with existing Managed Package Components to minimize the risk of errors and conflicts within the system, ultimately enhancing system stability and reliability.
nCino Custom Fields with Duplicate Names: Avoid naming conflicts with existing Managed Package Fields to minimize the risk of errors and conflicts within the system, ultimately enhancing system stability and reliability.
nCino Data Integration User Configuration: The Data Integration user is authenticated for background jobs such as nightly batched updates of records. Configure this user’s Permission Sets correctly to ensure updates by the Data Integration User don't execute additional tasks.
nCino Deprecated Fields: Deprecated fields in an nCino environment are labeled with a '-D' to make the deprecation visible when configuring the environment. This rule is to identify the location when deprecated fields are used and should be addressed.
nCino Trigger Handler Framework: The Trigger Handler Framework removes logic from Triggers and enforces consistency across the platform. There are many ways to create a Trigger Framework/Factory; however, the nCino Managed Package can save users time and effort. By levering the nCino Trigger Framework, users can control the execution of triggers at runtime to simplify existing customizations and logic.
System Bypass Logic – Flows: System bypass logic is required for custom Flows. Checking for the Exclude Flows Permission Set allows the system to cease further processing of the Flow if it is found at the outset. This improves the efficiency of flow execution and reduces unnecessary processing steps.
System Bypass Logic – Triggers: System bypass logic is required for custom triggers. Checks for the Exclude Trigger Permission Set allow the system to cease further processing of the Trigger if it is found at the outset. This improves the efficiency of Trigger execution and reduces unnecessary processing steps.
System Bypass Logic - Validation Rules: System bypass logic is required for Validation Rules. Checks for the Exclude Validation Permission Set allow the system to cease further processing of the rule if it is found at the outset. This improves the efficiency of Validation Rule execution and reduces unnecessary processing steps.









The delegation wizard opens and lists everything tied to the departing user:
Salesforce Orgs registered in their name.
Version Control Repositories and branch permissions.
Any scheduled tasks or approval queues.




Component details are listed in their corresponding sections within this document.
There are no new features associated with this release.
Enhanced rule “Avoid Untrusted/Unescaped Variables in DML Query" to account for potential SOQL injections when “queryWithBinds” is used. Historically, CodeScan has offered our “Avoid Untrusted/Unescaped Variables in DML Query” rule to inspect customer’s code and flag where there are SOQL Injection possibilities. Recently, one of our customers performed a test and expected this rule to flag an issue in their code, but it did not. We determined the rule should be enhanced for when “queryWithBinds” is used. Our engineering team utilized specifications within Salesforce documentation (specifically, Help and Training Community) in order to consider only the query for executed with queryWithBinds() for vulnerability check and violation, avoiding the other parameters such as: (Map, accessLevel) . Database.queryWithBinds(query, bindVariablesMap, accessLevel) Example:
Verified after the rule enhancement was engineered that users are able to see the violation for rule “Avoid Untrusted/Unescaped Variables in DML Query” as expected.
Enhancement to our disconnected license type for self-hosted customers requiring a license with a project key embedded. CodeScan has a disconnected license type option for self-hosted license where the project key is embedded.
This feature ensures that when the license check is performed, if the project being scanned has a key that is embedded in the license, then the check will pass without needing to reach out to the license server. This is very useful for customers who are not allowed any connection to sites outside their organization, as it allows the project analysis to complete without connecting to the license server.
Recently, some customers were reporting that while the scans were completing but also throwing a timeout error. We have enhanced this feature by changing this notification to occur as a warning log instead of as an error log.
Enhanced rule “Field Level Security Vulnerabilities”: Violation message now displays the correct object instead of '{0}'.
The existing violation message was neither clear nor accurate. Instead, when the violation is flagged, the message should display the correct object instead of '{0}'.
This fix includes a more clear and accurate message associated with the violation.
New Rule for Apex: “OuterClassExplicitSharing” Enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared. This prevents accidental data exposure and enhances code maintainability and compliance with security policies.
Name: Outer Class Explicit Sharing
Key: OuterClassExplicitSharing
Type: Vulnerability
Severity: Major
Message: Class '{className}' does not have an explicit sharing rule
Tags: convention
Remediation: 5 minutes
Verified the rule: OuterClassExplicitSharing for the following scenarios:
Verified the Rule’s description, type, severity, message, tag, Remediation, Key, Name
Verified the rule is not throwing a violation if with sharing, without sharing, or inherited sharing are used.
Verified the violation is thrown if with sharing, without sharing, or inherited sharing are not used.
Fixed rule “Require CSRF protection on GET requests” to distinguish Visualforce Page settings from Aura components. Previously, this rule was flagging violations on .cmp files that are aura:component files. The guidance in the rule suggested to change the Visualforce page setting, but this is not possible on Aura components because they are not Visualforce components. This fix for the rule “Require CSRF protection on GET requests” now enables CodeScan to distinguish Visualforce Page settings from Aura components.
Fixed issue with rule “Flow DML Should Not Be Called in Loops" Recently, we observed that the rule “Flow DML Should Not Be Called in Loops" throws null pointer exception because of access of parent node without null check. This fix corrects this issue. Verified the fix by testing and confirming that the rule now throws a violation as expected, and, additionally, we are no longer getting the null pointer exception.
Fixed issue in rule for APEX “sf: {{FieldLevelSecurity}} ” {Permissions should be checked before accessing resource }. Previously, this rule was throwing violations that were false positives. This was occurring when a SOSL query having an inner query calls the related Object. The Object needs to be checked by using isAccessible() before accessing its data. As per Salesforce documentation, when checking the Access for the inner query object it allows to check by using __c, but while making inner query on related Objects it must be in plural and end with__r. This fix corrects this issue. In this enhancement, the Object is checked by using isAccessible() before accessing its data.
Verified the rule “Field Level Security Vulnerabilities” for the following scenarios:
Rule is throwing the violation if we didn’t check isAccessible for the objects used in inner query.
Rule is not throwing the violation if we checked isAccessible for the objects used in inner query.
REMINDER: In the previous release, we added support for SYSTEM_MODE in this rule. A new parameter has been added, allowing users to choose true or false to include or ignore violations related to SYSTEM_MODE.
We have verified the rule:FieldLevelSecurity for the following Sscenarios:
Rule is throwing the violation if the object is NOT checked via isAccessible for the methods used in inner query
Rule is not throwing violation if system mode value is set = “true” (and the object IS NOT checked via isAccessible for methods)
Rule is not throwing violation if system mode value is set = “false” (and the object IS checked via isAccessible for the methods)
Fixed issue with CodeScan rule to check for special characters in Page Layout Name (for example: : , ( ) ' " - & ) Recently, we added a new rule that checks for special characters used in a Page Layout name (note: Metadata API name: “Layout”). This rule will enforce naming conventions for Page Layouts, which are in line with Salesforce best practices as well as several existing customers’ standards. The aim of this new rule will help identify components for refactoring of current Page Layouts that are incorrectly named. The rule checks layout and layout-meta.xml files for file names that include: - ! @ # $ % ^ & * ? ' : ; ” + = However, we recognize that we inadvertently included hyphen (-) in this special character list. Hyphen should NOT be included because Salesforce automatically adds this special character. This fix removes hyphen in the check for special characters in Page Layout Name.
Release Date: November 13, 2024
The CodeScan On-Premises/Self Hosted Eagle 2.0 (24.1.1) edition is comprised of the following 12 components:
Component details are listed in their corresponding sections within this document.
New CodeScan rule to check for special characters in Page Layout Name (for example: : , ( ) ' " - & ) This is a new rule that checks for special characters used in a Page Layout name (note: Metadata API name: “Layout”). This rule will enforce naming conventions for Page Layouts, which are in line with Salesforce best practices as well as several existing customers’ standards. Further, this new rule will help identify components for refactoring of current Page Layouts that are incorrectly named. The rule checks layout and layout-meta.xml files for file names that include: - ! @ # $ % ^ & * ? ' : ; ” + =
Verified the rule:PageLayoutNaming for the following scenarios:
Verified the rules: Name, Key, Description, Type, Severity, Message, Tags, and Remediation.
New Rule for APEX: “IsBlankForNullChecks”
This is a new rule that leverages the built-in {{isBlank}} and {{isNotBlank}} methods instead of the {{!=}} and {{==}} operators to check for null or empty values.
This approach is especially relevant in programming environments and languages where {{IsBlank}} or equivalent methods are provided for more readable, maintainable, and less error-prone code. Using the {{IsBlank}} method for null checks improves code clarity, reduces the likelihood of bugs, and enhances maintainability compared to using the {{!=}} operator. Developers are less likely to encounter unexpected behavior due to differences in how null and empty values are handled. Additionally, built-in methods like {{IsBlank}} are optimized and tested to handle various edge cases, reducing the potential for errors compared to using the {{!=}} operator. It also makes the code easier to read and understand.
New Rule for LWC: “API Version is Too Old” This is a new rule to ensure that all LWC components are using an acceptable API version (including the most current API version). Using outdated API versions can lead to compatibility issues, missed opportunities to leverage new features, and potential security vulnerabilities. This rule aims to streamline the process of identifying and updating LWC components to the latest API version. By identifying and updating LWC components to the latest API version, developers can maintain higher code quality, reduce the risk of deprecated features, and improve the overall performance and security of the application. Verified the new LWC rule (API Version is Too Old) for these scenarios:
Enhancement to Rule for APEX: “"sf:ClassExplicitSharing” {Avoid Classes Without Explicit Sharing} In order to help enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared, CodeScan recently added a new rule to enforce sharing rules in classes. This rule helps prevent accidental data exposure and enhances code maintainability and compliance with security policies. However, there was a limitation on this rule causing customers to get violations flagged on interfaces. This was occurring because using “Sharing” as a keyword is not allowed on interfaces. As a result, these issues flagged on interfaces were false positives. This issue was addressed by updating the rule to exclude interfaces from its check for the Sharing keyword, ensuring accurate validation and preventing incorrect flags, an effective enhancement to the rule. Verified the rule:ClassExplicitSharing for the following scenarios is working as expected:
Verified that NO violation is thrown when used with/without sharing for classes.
Fixed issue in rule “sf:OptimizeParallelUnitTests” (IsParallel) This rule is designed to ensure that isParallel is present, either True or False. Previously, when a second flag was added to a test, the rule threw a violation, e.g., @IsTest(SomeFlag=True IsParallel=False). This should not throw a violation since IsParallel is specified. Instead, something like @IsTest(SomeFlag=True) should throw a violation, as IsParallel is not specified. This issue was occurring because the rule detection logic was looking for “@isTest(isParallel=true/false)” annotation being defined/set individually on its own (only), but not when used in combination with other annotations. Not being able to detect combination annotations setting was thereby causing false positive violations. Various scenarios tested outcomes for the rule BEFORE the fix was added:
Not setting “@isTest(isParallel=false)” (or true) – Violation – Correct behavior.
Setting @isTest(isParallel=false) or @isTest(isParallel=true) – No violation – Correct behavior.
Assign at least one role to every user so they can perform actions in AutoRABIT (ARM). If a user has multiple roles, the role that grants more permissions always overrides the more restrictive one.
Hover over Admin and click Roles.
Click Create Role.
Provide a Role Name and Description.
In the Permissions tab, tick the checkboxes for every capability this role should grant.
Click Save.
Enforcing Single Sign-On (SSO) guarantees that every team member authenticates through your identity provider (IdP), enhancing security and simplifying password policies. Administrators can enable or selectively override SSO as needed.
Open My Account.
In SSO Configuration, tick Disable login with AutoRABIT credentials.
Click Save.
From now on, all users must log in via SSO. Org Administrators can still sign in with either SSO or their AutoRABIT username/password—useful for IdP outages.
An Org Admin can exempt individuals (e.g., contractors) from SSO without disabling it globally.
Go to Admin › Users.
Select the user(s) you want to exempt.
Untick the Enforce SSO checkbox next to their names.
Click Save.
Yes! Login IPs can be restricted via SSO irrespective of how you are hosted (shared or dedicated tenant). These restrictions can be enforced via SSO using various providers.
Here is documentation from Okta on how to set up network zones that restrict access to registered apps: .
Likewise, here's one from Microsoft Entra SSO: .
Release Date: 6 April 2025
Enhanced Job Prioritization in Queue: The queue functionality has been enhanced to allow users to prioritize jobs effectively. Users can now rearrange jobs based on priority, and the updated job order will be saved persistently in the queue, ensuring execution follows the defined priority.
VC Code Performance Optimization: Refactored the VC code to enhance performance and efficiency, ensuring smoother execution and improved system responsiveness.
Improved Circular Reference Handling: Fixed an issue to ensure circular references are correctly identified and not ignored during processing, improving data integrity and system stability.
Source ID Column Visibility Fix: Resolved an issue where the "Source ID" column was not visible on the results screen. The column is now correctly displayed to ensure complete data visibility.
Release Date: 9 March 2025
Optimized Field Extraction: nCino introduced an enhancement that optimizes the field extraction process during data retrieval. Previously, Data Loader Pro fetched all available fields from an object during extraction, which could lead to unnecessary data processing and performance inefficiencies. Data Loader Pro now retrieves only the fields explicitly mapped by the user.
Data Loader Performance Improvement
Enhanced Object Selection: Newly identified objects during job execution are now included only if the selected child objects have Master-Detail parents apart from the master object, preventing unintended inclusion of lookup relation parents.
Database Persistence: Any newly identified objects during job execution are now saved to the database for future reference.
Improved Error Handling: If an exception occurs, the job status is now set to "Failed" instead of "No Records," ensuring accurate job execution tracking.
AutorabitExtId__c Validation: The system now verifies whether AutorabitExtId__c exists and ensures it is marked as "External Id" and "Unique," automatically setting it to true if necessary.
Release Date: 23 February 2025
Increased Unit Coverage for Data Loader & Data Loader Pro: Expanded unit test coverage to enhance efficiency in nCino & Data Loader.
Data Loader API Migration: SOAP to REST: Converted Data Loader APIs from SOAP to REST for improved performance and maintainability.
Performance Optimization: Enhanced job execution performance for faster processing.
Data Consistency Fix: Resolved an issue to ensure reliable and consistent data transfers.





Verified that a violation is thrown for layout and .layout-meta.xml files when file names include: - ! @ # $ % ^ & * ? ' : ; ” + =
Verified that NO violation is thrown for other file suffixes (other than layout and .layout-meta.xml files) when file names include: - ! @ # $ % ^ & * ? ' : ; ” + =
Verified that NO violation is thrown for layout and .layout-meta.xml files when file names do not include: - ! @ # $ % ^ & * ? ' : ; ” + =
New Rules for LWC: Added ESLint rules from @lwc/eslint-plugin-lwc Expanding the rules in our LWC set is vital to support the needs of our customers using Lightning Web Components. This new set expands our list of LWC rules significantly. This library is comprised of Salesforce’s official ESLint plugin, allowing CodeScan to analyze LWC code more effectively. Detailed documentation is available at https://github.com/salesforce/eslint-plugin-lwc|https://github.com/salesforce/eslint-plugin-lwc
Enforce wire adapters to be used with wire decorator (due to the complex parameter type).
Disallow usage of unknown wire adapters (due to the complex parameter type).
Verified the description, issue type, severity, message, tags, remediation, and parameters of the rule.
Verified that a violation is thrown if the API version used is lower than the minimum version allowed.
Verified that a violation is thrown if the API version used is higher than the maximum version allowed.
Verified that no violation is thrown when the API version is between the minimum and maximum versions allowed.
Verified that a violation is thrown when NOT used with/without sharing for classes.
Verified that NO violation is thrown for interface class even when NOT used with/without sharing.
Verified that a violation is ONLY thrown when used with sharing for classes.
Enhancement to Rule for VF: “"vf:AvoidJavaScriptScriptlets” We recognize that using direct <script> tags in components or pages can pose a security risk by increasing the likelihood of cross-site scripting (XSS) attacks. Separately, but importantly, you cannot use “includeScript” to embed an Aura Application to a Visualforce page (as the $Lightning global object is not available if put in a separate .js file as a static resource). To address this, Salesforce details how to “create a component on a Page,” advising you to add your top-level component to a page using $Lightning.createComponent(String type, Object attributes, String domLocator, function callback). Note that this function is similar to $A.createComponent(), but it includes an additional parameter, domLocator, which specifies the DOM element where you want the component inserted. Access the full documentation athttps://developer.salesforce.com/docs/atlas.en-us.lightning.meta/lightning/components_visualforce.htm. Considering both of these items together, we recognize that there was limitation on this rule where customers were getting violations flagged as false positives. This enhancement involves implementing Regex to detect the use of Lightning components within a {{<script>}} tag in Visualforce pages. The rule {{vf:AvoidJavaScriptScriptlets}} should not trigger a violation if only Lightning components are found. However, if any additional lines of non-Lightning code are detected within the script, a violation will be raised. This ensures the proper use of Lightning components while avoiding insecure or outdated practices in scriptlets.
Enhancement to ECMA Intrinsic Methods We recognize that the listed ECMA methods and their properties should be updated dynamically upon any new updates. This custom ESLint list will be maintained by CodeScan; as such, if any violation is thrown based on the ESLint Salesforce Repo, this custom ESLint library will be checked. If the latest method is available, we will not violate it, including:
Setting @isTest(OnInstall=true isParallel=False) – Violation – Incorrect behavior as isParallel is set.
Setting @isTest(SeeAllData=False isParallel=True) – Violation – Incorrect behavior as isParallel is set.
Results demonstrated that scenarios a and b were working as expected; however, in scenarios c and d, the rule was not able to understand multiple combined annotations format of @IsTest(xxx=false yyy=true) This fix corrects the issue. We have verified the Apex rule sf:OptimizeParallelUnitTests via multiple scenarios, and all are working as expected.
Fixed issue in rule for VF “vf:AvoidExternalResources” (in which the rule was checking ALL attributes for external resources, producing false positives). Previously, the rule vf:AvoidExternalResources was checking ALL attributes for external resources, which it should not do. This resulted in false positives being flagged as violations. This fix ensures that the check is limited to the “value” attribute only, to avoid false positives and ensure the rule functions as intended. As an example, the following will NOT be flagged as a violation:
<apex:includeScript value="{!$Resource.example_js}" loadOnReady="true"/> //Good: Uses a static resource.
Fixed issue in APEX rule “sf:AvoidPublicFields”, in which issues were being flagged on private classes (which are false positives)
The rule sf:AvoidPublicFields identifies when public fields are used and flags them as issues. Two of the three reasons this rule is important are:
The internal representation is exposed, and thus cannot be easily changed.
When the value is changed in an unexpected way (for example nulled), the implementation may not handle it correctly.
But these are not concerns when those public fields are on a private class.
This enhancement adds a private class validation check first and will not flag these two issues if the class is a private class.
Fixed issue in rule for APEX “sf: {{FieldLevelSecurity}}” (Permissions should be checked before accessing resource). Previously, this rule was throwing violations that were false positives. This was occurring when an SOQL query having an inner query calls the related Object. The Object needs to be checked by using isAccessible() before accessing its data. As per Salesforce documentation, when checking the Access for the inner query object, it allows to check by using __c, but while making inner query on related Objects, it must be in plural and end with __r. This fix corrects this issue. In this enhancement, the Object is checked by using isAccessible() before accessing its data. We also added support for the SYSTEM_MODE in this rule. A new parameter has been added, allowing users to choose true or false to include or ignore violations related to SYSTEM_MODE. We have verified the rule:FieldLevelSecurity for the following scenarios:
Rule throws the violation when the object is NOT checked via isAccessible for the methods used in inner query.
Rule is NOT throwing a violation if the system mode value is set = “true” (and the object IS NOT checked via isAccessible for methods).
Rule is NOT throwing a violation if the system mode value is set = “false” (and the object IS checked via isAccessible for the methods).
Fixed issue in rule “sf:FixDuplicateMethods”, in which nested statements were being flagged (which was a false positive issue).
Previously, the sf:FixDuplicateMethods rule was throwing violations for nested statements, which is not the intended behavior. The root cause was identified and fixed, and now the rule is working as designed and expected.

Static code analysis (SCA) lets you catch bugs, security risks, and “code smells” before code is compiled or deployed. This guide shows how to configure and run SCA tools in ARM so every build, commit, and deployment meets your organization’s quality standards.
Static code analysis is the process of scanning source code without executing it. Automated tools check the code against coding standards and best practices to surface:
Syntax and semantic errors
Unused variables and dead code
Potential performance issues
Security vulnerabilities
General “code smells” indicating poor design
Running SCA early and often improves code quality, maintainability, and reliability while reducing the cost of fixing issues later in the lifecycle.
ARM supports the following SCA tools:
Apex PMD
Checkmarx
CodeScan
Salesforce Scanner
Add an SCA tool to any build or continuous integration (CI) job:
Log in to ARM.
Navigate to Admin > Plugins.
In Static Code Analysis, select the tool you want to enable for builds or CI jobs.
Apex PMD ships with a comprehensive default rule set, but you can supply your own:
Click the Edit icon next to Apex PMD.
Under Choose file, upload a custom ruleset XML.
To start from the defaults, click the Download icon, edit the XML locally, then re-upload it.
Click the Edit icon next to Checkmarx.
Enter:
CxServer – Checkmarx server URL (e.g., http://server-name).
Prerequisites
CodeScan security token – generate under My Account > Security in CodeScan.
Organization key – shown in the upper-right corner of your CodeScan organization page.
Steps
Click the Edit icon next to CodeScan.
Enter the host URL:
https://app.codescan.io/ (US)
Excluding a file in ARM + CodeScan
Go to Admin > My Account > Plugins > Static Code Analysis.
Click Edit for CodeScan.
Use Source File Exclusion to list files you want to skip.
Click Save, then rerun the analysis.
Select CodeScan Project & Branch
Users begin by selecting a CodeScan project from a dropdown list.
Available branches are automatically fetched from CodeScan, allowing users to select a default branch for analysis.
Next, users select their ARM repositories and Salesforce orgs — automatically fetched from ARM’s registered resources.
These repositories or orgs are then mapped to the chosen CodeScan project and branch, establishing the link between the source (ARM) and the analysis destination (CodeScan).
Optional Setup Behavior
The configuration is not mandatory. only optional.
If skipped, ARM follows the normal scanning process—scans will run in the default CodeScan project/branch setup.
Once mappings are configured, all future scans will run in the specified project/branch instead of creating new ones.
Salesforce Scanner combines several static analyzers under one ruleset.
Optional custom rules
Create files with the exact names:
pmdconfig.xml
.eslintrc.json
tsconfig.json
Steps
Select the Salesforce Scanner checkbox.
For extra configuration:
Click Edit.
Use
Prerequisites
SonarQube security token – create under User > My Account > Security.
Organization key – view under My Account > Organizations.
Steps
Click the Edit icon next to SonarQube.
Enter the host URL (e.g., https://sonarcloud.io).
Choose host type (cloud or on-premises). If cloud, enter the Organization key.
You can enforce pass/fail thresholds for SCA across CI jobs, deployments, and gated commits.
Go to Admin > My Account > Validation Criteria – Static Code Analysis.
Select Enable Validation Criteria – SCA.
For each tool, define priority/severity thresholds (e.g., Apex PMD priorities 1–5). Use + to add multiple thresholds.
To include SCA in a CI job:
In the Build section, select Run Static Analysis Report.
Choose an SCA tool.
Complete any tool-specific fields.
Apex PMD and Salesforce Scanner
Run On All Supported Metadata Types – scans all metadata listed below.
Apex PMD: Apex Classes, Apex Triggers, Apex Pages, AuraDefinitionBundle, LightningComponentBundle
Checkmarx
Run On All Apex Classes, Triggers, Apex Pages & AuraDefinitionBundles – scans supported metadata.
Criteria rules for the stable build – set thresholds as above.
CodeScan and SonarQube
Run On All Supported Metadata Types – scans everything in the branch (merge) or commit (pre-validation).
Run On Newly Added Supported Metadata Types – scans only new/changed items.
Run On All Supported Metadata Types from the full source – scans the entire branch in CI jobs.
Mark Build As Unstable If Doesn't Meet Below Criteria – fail if thresholds aren’t met.
ARM also enforces SCA during EZ-Commits.
Go to Admin > My Account > Commit Validation – Approval Settings.
Select Enable criteria-based review process.
Check Should pass validation criteria for Static Code Analysis and choose one or more tools.
On the Deployment Settings screen you can enable an SCA tool before deployment starts.
ARM stores SCA source content for 90 days and deletes it afterward. PMD reports younger than 90 days omit source files from the report.
Supported metadata
Apex PMD, Checkmarx, SonarQube: Apex Classes, Apex Triggers, Apex Pages, AuraDefinitionBundle, LightningComponentBundle
CodeScan: everything above plus CustomObjects, Flow, PermissionSets
Select Stop deployment if build doesn't meet global criteria to block deployment until thresholds pass. Use SCA Mail Notifications to alert recipients.
Choose an SCA tool during a pre-validation merge.
Run Static Code Analysis – enabled by default if SCA criteria are set globally.
All supported metadata – scans the whole target branch during an EZ-Merge, or only commit files during an EZ-Commit.
Timeouts
ARM waits up to 5 hours for any SCA tool to finish.
A merge label stays valid for 7 days; related SCA reports expire at the same time.
Release: 01 August 2021
nCino Template Sync: Now that Vault is linked to nCino, whenever the nCino team changes or releases a template, Vault's will be updated as well.
AutoRABIT’s help desk access via Vault had certain issues that have been rectified. Now you can see all of your support tickets when you access the helpdesk via Vault.
The combination of full and incremental was not picking up all metadata for restore. This has now been rectified and is working as it should.
Due to a certificate issue, SSO for Azure Blob storage was not working. This has been resolved. SSO now functions as intended.
Release: 06 June 2021
Pre Restore/ Replicate Checklist: Now you can achieve improved governance for restore/ replicate jobs by following a set of guidelines to maximize the success rate.
UI Improvement: With this release, you will see all the jobs on a single summary page. The In-Progress tab under Backup, Restore, Replicate, Archival, GDPR module has been deprecated.
Vault now provides a capability to download backed-up metadata files for the on-premise offering
Field level restores fix for On-Premise offering: The field level restore showed peculiar behavior for on-prem hosting this issue was identified and fixed. Now you can successfully restore at field level for the on-prem offering.
Backup member count for Dashboard, Reports, and EmailTemplate: There was an issue identified on backup count mismatch for incremental backups for metadata (Dashboard, Reports, and EmailTemplate). This is issue has been fixed, now you can see the exact count of the metadata that got changed and picked up in an incremental backup.
Release: 26 April 2021
For our customers in regulated industries with extended needs to meet compliance and security auditing standards – Now Vault is fully available for on-premises or in-your-cloud deployment and use of on-premises storage (including SANs). These new deployment and storage options give you complete control of the environment where Vault is deployed and your data sets are stored.
On-premises or “in-your-cloud” deployment
Now Vault can be deployed where you need it to be. You can choose our AutoRABIT hosted and managed SaaS deployment within your premises or at a cloud location (Private or Public Cloud). Contact your sales representative if your organization would like to pursue this.
On-premises storage from your AutoRABIT-hosted Vault
We now support on-premises as well as cloud storage. Host your backups and archives within your premises, DR sites, or cloud environments. And get all the control you need to meet regulated industries' extended security, compliance, and risk reduction needs.
Continued updates to the UI
We’ve continued updates that we started in the UI with our March release. Again – there are no changes to where you’ll find content in the UI – just our updated look and feel with fonts, colors, buttons, and more.
Email notifications with job status in the subject line
Until now, when you received a Vault job status notification from us, you had to read the body of the email to find out what it would refer to. Now you’ll be able to quickly read the status line and select those that most need your attention for immediate reading.
Some button naming changes: Full Restore to EZ Restore – Full Replicate to EZ Replicate
EZ Restore (formerly Full Restore) enables restoration from a backup of all content from a selected backup. No functionality changes.
EZ Replicate (formerly Full Replicate) simplifies all the content from a backup set with just a few clicks. Again, no functionality changes.
Support for additional FinancialForce Metadata types
We’ve added support for some previously unsupported FinancialForce metadata types – (Layout, QuickAction, CustomObject, DuplicateRule).
Release: 25 March 2021
The first thing you’ll notice with this new release is our updated look and feel. All your familiar tools and features are available with updated fonts, colors, and logos. We hope you’ll like it.
Elsewhere you’ll find new capabilities for using Google Cloud Platform (GCP) storage, enhanced support for Azure retention policies, and restore/replication functionality for non-required parents.
Google Cloud Platform (GCP) storage support for Vault
You can now use GCP storage for backups. Options available are to use either AutoRABIT’s hosted storage on GCP or your own GCP storage environment.
Application Rebranding
Here’s a quick look at the product's updated UI and branding changes. Again – there are no changes to where you’ll find content in the UI (except for the new features below) – just our updated look and feel:
Login/ Logout screens
Logos
Application fonts
Application colors
Restore/Replicate parents with relationship lookups
We’ve now added the capability to restore or replicate any non-required parents. To do this, select them from the schema before running a restore/replicate job.
Retention policy enhancements for Azure
With our January release, we added the capability to configure the Azure Blob Retention Policy for Azure-hosted backups from within the Vault UI to meet your retention requirements.
We’ve now enhanced this feature with the capability to define retention periods in previously existing Azure Blob-hosted backups or archives to start using retention periods. Keep in mind that once you’ve applied a retention policy, your backups will no longer be available after the retention period has expired.
August 29, 2024
CodeScan Self Hosted 24.1.0 is comprised of the following 8 components:
4
2
1
Component details are listed in their corresponding sections within this document.
Feature Enhancement: The “sf.testfile” parameter in project settings UI Summary: Previously, customers using our Git integration could store their test coverage in their repo branches by using a parameter called sf.testfile (which allows people to add coverage to their code with SFDX JSON outputs) With this enhancement, CodeScan now allows for the parameter to be configured (at the project or instance level) within the UI (in General Settings ->CodeScan section).
Adding this parameter will allow teams that work like this to view the coverage on the CodeScan dashboard. The addition of this parameter notably provides more value for SFDX workflows.
Further details are within the following article:
Enhancement to rule: “Use the null coalescing operator instead of ternary” The original aim of this rule is to identify ternary statements and suggest the potential use of "??" operator. Previously, CodeScan was checking for ternary statements only. This rule was originally developed according to common development practices in Salesforce where most usages would be in ternary. However, it can be applied in scenarios involving if-else and return statements. As such, we have adjusted the rule to account for these use cases. With this enhancement, CodeScan suggests where null coalescing could be used instead of an “if” block (recognizing that if a developer is already thinking about shortening their code with ternary, then they are likely to be considering null coalescing operator as well).
Enhancement to rule: “Validation Rule Must Reference Product” This existing CodeScan rule was enhanced to be compatible with SFDX. Please note that this rule update is part of a larger initiative where we are making “validationRules of CustomObject” Compatible with SFDX. All Metadata rules need to be checked that they support both metadata API and SFDX formats of the issue they were built to find. Metadata pulled with SFDX has a different structure than Metadata pulled with Salesforce’s Metadata API. CodeScan can scan this different structure with some additions to the sf-meta suffixes. However, we need to make sure that the differences are covered within the types of metadata that have these differences. For example, the Object metadata contains all field metadata when pulled from the metadata API. When this is pulled with SFDX, the object and field metadata are separate. See the following SF article for details of these differences:
New Rule for “Cognitive Complexity” in CodeScan This is a new rule for assessing Cognitive Complexity. This rule aims to enhance the understanding of code readability and maintainability by identifying areas where the cognitive load on developers may be high. Hypothesis: By introducing a new rule for Cognitive Complexity assessment in CodeScan, we expect to pinpoint specific code structures and circumstances that contribute to increased cognitive load. This will enable developers to refactor complex sections of code, leading to improved code quality, readability, and maintainability. Basic criteria and methodology: A Cognitive Complexity score is assessed according to three basic rules:
# Ignore structures that allow multiple statements to be readably shorthanded into one
# Increment (add one) for each break in the linear flow of the code
Fixed issue in rule “sf:AvoidSoqlInLoops” This CodeScan rule was found to have 2 issues:
SOQL in the code does not appear to be in a loop, but CodeScan is flagging as a violation
A violation message is displayed multiple times for the perceived detected violation
The root causes of these issues were identified, and the following enhancements were added:
Top of Form
Added condition to check if the method call is matching to the Method name; if not, do not flag as a violationBottom of Form
Top of Form
· When checking the nested method call, if method name matches, only then it will throw violation.
· Bottom of Form
Top of Form
· Avoid false positive when a recursive call happens without matching to the method name
We are excited to announce that CodeScan now supports SonarQube versions 10.4, 10.5 and 10.6. In order for the Self-Hosted plug-in to function properly, the following configuration settings are introduced. They are:
· sonar.lang.patterns.sf (Replacement for sf.apex.suffixes)
· sonar.lang.patterns.sfmeta (Replacement for sf.sfmeta.suffixes)
· sonar.lang.patterns.vf (Replacement for sf.vf.suffixes)
These properties have the same defaults as those of the existing ones. These properties offer more control than the previous ones as they support wildcards. To learn more about wildcards, refer to the Wildcards section in
Team Name – your project’s team name.
Select Credential – choose or create credentials (see Create User’s Credentials).
Click Test Connection.
Click Save.
Click Save again on My Account.
https://app-eu.codescan.io/ (EU)https://app-aus.codescan.io/ (AUS)
Choose host type (cloud or on-premises).
Select or create credentials (use the token in the Password field).
Enter the Organization key (cloud only).
Click Test Connection, then Save (twice).
Users can review, confirm, or override any mapping if required.
Click Save.
Click Save again on My Account.
Click Test Connection, then Save.
Click Save again on My Account.
Salesforce Scanner: all of the above plus CustomObject, Flow, Profile, PermissionSet, Settings, SharingRules, Workflow, StaticResource
Run On Newly Added Supported Metadata Types – scans only new or changed metadata.
Mark Build As Unstable If Doesn't Meet Below Criteria – fail the build if thresholds aren’t met.
Optional:
Auto reject commit process if the criteria are not met – reject automatically.
Auto-approve on commit validation – approve when thresholds pass.
Auto-commit on approval – commit immediately after approval.
ProfilesSettingsSharingRulesWorkflows













Enhancement to rule “Misuse of Assert Class” This CodeScan rule was introduced in Self-Hosted version 24.0.8. It is comprised of several parameters. This enhancement ensures that a newly created instance is never null. With the fix, a violation is now thrown at the line in bold. Example: public class nullCheck { public void checkOtherClassInstance() { Assert.isNull(new OtherClass()); } } (where the parameter associated with this enhancement is nullCheck)
# Increment when flow-breaking structures are nested Additionally, a complexity score is made up of four different types of increments:
# Nesting - assessed for nesting control flow structures inside each other
# Structural - assessed on control flow structures that are subject to a nesting increment, and that increase the nesting count
# Fundamental - assessed on statements not subject to a nesting increment
# Hybrid - assessed on control flow structures that are not subject to a nesting increment, but which do increase the nesting count
New Rule for APEX: “Avoid Classes Without Explicit Sharing” New Rule to Enforce Sharing Rules in Classes Summary: Enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared. This prevents accidental data exposure and enhances code maintainability and compliance with security policies.




The CodeScan On-Premises/Self-Hosted Tiger 2.0 (24.0.13) is comprised of the following nine components:
Component details are listed in their corresponding sections within this document.
New CodeScan rule to check for special characters in Page Layout Name (for example: : , ( ) ' " - & ) This is a new rule that checks for special characters used in a Page Layout name (note: Metadata API name: “Layout”). This rule will enforce naming conventions for Page Layouts, which are in line with Salesforce best practices as well as several of existing customers’ standards. Further, this new rule will help identify components for refactoring of current Page Layouts that are incorrectly named. The rule checks layout and layout-meta.xml files for file names that include: - ! @ # $ % ^ & * ? ' : ; ” + =
Verified the rule:PageLayoutNaming for the following scenarios:
Verified the rules: Name, Key, Description, Type, Severity, Message, Tags, and Remediation.
Verified that a violation is thrown for layout and .layout-meta.xml files when file names include: - ! @ # $ % ^ & * ? ' : ; ” + =
Verified that NO violation is thrown for other file suffixes (other than layout and .layout-meta.xml files) when file names include: - ! @ # $ % ^ & * ? ' : ; ” + =
Verified that NO violation is thrown for layout and .layout-meta.xml files when file names do not include: - ! @ # $ % ^ & * ? ' : ; ” + =
New Rules for LWC: Added ESLint rules from @lwc/eslint-plugin-lwc Expanding the rules in our LWC set is vital to support the needs of our customers using Lightning Web Components. This new set expands our list of LWC rules significantly. This library is comprised of Salesforce’s official ESLint plugin, allowing CodeScan to analyze LWC code more effectively. Detailed documentation is available at
New Rule for LWC: “API Version is Too Old” This is a new rule to ensure that all LWC components are using an acceptable API version (including the most current API version). Using outdated API versions can lead to compatibility issues, missed opportunities to leverage new features, and potential security vulnerabilities. This rule aims to streamline the process of identifying and updating LWC components to the latest API version. By identifying and updating LWC components to the latest API version, developers can maintain higher code quality, reduce the risk of deprecated features, and improve the overall performance and security of the application. Verified the new LWC rule (API Version is Too Old) for these scenarios:
Verified the description, issue type, severity, message, tags, remediation, and parameters of the rule.
Verified that a violation is thrown if the API version used is lower than the minimum version allowed.
Verified that a violation is thrown if the API version used is higher than the maximum version allowed.
Verified that no violation is thrown when the API version is between the minimum and maximum versions allowed.
Enhancement to Rule for APEX: “"sf:ClassExplicitSharing” {Avoid Classes Without Explicit Sharing} In order to help enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared, CodeScan recently added a new rule to enforce sharing rules in classes. This rule helps prevent accidental data exposure and enhances code maintainability and compliance with security policies. However, there was a limitation on this rule causing customers to get violations flagged on interfaces. This was occurring because using “Sharing” as a keyword is not allowed on interfaces. As a result, these issues flagged on interfaces were false positives. This issue was addressed by updating the rule to exclude interfaces from its check for the Sharing keyword, ensuring accurate validation and preventing incorrect flags, an effective enhancement to the rule. Verified the rule:ClassExplicitSharing for the following scenarios is working as expected:
Verified that NO violation is thrown when used with/without sharing for classes.
Verified that a violation is thrown when NOT used with/without sharing for classes.
Verified that NO violation is thrown for interface class even when NOT used with/without sharing.
Verified that a violation is ONLY thrown when used with sharing for classes.
Enhancement to Rule for VF: “"vf:AvoidJavaScriptScriptlets” We recognize that using direct <script> tags in components or pages can pose a security risk by increasing the likelihood of cross-site scripting (XSS) attacks. Separately, but importantly, you cannot use “includeScript” to embed an Aura Application to a Visualforce page (as the $Lightning global object is not available if put in a separate .js file as a static resource). To address this, Salesforce details how to “create a component on a Page,” advising you to add your top-level component to a page using $Lightning.createComponent(String type, Object attributes, String domLocator, function callback). Note that this function is similar to $A.createComponent(), but it includes an additional parameter, domLocator, which specifies the DOM element where you want the component inserted. Access the full documentation at. Considering both of these items together, we recognize that there was limitation on this rule where customers were getting violations flagged as false positives. This enhancement involves implementing Regex to detect the use of Lightning components within a {{<script>}} tag in Visualforce pages. The rule {{vf:AvoidJavaScriptScriptlets}} should not trigger a violation if only Lightning components are found. However, if any additional lines of non-Lightning code are detected within the script, a violation will be raised. This ensures the proper use of Lightning components while avoiding insecure or outdated practices in scriptlets.
Enhancement to ECMA Intrinsic methods We recognize that the listed ECMA methods and their properties should be updated dynamically upon any new updates. This custom ESLint list will be maintained by CodeScan; as such, if any violation is thrown based on the ESLint Salesforce Repo, this custom ESLint library will be checked. If the latest method is available, we will not violate it, including:
Fixed issue in rule “sf:OptimizeParallelUnitTests” (IsParallel) This rule is designed to ensure that isParallel is present, either True or False. Previously, when a second flag was added to a test, the rule threw a violation, e.g., @IsTest(SomeFlag=True IsParallel=False). This should not throw a violation since IsParallel is specified. Instead, something like @IsTest(SomeFlag=True) should throw a violation, as IsParallel is not specified. This issue was occurring because the rule detection logic was looking for “@isTest(isParallel=true/false)” annotation being defined/set individually on its own (only), but not when used in combination with other annotations. Not being able to detect combination annotations setting was thereby causing false positive violations. Various scenarios tested outcomes for the rule BEFORE the fix was added:
Not setting “@isTest(isParallel=false)” (or true) – Violation – Correct behavior.
Setting @isTest(isParallel=false) or @isTest(isParallel=true) – No violation – Correct behavior.
Setting @isTest(OnInstall=true isParallel=False) – Violation – Incorrect behavior as isParallel is set.
Setting @isTest(SeeAllData=False isParallel=True) – Violation – Incorrect behavior as isParallel is set.
Results demonstrated that scenarios a and b were working as expected; however, in scenarios c and d, the rule was not able to understand multiple combined annotations format of @IsTest(xxx=false yyy=true) This fix corrects this issue. We have verified the Apex rule sf:OptimizeParallelUnitTests via multiple scenarios, and all are working as expected.
Fixed issue in rule for VF “vf:AvoidExternalResources” (in which the rule was checking ALL attributes for external resources, producing false positives). Previously, the rule vf:AvoidExternalResources” was checking ALL attributes for external resources, which it should not do. This was resulting in false positives being flagged as violations. This fix ensures that the check is limited to the “value” attribute only, to avoid false positives and ensure the rule functions as intended. As an example, the following will NOT be flagged as a violation:
<apex:includeScript value="{!$Resource.example_js}" loadOnReady="true"/> //Good: Uses a static resource.
Fixed issue in rule for APEX “sf: {{FieldLevelSecurity}}” (Permissions should be checked before accessing resource). Previously, this rule was throwing violations that were false positives. This was occurring when a SOQL query having an inner query calls the related Object. The Object needs to be checked by using isAccessible() before accessing its data. As per Salesforce documentation, when checking the Access for the inner query object it allows to check by using __c, but while making inner query on related Objects it must be in plural and end with__r. This fix corrects this issue. In this enhancement, the Object is checked by using isAccessible() before accessing its data. We also added support for the SYSTEM_MODE in this rule. A new parameter has been added, allowing users to choose true or false to include or ignore violations related to SYSTEM_MODE. We have verified the rule:FieldLevelSecurity for the following scenarios:
Rule throws the violation when the object is NOT checked via isAccessible for the methods used in inner query.
Component details are listed in their corresponding sections within this document.
1. Feature Enhancement: The “sf.testfile” parameter in project settings UI
Summary: Previously, customers using our Git integration could store their test coverage in their repo branches by using a parameter called sf.testfile (which allows people to add coverage to their code with SFDX JSON outputs).
With this enhancement, CodeScan now allows for the parameter to be configurable at a project level. The addition of this parameter will allow teams that work like this to view the coverage on the CodeScan dashboard. The addition of this parameter notably provides more value for SFDX workflows.
Further details are within the following article: https://knowledgebase.autorabit.com/product-guides/codescan/codescan-integration/codescan-sfdx-plugin/importing-code-coverage-from-sfdx-projects|https://knowledgebase.autorabit.com/product-guides/codescan/codescan-integration/codescan-sfdx-plugin/importing-code-coverage-from-sfdx-projects|smart-link
2. Enhancement to rule “Use the null coalescing operator instead of ternary”
The original aim of this rule is to identify ternary statements and suggest potential use of "??" operator. Previously, CodeScan was checking for ternary statements only.
This rule was originally developed according to common development practices in Salesforce where most usages of this would be in ternary. However, it can be applied in scenarios involving if-else and return statements. As such, we have adjusted the rule to account for these use cases. With this enhancement, CodeScan suggests where null coalescing could be used instead of an “if” block (recognizing that if a developer is already thinking about shortening their code with ternary, then they are likely to be considering null coalescing operator as well).
3. Enhancement to rule: “Validation Rule Must Reference Product”
This existing CodeScan rule was enhanced to be compatible with SFDX.
Please note that this rule update is part of a larger initiative where we are making “validationRules of CustomObject” Compatible with SFDX
All Metadata rules need to be checked that they support both metadata api and sfdx formats of the issue they were built to find.
Metadata pulled with SFDX has a different structure than Metadata pulled with Salesforce’s Metadata API. CodeScan can scan this different structure with some additions to the sf-meta suffixes. However, we need to make sure that the differences are covered within the types of metadata that have these differences. For example, the Object metadata contains all field metadata when pulled from the metadata API. When this is pulled with SFDX, the object and field metadata is separate.
See the following SF article for details of these differences:https://developer.salesforce.com/docs/atlas.en-us.sfdx_dev.meta/sfdx_dev/sfdx_dev_source_file_format.htm|https://developer.salesforce.com/docs/atlas.en-us.sfdx_dev.meta/sfdx_dev/sfdx_dev_source_file_format.htm|smart-link
NOTE: This rule is only applicable to nCino customers
4. Enhancement to rule “Misuse of Assert Class”
This CodeScan rule was introduced in Self Hosted version 24.0.8. It is comprised of several parameters. This enhancement ensures that a newly created instance is never null.
With the fix, a violation is now thrown at the line in bold.
Example: public class nullCheck { public void checkOtherClassInstance() { Assert.isNull(new OtherClass()); } class OtherClass { public void doSomething() { System.debug('Doing something in OtherClass'); } } }
(where the parameter associated with this enhancement is nullCheck)
New Rule for “Cognitive Complexity” in CodeScan This is a new rule for assessing Cognitive Complexity. Note that we had a previous Cognitive Complexity rule. What’s different is that this rule aims to enhance the understanding of code readability and maintainability by identifying areas where the cognitive load on developers may be high. Hypothesis: By introducing a new rule for Cognitive Complexity assessment in CodeScan, we expect to pinpoint specific code structures and circumstances that contribute to increased cognitive load. This will enable developers to refactor complex sections of code, leading to improved code quality, readability, and maintainability. Basic criteria and methodology: A Cognitive Complexity score is assessed according to three basic rules:
# Ignore structures that allow multiple statements to be readably shorthanded into one
# Increment (add one) for each break in the linear flow of the code
# Increment when flow-breaking structures are nested Additionally, a complexity score is made up of four different types of increments:
# Nesting - assessed for nesting control flow structures inside each other
# Structural - assessed on control flow structures that are subject to a nesting increment, and that increase the nesting count
# Fundamental - assessed on statements not subject to a nesting increment
New Rule for APEX: “Avoid Classes Without Explicit Sharing” New Rule to Enforce Sharing Rules in Classes Summary: Enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared. This prevents accidental data exposure and enhances code maintainability and compliance with security policies.
New Rule for APEX: “IsBlankForNullChecks” This is a new rule that leverages the built-in {{isBlank}} and {{isNotBlank}} methods instead of the {{!=}} and {{==}} operators to check for null or empty values. This approach is especially relevant in programming environments and languages where {{IsBlank}} or equivalent methods are provided for more readable, maintainable, and less error-prone code. Using the {{IsBlank}} method for null checks improves code clarity, reduces the likelihood of bugs, and enhances maintainability compared to using the {{!=}} operator. Developers are less likely to encounter unexpected behavior due to differences in how null and empty values are handled. Additionally, built-in methods like {{IsBlank}} are optimized and tested to handle various edge cases, reducing the potential for errors compared to using the {{!=}} operator. It also makes the code easier to read and understand.
Fixed issue in rule “sf:AvoidSoqlInLoops” This CodeScan rule was found to have 2 issues:
SOQL in the code does not appear to be in a loop, but CodeScan is flagging as a violation
A violation message is displayed multiple times for the perceived detected violation
The root causes of these issues were identified, and the following enhancements were added:
Top of Form
Added condition to check if the method call is matching to the Method name; if not, do not flag as a violationBottom of Form Top of Form
When checking the nested method call, if the method name matches, only then will it throw a violation.
Bottom of Form
Top of Form
Avoid false positives when a recursive call happens without matching the method name.
Fixed issue in rule “sf:AvoidPublicFields”, where issues being flagged on private classes(which are false positives). The rule sf:AvoidPublicFields identifies when public fields are used, and flags them as issues. Two of the three reasons this rule is important are:
The internal representation is exposed, and thus cannot be easily changed
When the value is changed in an unexpected way (for example nulled), the implementation may not handle it correctly
But these are not concerns when those public fields are on a private class. This enhancement adds a private class validation check first, and will not flag the 2 aforementioned issues if the class is a private class.
Fixed issue in rule “sf:FixDuplicateMethods”, where Nested statements were being flagged (which was a false positive issue). Previously, the sf:FixDuplicateMethods rule was throwing violations for nested statements, which is not the intended behavior. Root cause was identified and fixed, and now the rule is working as designed and expected.
Release Date: 26 February 2025
CodeScan Self-Hosted—versions 25.0.1 (Tiger v3) and 25.1.0 (Eagle v3)—are comprised of the following eight components:
Component details are listed in their corresponding sections within this document.
There are no new features associated with this release.
Enhanced rule “Avoid Untrusted/Unescaped Variables in DML Query" to account for potential SOQL injections when “queryWithBinds” is used. Historically, CodeScan has offered our “Avoid Untrusted/Unescaped Variables in DML Query” rule to inspect customer’s code and flag where there are SOQL Injection possibilities. Recently, one of our customers performed a test and expected this rule to flag an issue in their code, but it did not. We determined the rule should be enhanced for when “queryWithBinds” is used. Our engineering team utilized specifications within Salesforce documentation (specifically, ) in order to consider only the query for executed with queryWithBinds() for vulnerability check and violation, avoiding the other parameters such as: (Map, accessLevel) . Database.queryWithBinds(query, bindVariablesMap, accessLevel) Example:
Verified after the rule enhancement was engineered that users are able to see the violation for rule “Avoid Untrusted/Unescaped Variables in DML Query” as expected.
New Rule for Apex: “OuterClassExplicitSharing” Enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared. This prevents accidental data exposure and enhances code maintainability and compliance with security policies.
Name: Outer Class Explicit Sharing
Key: OuterClassExplicitSharing
Verified the rule: OuterClassExplicitSharing for the following scenarios:
Verified the Rule’s description, type, severity, message, tag, Remediation, Key, Name
Verified the rule is not throwing a violation if with sharing, without sharing, or inherited sharing are used.
Verified the violation is thrown if with sharing, without sharing, or inherited sharing are not used.
Fixed rule “Require CSRF protection on GET requests” to distinguish Visualforce Page settings from Aura components. Previously, this rule was flagging violations on .cmp files that are aura:component files. The guidance in the rule suggested to change the Visualforce page setting, but this is not possible on Aura components because they are not Visualforce components. This fix for the rule “Require CSRF protection on GET requests” now enables CodeScan to distinguish Visualforce Page settings from Aura components.
Fixed issue with rule “Flow DML Should Not Be Called in Loops" Recently, we observed that the rule “Flow DML Should Not Be Called in Loops" throws null pointer exception because of access of parent node without null check. This fix corrects this issue. Verified the fix by testing and confirming that the rule now throws a violation as expected, and, additionally, we are no longer getting the null pointer exception.
Fixed issue in rule for APEX “sf: {{FieldLevelSecurity}} ” {Permissions should be checked before accessing resource }. Previously, this rule was throwing violations that were false positives. This was occurring when a SOSL query having an inner query calls the related Object. The Object needs to be checked by using isAccessible() before accessing its data. As per Salesforce documentation, when checking the Access for the inner query object it allows to check by using __c, but while making inner query on related Objects it must be in plural and end with__r. This fix corrects this issue. In this enhancement, the Object is checked by using isAccessible() before accessing its data.
Verified the rule “Field Level Security Vulnerabilities” for the following scenarios:
Rule is throwing the violation if we didn’t check isAccessible for the objects used in inner query.
Rule is not throwing the violation if we checked isAccessible for the objects used in inner query.
REMINDER: In the previous release, we added support for SYSTEM_MODE in this rule. A new parameter has been added, allowing users to choose true or false to include or ignore violations related to SYSTEM_MODE.
Fixed issue with CodeScan rule to check for special characters in Page Layout Name (for example: : , ( ) ' " - & ) Recently, we added a new rule that checks for special characters used in a Page Layout name (note: Metadata API name: “Layout”). This rule will enforce naming conventions for Page Layouts, which are in line with Salesforce best practices as well as several existing customers’ standards. The aim of this new rule will help identify components for refactoring of current Page Layouts that are incorrectly named. The rule checks layout and layout-meta.xml files for file names that include: - ! @ # $ % ^ & * ? ' : ; ” + = However, we recognize that we inadvertently included hyphen (-) in this special character list. Hyphen should NOT be included because Salesforce automatically adds this special character. This fix removes hyphen in the check for special characters in Page Layout Name.
New Cloud Features
Native GitLab Integration: Your GitLab cloud repo's are now just one click away from our new GUI integration.
Verbose Billing Warnings: Billing warnings will now be more verbose.
New Apex Rules
Avoid using null conditions in SOQL WHERE clause: by default, index tables do not include null records. WHERE clauses that include nulls will therefore require a full scan, which can be very slow for large data volumes. The developer must determine if a fix is needed.
Page Action with a simple redirection: avoid creating a page action that makes a simple client side redirect.
Sending outbound emails using Messaging.sendEmail: emails sent with Messaging.sendEmail count against daily limits which can cause rejection. The developer must determine if a fix is needed.
DMLWithoutSharingEnabled now takes Inheritance into account (v4.5.2).
FieldLevelSecurity now has a parameter to check classes that extend system level classes ie. Database.Batchable, Queueable, and Install Handler (v4.5.3).
CommentRequired now checks for private methods via parameter (v4.5.3).
Parsing issues for the Safe Navigation Operator fixed (v4.5.1).
False positive fixed in SOQLInjection (v4.5.1).
False positive fixed in AuraEnabledWithoutCatchBlock (v4.5.1).
Using Batch Apex from a trigger is dangerous: ensure that jobs created by the trigger do not exceed job limit.
Using Database.AllowCallouts interface in Batch Apex: it is not recommended to make HTTP calls as part of Batch Apex logic.
Source files should have a sufficient density of comment lines (v4.5.3): this version of the rule is able to be used in the IDE. An issue is created on a file as soon as the density of comment lines on this file is less than the required threshold.
EsLint configuration files are no longer picked up with analysis (v4.5.3).
False positive fixed in BadCrypto (v4.5.3).
False positive fixed in UseSingleton (v4.5.5).
IDE Plugin no longer creates files in the base directory (v4.5.5).
False positive fixed in FieldLevelSecurity (v4.5.6).
Rule is NOT throwing a violation if the system mode value is set = “false” (and the object IS checked via isAccessible for the methods).








Enhancement to our disconnected license type for self-hosted customers requiring a license with a project key embedded. CodeScan has a disconnected license type option for self-hosted license where the project key is embedded.
This feature ensures that when the license check is performed, if the project being scanned has a key that is embedded in the license, then the check will pass without needing to reach out to the license server. This is very useful for customers who are not allowed any connection to sites outside their organization, as it allows the project analysis to complete without connecting to the license server.
Recently, some customers were reporting that while the scans were completing but also throwing a timeout error. We have enhanced this feature by changing this notification to occur as a warning log instead of as an error log.
Enhanced rule “Field Level Security Vulnerabilities”: Violation message now displays the correct object instead of '{0}'.
The existing violation message was neither clear nor accurate. Instead, when the violation is flagged, the message should display the correct object instead of '{0}'.
This fix includes a more clear and accurate message associated with the violation.
Severity: Major
Message: Class '{className}' does not have an explicit sharing rule
Tags: convention
Remediation: 5 minutes
Rule is throwing the violation if the object is NOT checked via isAccessible for the methods used in inner query
Rule is not throwing violation if system mode value is set = “true” (and the object IS NOT checked via isAccessible for methods)
Rule is not throwing violation if system mode value is set = “false” (and the object IS checked via isAccessible for the methods)
The Team Administrator cannot view the Subscription Management page.
Org Admins added by the Registered User also cannot view the Subscriptions page.
ARM offers an easy and centralized solution for a Registered User of your organization to manage team subscriptions and accounts. This ensures tracking of all subscription activity, making sure everything is logged. You use the Subscription Management (SM) interface to review and manage how purchased subscriptions are used on your production instance.
Log in to your ARM account using the Registered User credentials.
Hover your mouse over the Admin tab and click on Subscriptions.
Your active plan details will be shown on the dashboard with details like:
Total Subscriptions: Number of licenses purchased by the organization. Only the Registered User of your organization can view the Subscription Management section.
Total Subscription Allotted: Number of licenses utilized to date.
Total Subscription Available: Total number of licenses available.
This section is about creating the teams and assigning members to those teams. This allows you to assign tasks to specific groups of people in your organization.
Log in to the Subscription Management dashboard using the Registered User credential.
On the right side of the screen, click Create Team.
Enter a name for your team.
Choose a Team Administrator or click on theicon to create a user account and assign them permission as a Team Administrator. Fill in the required details; the newly created user will be assigned as a Team Administrator.
Next, enter the number of licenses required in the Team Subscriptions field.
If you would like to add the current logged-in registered user as part of the team, select the checkbox: Grant access to this team for
Click Save.
The newly created team will be displayed on the Subscription Management home page.
For each team created, the following information is displayed:
Team Name: Name of the Team
Created Date: Date/time stamp for the team created
Team Admin: Team Administrator assigned to the current team
Subs. Allotted: Number of licenses allotted to the team
Subs. Consumed: Number of licenses consumed
Subs. Available: Number of licenses pending
Additional options:
Add New Resource: Click on thesymbol to add new resources to the team. The team administrator can create users with their login. However, if you need to add resources from the existing login, follow the steps mentioned in the section.
Edit Team: Click on theicon to modify the team details, like assigning a new team administrator, changing the subscription licenses, etc.
As an Account Administrator for your ARM account, you can manage the user licenses you have subscribed to for your organization.
You must submit a support ticket to purchase extra licenses for your organization. Our Customer Success (CS) team will provide you with a new license key, which you must upload to the Subscription Management page.
Step 1: Upload License Key
Navigate to Admin > Subscription Management once you've received the license key file from us. You'll see a summary of the Total Subscription count, Total Subscription Allotted so far, and Total Subscription Available (which can be assigned to a user or team).
Click on Choose File and upload the license key (.l4j file format). Click Upload.
The total subscription counts will be changed based on the user's license specified in the key.
ErrorIf an incorrect file is selected, a notification popup stating that the file is incorrect is displayed. Click on the Reset button and select the correct file.
Step 2: Updating Allotted Subscriptions
After uploading the license key, the administrator can allot the available subscriptions to the desired team.
Look for the desired team on the Subscription Management page.
Then, under the Actions tab, click on the Edit () icon to update the subscription count for a team.
The number of user licenses available for your account is displayed in the Subscriptions Available field.
In the Team Subscriptions section, click on the - or + buttons to update the license count, then click Save.
All fields on the Subscription Management page will get updated.
Update the total subscription allotted on your account. To do so, go to the Admin > Subscriptions Management section and update the Subs. Allotted and Sub. Consumed count.
Release Date: 17 December 2025
Vault’s data loading operations have been upgraded from Salesforce Bulk API 1.0 to Bulk API 2.0. This enhancement delivers improved handling of large data volumes, and more reliable error reporting. The update increases overall performance and efficiency in data loading workflows, resulting in a smoother user experience and improved operational reliability.
A new search and filtering panel makes it easier to locate objects, navigate complex relationships, and focus only on the schema elements that matter. This improvement helps users quickly identify required parent or child objects and reduces the effort needed to work within large data structures.
Addressed customer-reported vulnerabilities in the ARVault 25.2 release by applying the required security patches. This update strengthens platform security and ensures continued compliance with the latest security standards.
Vault now supports exporting up to 1 million records per Excel file, automatically splitting large datasets into multiple files and packaging them into a single ZIP. This ensures exported data remains accessible and avoids Excel size limitations.
Disabled the delete option for in-progress masking jobs to ensure that active jobs cannot be removed while execution is underway.
Corrected automation rule handling by using proper object API names, ensuring triggers and validation rules are disabled during masking.
No product changes made for extended job duration, as the issue was not reproducible and appears to be Salesforce-related.
Resolved an issue where SSO metadata file uploads were failing. The upload process has been updated, and SSO configuration via metadata file now works as expected.
Release Date: 26 November 2025
Resolved an issue in Masking where the Suffix masking rule incorrectly produced a double hyphen in email addresses containing a hyphen. Previously, values such as [email protected] were updated to [email protected] after masking. The masking logic has been corrected to preserve the original hyphen structure and apply the suffix mask as intended.
Addressed a performance limitation where incremental backups on the Share object could time out when large datasets were filtered using a LastModifiedDate range. Engineering has introduced optimizations to improve query handling for high-volume environments, ensuring greater stability for both full and incremental backups.
Resolved an issue where users logging in through SSO with MFA encountered the error message “Failed to verify MFA OTP.” The MFA validation flow has been corrected to properly route OTP verification through the SSO validation mechanism. Login now functions as expected across all login types, including SSO with MFA, SSO without MFA, and standard login with MFA.
Enhanced the support for the PermissionSetAssignment object during restore. Attempts to restore this object previously resulted in unexpected exceptions, which caused confusion for customers attempting permission recovery. This update provides clear guidance on supported restore behavior, ensuring administrators understand limitations and valid recovery approaches for PermissionSetAssignment data.
Release Date: 19 November 2025
A new enhancement allows users to filter comparison results to include only specific fields during a Compare operation. This improvement helps isolate changes in critical fields while ignoring updates to non-essential system-generated fields, such as Last_Login timestamps in the User object. This enhancement provides faster, more accurate comparisons by reducing false positives and improving focus on relevant data changes.
Vault now integrates with Azure Key Vault to securely store and manage sensitive credentials such as Salesforce tokens, database passwords, and encryption keys. Secrets are no longer stored in application configs and can now be centrally controlled, rotated, and audited, ensuring stronger security and compliance.
Vault has been upgraded to use the latest Salesforce API versions (v63,v64 & v65) to stay aligned with upcoming Spring ’25, Summer ’25, and Winter ’26 releases. All core integrations—SOAP, REST, Bulk, and Tooling APIs—are now updated to ensure compatibility, leverage new platform capabilities, and avoid feature disruptions.
Salesforce has deprecated the “username + password + security token” authentication method for integrations using the SOAP API starting with version 65. This legacy method will be completely disabled by Summer ’27 for API versions 31–64. Customers using this method in AutoRABIT connections (e.g., {{ConnectionName}}) must migrate to OAuth (JWT Bearer) authentication to ensure uninterrupted connectivity. The migration can be done through Connections → {{ConnectionName}} → Migrate to OAuth, followed by the on-screen steps to confirm the connection status as “OAuth (JWT)”.
A fix has been implemented to enforce proper MFA validation during JWT-based login. Previously, users could authenticate without providing the required OTP when MFA was enabled. The updated flow now ensures OTP verification is mandatory, restoring full MFA security compliance.
Spring Security is now explicitly configured to use stateless session management, preventing unnecessary HTTP session creation in our JWT-based REST architecture.
Resolved a 502 Bad Gateway error that occurred when updating scheduled backup configurations for the GS Prod org by optimizing the request payload during save operations.
Addressed and upgraded identified vulnerability patches in the ARVault 25.2 release to ensure strengthened security and compliance.
Release Date: 29 October 2025
Fixed an issue that prevented replication jobs from executing successfully. Filters are now correctly copied to the new edit configuration folder during each configuration update.
Addressed a problem where Live Data Masking results could not be downloaded. Improved file transfer handling ensures large files are now processed and downloaded efficiently.
Resolved an issue where alerts were not generated for failed backups. The system now correctly sends email notifications for scheduled job failures caused by invalid Salesforce credentials.
Fixed an issue causing intermittent backup job failures. Code enhancements now ensure backup jobs run reliably without interruptions.
Release Date: 8 October 2025
You can now retry only the records that failed during processing, without reprocessing the entire job. This feature streamlines error handling and saves time by allowing exclusive focus on failed records.
Vault now provides visibility into actual license usage, storage consumption, and other key metrics compared to Salesforce subscription limits.
Resolved an issue where list view restoration could fail. The restore process now includes all required dependencies to ensure successful recovery.
Introduced automation to handle Key-rotation activities, ensuring smoother key transitions and uninterrupted system operations. This enhancement strengthens security, reduces downtime, and minimizes the risk of errors.
Upgraded underlying platform components to enhance security, improve performance, and ensure compatibility with the latest standards.
Release Date: 24 September 2025
A fix has been implemented to ensure that certain metadata types are processed correctly. Previously, additional prefixes in metadata items during retrieval caused processing failures, which have now been resolved.
Additional information has been added to ensure that email alerts include relevant information that helps users with easier understanding of the source of alert.
Release Date: 3 September 2025
Fixed an issue that occasionally prevented some alerts from appearing. The Alerts section now consistently displays the full list of alerts.
Resolved an issue that impacted backup scheduling. Backup schedules now display accurately and run as expected.
Addressed an issue related to a legacy dependency. Archive processing is now fully reliable and unaffected by this component.
Fixed an issue that caused inconsistencies when handling ContentVersion records during deletion. Archive job processing now works correctly and without discrepancies.
Improved memory management during archive job execution. Archive jobs now run reliably without failures related to memory usage.
Release Date: 20 August 2025
Improved the job termination logic to ensure jobs end gracefully when timeouts occur, preventing partial processing and maintaining system stability.
Implemented a fix to prevent timeouts during data processing in synthetic backups, ensuring uninterrupted and reliable execution.
Resolved an error in archive record processing to guarantee that all records are handled accurately without failures.
Added additional logging to replication jobs, enabling more precise identification of root causes for quicker resolution of issues.
Release Date: 13 August 2025
The column headers in the Archive Summary screen have been updated to improve readability and ensure better understanding of the data presented.
A new capability has been added to Vault Connect, enabling backups to be selected as a source in the configuration.
This enhancement empowers customers to strengthen their business continuity strategies by seamlessly leveraging backup data during critical scenarios.
During email message restoration, the system now ensures that audit fields are preserved accurately, avoiding unintended updates and maintaining metadata integrity.
Improvements have been made to the event logging mechanism, including:
Consolidation of daily logs
Enhanced tracking of activities performed by anonymous users for improved auditability and compliance.
The Vault Compare operation has been optimized to provide a faster and more seamless user experience during large-scale data comparisons.
Enhancements have been made to the logic that fetches Salesforce Org details, ensuring more accurate identification of the Salesforce environment connected to Vault.
Release Notes: 21 July 2025
New Feature: Live Data Masking enables Salesforce administrators to protect sensitive information (such as PII) within a live production org without the need to replicate the full dataset. This targeted masking approach allows admins to:
Selectively mask specific fields across chosen objects
Minimize operational overhead by avoiding bulk data processing
Ensure only necessary data is altered, maintaining data integrity elsewhere
This enhancement provides a more efficient and secure way to manage data privacy in real-time environments.
A new provision allows seamless editing of Salesforce org configurations within Vault. This feature simplifies compliance-driven credential updates by enabling users to re-authenticate Salesforce orgs with updated login credentials directly from the Vault interface.
The fix ensures that only the explicitly selected child objects are processed during archival/hierarchical backup operations, providing more control and reducing unintended data processing.
Column labels and field names across the application interface have been standardized. This update ensures improved clarity and a more consistent user experience throughout Vault.
A fix is implemented to prevent special fields—such as audit fields—from being inadvertently updated during email data operations, preserving the integrity of email-related metadata.
Release Notes: 16 July 2025
Flexible Scheduling Enhancements
The scheduling functionality has been enhanced to support a wider range of intervals, providing greater flexibility in configuring backup and automation schedules.
Deleted Records Handling
A new option has been introduced to exclude records in the Recycle Bin from processing. This helps streamline operations and focus only on active data.
GDPR Compliance for Deleted Records
Release Notes: 9 July 2025
Archival Job Enhancement
Previously, the archival job retained additional information even after the configured data retention period had expired. This behavior has now been updated: expired data is fully cleared, ensuring more efficient resource utilization and improved system performance.
Backup Job Reliability Improvement
Resolved an issue where backup jobs processing millions of records would experience timeouts, leading to excessive and unproductive retries without successfully retrieving data. The underlying cause has been addressed to ensure more stable and efficient backup operations at scale.
Optimized Metadata Handling in Restore
Release Date: 02 July 2025
New Archive Enhancement: Disable Automation Rules
Vault now allows users to disable Salesforce automation rules during the archiving process. This improvement helps ensure a smoother and more reliable archival experience by preventing interference from active automation rules. As a result, users can expect fewer errors and increased stability during archival operations.
Selective Record Download for Backups and Archives
Users can now filter and download specific records from a backup or archive, enabling targeted data access without the need to browse through the entire dataset. The downloaded files are easily compatible with common tools like Excel, allowing for quick and convenient analysis of only the required information.
Release Date: 18 June 2025
Backup Optimization: Streamlined the object processing logic within the backup module to improve performance and reliability.
Dynamic Pagination for Replication Config: Introduced dynamic pagination during replication config creation, ensuring better scalability and responsiveness.
Improved Alert Search: Optimized the search functionality in the Alerts section for quicker results and enhanced user experience.
Release Date: 04 June 2025
Vault Compare Enhancements: Enhanced the user experience with easier navigation to specific fields and more intuitive change review capabilities.
Enhanced Scheduler Architecture: Improved tracking and queuing of jobs for more efficient and reliable execution.
Additional Validations During Cloning of Replicate Jobs: Introduced environment validation checks to alert users of any missing metadata before initiating the cloning process of replicate jobs.
May 2022 - New Features, Enhancements, and Improvements
The following are the "ncino-goldstandard" nCino-related rules that have been added to the current Apex/Salesforce Metadata rule sets.
CodeScan self-hosted is compatible with SonarQube™ 8.9 and SonarJS 6.2+. For more information, see
Below are the exisitng CodeScan rules key that are tagged as “ncino-goldstandard.”
Updated all third-party libraries to the most recent versions to address security, stability, and reliability issues.
The CodeScan portal has been updated to include minor speed, bug fixes, and security enhancements.
(12 July 2022) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Codescan and Visual Studio Code's rule and file-type issue counts were out of sync. We have updated Codescan Visual Studio Code extension to version 1.6.9, which fixes the issue with analysing metadata files ()
Writing XPath rules based on filename on SFMeta is now supported ().
There was an issue that prevented users from editing the settings for Branches and caused an error message that said, Cannot read properties of undefined (reading "config") ().
(23 June 2022) This is a maintenance release. The following items were fixed and/or added:
The sf:UnusedFormalParameter rule's false positive issue has been resolved ()
Fixed an issue that prevented SonarQube 9.4.0 from functioning properly with Java 11 version.
The sonar-java-plugin
(13 June 2022) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue that prevented the CodeScan and Azure DevOps integration from functioning as expected. The Azure DevOps plugin was updated to version 1.6.8 to overcome these issues.
Fixed an issue where the Field Level Security Rule displayed a false negative for the code below:
update Security.stripInaccessible(AccessType.UPDATABLE, new List<vlocity_ins__ContactEmployment__c> { ceLst.get(0) }).getRecords();
(30 May 2022) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue that prevented the user from logging into the CodeScan instance.
Fixed an issue that prevented the user from creating the Salesforce project in their CodeScan instance.
The issue where the user were not able to create a CodeScan project using the Gitlab plugin has been resolved.
Fixed an issue where the codeScan rules which were not a part of active Quality Profiles were getting applied.
Vulnerability detection in For-each loop. for eg., for(Contact c : [SELECT Name FROM Contact])
Vulnerability detection in Database method calls. for eg., Database.insert([SELECT Name FROM Contact]);
Migrated IntelliJPluginErrorAction web servlet to Spring MVC.
Audience: Org Administrators only – general users don’t see these controls.
When you move metadata between environments, small but critical differences can break deployments:
Hard-coded URLs that point to Production instead of Sandbox.
Object-level permissions that should exist only in lower tiers.
Label values that need slight tweaks per org.
Search & Substitute lets you define rules that automatically find and replace text inside selected metadata before the deployment or commit occurs. The rules run when you:
Deploy sandbox → sandbox
Deploy sandbox → Version Control
Commit Version Control → sandbox (CI jobs)
That means fewer manual edits, fewer post-deployment fixes, and more predictable pipelines.
Log in to ARM.
Go to Admin › Search and Substitute.
Click Create Rule.
Each rule has a label plus one or more parameters.
Click + to add up to 5 parameter sets per rule. Duplicate rows are not allowed.
AutoResponseRule, CustomLabel, CustomMetadata, CustomObject, CustomSite, Dashboard, DashboardFolderShare, Network, NamedCredential, PermissionSet, Portal, Queue, RemoteSiteSettings, Report
Tip: Combining Search & Substitute with CI Job deployment settings lets you adjust the same package differently for each target org.
Need to change an invoice number format in one org only? Create a rule like this:
Metadata Type: CustomObject › Invoice__c
Sub Element: Fields.displayFormat
Criteria: a-{000}
Click Save to store the rule. It appears in the list with Edit, Delete, and Clone icons.
On the Deployment Settings screen:
Open Apply Search and Substitute Rules.
Move rules to Selected with / .
Use the arrows to order execution (top rule runs first).
During Commit or Submit for Validation, pick your rule under Search and Substitute.
When creating a CI Job, expand the Deploy section and choose the rule.
Granularity first – target specific metadata members when possible to avoid false replacements.
Limit to five – ARM enforces a max of 5 parameters; combine similar changes into one rule.
Test in Sandbox – run a dry-run deployment to validate your substitutions before Production.
Clone, don’t copy-paste – use the
With Search & Substitute configured, your deployments self-adjust to each environment—no manual XML edits required.
Release Date: 17 October 2025
CodeScan Self-Hosted version 25.1.2 (Eagle v5) is comprised of the following 9 components:
8 Rule Enhancements
1 Fix
Component details are listed in their corresponding sections within this document.
1. Enhancement to “Switch Statements Should Have a When-Else Case” Rule
Currently, the rule is not working as expected, as it does not raise violations when a switch statement lacks a when-else block. We have modified that logic to correctly identify switch statements that are missing a when-else case, so users can ensure the code is more robust, future-proof, and does not miss handling unexpected cases.
Example:
Verified that the updated rule now correctly flags switch statements without a when-else block, ensuring violations are raised consistently for missing default cases.
Enhancement to “Avoid Reversed Operators” Rule
Modified the rule logic to correctly detect and report improper usage of reversed operators (=-, =+) in Apex code, so users can avoid mistakes where variables are unexpectedly reassigned rather than incremented/decremented.
Current Behavior:
Violations are not raised when using reversed operators like target =- num; or target =+ num.
Expected Behavior:
The rule should detect and flag cases of reversed operators (=-, =+) and provide a clear violation message.
The violation message should explain the confusion:
x =- y; assigns -y instead of subtracting.
x =+ y; assigns +y instead of adding.
This new logic will prevent developers from introducing subtle logic bugs caused by operator misuse. Further, we updated the rule example with the following:
Verified the new logic via the following scenarios: 1. Rule sf:AvoidReversedOperators raises violations for reversed operator cases (=-, =+).
2. Rule does not raise false positives on valid operator usage (+=, -=).
3. Enhancement to “CouplingBetweenObjects” Rule
Modified the rule logic to correctly detect and report violations, so users can identify classes with excessive dependencies and reduce code complexity for better maintainability and testability.
Verified that the violation is triggered when the number of classes used exceeds the defined threshold value in the rule parameter (for example, if the threshold is set to 4 and 5 classes are used, a violation will be raised).
4. Enhancement to “Add Empty String” Rule
Updated the rule logic to identify and flag expressions where literals are concatenated with an empty string (e.g., "" + 123 or 123 + ""). Also ensured that violations are reported with a clear message and that valid concatenations and type-specific toString() methods are not falsely flagged.
Verified the following scenarios are all working as expected:
Empty string with numeric or Boolean literals Examples: '' + 123, 123 + '', '' + -42, '' + 3.14, false + '', '' + true
Empty string with string/char literals or inside chains Examples: '' + 'abc', 'abc' + '', 'A' + '' + 'B', 1 + '' + 2
Empty string literals inside parentheses Examples: ('' + 1) + 2, 1 + ('' + 2)
Empty string at start of long chain with literals and variables Example: '' + 123 + 987 + var1 + var2
5. Enhancement to “Avoid Hard-Coded Resource References” Rule
Enhanced the rule logic to identify hard-coded file path references and raise violations with a clear issue message.
Validated the logic by verifying that users are able to see violations for use of the attribute value that starts with '/resource/'.
6. Enhancement to Suppress Warnings Rule
Our rule, TrackSuppressWarnings, had logic to find @SuppressWarnings, but the logic didn’t include find @suppresswarnings.
This suppression tag works in any case, and we recognized that our TrackSuppressWarnings rule needs to do the same (meaning the rule needs to be case-insensitive.)
This logic was added to the rule in this enhancement.
Verified the SuppressWarnings rule enhancement and validated that the suppression tag is working in all case-insensitive instances and our TrackSuppressWarnings rule is throwing violations for all cases.
7. Enhancement to Apex rule “Unused Formal Parameter” {sf:UnusedFormalParameter}
CodeScan has offered this rule since Dec 2017. Recently, a customer reported that the Unused Formal parameter doesn’t find when variables are used in SOQL. We replicated this issue where CodeScan flagged a variable as an unused variable, even though it is used in the SOQL string.
We have enhanced this rule to detect additional cases where string parameters are part of SOQL. The rule now detects cases where string parameters are used as part of building a SOQL query.
Verified the enhanced logic of rule “UnusedFormalParameter” via the following scenarios.
Previously, a parameter (e.g., encounterIds) used in a SOQL string (e.g., WHERE Id IN :encounterIds) was wrongly reported as unused. Now, this is correctly detected as usage — no violation.
Also verified the following cases are all working as expected: Verified: Parameter used in SOQL with bind variable (:encounterIds) — no violation Verified: Parameter used via clause string assembly — no violation Verified: Parameter incorrectly concatenated into SOQL string — violation Verified: Parameter declared but not used anywhere — violation
8. Another Rule Enhancement for sf:UnusedFormalParameter
In this rule enhancement, we introduce a configuration flag, ignoreUnusedParametersInInterfaceOverrides, in the sf:UnusedFormalParameter rule, so unused parameters in valid interface implementations and method overrides can be conditionally suppressed. By default, violations will continue to be reported unless this flag is explicitly set to true.
How to Identify These Parameters for Suppression
When designing your rule improvement, the logic should:
Check if the method is implementing a known Salesforce interface method:
Use method signature matching (name, parameters, visibility).
Confirm the containing class uses implements keyword for one of the known Salesforce interfaces.
Ensure parameter types match exactly, e.g., SchedulableContext, Database.BatchableContext.
Additionally, we updated the Rule Description to “Avoid passing parameters to methods or constructors without actually referencing them in the method body. Use the ignoreUnusedParametersInInterfaceOverrides parameter to suppress violations for unused parameters in valid interface implementations and method overrides.”
Verified the rule sf:UnusedFormalParameter and validated the following conditions:
The method implements a known Salesforce interface method.
Method signature matches exactly in terms of:
Name
Parameters
Fixed issue with CodeScan rule detecting SOQL Injections, which was causing analyses to break Previously, while analyzing for SOQL Injection, if a local variable is declared using a class-level variable of the same name, then CodeScan analyses were erroring with StackOverflowError, as it was stuck in a loop while resolving the reference. Example: class Foo { private static String QUERY = 'Select '; public static List<Opportunity> getData(String stage) { String query = QUERY + 'Id FROM Opportunity WHERE StageName = :stage'; return Database.query(query); } } With this fix, we added validation to detect and prevent such recursive reference resolution. Verified the SOQL Injection rule fix (which was causing stack overflow error). Validated that now users are not encountering the error and project analyses are working as expected.
New Apex Rules
Avoid Insecure Digest Algorithms: MD5 and SHA-1 algorithms are no longer considered secure because it's too easy to create a hash collision between two message contents.
Avoid Salesforce System Class Names: Classes with names that already exist as internal classes will take precedence due to namespacing.
Avoid Nested Switch Statements: Avoid creating nested 'switch' statements since they are error-prone, harder to read, and harder to maintain.
Avoid Reversed Operators: Reversing operators may be a bug, or at the very least make it hard to read.
Avoid Using HTTP Referer Headers: HTTP Referer headers can be modified by attackers. Making a decision based on the value of the referer can be dangerous.
Catch Block Should Do More Than Rethrow: Catch blocks that do nothing but rethrow an exception should either be changed or removed.
Field Level Security Vulnerabilities: This rule makes sure that the code checks for access permissions before running a SOQL, SOSL, or DML operation. Single Method Singleton: Avoid using overloaded getInstance methods. Statements Should Be On Separate Lines Statements should be on separate lines to increase readability and maintainability.
Suspicious For Loop Incrementer: Incrementers that do not match the body of the for loop could be a bug.
Ternary operators that can be simplified with || or &&: Ternary operators with the form condition ? literalBoolean : foo or condition ? foo : literalBoolean can be simplified.
Unexpected Casting of Types: When arithmetic is performed on a type, the type remains the same even if the result is a different type. This can return an unexpected result.
Updated Apex Rules
Division By Zero: Division by zero exception may occur when zero could be the denominator to a division or modulo operation.
Apex Classes should use Random IV/Key: Now checks for EncodingUtil.base64Decode(key);
New Visualforce Rules
Avoid using GETSESSIONID() and $API.Session_Id: Lightning Experience does not have access to the API session token. Visualforce pages that access the session ID should be tested within Lightning Experience.
External Script and Style Resources Should Be Avoided: Including content from untrusted sources can lead to various security issues including include injection of malware.
Remove OnClick Javascript: Javascript in "onclick", "onmouseover" and similar actions within components are ignored.
Improved documentation on vulnerabilities including links to OWASP and CERT explanations.
Support for Inherited Sharing Keywords in Apex -
Code coverage that does not match the current state of the codebase no longer causes unrecoverable errors (v4.2.0)
Fixed bug that caused component files to not scan correctly (v4.2.2)
Fixed issue that caused certain tags starting with "\" in comments to not parse (v4.2.3)
The rule "Class with only Private Constructors should be Final" has been deprecated and removed completely. Classes are final by default therefore this rule is unnecessary.
The rule "Remove OnClick Javascript" has been removed from the default Visualforce and Lightning Quality Profile.
SonarQube™ 7.6 Support
A selection of new rules has been added to the default Quality Profiles (

Require CSRF Protection On GET Requests: Require CSRF protection on GET requests must be enabled from the Visual Force Page settings.
Unencoded Formulas In Style Tags XSS: Makes sure that all values obtained from URL parameters are properly escaped / sanitized to avoid XSS attacks.
Unescaped Value Could Cause XSS: Reflected Cross-site Scripting (XSS) occurs when an attacker injects browser executable code within a single HTTP response. Using unescaped parameters can be a security risk.
Avoid Apex Tags Within Script: Avoid using <apex:*> tags within <script> tags for readability and security.
Fixed bug in Long Javascript rule that causes the length to be improperly calculated (v4.2.3)
Fixed issue that caused files to not highlight correctly (v4.2.3)
Fixed bug that caused Class Without Test Class rule to ignore certain files (v4.2.3)
Fixed bug that caused errors to appear and disappear (v4.2.3)
Fixed bug that caused certain code coverage data to be displayed incorrectly (v4.2.5)
Fixed bug in the Class Without Test Class rule (v4.2.6)
A fix has been implemented to ensure that opted-out deleted records are no longer visible in Vault, aligning with GDPR compliance and privacy expectations.
The system's capability to process metadata has been improved by increasing the number of files it can handle concurrently. This ensures smoother and more efficient metadata restore operations.
Improved Export Stability for Large Datasets in Compare Module
A fix has been deployed to enhance the reliability and performance of the export functionality in the Compare module. Users can now expect a smoother experience when exporting large datasets, especially during bulk compare operations.
Enhanced Event Logging for Improved Traceability and Integration
The event logging system has been upgraded to provide greater detail and reliability, enabling seamless analysis and traceability of system activities. Logs are now more easily integrated with tools like Splunk, streamlining monitoring and audit workflows.
Schema View Usability Fix: Easy Copying of Object Names
A fix has been implemented to allow users to easily copy object names while viewing the schema. This enhancement improves usability and efficiency, making it more convenient to reference or reuse object names during configuration or documentation tasks.
Performance Improvement – Replicate Job Optimization: Resolved a performance bottleneck in the replicate job process by identifying and addressing a delay issue. This enhancement improves execution speed and overall system efficiency.
Improved Salesforce Session Management: Improved session management to prevent inactivity during long-running jobs and enhanced API call tracking for greater accuracy.
Scheduler Distribution: Moved the scheduler to an external server to better manage processing load distribution.
Performance Enhancements: Optimized data retrieval logic to improve performance across backup and archival operations.
Replicate & Restore Performance: Optimized the data loading process, significantly improving replicate and restore performance.
Restore Logic Update: Refined logic to more effectively prevent duplicate record creation, ensuring more reliable and consistent restore operations.
Salesforce Winter ’25 Upgrade: Upgraded the Salesforce integration to support the latest Winter ’25 API version.
S3 Policy Management: Improved S3 configuration checks to surface errors early during Vault account setup.
Tomcat Upgrade: Upgraded Tomcat version 10 to 11 for improved security, performance, and standards compliance.
Vault Data Masking: Improved pattern recognition in specific data types to ensure accurate masking while preserving the original format required for valid data representation.
Restore UI Label Updates: Updated restore flow labels:
“Restore Now” is renamed to “Create Restore Job”
“Trigger Restore” is renamed to “Review and Restore”
“Selected Data to Restore” popup is renamed to “Restore Summary”
Big Objects Support: Implemented support for backing up Big Objects.
Knowledge Article Replication: Enhanced owner ID handling to prevent errors caused by owner mismatches, ensuring smooth and accurate replication of knowledge articles.









ReportFolderShareSamlSsoConfigSharingCriteriaRuleSharingOwnerRuleWorkflowSubstitute: a-{001}
1
Metadata Type
Choose a metadata type – or an individual member – where the replacement should occur.
2
Sub Element
The XML path / JSON key holding the text you want to change.
3
Criteria
The exact string (or pattern) to search for.
4
Substitute
The replacement value.








This rule is required as Salesforce does not allow more than 5 External IDs per object
Test Class Names Should Include 'Test'
This rule is required as Test classes should include the word 'Test' in their class names
Hard Coded Email Address
This rule is required as to avoid hardcoded email addresses
sf:UnitTestContainsTooManyAsserts
sf:AvoidUsingTestIsRunningTest
sf:OnlyOneReturn
sf:UnusedLocalVariable
sf:EmptyTryBlock
sf:EmptyFinallyBlock
sf:AvoidSoqlInLoops
sfmeta:ExcessiveWorkflowsOrgWide
sfmeta:RequireDescriptionComponent
sfmeta:LimitCustomFields
Resolved an issue where the Project Analysis jobs were stuck in the queue and were not triggered at the scheduled time (46552).
Fixed an issue where the CodeScan-Visual Studio Code plugin failed to detect javascript errors even though SonarQube have identified it at the Salesforce Lightning web component (46104).
7.6.0.28201Fixed an issue for all child rule violations that happen when files are crossed (rule violation location in two different files).. This was fixed by setting the correct file location for child rule violations.
Fixed an issue where users were experiencing an expired token error that appeared on the master branch every time a comparison branch was analysed before it (44492).
Fixed a bug where, after logging out from the CodeScan application, the user was directed to the CodeScan's Project screen rather than being asked for their login information (username and password) when they selected the Login with AuthO button.
Fixed an issue where the Field Level Security Rule shows false negative for the below cases:
Avoid Excess Workflow Rules per Object
This rule is required as the objects which contain too many decisions, are complex and difficult to maintain
Flow Decision Limits
Flows which contain too many decisions are complex and difficult to maintain. This rule will consider reducing the number of decisions or utilizing Apex.
Potential Overuse - Cross-Object Formulas
This rule is required as Salesforce does not allow more than 15 cross-object formulas per object
Potential Overuse - Object Lookups
This rule is required as Salesforce does not allow more than 25 lookup relationships on a single custom object
Potential Overuse - Relationship Objects
This rule is required as Salesforce does not allow more than 40 relationships per object
sf:AvoidUsingHardCodedId
sf:MultipleTriggersOnObject
sf:LongMethodName
sf:LongClassName
sf:LongTriggerName
sf:VariableNamingConventions
vf:HeaderCheck
sf:UncommentedEmptyMethod
sf:UncommentedEmptyConstructor
Potential Overuse - External IDs
sf:CommentRequired
Delete a Team: Click on theicon to delete the team. This process cannot be undone.








Empty string used with - operator and literals Examples: '' - 123, 123 - '', '' - -42
Visibility Enforcement
Only suppress violations if the method visibility is public or global, as required by the platform.
Private or protected methods should never be eligible for suppression under this rule.
This ensures that suppression only applies to methods actually callable by the platform or conforming to Apex interface rules.
Override Detection
If a method in a class overrides a method from a superclass or an abstract class:
Signature match is mandatory (same name, return type, and parameters).
Use of the override keyword confirms the intent, but even without it, structural matching should be enough.
In such cases, the parameter should not be flagged if unused, since it’s required by the parent contract.
Value / Purpose
Prevent misleading or incorrect violations in valid interface and override implementations (e.g., execute(SchedulableContext)).
Preserve backward compatibility by keeping the rule strict by default.
Visibility
The containing class uses the implements keyword with one of the known Salesforce interfaces (e.g., Schedulable, Database.Batchable).
Parameter types match exactly, including types such as:
SchedulableContext
Database.BatchableContext
















1
Profile - Developer Policy
Profile - Developer Policy gives visibility on access permissions related to Author APEX, Import Custom Objects. This violation means that this Profile conflicts with your policy for these settings.
2
Profile - Password Policy
Profile - Password Policy gives visibility on access permissions related to Passwords Expiry, Enforce password History, Minimum Password Length, Password Complexity Requirement, Password Question Requirement, Maximum Invalid Login Attempts, Lockout Effective period, Obscure answer for password resets, Require minimum One Day password lifetime, Don't Immediately expire links in forgot password emails.
3
PermissionSet - Security Settings Policy
PermissionSet - Security Settings Policy gives visibility on access permissions related to Manage Certificates,Manage IP Addresses,Manage Encryption Keys,View Threat Detection Events,Profile allows Manage Security Center.
The complete CodeScan rules list can be accessed HERE.
New interactive and appearance have been introduced to the CodeScan Welcome screen. Two new options, Application Security Testing and Policy Management are offered when you first log in to CodeScan. If you select Application Security Testing, you will be directed to the Projects page, which is now your default homepage. As a result, when you log in to CodeScan the next time, you will be immediately redirected to the Projects page. Similarly, if you choose Policy Management, you will be navigated to the Policy Results screen, now set as your default homepage.
The Policy Results page can now be accessed under the More tab in the CodeScan application.
This release includes minor stability fixes and improvements for the CodeScan platform.
(CodeScan v.23.1.6)
This update included minor improvements.
(CodeScan v.23.1.5)
The following was updated:
sf:AvoidPublicFields
Class Variable Fields should not have Public Accessibility
sf:AvoidUsingHardCodedId
Avoid Using Hard Coded Salesforce Id
(CodeScan v23.1.4)
The following rules were updated for release 23.1:
sf:InsecureEndpoint
Avoid Cleartext Transmission of Sensitive Information
sf:SOQLInjection
Avoid Untrusted/Unescaped Variables in DML Query
(CodeScan v23.1.3)
What's New:
CodeScan Self-Hosted version 23.1.3 (now compatible with SonarQube™ version 10).
(CodeScan v23.1.2)
This is a maintenance release. The following items were fixed and/or added:
Starting from version 23.1.2, CodeScan supports integration to GIT with SSH Keys and supports ssh:// protocol. Connecting to GIT repository using the Secure Shell Protocol (SSH) provides a secure channel over an unsecured network. (Learn More)
Salesforce Spring '23 (API version 57.0) Support: To keep our product up to current with the most recent Salesforce upgrades, CodeScan supports the most recent API 57.0 version in this release.
This release also includes insecure dependent libraries upgrade and other significant security improvements.
(CodeScan v23.1.1)
CodeScan self-hosted has been upgraded from 22.8 to 23.1.1 version.
This release includes Apex-pmd dependency upgrade and significant security improvements. Updating is strongly recommended.





Release Date: 19 January 2025
Group Jobs Stability: Fixed an issue to ensure group jobs execute without failure.
Import Process Stability: Resolved an issue to prevent failures during the import process.
Rollback Functionality: Fixed the rollback functionality on the nCino UAT instance to ensure it works as expected.
Release Date: 13 December 2024
Revision Range: Improved the checkout logic for the revision range to enhance performance.
Fixed Query Logic: Resolved an issue with adding conditions to queries.
Template Failure: Fixed the issue causing failures in the "nCino Template."
Publish Icon: Ensured the publish icon is visible for "nCino Customers" on the "Feature Template Manage" screen.
Release Date: 24 November 2024
The following enhancements ensure compliance, improve flexibility, and streamline the user experience.
CI Job Backup: CI job rollback backups have been further streamlined and organized to ensure compliance standards are met.
nCino RBC Deployment Options: Customers can now verify and configure the required externalID during RBC deployments, improving flexibility and control.
Trigger Build on Commit: Scheduling conflicts are now resolved when the "Trigger Build on Commit" option is enabled, ensuring seamless automation.
Release Date: 10 November 2024
The following enhancements include an upgrade for version compatibility and fixes to improve user experience and streamline performance.
Salesforce Winter '62 Compatibility: Upgraded nCino to support the latest Salesforce Winter '62 release.
RBC Fixes: Resolved issues with RBC deployments and commits for improved reliability.
Feature Version Loading: Fixed loading issues with the Feature Version page for a smoother experience.
Release Date: 27 October 2024
The following features, enhancements, and fixes have been implemented to improve user experience and streamline performance.
Auto Trigger nCino Jobs
Enabling “Auto Trigger on Commit” in CI Jobs now automatically starts jobs with each new version control commit, streamlining workflows and eliminating manual triggers.
Rollback Error
A rollback failed due to an issue with the selected baseline revision. Verify the baseline selection to proceed.
OwnerID Record Error
The ID of the user who created the record will be retained in the destination records.






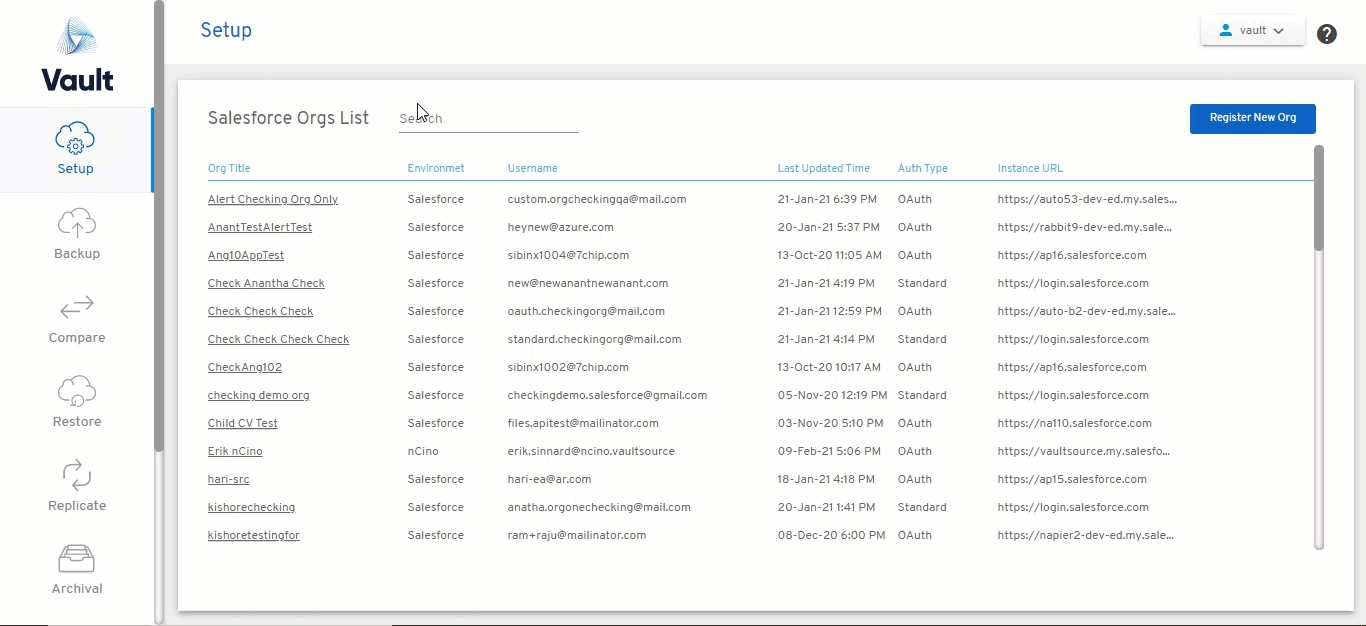
December 2023
Minor
V.S. Code 1.6.12 and support for IntelliJ 7.0.0 (Only Cloud customers)
Nov 2023
Major
North America includes 23.2.0–23.2.4, plus 3 fixes
Nov 2023
The VS code version 1.6.12 fixed several issues that were impacting the performance during the binding process. The issues that were identified and fixed are as follows:
Fixed NPM audit vulnerability to use the latest version of dependencies as the context menu
Added the CSS language that is supported in Sonar version 4.19
Upgraded to SonarQube LTS version 9.9 which has a single language plugin for JavaScript/TypeScript/CSS
Activated the CSS rules in the VS code Quality Profile so that the VS code extension and CodeScan UI are in sync
IntelliJ extension 7.0.0 Added support for newer IntelliJ versions (2023.1 and above)
NOTE: This is ONLY for Cloud customers
This fix leverages Org ID, which is not applicable for on-premises hosting, and thus requires additional engineering. Deployed fix relates to ARM Integration Null Pointer Exception causing an issue where CodeScan analyses were failing when being triggered from ARM. CodeScan scan failed to run analysis.
Deployed Fix for issue with the GitLab Handler required fix added configurations for US.UTF-8.
November 2023
Code fixes applied:
The inclusion of special characters into the Payload sent by the GitHub webhook is compelling. If there are any Unicode characters, the hash gets generated differently, which was causing this issue intermittently. With this fix, we have added support for UTF encoding to resolve the issue.
Correct HTTP 400 error during CodeScan execution
Corrected instances of CSV export report not matching the Issues tab in the project.
Application logic leaves existing issues from the target branch being displayed in PR. They only filter issues in a RESOLVED state. A code fix was applied to remove one condition and filter out all the remaining issues from the target branch with the decision to remove that condition only if the new feature flag is disabled.
Code fix applied to correct stack overflow error with SOQL injection rule
September 2023
This update introduces several significant improvements that will enhance your ability to maintain high-quality code and improve your security posture. This includes:
Greater flexibility and easier maintenance of Quality Profiles
Enhanced Token Generation
Improved editing control over Quality Gates
MuleSoft rules library with scanning XML configuration files
UI/UX updates and improvements
1. Maintenance of Quality Profiles A new update was made to the screen where Quality Profiles are maintained. With this release, users can:
Extend an existing Quality Profile: When you extend a profile, you create a child profile that inherits all the activated rules in the parent profile. You can then activate additional rules in the child beyond those inherited.
Copy an existing Quality Profile: When you copy a profile, you clone all activated rules of the original. From here, you independently activate or deactivate rules to fit your needs; your new profile will not inherit changes made to the original profile.
Create a blank Quality Profile: Create a new custom profile and activate rules per your organization’s needs.
Additionally, you can see your profile's inheritance hierarchy and change the parent profile by selecting the Change Parent option. Selecting the parent profile is now mandatory.
2. Enhanced Token Generation You can generate new tokens at User > My Account > Security.
You can now create two types of tokens: project analysis tokens and user tokens. A project analysis token allows you to run analyses on the project it was generated for. A user token gives you all the permissions of the user who issued it. For example, a global Admin's user token gives you full rights to the instance.
You can select an expiration for your token or choose ‘no expiration.’ If you select an expiration date, you will receive an email seven days before your token's expiry date to remind you to rotate your token.
3. Improved editing control of Quality Gates
Quality Gates permissions
The Quality Gates page now includes a section called 'Permissions.' By default, users with the global 'Administer quality gates' permission can edit quality gates.
Furthermore, CodeScan enables users with the global 'Administer quality gates' permission to grant specific permissions to individuals or user groups for managing a particular quality gate. These permissions apply only to the specific quality gate and not all quality gates.
Editing Quality Gates
Each quality gate condition comprises a measure, a comparison operator, and an error value.
In the latest update, users with the global 'Administer quality gates' permission must use the Unlock editing feature for adding or modifying existing conditions for quality gates.
4. Scanning MuleSoft XML configuration files CodeScan’s new MuleSoft scanner tool analyzes the security settings of sensitive configuration files to ensure vulnerabilities aren’t introduced to the system. For example, this tool can check if the credentials for a third-party database access are properly encrypted.
Setup:
1. Navigating to Your MuleSoft Project from Git Once you've created your MuleSoft project from Git, understanding the project's navigation and configuration becomes essential.
2. Accessing the MuleSoft Project Dashboard
Click on the name of your MuleSoft project.
This action will redirect you to the dashboard, where you can view the quantity of each type of issue present in your project.
3. Viewing & Filtering Issues On the dashboard, the numbers indicate different issue types. Clicking on any of the numbers will present a filtered list based on the issue type.
Alternatively, to see all issues:
Click on the Issues tab at the top of the screen.
Here, you can manually filter issues using the menu on the left.
Filter options include Type, Severity, and the specific Rule causing the issue.
4. Configuring a Quality Profile for Mule Language A quality profile determines the issues that appear on your dashboard.
Go to the organization screen.
Click on Quality Profiles.
Filter your profiles by selecting Mule.
Here, you'll see the built-in profiles available for Mule versions 3 and 4.
Creating a New Quality Profile You can create a new profile in two ways:
Copy an existing built-in profile and start editing it.
Create a new profile from scratch.
For an in-depth look at this process, refer to the upcoming Quality Profiles video.
5. Understanding Mule Quality Profile Rules
Inside your mule quality profile, you'll find rules that govern the profile's behavior.
Click on the number of rules to view a filtered list of active rules within that profile.
For details on a rule:
Click on any rule name. This provides a description of the rule and any parameters it contains.
6. Analyzing Your MuleSoft Project
Click on the name of your MuleSoft project.
Navigate to the More tab at the top of the screen.
Choose Project Analysis from the dropdown menu.
Manual Analysis
Click on the Run Manual Analysis button positioned at the top right corner.
Then select Analyze Now.
Automated Analysis An analysis will automatically start on your MuleSoft project under the following conditions:
Any changes are pushed to your specified branch in your Git project.
A pull request is made against your selected branch.
5. UI/UX Updates and Improvements
Enabling key shortcuts
Various actions in CodeScan can be performed using keyboard shortcuts. Use the question mark shortcut (hit ? on your keyboard) for a list of available keyboard shortcuts while working with CodeScan.
Additional UI/UX Updates
The Projects tab is newly added to CodeScan in this release. See My Account > Projects for a list of projects you are administering. You can select a project from there for full access.
The link "Why is this an issue?" on the Issues home screen has been relocated within each individual issue. Now when you click on an issue, a new page opens with two sections on the right side: Where is the issue? and Why is this an issue?
Original screen
New screen
A new addition to the My Projects section is the inclusion of the My Favorites | All tab. Under the My Favorites tab, you will find a collection of projects you marked as favorites. Selecting the All tab will display all the projects currently added to your organization.
Minor performance enhancements, bug fixes, and security improvements can also be observed in the CodeScan portal.
Nov 2023
This update introduces several new rules and bug fixes for current rules. This includes:
1. Flow Rules
There are 19 new rules for Salesforce flows:
Inactive flows should be removed: Inactive flows may cause clutter in the Salesforce org. In extreme cases, they can begin to hit the organization’s limits. These should be removed if not being used.
Avoid Large Flows: Too many nodes can cause your Flow to become complex and unmanageable. Consider using Subflows to make your Flow logic reusable and scalable.
DML statements should not be included in the loops: SOQL and DML in Salesforce is bound by “Governor Limits”. If a large amount of SOQL and or DML calls are made in a short amount of time, you can run into a Governor Limit Exception. This rule minimizes the chances of this by letting the user know when they are calling these in a loop.
Avoid creating nested loops in flows: Nested loops within your Flows can cause them to become unreadable, inefficient, and complex. Consider using Invoked Actions to clean up complex Flows.
Document Flows and the flow components: Flows should have adequate documentation. Any flow elements without a description should have a violation thrown independently.
Avoid Hard-Coded Values in Flows: Hard-coded values in flows can lead to unexpected output and make maintenance difficult. Instead, Get Records can be used for the respective object using the DeveloperName. If you’re creating criteria in an entry condition, you can reference DeveloperName (API Name) fields with a formula.
Flows Should Include Fault Paths: Fault paths are a way to handle errors that may occur in your flow. Depending on the Flow and its purpose, errors can be logged, show an error screen, or send an email of the failure to a group of users. Flows should include Fault paths to ensure that all errors are handled appropriately.
Flow Naming: Standardized naming conventions allow an organization's flows to be clean, maintainable, and readable. This rule enforces standard naming conventions for Flows and Domains.
Flow Variables & Resources Naming: Standardized naming conventions allow an organization's flows to be clean, maintainable, and readable. This rule enforces standard naming conventions for Variables, Formulas, and Choices.
Flow Interaction Naming: Standardized naming conventions allow an organization's flows to be clean, maintainable, and readable. This rule enforces standard naming conventions for Screens, Actions, and Emails.
Flow Logic Naming: Standardized naming conventions allow an organization's flows to be clean, maintainable, and readable. This rule enforces standard naming conventions for Decisions, Assignments, and Loops.
Flow DML Naming: Standardized naming conventions allow an organization's flows to be clean, maintainable, and readable. This rule enforces standard naming conventions for DML operations (Query, Update, Create, Delete).
Migrate Workflows and Processes to Flows: Process Builders and Workflows are being phased out over the coming year. In Winter '23 the ability to create new Workflows will be turned off, in Summer '23 the ability to create new Processes with Process Builder will be turned off. It is recommended that these Processes and Workflows be migrated to Flows.
Use Fast Field Updates: If a flow is only updating the record that triggered it, it should be using the Fast Field Updates option. This can be up to 10 times faster than the more flexible Actions and Related Records Flow.
Get Records Should Be Filtered: This rule mandates the usage of at least one filter in the Data element "Get Records" within Salesforce Flows. Enforcing this rule will encourage flow designers to think critically about their data retrieval needs and apply relevant filters, reducing the risk of performance bottlenecks and unoptimized queries.
Unused Flow Variables: Consider removing unused Flow variables to increase performance and readability.
Missing Null Handler After Get Records in Flow: By implementing a decision element to validate the result of the Get Records operation, we can proactively identify and handle cases where no data is retrieved. This allows us to avoid potential null reference errors and prevent unexpected crashes or data processing issues.
Duplicate DML operations in Flows: This rule aims to avoid potential issues caused by duplicate database operations that might occur if users go back and forth between screens, triggering the same actions multiple times.
Flows API Version Is Too Old: This rule identifies flows that are using older API versions. Consider updating the API versions of any flows found.
2. Bug Fixes:
Rule Misfire: Corrected Apex code incorrectly detecting TODOs.
·Task definition changes for SMTP on API and worker on all SaaS instances.
Fix for Copado integration permissions issue
When users run a comparison branch analysis using the wrong base branch (not the master), the application results in a runtime error while trying to view the project analysis page.
Error related to application logic, which leaves existing issues from the target branch being displayed in PR. They filter out only the issues with the RESOLVED state. A code fix was applied to remove one condition and filter out all the remaining issues from the target branch with the decision to remove the condition only if the new feature flag is disabled.
Stack overflow error fix with SOQL Injection Rule
4
PermissionSet - Flows Policy
PermissionSet - Flows Policy gives visibility on access permissions related to Run Flows, Flows Policy, Manage Flow. This violation means that this Permission Set conflicts with your policy for these settings.
5
Profile - API Admin Policy
Profile - API Admin Policy gives visibility on API Admin permissions.
6
Profile - Security Settings Policy
Profile - Security Settings Policy gives visibility on access permissions related to IP Restrict Requests,Manage Certificates,Manage IP Addresses,Manage Encryption Keys,View Threat Detection Events,Profile allows Manage Security Center.
7
PermissionSet - Packages Admin Policy
PermissionSet - Packages Admin Policy gives visibility on access permissions related to Create and Update Second-Generation Packages, Delete Second-Generation Packages, Manage Package Licenses, Download AppExchange Packages, Create AppExchange Packages, Upload AppExchange Packages.
8
PermissionSet - Platform Admin Policy
PermissionSet - Platform Admin Policy gives visibility on Platform Admin permissions.
9
PermissionSet - User Management Policy
PermissionSet - User Management Policy gives visibility on access permissions related to Manage Users, Manage Roles, Assign Permission Sets, Reset Passwords and Manage Internal Users.
10
Profile - Packages Admin Policy
Profile - Packages Admin Policy gives visibility on access permissions related to Packaging2, Packaging2Delete, ManagePackageLicenses, InstallPackaging, CreatePackaging, PublishPackaging.
11
PermissionSet - Data Admin Policy
PermissionSet - Data Admin Policy gives visibility on access permissions related to Manage Data Categories, View All Data, Manage Data Integrations, ModifyAllData , View Encrypted Data, Weekly Data Export, Edit Read Only Fields.
12
PermissionSet - Developer Policy
PermissionSet - Developer Policy gives visibility on access permissions related to Author APEX, Import Custom Objects.
13
Profile - Data Admin Policy
Profile - Data Admin Policy gives visibility on access permissions related to Manage Data Categories, View All Data, Manage Data Integrations, ModifyAllData , View Encrypted Data, Weekly Data Export, Edit Read Only Fields.
14
PermissionSet - Files and Content Policy
PermissionSet - Files and Content Policy gives visibility on access permissions related to Files Connect Cloud.
15
Profile - Platform Admin Policy
Profile - Platform Admin Policy gives visibility on Platform Admin permissions.
16
Profile - Reports and Dashboards Admin Policy
Profile - Reports and Dashboards Admin Policy gives visibility on access permissions related to Create Report Folders, Manage All Private Reports and Dashboards, Create and Customize Reports, Manage Reports in Public Folders, Manage Dashboards in Public Folders, Manage Custom Report Types, Report Builder, Report Builder (Lightning Experience), Run Reports, Create and Customize Dashboards, Manage Dynamic Dashboards, Export Reports.
17
PermissionSet - Permissions Admin Policy
PermissionSet - Permissions Admin Policy gives visibility on access permissions related to Manage Profiles and Permission Sets, Manage Sharing, Multi-Factor Authentication for User Interface Logins, Manage Auth. Providers, Manage Custom Permissions, Manage Login Access Policies, Manage Password Policies, Allow Password Never Expires, Manage Session Permission Set Activations, Exempt from Transaction Security, Waive Multi-Factor Authentication for Exempt Users.
18
PermissionSet - Reports And Dashboards Admin Policy
PermissionSet - Reports And Dashboards Admin Policy gives visibility on access permissions related to Manage All Private Reports and Dashboards, Create and Customize Reports, Manage Reports in Public Folders, Manage Dashboards in Public Folders, Manage Custom Report Types, Report Builder, Report Builder (Lightning Experience), Run Reports, Create and Customize Dashboards, Manage Dynamic Dashboards, Export Reports.
19
Organization - Session Policy
Organization - Session Policy gives visibility on access permissions related to Session Timeout, Enforce login IP ranges on every request.
20
Profile - Flows Policy
Profile - Flows Policy gives visibility on access permissions related to Run Flows, Flows Policy, Manage Flow.
21
Organization - Password Policy
Organization - Password Policy gives visibility on access permissions related to Passwords Expiry, Enforce password History, Minimum Password Length, Password Complexity Requirement, Password Question Requirement, Maximum Invalid Login Attempts, Lockout Effective period, Obscure answer for password resets, Require minimum One Day password lifetime.
22
Profile - Session Policy
Profile - Session Policy gives visibility on access permissions related to Required Session Level and Session Timeout Limit.
23
Profile - Files and Content Policy
Profile - Files and Content Policy gives visibility on access permissions related to Query All Files, Files Connect Cloud, Manage Salesforce CRM Content, Manage Content Permissions, Manage Content Properties.
24
Profile - Permissions Admin Policy
Profile - Permissions Admin Policy gives visibility on access permissions related to Manage Profiles and Permission Sets, Manage Sharing, Multi-Factor Authentication for User Interface Logins, Manage Auth. Providers, Manage Custom Permissions, Manage Login Access Policies, Manage Password Policies, Allow Password Never Expires, Manage Session Permission Set Activations, Exempt from Transaction Security, Waive Multi-Factor Authentication for Exempt Users.
25
PermissionSet - API Admin Policy
PermissionSet - API Admin Policy gives visibility on access permissions related to Modify Metadata Through Metadata API Functions, Bulk API Hard Delete, API Enabled, Multi-Factor Authentication for API Logins, Manage Multifactor Auth - API, Apex REST Services, Access Customer Asset Lifecycle Management APIs, Update Consent Preferences Using REST API.
26
Profile - User Management Policy
Profile - User Management Policy gives visibility on access permissions related to Manage Users, Manage Roles, Assign Permission Sets, Reset Passwords and Manage Internal Users.








Surface active and inactive sprints in one place.
Sync work-item status automatically during merges, commits, and CI jobs.
Enforce release governance with smart-commit patterns and webhook automation.
The ALM Management page (added in ARM 21.6) lives under Admin and lets you register new ALM connections, set integration rules, and manage repository mappings.
Log in to ARM as an admin.
Navigate to Admin > ALM Mgmt.
Click Register ALM on the ALM Mgmt. screen.
Configure the following settings:
For IBMRTC, CA Agile Central, VersionOne, and Azure DevOps:
ALM Name: Enter a name for your ALM connection.
ALM Type: Select the ALM type.
ALM URL: Add the ALM server URL.
Credentials: Specify your credentials. Refer to the section for more info on creating and storing your credential inside ARM.
For JIRA:
ALM Name: Enter a name for your ALM connection.
ALM Type: Select
Click on Test Connection to authenticate your credentials.
Click Save.
Once your ALM is registered successfully, you can view it in the ALM List menu.
Use the AR Comments toggle button to turn off the Jira comments from AR. By default, the Jira comments are ON for newly registered and existing ALMs.
Use the Access Type drop-down list to switch between Standard and OAuth. Click on Re-Authenticate if your credentials have expired. This is only applicable to Jira ALMs.
Log in to ARM as an administrator.
Navigate to Admin › ALM Mgmt.
Click Register ALM.\
Fill the form:
ALM Name – friendly label.
ALM Type – choose the platform.
Field Mapping for Work Item Updates in Salesforce
To enable AutoRABIT to update your Work Items (e.g., User Stories or Bugs) based on commit actions, please configure the following fields from your registered Salesforce Org: \
c. Salesforce Org Select the Salesforce Org from your list of registered orgs where the work item updates should be applied.
d. Custom Object / Work Item Type Choose the Custom Object that represents your Work Items (e.g., User_Story__c, Bug__c). This is where the Work Item ID will be updated.
e. Title Field Map the field that represents the project or feature to which the Work Item belongs. This is usually a custom text field like Project__c.
f. Assignee Field Select the custom field that stores the user assigned to the Work Item. This allows AutoRABIT to track ownership of the User Story or Bug.
g. Status Field Choose the custom field that reflects the current status of the Work Item (e.g., New, In Progress, Ready for QA, Closed). This field can be updated automatically based on the commit action.
h. Comment Field Select the custom field where commit-related comments should be posted. The system will populate this with detailed commit information after the action is performed. 1. Select Post Commit Action Under the Post Commit section, select:
2. Update ALM Work Item Status
Configure ALM Fields Fill in the required fields to ensure the correct ALM Work Item is updated post-commit:
ALM Type: Choose the integrated ALM tool (e.g., Salesforce).
ALM Label: Select the applicable label for this commit operation.
ALM Project: Pick the project or module name (e.g., User Story, Bug).
ALM Work item: Select the Work Item ID you wish to update.
ALM Work Item Status: Choose the new status you want to set (e.g., To Do, In Progress, Done).
Current Status: Shows the status of the item (e.g., In Testing).\
Complete the Commit Click Commit after configuring all required fields. The system will:
Perform the commit action.
Post-commit, automatically update the ALM Work Item to the new selected status.
Add relevant commit information to the comment field (if configured), including metadata, user, and validation results.
Sample Outcome Post Commit Comment Format: The selected Work Item will reflect the updated status in your ALM tool and include commit metadata like:
[Message] [************]# Saas tool Integration-2
[Repository] **********;
[Branch] 18235_test
[Revision] 3637289
[Committed by] ******@.com
[Committed metadata members] {Apex Class=[A000, A0000]}
[Pre-validation Results]
Label Name = **********.**
Apex Test Results = NA
Static Analysis = NA
Deployment Org = NA
Overall Validate Deployment Status = NA
Approved By = .@***.com
By default, we do not display the work items from the inactive sprints; however, if you want to view the hidden items, you can do so from this section.
Select the following checkbox to view the work items from the inactive sprints: Display work items from inactive sprints (we recommend setting up global filter criteria if are enabling this)
Enable global filter criteria on work items: This checkbox allows you to specify filter criteria.
You can select which fields are displayed by selecting the necessary column/field. However, you can refine the list of work items displayed by configuring a worklist filter.
Repeat these steps for each field if you want to set filter criteria.
Click Save Settings.
Define the pattern AutoRABIT uses to parse work-item references in commit messages—for example:
Enable auto update on webhook – reveals a webhook URL you can add to your VCS so external commits update the ALM automatically. See setup guides here.
Optionally sync external smart commits made outside AutoRABIT.
Repository mappings let AutoRABIT update ALM work-item status after a successful merge.
Choose the version-control Repository.
Select the Source Branch (click Register here if it’s missing).
Pick the ALM Project.
In ALM Work Item Status, define:
Work Item Type
Current status
Target status after merge
Click Save.
Suppress ALM email noise by listing addresses in Notify exception status updates to.
Minor
New rules for Salesforce flows and one rule misfire corrected.
Minor
Code fixes
Minor
Code fixes
Minor
Code fixes
Minor
Code fixes
Sept 2023
Major
Europe + Australia only

git commit -m "\[PROJECT-123] add README"

Access Type:Select one of the following:
Standard: Add the ALM URL and specify your Credentials.
OAuth: Select the access type as OAuth, and click on Validate & Save. You will be redirected to the ALM's website to authenticate your credentials and grant permission.














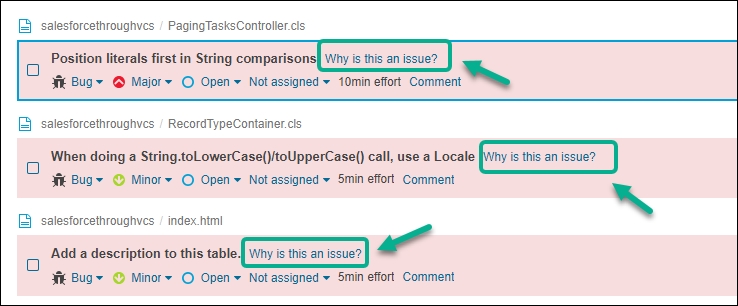
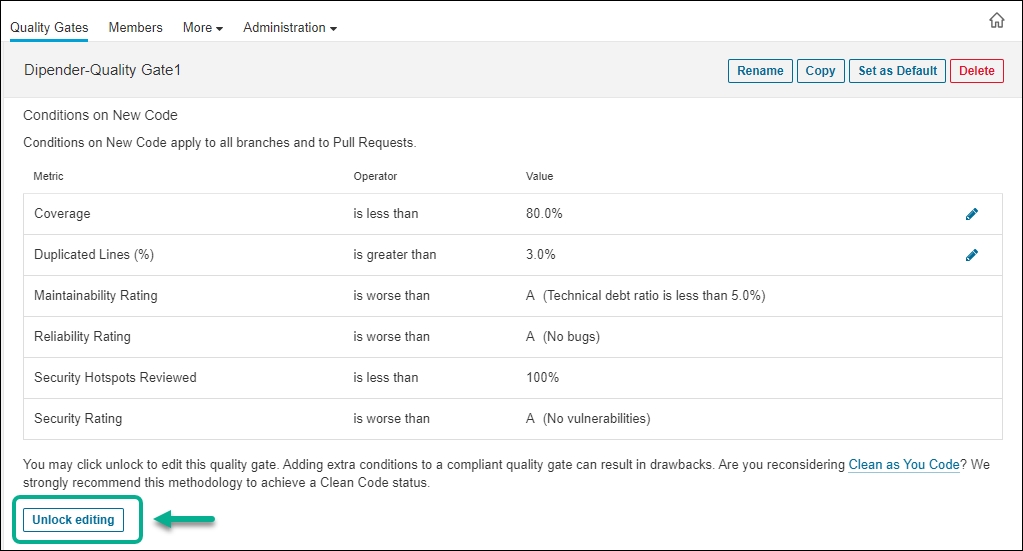
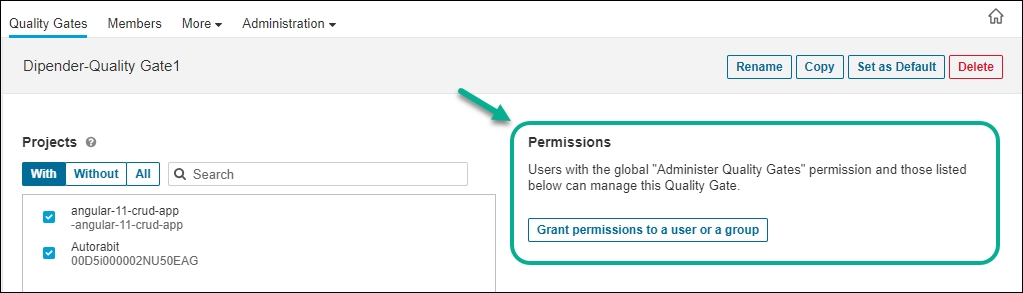
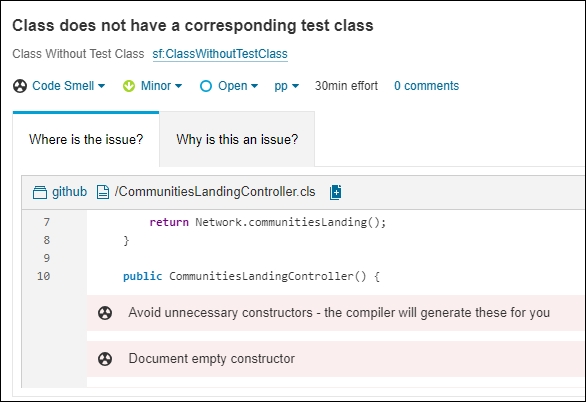
You can create, edit, and view user account details as an Org administrator. Admins can view their account details too.
Hover your mouse over the Admin tile and select My Account.
The My Account page appears. You’ll then be presented with a screen divided into different sections, as depicted below:
The Account Contact Details section contains your account's primary information and your subscription period with ARM.
Subscription Types are set up to match your organization's requirements. View the current subscription type and list of modules granted by ARM based on your subscription. Click on View Models to view the complete subscription model.
Single Sign-On (SSO) is an authentication process that allows a user to access multiple applications with only one set of credentials. ARM uses the secure and widely adopted industry-standard Security Assertion Markup Language 2.0 (SAML 2.0), which means our implementation of SSO integrates easily with any large identity provider that supports SAML 2.0.
SAML-based SSO enables two-way communication between an authentication server (the Identity Provider) and an application (the Service Provider). So, your account must be set up to declare who will be the authentication server and how the communication must work.
Using the information you gathered from your IdP (the Identity Provider), fill in the below details:
Entity ID: String that uniquely identifies your IdP (your IdP generally provides it).
Uploaded File Name: You must upload the XML file generated from IdP. (For more information, please refer to the Integration section on.
Disable login with ARM credentials:
How to override single sign-on (SSO)?Sub-users registered to that organization cannot log in to the ARM application using the standard (username + password) approach if the Disable login with AutoRABIT credentials checkbox is selected. If the org admin wants to override the SSO configuration for an individual user or group of users, he can do so under the Admin > Users section. Uncheck the Enforce SSO boxes after selecting the users from the list. Save the SSO Configuration by clicking Save.
The admin can add different mail extensions based on the organization's requirements in this section.
This allows new users to sign up for the ARM account by giving their mail extensions.
This section lists various plugins that are configured in ARM. Based on the organization's requirements, admins can select the desired plugins to be used and register by giving the correct credentials.
In addition to this, the admin can select the desired browsers to execute the selenium test cases. Selenium cannot automate desktop applications; it can only be used in browsers.
Browsers Supported:
Google Chrome 12+
Internet Explorer 7+
Firefox 3+
Developers must select the appropriate baseline branch to compare against. If they don't, a new branch will be created, which causes problems.
Admins can configure the default baseline branches for CodeScan and SonarQube SCA plugins in the My Account section. This resolves the confusion developers previously faced when selecting baseline branches for SCA and. It also helps Admins control the default baseline branches.
Configure the baseline branches
Select CodeScan or SonarQube.
Select Project from the dropdown list.
Click on the Select Default Branch
With the current release, users can set the global criteria to enforce Static Code Analysis (SCA) tools across CI jobs and merge jobs. Based on the priority set, the build will be successful only if the criteria are met. The build will only succeed if the Apex Classes, Triggers, and Visualforce pages pass the priority set.
Here the admin can specify specific evaluation criteria for which the commit will get reviewed before being committed to the version control branch.
Auto reject commit after XX days
Auto rejects an approval for pre-validation commit after the days mentioned here.
Enable criteria-based Review Process
Select the Enable criteria based Review Process checkbox to enable the commit criteria.
Next, choose the approval criteria based on your requirement:
Enable file comparison reports: When selected, this generates a code difference report upon completion of the commit operation.
Should pass validation criteria for Static Code Analysis: Select this option if you would like to run a static code analysis tool to identify potential software quality issues before the code moves to production.
Select the SCA tool according to your requirements.
Auto commit on Approval
Once the reviewer has approved the changes, or if you have opted to auto-approve upon successful validation, the commit process is automatically pushed to the destination branch.
Admins are now able to configure the approvals process for the custom deployment module.
By Admin → My Profile -> Deployment Approval Settings.
Select the Salesforce Org from the drop-down menu, which requires approval before deployment. (This menu provides a list of Orgs that you have already configured in SF Org MGMT.)
You can also configure the approval process for multiple Orgs.
Click on the drop-down menu to select the approvers for Level 1 and Level 2. The list will contain only users who can access the deployment module. Note : The App doesn't allow you to select the same approvers for Level 1 and Level 2.
Here the administrator can specify specific evaluation criteria on which the merge will be reviewed before committing to the version control branch. The New Merge screen reflects the same option based on the criteria selected.
Select the Enable criteria based Review Process checkbox to enable the merge setting.
Merge Criteria
Enable file comparison reports: When selected, this generates a code difference report on completion of the merge operation.
Should pass validation criteria for Static Code Analysis: Select this checkbox to run one or more SCA tools to identify potential software quality issues before the code moves to production.
Should pass mock Deployment:
ARM supports all the metadata types based on the Salesforce API Version. ARM now supports the Salesforce API 64.0 version, which means it can support any Salesforce standard or custom objects that require Salesforce API version 64. The newly supported Salesforce objects for each API version can be found .
Select the API version to see the supported metadata types and avoid errors while accessing Salesforce orgs in Version Control, CI Jobs, Deployment, or SFDX modules.
Configuration for recordTypes picklistValues: This topic is covered separately. to go directly to the mentioned topic.
Configuration for Translations: Options to choose the configuration for the LabelTranslations, i.e., either replace or append. When selecting the Replace option for the Configuration for LabelTranslations option for every EZ-commit operation, if the Label Translation has no custom label metadata type, it will override the LabelTranslations in Version Control, even if it has more than one custom label metadata type value. For the Append option, instead of overriding the custom label metadata types, it keeps adding to the existing one.
Rollback Settings
Ensure you exclude them to avoid retrieving unwanted metadata types during deployment or commits rollback.
Profile/PermissionSets Settings
This section pertains to granting or revoking permissions to the Profiles/PermissionSets of any org. Based on the permission granted or revoked, the same is affected after committing the custom object in the Version Control.
What is a Profile?
Profiles define how users access objects and data and what they can do within the application. When you create users, you assign a profile to each one.
What are Permission Sets?
A permission set is a collection of settings and permissions that give users access to various tools and functions. Users can have only one profile, but they can have multiple permission sets. You can assign permission sets to different users, regardless of their profiles.
Create a Profile or Permission Set permissions
Create permission sets to grant access among logical groupings of users, regardless of their primary job function. For example, if you have an Inventory custom object in your org. Many users need Read access to this object, and fewer users need Edit access. You can create a permission set that grants Read access and assign it to the appropriate users. You can then create another permission set that gives Edit access to the Inventory object and assign it to the other group of users.
Click the New button.
Select the Salesforce Org.
Click either Get Profiles or Get PermissionSets
Additional configuration for "Field Permissions" and "Object Permissions" settings
Field Permissions represent the field-level permission for users assigned to a profile.
Object Permissions represent a user's access to custom objects.
Vlocity integration with ARM allows you to retrieve and deploy Vlocity metadata in the same way as for the Salesforce metadata, and commit the changes either to the repository or to a Version control branch.
Vlocity Version Supported: v1.17.1
Integrate Vlocity as a plugin in ARM
In the Vlocity Configuration Settings section, select the Enable Vlocity checkbox.
Next, you must select the various parameters required to integrate Vlocity with ARM:
Compile On Build:
After logging in, a user establishes a session with the ARM platform. As an admin, you can control when an inactive user session expires. The default session timeout is 30 mins of inactivity. When the session timeout is reached, users are prompted with a dialog that allows them to log out or continue working.
In this section, the admin can define the period for which data is retained by ARM in the history tables.
Clearing historical and irrelevant data from the database helps prevent the application from lagging, resulting in better performance in all modules. The default retention period is set as 12 months. Data older than 12 months will be automatically cleaned. Admins can later change it to 6 months or 3 months.
This is applicable to the historical data on the following pages:
Deployment history
CI Job History
Org Sync History
Commits page
Other options:
Click the icon to add a project.
Click theicon to remove a branch from a project.
Click theicon to delete the project completely.
Click Save after selecting, adding, or deleting the required projects and corresponding branches.
Select the Auto reject commit process if the criteria are not met checkbox to auto-reject the commit if the set criteria are not met.
Auto approve on commit validation success: If all the criteria selected under Enable criteria based Review Process are successfully validated, selecting this checkbox will automatically approve the commit.
Click on Save to enable the approval process for deployments.
Disable Merge Self Approval: This option allows the Admin to prevent users who have committed to a merge request from approving it.
Auto commit on Approval: This option allows developers to work on their feature branches, and after review (approval), it gets automatically committed to the trunk. View the commit revision information when you click the Revisions link.
Enable Merge Approver: Enables the pprover to perform enforced code review by requiring specified people to approve a merge request before it can be unblocked for merging. Please set the number of necessary approvers before open merge requests can be merged under the Approval Levels drop-down box. The minimum approval level can be 1.
Auto approve on merge validation success: If all the criteria selected under Enable criteria based Review Process are successfully validated, selecting this checkbox will automatically approve the merge. The merge will appear to have been approved by ARM. If the user has selected multiple approver levels, both levels will automatically be approved upon successful validation.
Notify All Criteria Overwrites To: The email address(es) specified here will receive an overwrite email notification every time the user tries to overwrite the evaluation criteria set in the Merge Settings section and tries to merge the files to a branch.
Configuration for running delta on RecordType Picklist values: On selection, this allows you to check delta on RecordType Picklist values during a Deployment.
Packaging and Deployment Settings: Several options can be configured in this section:
Manageable States: In Salesforce, the ManageableState attribute indicates the status of a component within a package, reflecting its lifecycle stage and editability. The possible states are:
Beta: The component is in a managed package version marked as beta, suitable for testing but not for production use.
Released: The component is in a managed package version officially released for production use.
Deleted: The component has been deleted from the package.
Deprecated: The component is marked as deprecated, indicating it's outdated or should no longer be used.
Unmanaged: The component isn't part of a managed package, allowing full editing and deletion.
Installed: The component is part of a managed package installed in a subscriber's org, and it can't be edited or deleted by the subscriber.
InstalledEditable: The component is part of an installed managed package but can be edited by the subscriber.
DeprecatedEditable: The component is deprecated but remains editable.
b. Include Default Apex Tests For Run Tests Based On Changes: When selected, the default configured tests are added to the set, even if Test classes or Apex Class Apex Triggers are unavailable. Apex Test Level executes as RunSpecifiedTests. However, if the checkbox is unchecked, no default tests are added, and no Apex Test Level is set. Salesforce default behavior is expected in such cases.
c. Enable Delta on PermissionSets: Per the Salesforce behavior, for Salesforce API 40 or later, all PermissionSets are replaced with the latest changes. However, when the Enable Delta on PermissionSets checkbox is selected, the PermissionSets are retrieved from the source org and will append with the latest changes in the deployment package.
d. Include/Exclude Metadata Types: Be sure to exclude them to avoid retrieving unwanted metadata types during the deployment or merge.
Get Profiles will fetch all the profiles available in selected Salesforce Orgs.
Get PermissionSets will list all permission sets available in Salesforce Orgs.
Based on the above selection, choose either the Profile or Permission from the list.
Next, grant or revoke the permissions for the selected Profiles/Permission Sets.
viewAllRecords
Indicates whether the object referenced by the object field can be read by the users assigned to this profile (true) or not (false), regardless of the sharing settings for the object.
Compile On BuildAuto Update Settings: This option ensures you have the latest Data Pack settings before each export and deployment. This check is quick, and we recommend that you allow it.
Separate Matrix Versions: Add the ability to export matrix versions separately.
Local Compilation: To perform a local compilation of FlexCard and OmniScript metadata types, select this checkbox and enter the Access Key of Vlocity's private NPM repository to load the OmniStudio LWC compiler and deploy the compiled objects.
NoteIf you do not have the NPM repository Access Key, you can request one from your Vlocity customer representative at https://repo.vlocity.com/repository/vlocity-public/, by filing a support case with the subject Request for Access Key to Vlocity's Private NPM Repository.
MaxDepth: MaxDepth decides the level of dependencies that will be executed while fetching and committing vlocity components. By default, MaxDepth is set to -1.
When MaxDepth Values is set to -1 means, it will execute all-level dependencies of selected data pack record
When MaxDepth Values is set to 0 means, it will execute only selected data pack record and
When MaxDepth Values is set to 1 means, it will execute only first-level dependencies of the selected data pack record.
Data Pack Types: This gives you an option to choose your specific Vlocity components that will be committed to your destination org/branch.
Click Save.
EZ-Commits history
Prevalidation commits history
Reverted commits history
Merges history
Prevalidation merge history
Merge Requests history
External Pull Requests page
Branching baseline page
Change the Labels page
Commit Labels
Release Labels
ALM Labels
Editable
Indicates whether this field is editable (true) or not (false).
Readable
Indicates whether this field is readable (true) or not (false).
allowCreate
Indicates whether the object referenced by the object field can be created by the users assigned to this profile (true) or not (false).
allowDelete
Indicates whether the object referenced by the object field can be deleted by the users assigned to this profile (true) or not (false).
allowEdit
Indicates whether the object referenced by the object field can be edited by the users assigned to this profile (true) or not (false).
allowRead
Indicates whether the object referenced by the object field can be seen by the users assigned to this profile (true) or not (false).
modifyAllRecords
Indicates whether the object referenced by the object field can be read, edited, or deleted by the users assigned to this profile (true) or not (false), regardless of the sharing settings for the object.



























Release Date: 18 July 2025
CodeScan Self-Hosted (versions 25.0.2 [Tiger v4] and 25.1.1 [Eagle v4]) are comprised of the following 19 components:
5 Enhancements
2 New Rules
12 Fixes
Component details are listed in their corresponding sections within this document.
1. Enhanced rule “vf:AvoidJavaScriptScriptlets” by adding a new parameter to the rule
Historically, CodeScan has offered our “Avoid JavaScript Scriptlets” rule to inspect customer’s code and flag where there JavaScript Scriplets.
With this release, a new parameter was introduced to allow users to choose whether to include or ignore violations related to code supporting the Lightning functions within script.
Parameter Name: ignoreSupportingCode
Type: Boolean (true or false)
Default: false
Description: This option allows users to ignore violations related to code supporting the Lightning functions within script. By default, it is set to false.
Verified the below scenarios for rule vf:AvoidJavaScriptScriptlets and report that all scenarios are working as expected.
Validated the rule with LightningFunctions and set the default value false then user is able to see the violations.
Validated the rule with LightningFunctions and set the value true then user is not able to see the violations which is expected.
Validated the rule without LightningFunctions then user is able to see the violation which is expected.
Validated the rule by setting the parameter ignoreSupportingCode as false/true working as expected.
1. Updated description for Deprecated rules
Historically, CodeScan has deprecated rules over time. However, we recognize that we can be clearer about why the rule is being deprecated. In this release, we have initiated this practice (and plan to adhere to this practice in the future).
1.Update the description of deprecated Apex Rule “Use System.assertEquals instead of System.assert“ and key”sf:UseAssertEqualsInsteadOfAssertEquality” with the following:
This rule detects unit test assertions in object references equality. Instead of using System.assert combined with "==" as an equality operator, these assertions should be made by more specific methods, like assertEquals.
This rule has been deprecated, as Salesforce recommends using the Assert class for unit tests. Please remove this deprecated rule from your custom Quality Profile and instead add the rule sf:UseAreEqualInsteadOfAssertBoolean.
2.Update the description of deprecated Apex Rule “Use System.assertEquals instead of System.assert“ and key”sf:UseAssertEqualsInsteadOfAssert” with the following:
This rule detects Unit test assertions in object references equality. Instead of using System.assert combined with ".equals()" as an equality check, these assertions should be made by more specific methods, like assertEquals.
This rule has been deprecated, as Salesforce recommends using the Assert class for unit tests. Please remove this deprecated rule from your custom Quality Profile and instead add the rule sf:UseAreEqualInsteadOfIsTrue
3.Update the description of deprecated Apex Rule “Use System.Assert instead of System.assertEquals“ and key”sf:UseAssertInsteadOfAssertEquals” with the following:
When asserting a value is the same as a boolean literal, use System.assert, instead of System.assertEquals.
This rule has been deprecated, as Salesforce recommends using the Assert class for unit tests. Please remove this deprecated rule from your custom Quality Profile and instead add the rule sf:UseIsTrueInsteadOfAreEqual
4.Update the description of deprecated Apex Rule “Unnecessary Parentheses“ and key”sf:UnnecessaryParentheses” with the following:
Sometimes expressions are wrapped in unnecessary parentheses, making them look like function calls.
This rule has been deprecated. Please remove it from your custom Quality Profile and instead add the rule sf:UselessParentheses as a best practice for code styling.
2. Enhancement to CodeScan Rule “URL Redirection to Untrusted Site” {sf:OpenRedirect}
CodeScan has traditionally used this rule to check against redirects to user-controlled locations. This is important because untrusted input could cause an attacker to redirect the user to a malicious site thereby allowing the attacker to launch a phishing scam and steal user credentials.
However, our existing rule did not specifically check for the use of Network.forwardToAuthPage.
This rule has now been enhanced with this logic and we have verified that users are now able to see the violation for the use of both Network.forwardToAuthPage and PageReference.
More details regarding the Network class can be found here:
1. Enhanced rule “Avoid Untrusted/Unescaped Variables in DML Query" to account for potential SOQL injections when “queryWithBinds” is used.
Historically, CodeScan has offered our “Avoid Untrusted/Unescaped Variables in DML Query” rule to inspect customer’s code and flag where there are SOQL Injection possibilities. Recently, one of our customers had performed a test and expected this rule to flag an issue in their code, but it did not. We determined that the rule should be enhanced for when “queryWithBinds” is used.
Our engineering team utilized specifications within Salesforce documentation (specifically, ) in order to consider only the query for executed with queryWithBinds() for vulnerability check and violation, avoiding the other parameters such as: (Map, accessLevel) . Database.queryWithBinds(query, bindVariablesMap, accessLevel)
Example:
Verified that after the rule enhancement was engineered, users are able to see the violation for rule “Avoid Untrusted/Unescaped Variables in DML Query” as expected.
1. Enhanced rule “Controller Naming Convention” for Apex and Visualforce
Some customers are reporting that CodeScan is flagging violations on components that should not be flagged (i.e., SandboxRefreshAdminController)
This issue is remediated in this release.
We validated the fix by:
Creating a class file in salesforce org using UI and name the controller like in example.
Creating a vf page in salesforce org with the controller attribute like shown in the example.
Setting parameters for controller naming in CS, try the parameters with different cased letters ex: ConTroLLer etc.
After scanning false positives should not be visible
1. Server Side Request Forgery
This is a rule that checks for any changeable inputs to a url string in a method that returns a PageReference.
Type: Vulnerability Severity: Critical Name: Server Side Request Forgery (SSRF) Key: ServerSideRequestForgery Message: Sanitize input to avoid possible SSRF Description: This rule identifies potential Server-Side Request Forgery (SSRF) vulnerabilities by detecting unsafe URL construction and external network requests that could allow an attacker to manipulate server-side network calls.
Server-Side Request Forgery (SSRF) occurs when an attacker can influence the server to make arbitrary network requests, potentially accessing internal resources, sensitive endpoints, or bypassing security controls.
Input can be cleansed by using Id.valueOf, Date.valueOf, etc. Or escaped using String.escapeSingleQuotes().
Parameters Name: sanitizationMethod Description: A comma separated list of custom methods that provide input sanitization.
CWE: 918
Test Cases with Violations 1. Validated direct embedding of user input into a URL without sanitization, resulting in a violation (SSRF) as expected.
Validated unescaped dynamic input into URL, resulting in a violation (SSRF) as expected.
Validated that one parameter is sanitised but the other is not sanitised, still resulting in a violation (SSRF) as expected.
Validated concatenated unsafe dynamic parameters in a URL, resulting in a violation (SSRF) as expected.
Test Cases with No Violations
1. Validated input sanitized using Id.valueOf, resulting in no violation as expected.
Validated input escaped using String.escapeSingleQuotes, resulting in no violation as expected.
Validated that the URL starts with "/" ensuring an internal redirect, resulting in no violation as expected.
Validated date validated using Date.valueOf, resulting in no violation as expected.
Resource Injection
Prior to this new rule, CodeScan did not catch resource injection in Apex. This is very similar to our new rule “Server Side Request Forgery” (also included in this release)
However, there are some basic things that make it resource injection and not SSRF. In this example: public PageReference init(){ AccListString = 'INIT'; BaseObjId = system.label.MY_Label; return null; }
public PageReference prepareAccs(){ String newUrl = '/apex/maps__Maps?baseOjectId='+BaseObjId+'&recordIds='+AccListString; PageReference p = new PageReference(newUrl); p.setRedirect(true); return p; }
Here, we are looking at resource injection because the URL is internal (starts with / ) This rule should find any external variables that are used to create dynamic internal URLs.
Acceptance Criteria
Type: Vulnerability Severity: Critical Name: Resource Injection Key: ResourceInjection Message: Sanitize input to avoid possible resource injection Description: This rule identifies potential resource injection vulnerabilities by detecting unsafe URL construction for internal network requests.
Resource injection occurs when user-controllable data is used to specify a resource identifier without proper validation.
Input can be cleansed by using Id.valueOf, Date.valueOf, etc. Or escaped using String.escapeSingleQuotes().
See:
- Improper Control of Resource Identifiers ('Resource Injection')
Tags: cwe
Remediation Time: 10 minutes
Parameters: Name: sanitizationMethod Description: A comma separated list of custom methods that provide input sanitization.
CWE: 99
Verified the following scenarios are all working as expected
Verified that sanitizing both BaseObjId and AccListString before URL building prevents violations.
Verified that validating BaseObjId using Id.valueOf() ensures the ID is valid and safe to use in URLs.
Verified that input AccListString validated with regex and sanitized prevents violation.
Fixed issue with the rule “vf:UnescapedAttributes vulnerability” {where false positive violations were being flagged}
CodeScan suggests the remediation for this issue is to use JSENCODE() to escape values. However, some customers reported that when this is added to their code, the issue was still being flagged as a violation. We validated the fix by:
• Verified the updated description and example under rule: vf:UnescapedAttributes vulnerability
• Verified that Rule is throwing violation as expected
This CodeScan rule was updated with the following changes:
1. Changed the description to the following:
Reflected Cross-site Scripting (XSS) occurs when an attacker injects browser executable code within a single HTTP response.
Using unescaped parameters can be a security risk. c:* and apex:* attributes are not checked unless they are known to cause problems. You can check other attributes by adding them to the configuration for this rule.
In Visualforce, escape methods such as JSENCODE can be used to sanitize variables as shown below.
For Aura components, sepcifically aura:unescapedHtml, make sure to sanitize variables in controllers before using them. This component is intended to output properly sanitized HTML from a trusted source. If properly handled, mark the issue as Resolved: False Positive/Won't Fix.
2. Added the following Aura Example Bad Scenario:
Example :
<aura:component>
<aura:unescapedHtml value="{!v.htmlstring}"/>. //Bad: not recommended.
</aura:component>
1. Fixed issue with the rule “Field Level Security Vulnerabilities” (sfmeta:PageLayoutNaming) for classes using “Without Sharing” {where false positive violations were being flagged}
Some customers have reported an issue with CodeScan's reporting of "Permissions should be checked before accessing resource" vulnerabilities in our Apex codebase, specifically within classes that are declared without sharing.
The without sharing keyword in Apex classes causes the code to execute in system context, bypassing standard Salesforce sharing and field-level security checks. This is intentional for certain system-level operations and utility classes within our application.
However, CodeScan is flagging fields within these without sharing classes as vulnerabilities, stating "Permissions should be checked before accessing resource." This is creating an inflated number of false positives and incorrectly portraying our code's security posture.
CodeScan is designed to identify potential security issues; however, in the context of without sharing classes, these field-level security checks are redundant and misleading.
As such, the rule update in this release enables CodeScan to recognize that when a class is declared without sharing, field-level security checks are irrelevant, and the "Permissions should be checked before accessing resource" rule is suppressed for fields within without sharing classes.
Note that a new parameter has been added to this rule to Ignore Without Sharing
Name: ignoreWithoutSharing Message: When this parameter is true, this rule ignores Field Level Security issues in all without sharing classes. Default: false
Appropriately, CodeScan is flagging violations properly when “with sharing” is used.
1. Fixed Deprecation Warning associated with sonar.login
Some customers were reporting that they were
receiving deprecation warnings in their scans indicating that the use of sonar.login is deprecated, and that instead, going forward, authentication should be done using sonar.token.
This issue has been remediated in this release. CodeScan now supports both sonar.login and sonar.token for authentication during Codescan analyses. Top of Form
Verified the below plugins by using sonar.token and sonar.login parameters in the sonar command and sfdx; both scenarios are working as expected.
SFDX -@salesforce/cli/2.61.8
Sonar-scanner - 5.0.1.3006V
Validate Project analysis through above plugins
Validate branch analysis.
2. Fixed issue with the rule “sf:AtLeastOneConstructor”
The rule sf:AtLeastOneConstructor is currently not throwing violations in scenarios where both the class and methods are present; however, it should be violated.
Additionally, the current implementation flags only non-static classes without constructor. As part of the fix, classes with at least one non-static member (method or field) will also be flagged.
Also, the description will be updated from “Each class should declare at least one constructor" to “Each class should declare at least one constructor. Classes with solely static members are ignored."
Verified rule: sf:AtLeastOneConstructor for the below scenarios, and confirmed users are able to see the violations as expected Below are the scenarios for which violations should be throw as per the rule 1. Missing constructor with all non-static methods
Missing constructor with a mix of static and non-static methods
Below are the scenarios which should be ignored as per the rule
Interface with method declarations
Enum with constant values
Below are the scenarios for which violations should not throw
Missing constructor, but all methods and fields are static (utility class)
Class with an explicit constructor
1. Fixed 2 issues with our SOQL Injection rule
We have discovered that the issues flagged disappear on different lines; we have also discovered that CodeScan doesn’t find the fflib method escape.
These 2 issues are remediated in this release.
Verified the SOQL Injection rule and confirm users are able to see the violations for the rule as expected.
1. Fixed issue with rule “sf: FieldLevelSecurityRule”
During maintenance testing, we discovered that this rule was triggering the null pointer exception when parsed through the trigger files. In the rule logic it was searching for relevant ASTClassOrInterfaceBody to get all the constructors in that class. Since triggers don't have constructors, control flow proceeds further if we get a non-null node for ASTClassOrInterfaceBody. We updated this rule to parse the trigger files by adding extra logic to find the Trigger specific nodes (TriggerBodyDeclaration etc).
We tested the fix to the Null pointer Exception with sf: FieldLevelSecurityRule and verified we are now no longer able to see the Null pointer exception for the trigger files in the logs (as expected).
1. Fixed issue with rule “RequireDescriptionComponent”
Some customers reported that the CodeScan rule “RequireDescriptionComponent” rule was not working for custom fields on standard objects.
This issue has been remediated in this release. Previously, CodeScan offered a rule “sfmeta:RequireDescriptionField” which had been deprecated for this updated rule. But the updated rule was not designed for standard objects. When we tested the logic of the deprecated rule, we found that it could be used for reference for this update to the new rule “RequireDescriptionComponent”
The rule enhancement was verified via the below scenarios: 1. Verified Custom Field on Standard Object – Missing Description
Verified Custom Field on Custom Object – Missing Description
Verified Standard Fields on Standard Object – Missing Description
Verified Custom Field on Standard Object – With Description
Verified Custom Field (With Description) on Custom Object (Without description)
1. Fixed issue with CodeScan’s APEX parser
Some customers reported that the CodeScan parser was incorrectly flagging valid Apex code using the UPDATE AS SYSTEM syntax as a parsing error. This was occurring because the parser doesn't recognize the AS SYSTEM portion of the UPDATE statement, leading to a ParseException and preventing accurate code analysis.
This issue has been remediated with this release.
We had previously verified the Parsing error in APEX Code for DML queries if user using UPDATE AS SYSTEM syntax would throw the parser exception. With this fix, users are now able to see the violations as expected for the file.
Verified the below queries in Apex code that users do not get any Parser errors; instead the updated CodeScan parser is working as expected.
INSERT AS SYSTEM
DELETE AS SYSTEM
UNDELETE AS SYSTEM
UPDATE AS SYSTEM
1. Fixed issue with rule “Avoid running Soql and DML inside loops” {sf:AvoidSoqlInLoops}
Some customers reported unexpected behavior in this rule, producing false positives.
The root cause of the false positives is that when a method of an object is invoked within another method, and both methods share the same name, the current rule implementation incorrectly interprets this as a recursive call and subsequently triggers a violation. Further, the Stack Loop trace is indefinite.
This has been remediated in this release. The updated rule logic now handles these edge cases by checking for method image to be exactly the same (method != diffObj.method).
We have verified the fix across related and existing test cases and edge conditions by confirming that if a method of an object is invoked within another method, and both methods share the same name, the user will not see the violation (as it is false positive).
Verified the the rule sf:AvoidSoqlInLoops confirming that if a method of an object is invoked within another method, and both methods share the same name, the user will not see the violation as it is false positive.
However, there’s more to this issue and fix! A scenario which was earlier covered stopped working as expected as a result of the fix made above.
As such, an additional update to the rule implementation was made to accommodate both scenarios (the pre-existing condition but also indefinite stack loop trace).
Verified the Fix for rule sf:AvoidSoqlInLoops via several scenarios, including:
Verified – SOQL inside a method (not directly in a loop) — no violation as expected
Violations Expected for the below scenarios
Verified SOQL directly inside a for loop — got violation as expected
Verified SOQL inside nested if blocks within a loop — got violation as expected
Verified SOQL inside a try/catch block within a loop — got violation as expected
Verified SOQL in a method (or recursive call) invoked from a loop — got violation as expected
Verified SOQL in static helper method called from a loop — got violation as expected
Verified SOQL inside a while loop — got violation as expected
Verified SOQL inside a do-while loop — got violation as expected
Verified SOQL directly inside System.debug() within a loop — got violation as expected
No Violations Expected for the below scenarios
Verified Bulkified SOQL outside the loop (e.g., IN :ids) — no violation as expected
Verified SOQL in deep conditional logic but not inside a loop — no violation as expected
Verified SOQL inside try/catch block, not inside a loop — no violation as expected
Verified SOQL in method not called from a loop — no violation as expected
14. Verified SOQL inside constructor called from a loop — no violation (as expected for shallow analyzers)
1. Fixed issue ARM users recieving an error: “Component can't be null” while running a CodeScan analysis from ARM.
The issue is occurring in the SFDX retrieval. From ARM, when the user commits only the fields (or, for example, lookup fields), the .object-meta.xml is not retrieved. As a result, the retrieved file structure differs from what was expected. After analysing the rule’s implementation, it was found that the rule does not check if the .object-meta.xml file exists first and forcibly tries to throw the violation on the file. Hence, the "component can't be null" error is thrown. This required an engineering fix in the rule.
Note: The issue lies in one of the common methods many rules use, so this error is not confined to these two rules.
Other rules that use this method include:
With this fix, users are now able to see the violations for all 7 rules when running a CodeScan analysis from the ARM side using the CodeScan plugin:
Rules:
sfmeta:CrossObjectFormulaOveruse
sfmeta:ObjectLookupsOveruse
sfmeta:RelationShipOveruse
sfmeta:ExternalIdOveruse
sfmeta:RollUpOveruse
sfmeta:LimitCustomFields
sfmeta:nCinoFieldHistoryTracking
Verified by committing only specific fields and triggering SCA analysis — violations appeared as expected.
Ran analysis for the entire Salesforce org, including objects — violations were also detected."
1. Fixed issue with rule: “sf:AvoidGlobalModifier” {where CodeScan is flagging a false positive}
Some users have reported that CodeScan was throwing an error related to usage of a global class on the highlighted line, where the inner class CustomWrapper is defined.
Since the GET() is annotated with @HttpGet, it must be set as global static as per Salesforce rules.
(See for more info.)
Since the return type of GET() is a custom wrapper type, the wrapper class also must be declared as global. If not, the compilation error will be thrown.
This fix addresses that false positive in the 'sf:AvoidGlobalModifier' rule. The violation is now ignored for global classes used as return types in any global static method.
12. Fixed error in scanning apex classes in SQ 25.1.0
Some users have reported that CodeScan reports an error in the logs (although the analysis is successful, there is a corresponding error in the log.)
This was being caused by metrics that had been deprecated. This fix removes those deprecated metrics.
Verified the analysis on SQ-25.1.0 v with the latest CodeScan jars provided. Confirmed that users no longer see the error in the logs when the analysis is successful (working as expected).
Validated the presence of a malicious SSRF-style payload embedded in the URL, resulting in a violation (SSRF) as expected.
Validated the attempt at "sanitization" using regex, which is not an approved method, resulting in a violation (Improper sanitization) as expected.
Validated a static URL with no dynamic input, resulting in no violation as expected.
6.Validated fully escaped input and use of safe methods, resulting in no violation as expected.
Verified that using AccListString directly in URL without any sanitization or validation causes violations.
Verified that sanitizing only BaseObjId but not AccListString leads to a violation.
Verified that sanitizing the URL string after using variables has no effect, resulting in a violation.
Verified that URL encoding AccListString without further format validation leads to violation.
Verified that replacing characters rather than proper sanitization leads to security violations.
Verified SOQL inside interface/abstract method (called via polymorphism from loop) — no violation as expected































































Release Date: 07 May 2025
Security Enhancement: A security-related update has been implemented to strengthen the overall protection and integrity of the application.
Release Date: 30 April 2025
Improved Person Account Contact Handling: Processing Person Account records is now streamlined when their related contacts are selected as parent records.
Optimized Query Execution: A code fix ensures accurate record retrieval based on the value specified in the LIMIT clause.
Support for Common Object Retrieval: Added support to fetch common child objects associated with the selected parent object, improving data selection flexibility.
Release Date: 16 April 2025
Data Restore: Fixed an issue to ensure only selected parent records are restored.
Email Triggers: Resolved an issue where alerts were sent for deactivated schedules.
Special Characters in Email: Email addresses can now include special characters (+ . - _ %).
Addressed Vulnerability: Patched a security vulnerability to enhance overall system security.
Release Date: 16 April 2025
Automate Vault Connect Config: Added support for “Automatically Include New Jobs”—new jobs created under the archive config will now be auto-included in the Connect config.
Respect Restricted Delete: When enabled, child records with restricted delete settings will be skipped during the archive process.
Cascade Delete Handling in Archival Process: Child records associated with cascade delete relationships will no longer be explicitly deleted during the archival process. Instead, they will be deleted as part of the parent record’s archival. This ensures that child records are preserved in the Recycle Bin if the archival is performed mistakenly.
Case Data Not Visible: Fixed an issue where Case object data was not visible post-restore. Data now displays correctly after restoration.
Adding Job ID to Threads: Each processing thread now includes a Job ID for better traceability and easier handling of stuck threads.
Release Date: 16 April 2025
Common Child objects Selections: Users can now select common child records like Files, attachments, Tasks, events, etc. shared across multiple parents during data operations without having to select them from the complex schema.
Updating Parent Records in Destination: Parent records already present in the destination will no longer be updated during Restore/Replicate operations.
Release Date: 16 March 2025
Bug Fixes:
Audit Fields Preservation: Fixed an issue in which audit fields were not retained for files and attachments, even when the Set Audit Fields Upon Record Creation option was enabled.
Child Object Deletion Restriction: Resolved an issue in archival that prevented child objects from being deleted when parent record deletion was restricted due to existing child records in the Salesforce org.
Retention Policy Date Update: Fixed an issue in which the retention policy date in the UI was incorrectly updated each time archival reports were executed in Vault.
Release Date: 5 March 2025
Inline Images in Rich Text Fields: Resolved an issue preventing the display of inline images in Rich Text fields through Vault Connect.
Processing of Common Child Objects: Improved the handling of common child objects (e.g., Task, Event) during restore/replicate operations to eliminate redundant actions.
Disabling Salesforce Automation Rules: Resolved an issue where restore/replicate jobs did not properly disable Salesforce automation rules (e.g., Validations, Workflows, Flows, Triggers) for common child objects such as Task, Event, Attachment, and ContentVersion.
Release Date: 12 February 2025
Download Files from Backups and Archives: Users can now download files directly from backups and archives within the Vault UI, improving accessibility and efficiency.
Limitations
Inconsistent File Download During GDPR Requests: When a GDPR request is initiated within an organization, file downloads may behave inconsistently. This issue will be resolved in the upcoming release.
Backup Stability Improvements: Fixed an issue where backups could get stuck when multiple backup jobs were run in parallel on the same Salesforce org.
Schema Representation Fixes: Resolved a minor UI issue in archive job schema representation where EmailMessage was incorrectly displayed as a required child object for all Salesforce objects.
Archival Job Enhancements: Corrected the handling of Salesforce API’s cascade delete and restricted delete checks to ensure accurate interpretation by Vault.
Release Date: 29 January 2025
Rich Text Field Data: Enhanced Vault Connect to support display of images and HTML content seamlessly in rich text fields and in emailMessage body.
Objects Backup: Resolved issues to ensure proper backup of "Big Objects," "Special Objects," and "Entity Definition."
Query Limit: Set a limit on the number of records fetched by queries to prevent excessive data retrieval.
Optimized Query Performance:
Release Date: 18 December 2024
Customer Session Expired: Enhanced record processing to prevent user session timeouts.
OData Backward Compatibility: Fixed an issue to ensure old Archival jobs process files correctly in Vault Connect.
OData Archive Query View: Resolved an issue to ensure the complete query is visible in the view.
Content Version Records Processing: Implemented a check during archival to maintain the relationships of files linked to multiple records.
Release Date: 27 November 2024
Salesforce Spring '24 Upgrade: Upgraded Salesforce to the latest Spring '24 release for improved features and functionality.
Vault Connect – Seamless Access to Archived Files: Customers now have seamless access to files added to records.
FeedItem Failure Analysis: Vault now automatically identifies system-generated FeedItems and excludes them from processing.
Salesforce Summer '24 Upgrade:
Release Date: 6 November 2024
Addressed Vault Restore Issues: Enhanced restore functionality to ensure seamless performance while restoring records.
Addressed Issues in Archive Functionality: Optimized archive functionality for enhanced performance and reliability.
Release Date: 18 October 2024
UI Enhancements: Improved UI for a smoother user experience in multiple areas.
Vault Connect Updates: Now supports attachments with Salesforce External Objects, enabling a comprehensive view of archived data.
Organization Identification during Manual Backup Trigger: Simplified identification of the Salesforce org initiating the backup, with clearer labels for a more streamlined and intuitive experience.
Release Date: 4 October 2024
Improved Metadata Backups: Enhancements have been made to metadata backups to better handle expected errors during retrieval from Salesforce.
FeedComment Restore/Replication: Improved error handling ensures better support for FeedComment replication and restoration.
Improved Backup Performance: Backup performance has been optimized for Salesforce environments with proxy settings enabled, resulting in faster backups.
Release Date: 24 Sep 2024
AutoRABIT is thrilled to announce a series of significant enhancements to our platform. These updates are designed to elevate your experience, offering improved performance, enhanced security, and greater reliability. Below, you'll find detailed information on the key updates included in this release.
Operating System Upgrade
Upgrade Details: The platform's underlying operating system has been upgraded to the latest version.
Benefits:
3 July 2024
Enhanced Search Functionality: Introduced “$” based search functionality to enable users to find precise results efficiently.
Service Contracts & Price Book Fix: Fixed an issue where restored service contracts and price book entries were not being recovered properly.
Child Label Display Issue Resolved: Resolved the problem of child labels displaying identical names across entries.
Email Delivery for Deactivated Sub-users:
19 June 2024
Mail Notification Issue: Scheduled job notifications were being sent to deactivated Admin users. This issue has been addressed.
Duplicate Configuration Name Error: When a duplicate name is entered in the connect section, an incorrect 500 internal server error was displayed.
Updated Error Code: The error code has been updated to correctly display a 400 series "Bad Request" status instead.
12 June 2024
Backend Failure Display Fix: Failures were incorrectly shown due to users adding too many reference fields. The system now limits users to 40 reference fields.
Custom Price Book Entry Automation: Live replicate was failing to create entries in the standard price book, which is required by Salesforce. This process is now automated.
Archival Report Expiration Fix: Archival reports were not expiring after 7 days as intended. A fix ensures reports now expire 7 days after creation.
29 May 2024
Workflow Rule Reenablement After Restore/Replicate: After completing the Restore or Replicate actions, the workflow rules are not being reenabled. The expected behavior is that these rules should automatically be reenabled once the Restore or Replicate process is completed.
Config Details Display Fix: A fix has been implemented to address an issue where the configuration details of the selected record IDs were not being displayed as expected.
Logging for 'Unique Identifiers' Field Names: The field names of the 'Unique Identifiers' were not being displayed. To resolve this, additional logging has been added. Now, if these fields are enabled, they will be logged accordingly.
22 May 2024
Thread Pool Implementation for Network Error: Due to recurring network errors, a thread pool has been implemented to manage tasks more efficiently.
Archive Module File Downloads: Moving forward, all files downloaded from the Archive module will be automatically zipped before download.
Query Column Display Adjustment: The query column will now only be displayed at the criteria level, not at the object level, ensuring a more streamlined view.
15 May 2024
Parallel Threading for Record Processing: Parallel threading has been enabled with 5 active threads. Each thread will handle 5 million records whenever records are identified, processing them in parallel.
Restricted Object Selection for ActivityMetrics: Customers can now only select ActivityMetrics and ActivityMetricsRollup objects when working with 'ActivityMetrics'. To enforce this selection, a query with a WHERE condition must be entered.
Fix for Auto-Selection of Related Records: The reported issue occurred because all related records were auto-selected, even when child records did not need to be included. Now, if the parent object is selected, related child objects will also be processed. If only lookups are selected, the related child objects will not be processed.
08 May 2024
Alert Condition Misconfiguration: The customer set a condition to receive alerts for modifications of 2,000 records, but instead, they are receiving alerts for modifications of just 15 records. This issue is being addressed.
Data Replication Boolean Handling: During data replication, if a Boolean value is empty in the source, the application attempts to update the destination with a blank value, which can cause errors. A code fix now ensures that if a Boolean value is empty in the source, the corresponding field in the destination will be ignored instead of being updated with a blank.
Service Report Suggestion: In response to an earlier ticket about the same issue, the customer was advised to run service reports individually for each configuration and to handle the remaining objects in a separate column.
24 Apr 2024
Job Processing Time Tracking Fix: A fix has been implemented to accurately track and display the correct job processing time.
Record Download Improvement: For records taking more than a minute to download, it was becoming difficult for customers to access them. Going forward, customers will receive an email with a link to download the report. This link will be valid for 4 hours and will expire afterward.
User and Sub-User Tracking in Logs: A code fix has been provided to track and log both user and sub-user details more effectively.
03 Apr 2024
Scheduled vs. Actual Job Date Mismatch: A fix has been provided to resolve the mismatch between the scheduled dates and the actual dates when jobs are run.
Filter Modification Issue in Queries: When filters are modified in a query, the changes were not being reflected. A fix has been implemented to ensure that filter modifications are properly applied in the query.
Removal of Mobile Number Field: The mobile number field has been removed from the user profile sections.
27 Mar 2024
nCino Person Accounts Data Issue: A data issue in nCino person accounts has been identified and fixed.
Disabled Rules and Triggers Functionality Fix: There was an issue where the disabled rules and triggers functionality was not working as expected. A fix has been implemented to resolve this.
Optimized Destination ID Verification: A fix has been made to ensure that only the backup IDs in the destination are verified, rather than checking all destination IDs.
23 Mar 2024
nCino Person Accounts Data Fix: An issue with the data in nCino person accounts has been identified and resolved.
Disable Rules and Triggers Functionality Fix: The functionality for disabling rules and triggers was not working as expected. A fix has been implemented to correct this issue.
Optimized Backup ID Verification: A fix has been applied to ensure that only the backup IDs in the destination are verified, instead of checking all destination IDs.
13 Mar 2024
Password Modification Tracking: A provision has been added to the database to track when passwords were last modified.
Blank Value Restoration: A new feature has been added that allows the restoration of blank values from the source to the destination.
Asset Attribute Backup Support: A fix has been provided to ensure that the asset attribute is supported only during a full backup.
Post-Org Refresh Data Operations:
28 Feb 2024
AWS KMS support has been added for encryption and decryption to the ingestion service.
21 Feb 2024
Restore and Replicate Workflow Issues: Issues related to disabling and enabling workflows through Salesforce Metadata APIs during restore and replicate operations have been addressed.
Duplicate Parent IDs Restored: A fix has been implemented to prevent the same parent IDs from being restored multiple times.
Missing Records Information in Backup/Archive: When users select more 'Excluded Fields' for backups, the records information was not being displayed. This issue has been resolved.
14 Feb 2024
Managed Package Query Issue: When querying fields from managed packages, files related to those packages were not being retrieved. We have removed the triggers that were not retrieved from Salesforce, and going forward, only packages with available files will be processed.
Archiving Deleted Records Count: If a record was archived after being deleted, it was incorrectly counted in the success tally. This issue has been identified and addressed.
Batch Processing Failure Count: For data processed in batches, the failure count was previously calculated on a batch basis rather than as a consolidated total. This has been reviewed to ensure accurate reporting.
07 Feb 2024
Attachment and Content Version Processing: Previously, selecting both the attachment and content version led to errors. With the new fix, these records will now be processed without issues.
Org Registration Error Messaging: Users were encountering vague errors due to insufficient permissions during Org registration. The error message has been updated to provide clearer information.
nCino Feature Visibility Issue: Users couldn't view nCino features in Vault because property files were being read from the wrong location. This has been corrected.
31 Jan 2024
New Algorithm Implementation: The existing master map generation and its dependencies have been removed. A queue system is added, where selected objects are processed first, followed by their children. Instead of saving the full object result from Salesforce in memory, only the filtered result is saved.
Parallel Processing Restrictions: New restrictions have been applied to limit ID fetching during parallel processing.
API Count Fix: The displayed API count now accurately reflects both the files fetched and records processed, providing a consolidated total.
24 Jan 2024
DB Syntactical Error Fix: A syntactical error in the database has been corrected.
Backup Performance Issue: The latest backup is taking longer, with FeedItem and EmailMessages processing for more than an hour.
S3 File Download Fix: A fix has been implemented to allow clients to download files from S3.
OAuth Token Issue: Restore failures were occurring because the OAuth token was null. This issue has been resolved.
Anticipated Release Date: 17 April 2024
These release notes contain important information about Vault® 24.1.
This release incorporates new features, enhancements, and resolved issues from all previous significant releases. If you're upgrading from an earlier version of Vault, check the release notes for any interim versions or details about additional improvements in this release over your current release.
What’s new?
Exciting New Security Enhancements Await in Vault's Latest Release!
Security is paramount, and we're thrilled to introduce a range of robust features designed to fortify your data protection strategies. Get ready to bolster your defenses and streamline your workflows with these groundbreaking additions:
1. Elevated Security: Masking Rules at Org Level Take control of your data security like never before. Now, you can define masking rules at the Salesforce org level, ensuring compliance with organizational policies and enabling seamless reusability across multiple jobs.
2. Enhanced Security Monitoring: Seamless Viewing of Logs & Reporting on User Activity (SIEM) Empower your enterprise security with enhanced user activity and application event logging. Logs are now provided in CEF format, enabling seamless integration with tools like Splunk for comprehensive analysis and continuous monitoring.
3. Advanced Encryption: AWS KMS Support for Vault Connect Securely access archived data from AWS KMS encrypted storage using your own key with Vault Connect. Enjoy peace of mind knowing your data is protected while viewing it directly in Salesforce through external objects.
4. Supporting Vault with Azure Private Link Experience seamless and secure access to BLOB storage from Azure VMs with support for Azure private link in the Vault application, eliminating the need for access keys.
Now, let's dive into additional enhancements aimed at optimizing your data management processes:
5. Enhanced Vault Capabilities: Reusable Replicate Configurations Say goodbye to repetitive setup tasks! With our enhanced Vault capabilities, you can now create reusable Replicate configurations, saving you valuable time and effort by efficiently rerunning configurations and generating multiple jobs as needed.
6. Streamlined Workflow: Org-to-Org Cloning of Masking Rules Simplify your data masking process with ease! Introducing the ability to clone masking rules directly from one Salesforce org to another, eliminating the hassle of defining rules from scratch for sandboxes and other Salesforce orgs with identical masking requirements.
7. Enhanced Clarity: Naming Masking Rules Bring clarity and organization to your masking rules by providing them with descriptive names of your choice. With this new feature, managing and identifying rules has never been easier.
8. Real-Time Replication: Replicate with Salesforce Live Data Experience the power of near real-time data replication with support for Salesforce Live Data sources. Seamlessly seed your org with actual data without relying solely on backups.
9. Insightful Analytics: Drawing Metrics on Archived Data Unlock valuable insights from your archived data with built-in reporting capabilities within the Vault application. Now, you can analyze metrics on up to 6 months' worth of archived data effortlessly.
10. Simplified Data Management: Mapping Restricted Picklists & Record Types Streamline your data management processes with automated mapping of restricted picklist values and record types between source and destination Orgs, eliminating the need for manual intervention.
11. Preserved Data Integrity: Restore with Blank/Null Values Ensure data integrity throughout the restoration process with the ability to seamlessly restore null or blank values from backups during rollback or replication.
12. Improved Connectivity: Vault Connect - OData Connector V4.01 Support Stay connected effortlessly with support for the OData connector V4.01, ensuring seamless connectivity and data exchange while bypassing callout limits.
Upgrade now and fortify your data defenses with Vault's latest release!
Reliable Archival Job Execution: Enhancements have been made to ensure smoother and more consistent archival job processing.
Retention Policy in Backup: The backup process now correctly applies the defined retention policy to all backed-up files, ensuring compliance and data lifecycle integrity.
Proxy Error on Org Registration: Fixed a proxy-related issue during Org registration.
Applying Clause in Filter: The filter logic has been improved to support queries where the clause is part of the statement—no separate WHERE condition is required.
Vault Connect Compatibility: Added backward compatibility for viewing files through Vault Connect that were archived before Vault version 24.2.6.
Salesforce Session Stability: Fixed an issue causing Salesforce session timeouts when archiving files in Vault.
WHEREBigObjects Availability During Backup: Ensured "BigObjects" are available under special objects during backup configuration creation.
Excluded Child Objects from Deletion: Fixed an issue to prevent task and email message data from being included in deletion processes.
OwnerID Exclusion for ContentVersion: Excluded the OwnerID field from upsert operations to improve data handling.
Provision to Exclude Flows: Customers are now able to disable flows during the replicate and restore processes and auto-enable them upon completing the process.
Enhanced Metadata Processing: Improved the handling of child metadata for more efficient processing. Added detailed logging for better visibility into the reasons behind any record-processing failures.
Upgraded Archive & Restore for Emails: Enhanced the Archive & Restore functionality to ensure emails and their respective attachments are properly archived and restored to the email body.
Salesforce Authentication Fix: Resolved the reauthentication issue to ensure seamless and uninterrupted access.
Improved Viewing of nCino Backup Records: Enhanced functionality to ensure users can view nCino backup records without any disruptions.
Optimized Restore/Replicate Functionality: The common object operation has been upgraded from "insert" to "upsert" to improve the performance of restore and replicate processes.
Archival Issue Resolved: We fixed an issue with deleted records being incorrectly picked up during archival.
Improved Restore/Replicate Results: The user experience for restore and replicate operations has been enhanced with an improved results presentation.
Log Enhancements: Job logs have been upgraded to provide more detailed information about where time is being spent during job execution, improving transparency and troubleshooting.
Improved Performance: Users will experience faster processing speeds and more efficient resource management.
Core Libraries Upgrade
Upgrade Details: We have upgraded the core libraries that support our platform's infrastructure.
Benefits:
Boosted Security: Updated libraries reduce the risk of security breaches by addressing known issues.
Optimized Performance: These upgrades enhance the overall performance, resulting in a smoother user experience.
Database Version Upgrade
Upgrade Details: The database powering our platform has been upgraded to a newer version.
Benefits:
Smoother Operations: The upgraded database improves transaction handling and data retrieval, leading to more reliable operations.
Increased Reliability: Users can expect reduced downtime and improved stability, ensuring a seamless experience.
Case Object Relationship Fix: Addressed a bug preventing relationships from being established with the Case object.
Job Duration Display Fix: Fixed the issue where job duration was inaccurately displayed as 1 second during processing.
Special Character Handling: Implemented a fix to properly handle and escape special characters.
Salesforce Toggle State Issue: Resolved an issue in which the “Auto-pick new objects and metadata in Salesforce” toggle appeared disabled, despite being enabled.
File Size Limit Increase: The initial file size limit was set to 5MB. This limit has now been increased to 500MB, applicable to both the front end and backend.
Serial Mode Logging Issue: Even though customers selected 'serial mode,' the backend logs incorrectly showed it as 'parallel mode.' A fix has been implemented to ensure that the logs correctly reflect the selected serial mode.
Email Body Logging Issue: Previously, the email body was being printed in the logs along with email activity tracking. A fix has been applied to prevent the email body from being logged.
Enhanced Log Failure Details: The logs have been updated to provide more detailed information regarding the reasons for log failures.
Fix for Circular References: A reported issue occurred due to circular references. A code fix has been delivered to resolve this problem.
Alert Criteria Issue: Customers should only receive alerts when the specified criteria are met. However, an issue was causing random alerts to be sent. A code fix has been implemented to ensure alerts are only triggered when criteria are met.
Typographic Error in Column Name: A typographic error in a column name was identified and corrected.
Field Mapping for Target Environment: The customer selected an object and set individual mappings for fields to be moved to the target environment.
Knowledge Article Attachment Fix: The knowledge article was not being attached to the corresponding account and case. A code fix has been implemented to ensure that the KB article is properly associated with the relevant account and case.
'Does Not Contain' Filter Issue: To address an issue with the 'Does Not Contain' filter, double brackets have been added to the code to improve its functionality.
Error Message for Apache Drill Unavailability: When a report is triggered and the Apache Drill service is down, users receive a "Request Cannot Be Processed" error message. This behavior is now documented and understood.
Session Information Tracking Bug: A bug was reported by the performance team because session creation information was not being tracked. A fix has been provided, and now session creation is tracked correctly.
Logging Excess Information: Logs were capturing unnecessary information. A code fix has been applied to prevent unnecessary data from being processed in the logs moving forward.
Apache Drill Unavailability: This issue is related to the unavailability of Apache Drill, and it has been addressed with the appropriate fixes.
Non-Expiring Download Links: The download links shared with customers for downloading archival records were not expiring after the designated four-hour period. This issue has been resolved to ensure the links expire as expected.
Persistent Replicate Configuration Details: Even after deleting Orgs, replicate configuration details still remained in the system. A fix has been implemented so that these details will no longer remain in the system after Orgs are deleted.
Lookup-Related Parent Processing: When a lookup was selected, related parent objects were not being processed. The fix now ensures that related objects are automatically picked up and processed accordingly.
Replicate Label Display Issue: The label "Replicate Label" was not being displayed in the configuration details. A code fix has corrected this, and the label now appears correctly in the configuration details pop-up.
Alert Display Order Fix: A fix has been provided to ensure that the most recent alerts are displayed at the top of the list.
Session Termination Logging Fix: A fix was provided to display the name of the user who terminated a session. If an Admin terminates the session, the Admin's name will now be displayed in the log.
File Extension Normalization: The Vault was using multiple notations for compressed file extensions. A fix has been delivered to standardize these extensions across the application, and moving forward, the file extension will consistently be ".gz".
Alert Delivery Issue: Alerts were supposed to be sent to the intended user when more than one record was deleted from a set object. However, users were not receiving these alerts. A code fix has been implemented to resolve this issue.
Filter Limit Visibility Issue: The limit set on the filter was not visible when users tried to edit it. This issue has been resolved with the latest fix.
Child Record Processing Fix: Child records should not be processed unless explicitly selected. In scenarios where child records were being processed automatically, a fix has been applied to correct this behavior.
Archival Job Restore Improvement: Steps have been taken to ensure that deleted entities are not incorrectly shown during the archival job restore process.
Username and Refresh ID Logging: The username and refresh ID have been added to the logs to ensure that users receive accurate error messages and notifications.
Customer ID Replacement: The customer ID has been replaced with the bucket name to ensure that the appropriate folder is created.
Thread Writing Conflict Resolution: Previously, multiple threads were writing into a single file, causing some threads to move into a wait state. A fix has been implemented so that each thread writes to its own file, with all files being merged at the end.
Admin Session Visibility Update: Admin users were unable to see other users' sessions. New updates have been made to address this issue.
Archival Job Restore Accuracy: Steps have been taken to ensure that deleted entities are not incorrectly displayed during the archival job restore process.
Enhanced Error/Notification Logging: The username and refresh ID have been added to the system to ensure that users receive precise error messages and notifications.
Customer ID Replacement with Bucket Name: The customer ID has been replaced with the bucket name to ensure that the correct folder is created during the process.
Job Status Display Fix: A fix has been rolled out to ensure that jobs display the correct status throughout their execution.
Secure File Download via HTTPS: A fix has been implemented to ensure that files are downloaded securely through HTTPS.
Connect Config Deletion: A fix has been provided to ensure that the connect configuration is properly deleted when required.
Delete Flow Corrections: Necessary corrections have been made to ensure that the delete flow operates correctly and as intended.
Encrypted Vault Connect Job Logs: The downloaded file for Vault Connect job logs was displaying in encrypted mode. This issue has been corrected.
Vault Connect UI Data Alignment: The data alignment on the Vault Connect UI has been corrected as part of the recent fix deployment.
Log Output Simplification: Logs have been streamlined to print on a single line instead of across three lines.
Null Pointer Exception Handling: A fix has been provided to handle null pointer exceptions, ensuring successful records are processed without failure.
Parent-Child Mapping Bug Fix: A bug related to the isDisableParentChildMapping flag, which was disrupting the flow, has been addressed by introducing a new flag, disableParentChildMappingForCommonObjects.
Restore and Replicate Bug Fix: A fix has been rolled out to resolve issues causing restore and replicate failures.
New Flag for Child File Processing: A new Boolean flag, personAccountChecked, has been added to ensure child files are processed
Release Date: 04 December 2024
CodeScan 24.0.14 is comprised of the following eight components:
Component details are listed in their corresponding sections within this document.
There are no new features associated with this release.
Added “Project Search” in CSV Export Customers with a large number of projects were experiencing a UI issue with the export feature: users who wanted to export issues in CSV format were only able to see the first 100 projects on the list. In this release, we have addressed this issue by adding a search function in the drop-down list to allow users to search for the name of the project they wish to export.
We verified the added “Project Search” on CSV Export page for multiple scenarios including:
Verified search option functionality with the drop-down list of projects:
New Rule for LWCs: “API Version Is Too Old” This is a new rule to ensure that all Lightning Web Components (LWCs) are using an acceptable API version (including the most current API version). Using outdated API versions can lead to compatibility issues, missed opportunities to leverage new features, and potential security vulnerabilities. This rule aims to streamline the process of identifying and updating LWCs to the latest API version. We recognize that by identifying and updating LWCs to the latest API version, developers are able to maintain higher code quality, reduce the risk of deprecated features, and improve the overall performance and security of the application. Verified the new LWC rule (API Version Is Too Old) for these scenarios:
Verified the description, issue type, severity, message, tags, remediation, and parameters of the rule:
Fixed an issue in the CodeScan application in which flagged violations were not being displayed when using the "issues in new code" filter NOTE: This issue only relates to a separate fix stemming from our last release (24.0.13), when we fixed an issue with reference branch analyses. After that fix, however, users were experiencing a new issue, in which flagged violations were not being displayed when using the "issues in new code" filter. The other parts of the CodeScan application were NOT impacted by the reference branch analyses fix in release 24.0.13. As such, all other parts of CodeScan continued to show the accurate new issue count. Regarding this issue, users were unable to navigate to the issues page after running the project analysis. Further, users were not able to see the issues if the user selected any of the issue types (e.g., vulnerability) after running the project analysis. This fix corrects this issue. Users are now able to navigate to the issues page after running the project analysis. Further, users are now able to see the issues if they select any of the issue types (e.g., vulnerability) after running the project analysis.
Fixed issue in rule for APEX “sf: {{FieldLevelSecurity}}” {Permissions should be checked before accessing resource}. Previously, this rule was throwing violations that were false positives. This was occurring when a SOSL query having an inner query calls the related Object. The Object needs to be checked by using isAccessible() before accessing its data. NOTE: We addressed a similar issue related to SOQL queries in a previous release. That update has been extended in this release to also include SOSL queries.
Release Date: 30 October 2024
CodeScan 24.0.13 is comprised of the following 4 components:
Component details are listed in their corresponding sections within this document.
There are no new features associated with this release.
Enhancement to Rule for VF: “"vf:AvoidJavaScriptScriptlets” We recognize that using direct <script> tags in components or pages can pose a security risk by increasing the likelihood of cross-site scripting (XSS) attacks. Separately, but importantly, you cannot use “includeScript” to embed an Aura Application to a Visualforce page (as the $Lightning global object is not available if put in a separate .js file as a static resource). To address this, Salesforce details how to “create a component on a Page,” advising you to add your top-level component to a page using $Lightning.createComponent(String type, Object attributes, String domLocator, function callback). Note that this function is similar to $A.createComponent(), but it includes an additional parameter, domLocator, which specifies the DOM element where you want the component inserted. Access the full documentation at. Considering both of these items together, we recognize that there was limitation on this rule where customers were getting violations flagged as false positives. This enhancement involves implementing Regex to detect the use of Lightning components within a {{<script>}} tag in Visualforce pages. The rule {{vf:AvoidJavaScriptScriptlets}} should not trigger a violation if only Lightning components are found. However, if any additional lines of non-Lightning code are detected within the script, a violation will be raised. This ensures the proper use of Lightning components while avoiding insecure or outdated practices in scriptlets.
There are no new rules associated with this release.
Fixed issue with reference branch analyses: Branch initially fails the quality gate, then passes on subsequent scans without changes.
Previously within CodeScan, branches with new code consistently failed the quality gate when they contained unresolved new issues (such as bugs, vulnerabilities, code smells, or security hotspots). This failure persisted until all new issues were addressed, ensuring only clean code passed the quality gate.
Recently it was reported that "New Code -> Reference Branch" functionality was no longer working as designed, which was impacting quality gate evaluations for new code on branches for some customers. Indeed, branches with new code were initially failing the quality gate if new issues are detected (as expected and desired). However, on subsequent analyses of the same branch—without addressing the new issues—the quality gate was incorrectly passing.
We recognize that this behavior could result in code potentially being deployed to production despite unresolved issues, as the quality gate no longer blocks the release after the first analysis. As such, a fix has been implemented to ensure the quality gate consistently fails whenever unresolved new issues exist in the code, preventing deployment until all issues are addressed.
Fixed issue in rule for VF “vf:AvoidExternalResources” (in which the rule was checking ALL attributes for external resources, producing false positives). Previously, the rule vf:AvoidExternalResources was checking ALL attributes for external resources, which it should not do. This resulted in false positives being flagged as violations. This fix ensures that the check is limited to the “value” attribute only, to avoid false positives and ensure the rule functions as intended. As an example, the following will NOT be flagged as a violation: <apex:includeScript value="{!$Resource.example_js}" loadOnReady="true"/> //Good: Uses a static resource.
Release Date: 9 October 2024
CodeScan 24.0.12 is comprised of the following 2 components:
1 Rule Enhancement
1 Fix
Component details are listed in their corresponding sections within this document.
Enhanced the rule sf: {{FieldLevelSecurity}} to eliminate false positives
Summary: Previously, this rule was flagging issues that were actually false positives. This was occurring when an SOQL query has an inner query calling the related Object.
In this enhancement, the Object is checked using isAccessible() before accessing its data.
Per Salesforce, when checking the Access for the inner query object, it allows you to check by using __c, but while making an inner query on related Objects, it must be plural and end with __r.
Further, we added SYSTEM_MODE support to the rule enhancement via a rule parameter (where rules admins can choose true or false to include SYSTEM_MODE).
For additional info on Object permission Checks and SYSTEM_MODE, refer to:
Fixed errors when reattaching Bitbucket projects using new enhanced security.
In the previous CodeScan release (24.0.11), we enhanced the security of our Bitbucket webhooks to stay current with the guidelines provided in Bitbucket’s documentation ().
We also implemented a process to make this update easier for existing customers using Bitbucket projects.
Some customers were experiencing errors with this process. This fix has corrected those errors in full, and we have validated that the process works as expected.
For more information on reattaching Bitbucket projects, please refer to our Knowledge Base:
For your convenience, we are also including the documentation from CodeScan release 24.0.11 regarding the enhanced security for Bitbucket projects.
With this enhancement (in 24.0.11), when you create a new Bitbucket project, you must generate a “secret” key and send it to Bitbucket to create a Webhook. In the Webhook endpoint, you should validate the {{X-Hub-Signature}} header value in accordance with Bitbucket guides.
Release Date: 25 September 2024
CodeScan 24.0.11 is comprised of the following 3 components:
2 Functional Enhancements
1 Security Enhancement
Component details are listed in their corresponding sections within this document.
Org Names are no longer restricted to a single word only
Summary: Previously, customers had a restriction limiting Org Names to a single word. With this enhancement, that restriction has been removed.
Valid strings now include names such as:
"My Organization"
"Organization-123"
"My Organization-123"
"Org 123"
However, there are some restrictions regarding leading spaces, trailing spaces, trailing hyphens, and invalid characters, such as:
" Organization" (leading space)
"Organization " (trailing space)
"Organization-" (trailing hyphen)
"My Organization-" (trailing hyphen)
Enhancement of rule “sf:AvoidPublicFields” (reducing false positives on private classes).
The rule sf:AvoidPublicFields identifies when public fields are used and flags them as issues. Two of the three reasons this rule is important are:
The internal representation is exposed and, thus, cannot be easily changed.
When the value is changed in an unexpected way (for example nulled), the implementation may not handle it correctly.
But these are not concerns when those public fields are on a private class.
This enhancement adds a private class validation check first and will not flag the two previously mentioned issues if the class is a private class.
Enhanced security for Bitbucket webhooks
We have enhanced the security of our Bitbucket webhooks to stay current with the guidelines provided in Bitbucket’s documentation ()
With this enhancement, when you create a new Bitbucket project, you must generate a “secret” key and send it to Bitbucket to create a Webhook. In the Webhook endpoint, you should validate the {{X-Hub-Signature}} header value in accordance with Bitbucket guides.
Release Date: 28 August 2024
CodeScan 24.0.10 is comprised of the following components:
1 Enhancement
2 New Rules
6 Fixes
Component details are listed in their corresponding sections within this document.
1. Enhancement to rule “Use the null coalescing operator instead of ternary”
The original aim of this rule is to identify ternary statements and suggest potential use of "??" operator. Previously, CodeScan was checking for ternary statements only.
This rule was originally developed according to common development practices in Salesforce where most usages of this would be in ternary. However, it can be applied in scenarios involving if-else and return statements. As such, we have adjusted the rule to account for these use cases. With this enhancement, CodeScan suggests where null coalescing could be used instead of an “if” block (recognizing that if a developer is already thinking about shortening their code with ternary, then they are likely considering null coalescing operator as well).
1. New Rule for APEX: “IsBlankForNullChecks”
This is a new rule that leverages the built-in {{isBlank}} and {{isNotBlank}} methods instead of the {{!=}} and {{==}} operators to check for null or empty values.
This approach is especially relevant in programming environments and languages where {{IsBlank}} or equivalent methods are provided for more readable, maintainable, and less error-prone code. Using the {{IsBlank}} method for null checks improves code clarity, reduces the likelihood of bugs, and enhances maintainability compared to using the {{!=}} operator. Developers are less likely to encounter unexpected behavior due to differences in how null and empty values are handled. Additionally, built-in methods like {{IsBlank}} are optimized and tested to handle various edge cases, reducing the potential for errors compared to using the {{!=}} operator. It also makes the code easier to read and understand.
2. New Rule for APEX: “Avoid Classes Without Explicit Sharing”
New Rule to Enforce Sharing Rules in Classes
Summary: Enforce security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared. This prevents accidental data exposure and enhances code maintainability and compliance with security policies.
1. Make fields of CustomObject Compatible with SFDX
CodeScan is in the process of updating all of our Salesforce metadata rules to ensure they support both the Salesforce metadata API as well as SFDX formats for the issues they were built to find.
We’ve architected this change because metadata pulled with SFDX has a different structure than metadata pulled with Salesforce’s metadata API. CodeScan can scan these different structures with some additions to the sf-meta suffixes. For this release, we have ensured that the differences are covered within the types of metadata that have these differences (specifically, the Object metadata contains all field metadata when pulled from the metadata API; however, when this is pulled with SFDX, the object and field metadata are separate).
See the following SF article for details of these differences:
2. Fixed issue in rule “sf:AvoidSoqlInLoops”
This CodeScan rule was found to have two issues:
SOQL in the code does not appear to be in a loop, but CodeScan is flagging as a violation.
A violation message is displayed multiple times for the perceived detected violation.
The root causes of these issues were identified, and the following enhancements were added:
Top of Form
Added condition to check if the method call matches the Method name; if not, do not flag as a violation
Bottom of Form
Top of Form
When checking the nested method call, if method name matches, only then it will throw violation.
Bottom of Form
Top of Form
Avoid false positives when a recursive call happens without matching the method name
Bottom of Form
3. Fixed issue when attaching a GIT project for a second time after initially canceling the request
CodeScan UI was inaccessible (page greys out) during scenarios where users were attaching Git analysis to a project in CodeScan where those projects previously had an unattached analysis.
Detail: When users would follow this navigation, they would encounter an error:
Select a project with an unattached analysis ->
Attach analysis ->
select Git ->
cancel ->
RESULT: Page is grayed out until the page is refreshed.
The root cause of the issue was identified and fixed. Verification the issue is now resolved included:
Creating an empty project and subsequently attaching a Git analysis to the project
Deleting the project analysis and attaching a new Git analysis
Validating attaching analyses with no issues for:
Salesforce
GITHUB
BITBUCKET
GITLAB
4. Fixed issue in rule “sf:FixDuplicateMethods”, where Nested statements were being flagged (which was a false positive issue).
Previously, the sf:FixDuplicateMethods rule was throwing violations for nested statements, which is not the intended behavior. The root cause was identified and fixed, and now the rule is working as designed and expected.
5. Fixed issue with Date Filter on IDE Usage Page
In the 24.0.9 release, we made several UI enhancements to the “IDE Usage” page, including the addition of a date filter for:
Last 30 days
Last 60 days
Last 90 days
Last 180 days
However, the action “On click” wasn’t showing the filtered list as expected. The root cause was identified and the issue has been remediated. The date filter now works as designed and expected.
6. Fixed issue with Individual / All Filter on IDE Usage Page
In the 24.0.9 release, we made several UI enhancements to the “IDE Usage” page, including the addition of a filter toggle for Individual / All where:
Upon toggling to “Individual,” the last connection for each individual unique user list is shown.
Upon toggling to “All," the full list of activity is shown (every connection for the selected duration).
However, the action “On click” wasn’t showing the filtered list as expected. The root cause was identified, and the issue has been remediated. The date filter now works as designed and expected.
7 August 2024
The latest CodeScan release is comprised of the following components:
Feature Enhances the “sf.testfile” parameter in project settings UI Summary: Previously, customers using our Git integration could store their test coverage in their repository branches by using a parameter called sf.testfile, which allows you to add coverage to your code with SFDX JSON outputs. With this enhancement, CodeScan allows the parameter to be configurable at a project level. Adding this parameter will allow teams to view the coverage on the CodeScan dashboard. The addition of this parameter notably provides more value for SFDX workflows. Further details are available at the following link: .
UI Enhancements to the IDE Usage Page Summary: The “IDE Usage” page has been updated with the following UI components:
For the IDE Type, logos are now shown instead of text Added a date filter, including: Last 30 days Last 60 days Last 90 days Last 180 days Updated the Column title of “Use at” to “Time Stamp.“ Added a filter toggle for Individual / All as shown. Upon toggling to “Individual,” the last connection for each unique user list is shown. Upon toggling to “All," the full list of activity—every connection for the selected duration—is shown.
New “Exception” status for Security Hotspots Summary: For this release, the “Exception” status essentially mirrors the functionality of the “Acknowledged” status; but this is just temporary. We will be adding the ability to assign a “date time stamp” to this feature, which will then allow the issue to be flagged after the expiration of the date time stamp.
New Rule for “Cognitive Complexity” in CodeScan
This is a new rule for assessing Cognitive Complexity. Note that we had a previous Cognitive Complexity rule. What’s different is that this rule aims to enhance the understanding of code readability and maintainability by identifying areas where the cognitive load on developers may be high.
To introduce this new rule for assessing Cognitive Complexity, we pinpointed specific code structures and circumstances that contribute to increased cognitive load. This enables developers to refactor complex sections of code, leading to improved code quality, readability, and maintainability.
Basic criteria and methodology: A Cognitive Complexity score is assessed according to three basic rules:
Ignore structures that allow multiple statements to be readably shorthanded into one. Increment (add one) for each break in the linear flow of the code.
Increment when flow-breaking structures are nested.
Additionally, a complexity score is made up of four different types of increments:
Nesting – Assessed for nesting control flow structures inside each other
Fixed intermittent “400 bad request error” experienced by some users after successfully logging in via SSO. This issue is now resolved. We have verified that users who have been assigned to an organization and have since converted to SSO are able to log in to the application successfully.
Release Date: 10 July 2024
This update includes several New Features within CodeScan’s Visual Studio Code IDE Extension:
New CodeScan Issue Filter: Quickly sort and filter issues by type and severity for efficient code review.
Fixed a plugin issue that failed to recognize CodeScan-specific JavaScript (JS) and VisualForce (VF) rules.
Resolved duplicate issue detection for specific Apex rules.
Added automatic token generation and connection flow UI.
Added support for SonarQube 9.9 and later versions.
Rule Enhancement for “Avoid Using Test.isRunningTest()” {APEX Rule}: Summary: Previously, this rule was flagging violations when finding methods written as Test.isRunningTest(). This rule has been enhanced to also flag violations when finding methods written as System.Test.isRunningTest().
Decrease False Positives reported for Rule “sf:FixDuplicateMethods” Summary: CodeScan recognizes that methods should not share the same implementations. As such, the scope of the rule will be limited to methods with actual implementations, rather than including interface method declarations. This means the rule will now focus solely on detecting and addressing duplicate implementations within concrete classes, ensuring that only methods containing executable code are evaluated. Violations reported by this rule will now include details of all duplicate methods affected. This means each violation will list every instance of a method that shares the same implementation, making it easier to identify and resolve duplicated code. These updates will make the rule more precise, and its violation reports more comprehensive, enhancing its effectiveness.
UI Improvement on Rule “NullCoalescing operator” We completed an alignment adjustment within the CodeScan UI for this specific rule. Previous UI:
Adjusted UI:
UI Improvement on Rule “Lightning channel Exposed” We completed an alignment adjustment within the CodeScan UI for this specific rule. Previous UI:
Adjusted UI:
Improved IDE Usage Tracking Previously, the IDE tracking page was tracking every use of a token by a user and displaying it on this page. The updated functionality is: 1 entry per user, where the tracking page gets updated / refreshed when a user token is used within VS Code. NOTE: Only VS Code updates on the page. Additionally, instead of login ID, we now display the name of the user and the email under a single column called ‘User’. Also, we changed the title to IDE Usage instead of “IDE Usages” * Finally, we removed the token information, as it is not needed.
Fixed CodeScan IntelliJ Plugin error Previously, the CodeScan IntelliJ Plugin was throwing an error during binding updates when connected to SonarQube 10. The issue was caused by self-hosted connections being incorrectly detected as cloud connections, resulting in an error popup. This issue occurred when connecting to self-hosted SQ 10.x versions in both 2023 and 2024-based IntelliJ versions. The issue error message (popup) resulted from an API call failure. This issue has now been remedied with this fix.
Release Date: 6 July 2024
We are excited to announce that CodeScan has been updated with crucial enhancements to address recent security concerns related to polyfills. Recent advisories have highlighted significant threats stemming from polyfills, particularly those distributed via the CDN polyfill.io, which are linked to malware.
This update, effective July 6th, introduces advanced protection mechanisms to ensure your Salesforce environment remains secure.
Here’s how CodeScan is advancing your security:
Configuration Scanning: Our enhanced system now scans the configuration settings of Salesforce components, including Salesforce Sites, Salesforce CORS (Cross-Origin Resource Sharing), and Salesforce CSP (Content Security Policy), to detect any unauthorized calls to polyfill.io domains.
Component Scanning: We are scanning the core Salesforce components that enable developers to build sophisticated, custom user interfaces including Visualforce, Aura, Lightning, and other web components
Package Scanning: Our updated scanning mechanism checks downloaded packages from Salesforce AppExchange to ensure they do not contain insecure calls to polyfill.io domains
Why This Matters
Recent security advisories highlight the risks associated with compromised polyfills.
What Do I Need to Do?
For our SaaS Cloud clients, these updates were included in the most recent maintenance release on July 06, so no action is required on your side. For our On Prem clients, these rules will be included in the 24.0.8 On Prem release, which is scheduled for July 17. For our Dedicated Cloud clients, please contact your Account Team to schedule your upgrade.
Release Date: 19 June 2024
The 'Hard Coded Credentials' rule name has been changed to 'Use Named Credentials' for clarity.
'Use Named Credentials' and 'Field Level Security' rules have updated descriptions highlighting Salesforce best practices and better paths to resolution.
Fixed a false positive in the rule 'Avoid using methods getDescribe and getMap inside Loops' when using custom methods with similar names.
A link was fixed on the rule description pages.
Filtering the list by project, the rule now works correctly.
New code settings no longer switch depending on the main branch of the project; all branches can be configured independently. A warning will be shown if the setting chosen will have no effect.
Release Date: 5 June 2024
CodeScan 24.0.6 is comprised of the following 3 enhancements:
SBOM Upgrade for ADO extension:
CodeScan currently provides an ADO extension to integrate with Azure DevOps. For this enhancement, we have upgraded components and libraries (within our SBOM), eliminating all high-severity vulnerabilities.
Severity added to SARIF output:
Field 6
Label = “Comparison Branch – Last Analysis Date”
Value = Date of the last analysis of the comparison branch
Field 7
Label = “Version”
Value = The corresponding version number listed in version history / measure history
v. 2.0.3
Changes were required to support fixes and enhancements of the VS Code CodeScan Plugin (v2.0.3) to VS Code Extension Marketplace; specifically, we fixed a plugin issue that caused non-recognition of CodeScan-specific JS and VF rules. Support ticket #114684
13 June 2024
v. 2.0.2
New CodeScan Issue Filter: Quickly sort and filter issues by type and severity for efficient code review. You can click on the specific Type or Severity to only see issues of that type.
The released plugin can be updated directly from VSCode and also can be found in this link:
Release Date: 15 May 2024
Rule Name: “Comment All Hardcoded Values” Category: New APEX rule in CodeScan Purpose: Ensure comments are included when using hardcoded values in Apex classes Detail: Ensures any hard-coded values or strings in the code are accompanied by descriptive comments or, alternatively, use constants. This practice enhances code readability, maintainability, and will make it easier for other developers to understand the purpose of these values.
Rule Name: “Use the null coalescing operator instead of the ternary operator” Category: New APEX rule in CodeScan Purpose: CodeScan recommendation to consider replacing ternary operators (? :) for explicit null checks with the Null Coalescing operator (??) where applicable to enhance code performance and clarity. Detail: In Salesforce's Spring '24 release, the null-coalescing operator has been introduced in Apex. This rule will identify where this operator could be used but isn’t being utilized. For further information, please refer to Salesforce Release Documentation - .
Rule Name: “Avoid JavaScript Scriptlets in Aura Components and Apex Pages” Category: New Aura / Lightning / Visualforce Rule in CodeScan Purpose/Detail: JavaScript scriptlets should not be directly embedded within the markup of Aura components or Apex pages. Instead, utilize Salesforce Static resources for including JavaScript code. Using direct <script> tags in components or pages can pose a security risk, increasing the likelihood of cross-site scripting (XSS) attacks. For further information, please refer to: - - Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
Rule Name: “Exposed Lightning Message Channel” Category: New LWC / Aura / Visualforce rule in CodeScan Purpose: It is recommended to verify instances where the 'isExposed' flag in Lightning Message Channels is set to true. Setting this flag can lead to unintended access to the Lightning Message Service (LMS) API, potentially resulting in unauthorized message publishing and subscribing across components within the Salesforce ecosystem. Detail: This term specifically refers to cases where you have not configured the 'isExposed' flag in Lightning Message Channel to false. Since this provides access to the Lightning Message Service (LMS) API, which lets you publish and subscribe to messages across the DOM and between Aura, Visualforce, and Lightning Web Components, it should be set to false. For further information, please refer to:
Updated the rule “Avoid duplicate conditions in "if"/"else if" and "switch" statements to eliminate dead code." Detail: In the Initial implementation, the "if/else-if" statements and the nested "if/else-if" statements present within them were not allowed to have duplicate conditions. Now only the related "if/else-if" statements are checked for duplicate conditions, without considering the nested "if/else-if" statements present within them. Value: The same conditions can cause duplication and lead to dead code in statements such as "if"/"else if" and "switch." This issue often occurs due to a copy/paste error. In the best-case scenario, it results in dead code that serves no purpose, but in the worst-case scenario, it introduces bugs that may propagate as the code is maintained, potentially leading to unexpected behavior.
Updated the documentation and example on rule “API Version is Too Old” to: “This rule identifies visual force pages which are using older versions of the API. Change the API Version of this visual force page.” Reason for change: The description and example needed to be updated for the rule.
Release Date: 21 April 2024
In this release, we've added more metadata suffixes as recognized types for Salesforce metadata:
Newly added CodeScan logic:
Any suffix with .[dot] present will be treated as a correct suffix and not be modified. This means:
.field-meta.xml - will treat all files ending with .field-meta.xml as metafiles.
-meta.xml - will treat all files ending with -meta.xml as metafiles.
.xml - will treat all files with .xml suffix as metafiles.
xml - will treat all files with .xml suffix as metafiles. (.[dot] is added at the start if not provided)
Add UI element within the CodeScan Administration tab to list IDE license usage at the Org level.
Admins are now notified within the UI when IDE licenses have exceeded the maximum allotment.
Users are now notified in IDE when additional IDE licenses are required (i.e., the company has allocated all available licenses).
CodeScan now removes IDE usage records for users who have been removed from their organization’s member group.
Improved the CodeScan parser as it relates to Visual Force. Specifically, the parser had some issues recognizing parts of Aura code (for example, with components (cmp), the parser was unable to recognize divs and spans across multiple lines). With this release, we have corrected these issues and verified that the Visual Force parser for .cmp, vf, xml, and .page files are all parsed properly. Further, CodeScan users can successfully see these issues after analysis.
Fixed a NullPointerException with the Apex rule “Null Coalescing Operator.”
Fixed an issue with New Code settings. Customers who were changing new code settings while selecting the reference branch as “main” were receiving a notification that the settings had been saved. However, the change was not reflected/applied properly to the CodeScan engine. This issue is now resolved.
Release Date: 27 March 2024
This release has several new features that support enhanced user capabilities.
CSV Export: With this fix, we added a URL column to the CSV Export that enables teams to quickly navigate to the Issue and get a fix in place.
CSV Export not exporting all issues: To avoid doubling up the queries, when a user presses the Export button, the Export and Reset buttons are grayed out and unusable. After the buttons are clicked, the following message should show underneath: "Please remain on this page while your report is generated. Depending on the number of issues in your report, this may take up to 5 minutes. Your download will start shortly."
CSV Export added functionality – Pull Requests: This enables CSV Exports to include the options to filter and group code issues by specific pull request(s).
March 2024
This update introduces several new rules and bug fixes for current rules. This includes:
Apex Rules:
Duplicate method implementations: Methods should not share the same implementations. To prevent duplication and confusion, avoid using two methods with identical implementations.
Code length: Lines should not be too long in APEX. Limiting the length of code lines enhances code clarity and readability by reducing complexity and improving quick understanding.
System.runAs to test user permissions: To ensure accurate and realistic testing of user permissions, it is crucial to utilize System.runAs during test execution, ensuring logic is tested in the same context in which it will run.
Assertion Rules:
Use Assert.areEqual instead of Assert.isTrue: This rule detects Unit test assertions in object references equality. Instead of using Assert.isTrue as an equality check, these assertions should be made by more specific methods, like Assert.areEqual.
Use Assert.isTrue instead of Assert.areEqual: When asserting a value that is the same as a Boolean literal, use Assert.isTrue, instead of Assert.areEqual.
Use Assert Equals Instead of Boolean Equality Assertion: This rule detects unit test assertions in object references equality. Instead of using Assert.isTrue combined with "==" as an equality operator, these assertions should be made by more specific methods, like Assert.areEqual (expected, actual).
LWC Rules:
Enable Salesforce Lightning Web Security (LWS): Enabling LWS ensures that the Lightning components within our Salesforce instance are executed in a secure and controlled environment, reducing the risk of potential security vulnerabilities.
SF Meta:
Adopt the ICU Locale Formats instead of JDK locale formats: Salesforce is retiring the JDK locale formats with the Spring ’24 release. ICU is the new standard enforced in API version 45. Make sure your custom code does not use JDK locale formats and instead uses locale-neutral methods.
Set Flows to Auto Layout: Implementing auto-layout for your flows helps designers modify layouts more quickly, allowing them to iterate on their designs with greater speed. It ensures elements are perfectly aligned and evenly spaced, improving readability in complex Flows.
Potential Overuse of Rollup Summaries: Ensure compliance with Salesforce's limit of 25 roll-up summary fields per object to prevent potential issues arising from exceeding Salesforce platform limits.
Bug Fixes:
Improvement was provided on how to fix for the "Deserializing JSON is Security Sensitive" rule.
We provided a fix on the "sf:AvoidUsingHardCodedId" rule not detecting hard-coded IDs as expected.
Wrongly identified violations in specific scenarios were fixed for the "Comments are Required" rule.
The rule "sf:AvoidPublicFields"
The following items were implemented, fixed, or enhanced with this release:
We fixed a parser issue in the "Avoid Untrusted/Unescaped Variables in DML Query" rule.
A new rule parameter, allowList, was added to the "Track Usage of @SuppressWarnings" rule.
We fixed the "Get help" action, which was not working when users clicked the plus (+) icon.
Security tokens are now sorted by creation date.
Updated the message for Security Hotspot Status “Exception” We recently added a new status type for Hotspots (status = “Exception”). Its intent is to serve as a more accurate status than 'Acknowledged' or 'Open' for issues being treated as exceptions. When we first delivered an “Exception” status, the associated message was: “The code has been reviewed and does not pose a risk currently. Further review is needed at a later date.” Based upon numerous client suggestions, we have enhanced the message to read: "The issue has an approved exception and will be re-reviewed until mitigated or upon exception expiry.”
Verified that a violation is thrown if the API version used is higher than the maximum version allowed:
Verified that no violation is thrown when the API version is between the minimum and maximum versions allowed.
New Rule for APEX: “OuterClassExplicitSharing” Enforces security best practices on classes by ensuring that sharing settings ('with sharing', 'without sharing', or 'inherited sharing') are explicitly declared. This prevents accidental data exposure and enhances code maintainability and compliance with security policies.
Name: Outer Class Explicit Sharing
Key: OuterClassExplicitSharing
Type: Vulnerability
Severity: Major
Message: Class '{className}' does not have an explicit sharing rule
Tags: Convention
Remediation: 5 minutes
Verified the rule: OuterClassExplicitSharing for the following scenarios:
Verified the rule’s description, type, severity, message, tag, remediation, key, and name:
Verified the rule is not throwing a violation if used with sharing, without sharing, or inherited sharing:
Verified that a violation is thrown if not used with sharing, without sharing, or inherited sharing.
Rule is throwing a violation if isAccessible is not checked for the objects used in the inner query:
Rule is not throwing the violation if isAccessible is checked for the objects used in the inner query.
REMINDER: In the previous release, we added support for SYSTEM_MODE in this rule. A new parameter has been added, allowing users to choose true or false to include or ignore violations related to SYSTEM_MODE. We have verified the rule: FieldLevelSecurity for the following scenarios:
Rule is throwing the violation if the object is NOT checked via isAccessible for the methods used in the inner query.
Rule is not throwing the violation if the system mode value is set = “true” (and the object IS NOT checked via isAccessible for methods).
Rule is not throwing the violation if the system mode value is set = “false” (and the object IS checked via isAccessible for the methods).
Fixed issue with Retention Period settings The retention period for project branches in CodeScan was not functioning properly. The UI is able to be set, but it does not affect the cleanup of branches within the project. This setting can be found in Project Settings > General Settings > Housekeeping > Delete inactive branches and PRs after. Also, the text in the “Branches” menu did not reflect the branch retention length change:
Verified the Retention Period fix for the following scenarios:
In the UI, users are able to set Delete inactive branches and PRs after value:
Users are able to see the same branch retention length value on the Branches & Pull Requests page.
Fixed issue with Group Synchronization for SAML connections We uncovered an issue with Group Synchronization during a recent customer implementation. We identified the root cause and a code change delivered in this release fixes the issue. Group synchronization is now working as designed. Further, we verified the Group synchronization option in SAML connection on a customer environment and have reported that this capability is working as expected.
Verified the functionality of reference branch for the following scenarios:
Verified the new code of a branch where user is able to see the issues exactly when compared with the reference branch.
Verified that the quality gate failed status if the new branch has any new code compared to the reference branch.
Verified that the quality gate passed status if the new branch has no new code compared to the reference branch.
Verified that we can change the reference branch in the UI and run the analysis locally, with or without specifying the reference branch in the command. (If we didn’t specify the reference branch, it should take master as RB.)
Verified that renaming of the reference branch and using the new name for analysis are working correctly.
Verified that when a branch is deleted in the UI and then used as a reference branch in the SFDX command, a 404 error is returned.
Verified the version option on activity page by providing name and editing name.
Verified the following options that are present under new code period for any branch under specific settings for a branch.
Previous version
Number of days
Specific analysis
Verified the functionality by adding new code with vulnerabilities and fixed some issues that were marked as false positives in the UI.
Verified the sonar scanner command as well for the reference branch.
Fixed issue in rule “sf:OptimizeParallelUnitTests” (IsParallel) This rule is designed to ensure that isParallel is present, either True or False. Previously, when a second flag was added to a test, the rule threw a violation, e.g., @IsTest(SomeFlag=True IsParallel=False). This should not throw a violation since IsParallel is specified. Instead, something like @IsTest(SomeFlag=True) should throw a violation, as IsParallel is not specified. This issue was occurring because the rule detection logic was looking for “@isTest(isParallel=true/false)” annotation being defined/set individually on its own (only), but not when used in combination with other annotations. Not being able to detect combination annotations setting was thereby causing false positive violations. Various scenarios tested outcomes for the rule BEFORE the fix was added:
Not setting “@isTest(isParallel=false)” (or true) – Violation – Correct behavior.
Setting @isTest(isParallel=false) or @isTest(isParallel=true) – No violation – Correct behavior.
Setting @isTest(OnInstall=true isParallel=False) – Violation – Incorrect behavior as isParallel is set.
Setting @isTest(SeeAllData=False isParallel=True) – Violation – Incorrect behavior as isParallel is set.
Results demonstrated that scenarios a and b were working as expected; however, in scenarios c and d, the rule was not able to understand multiple combined annotations format of @IsTest(xxx=false yyy=true) This fix corrects the issue. We have verified the Apex rule sf:OptimizeParallelUnitTests via multiple scenarios, and all are working as expected.
If true, when Org Admins log in, they will receive this *WARNING* message: “You have to reattach the following Bitbucket projects by the end of 2024 to enhance security: project_key_1, project_key_2, project_key_3, etc."
If true, when Org Admins log in, they will receive this *WARNING* message: “You have to reattach the following Bitbucket projects by the end of 2024 to enhance security: project_key_1, project_key_2, project_key_3, etc."
WEBHOOK
Structural – Assessed on control flow structures that are subject to a nesting increment and that increase the nesting count.
Fundamental – Assessed on statements not subject to a nesting increment.
Hybrid – Assessed on control flow structures that are not subject to a nesting increment but increase the nesting count.
Enhancement to Rule: "Cyclomatic Complexity" Summary: Several enhancements were applied to the rule cyclomatic complexity, including adding the decision points '?', '&&', '||', and 'catch'.
Added dashboard Url to Job status API Summary: On the Project Analysis page, we have added dashboard Url to Job status API on success/failure of analysis:
CodeScan currently generates SARIF output; however, that SARIF output in GitHub does not contain the severity. By adding severity to our SARIF output, CodeScan can now provide a more verbose presentation of the issues in GitHub. This change will provide a better experience for our customers working in GitHub Actions.
Added more fields in our Report Header:
CodeScan report header contained limited information regarding the context of the report. This enhancement provides much more detailed information including:
Field 1
Label = "Report Generation Date"
Value = Date report was created
Field 2
Label = “Project Name”
Value = Name of project
Field 3
Label = “Main Branch”
Value = Name of the main branch
Field 4
Label = “Main Branch – Last Analysis Date”
Value = Date of the last analysis of the main branch
Field 5
Label = “Comparison Branch”
Value = Name of the comparison branch or pull request branch
Rule Name: “Use Accessibility Attributes” Category: New Lightning Web Component Rule in CodeScan Purpose: Updating LWCs with certain attributes makes these components more accessible to users of assistive technology. Detail: Accessibility software such as screen readers interpret the elements on a webpage using the title attribute, so specifying a value for components is very important. Salesforce’s ARIA attributes allow accessibility software to gather more information on the state of the page and align with the ARIA standard. For further information, please refer to: Component Accessibility Attributes Accessible Rich Internet Applications (WAI-ARIA)
Rule Name: “nCino Inactive Workflow Rules” Category: New nCino Gold Standard Rule in CodeScan Purpose: Removing inactive, unmanaged workflow rules in a Salesforce instance allows organizations to maintain an organized workflow environment Detail: Removing inactive UNMANAGED workflow rules will streamline workflow processes, reduce confusion among users, and improve system performance. This action leads to a cleaner and more efficient Salesforce instance. Further, removing inactive UNMANAGED workflow rules helps declutter the Salesforce environment, making it easier for administrators and users to navigate and manage active workflows effectively.
Rule Name: “Utilizing Apex Unit Tests with @IsTest(IsParallel)” Category: New APEX rule in CodeScan Purpose: The annotation “@isTest(isParallel=true/false)” can be set in Apex test classes to indicate whether the particular test can be executed parallelly or sequentially (performance enhancement). Detail: When writing Apex unit tests, ensure that the @IsTest(IsParallel) annotation is set, whether true or false. This keeps the option of running tests in parallel visible through development to optimize test execution times. However, it should only be enabled in scenarios where it adds value without introducing risks or conflicts. Further information: When utilizing Apex unit tests with the annotation @IsTest(IsParallel=true), it's essential to be aware of potential drawbacks to ensure smooth execution and accurate results. Enabling parallel testing with @IsTest(IsParallel=true) may lead to UNABLE_TO_LOCK_ROW errors due to resource competition, which in turn can result in rerunning failed tests in serial mode. Additionally, it's important to note that this setting does not affect change set deployment or package upload processes. By understanding these drawbacks, developers can effectively manage test execution and deployment processes, minimizing errors, and ensuring the reliability of test results.
Quality Profile error: A bug that caused project analysis issues is now fixed in the sfmeta:FlowNullHandler rule.
NullPointerException in IdempotentBinaryOperatorsRule: This fixes an exception when a null pointer is thrown in IdempotentBinaryOperatorRule.txt.
Quick Report — Issue Counts: This fixes a bug causing issue count errors in Quick Report.
Null Pointer Exception — Apex classes: This fixes an error causing an exception during analysis of Apex classes.
Null Pointer Exception for IfElseDefaultCase Rule: This fixes a null pointer exception thrown for triggers.
False Positives: This fixes false positive errors for the sf:FixDuplicateConditions rule. The same conditions can cause duplication and lead to dead code in statements such as "if"/"else if" and "switch". This issue often occurs due to a copy/paste error. In the best-case scenario, it results in dead code that serves no purpose, while in the worst-case scenario, it introduces bugs that may propagate as the code is maintained, potentially leading to unexpected behavior. Addressing false positives for cases such as:
Use Relative, not Absolute URLs: Code that uses absolute URLs for Salesforce pages will only work when running on the corresponding Salesforce instances. This can cause code to fail when deployed in another sandbox or production environment. Use relative URLs to avoid this issue.
Null Pointer Exception – sf:AvoidAbsoluteURL rule: Fixed a null pointer exception during analysis associated with the sf:AvoidAbsoluteURL rule.
“If ... else if” should have “else” case: Include a default case using an "else" statement at the end of "if" and "else if" clauses to handle all conditions and provide code clarity.
Limit case clauses in switch statements: Using a large number of case clauses in switch statements creates complex, difficult-to-read code.
Avoid Identical Expressions on Both Sides of a Binary Operator: When both sides of a binary operator have identical values, the condition will always give the same result.
Avoid Sending Emails in Loops: Avoid using Messaging.sendEmail within loops to prevent exceeding Salesforce governor limits and to enhance application performance.
Avoid duplicate conditions in "if"/"else if" and "switch": When the same conditions are used in statements like "if"/"else if" and "switch", it can lead to duplicate or dead code.
API Versions 7.0 through 20.0 Retirement: The retirement of older Salesforce Platform API versions (7.0 through 20.0) after the Summer '22 release is a critical step to ensure the continued smooth operation of Salesforce applications.
Avoid using methods getDescribe and getMap inside Loops: The ‘getDescribe’ and ‘getMap’ methods typically involve fetching metadata information for objects and fields. Invoking them inside loops can result in unnecessary overhead.
Unit Assertions should include a Message: Unit assertions should include a message. In other words, use the three-argument version of Assert.areEquals(), not the two-argument version.
Unit Test Method Contains Too Many Asserts: Unit tests should not contain too many asserts. Many asserts are indicative of a complex test, for which it is harder to verify correctness. Consider breaking the test scenario into multiple, shorter test scenarios. Customize the maximum number of assertions used by this Rule to suit your needs.
Non-Unit Test Methods Should Not Contain Asserts: Asserts should only be used in test methods.
Misuse of Assert Class: Assert Class can be misused if not applied correctly. To ensure the correctness of our code and avoid common pitfalls, establish best practices for its usage.
Use Messages in Assert Statements: Ensure that messages are included when using the assert method with the message parameter to improve code quality and make it easier to identify the cause of failures during testing and debugging.
Consider Using Assert in place of System.Assert: This new class aims to enhance the readability and maintainability of test code for developers. It is preferable to use Assert in your tests instead of older System.Assert methods.
@InvocableVariableWe provided a fix for the rule's missing root element in "RuleSet."
We provided a fix for the "Consider removing inactive flows" rule not working correctly.
A fix was provided for the "Flows API Version Is Too Old" rule to prevent Null Pointer Exceptions.






















public class sample{
public static void main(){
if(a==true){}
else if(a == null){}
if(super.a){}
else if(this.a){}
if(this.a){}
else if(this.b){}
}
}
Reference branch














CodeScan Cloud Release Notes
Please note that there are updated requirements for customers who are using one or more of the following to integrate with CodeScan:
SFDX
SonarScanner
ADO
VS Code
IntelliJ
Release Date: 30 November 2025
CodeScan 25.1.15 is comprised of the following 4 components:
1 Rule Enhancement
3 Fixes
Component details are listed in their corresponding sections within this document.
1. Enhanced the logic in the CodeScan rule “Unnecessary Boolean Assertion”
{Rule ID: sf:UnnecessaryBooleanAssertion}
Several customers have reported that the current rule detects unnecessary Boolean assertions only when using the System.assert() method.
However, it does not flag similar patterns when assertions are made through the Assert class methods such as Assert.isTrue(true) or Assert.isFalse(false).
To improve coverage, we enhanced the rule logic to include these Assert class scenarios, ensuring consistency across both assertion types.
Fix Summary
Extended the rule logic to detect unnecessary boolean assertions in the following cases:
Assert.isTrue(true)
Assert.isFalse(false)
Updated the rule message and description to clearly explain why these patterns are redundant.
Updated Rule Description:
A Unit test assertion with a Boolean literal is unnecessary since it always will evaluate to the same thing. Consider using flow control (in case of assertTrue(false) or similar) or simply removing statements like System.assert(true) and Assert.isFalse(false). If you just want a test to halt after finding an error, use the System.assert(false, 'message') or Assert.isFalse(false, 'message') methods and provide an indication message of why it did.
Verified the following scenarios are working as expected:
Noncompliant scenarios using System.assert(true), Assert.isTrue(true), and Assert.isFalse(false). All were correctly flagged as expected.
Compliant scenarios have been tested. (by using only string values).
1. Fixed an issue in the rule “Require CSRF Protection On GET Requests”
{Rule ID: vf:RequireConfirmationToken}
During our routine, internal rule evaluation process, we discovered that this rule wasn’t firing as expected. As such, we overhauled the rule logic to address this issue.
Summary:
The current xpath for this rule is:
//Document//Element[@Name='confirmationtokenrequired'][Text[@Image='false']]
We recognize that this will not work as expected, as the confirmation token is actually in the metadata of the page and the tag is in camel-case (confirmationTokenRequired).
The logic was updated to:
//Document//Element[lower-case(@Name)='confirmationtokenrequired'][Text[@Image='false']]
With this enhancement, the rule will:
find the correct tag
look in the page-meta.xml metadata file (not the page itself)
Verified the following scenarios and confirmed that the updated rule logic is working as expected.
“vf:RequireConfirmationToken” getting triggered only when the corresponding meta.xml has false for ConfirmationToken tag .
Verified the rule behavior using by uploading only page file and then with corresponding meta.xml file with true and meta.xml file with false.
2. Fixed an issue in the rule “Switch statements should not have too many case clauses”
{Rule ID: sf:MaximumNumberOfCase }
Some customers have reported that this rule throws out of bounds exceptions. Upon investigation, we determined that this is caused by an empty switch statement, which manifests as a parser error when this class is added in Salesforce.
The aim of fix is to make sure that the CodeScan parser sees empty switch statements as syntax errors.
Verified that the below scenarios are working as expected.
Verified that the rule does not throw out of bounds exceptions in the analysis logs (it should not throw this and, as such, has been validated as working as expected).
Verified “sf:MaximumNumberOfCase” rule is triggered only when the maximum limit is exceeded.
3. Fixed an issue in the CodeScan UI on the “Quality Gate Changelog” page, where the “author name” field overlaps with the “action taken” field.
Some customers reported an issue in the CodeScan UI on the “Quality Gate Changelog” page, where the “author name” field overlaps with the “action taken” field.
This fix remediates that issue in full.
Verified the below scenarios and validated that the fix is working as expected.
Verified that the “author name” filed does not overlap with the “action taken” field.
Verified with different actions (Updated, Activated, Deactivated).
Release Date: 16 November 2025
CodeScan 25.1.14 is comprised of the following 10 components:
1 New Feature
3 Rule Enhancements
2 Rule Deprecations
4 Fixes
Component details are listed in their corresponding sections within this document.
1. New rules to Identify Potential Sensitive Data /PII Fields
Description
These rules identify potential sensitive data and Personally Identifiable Information (PII) fields within the Salesforce Apex code. This helps organizations ensure these fields are handled securely and comply with data privacy regulations.
Hypothesis:
By implementing these rules to identify potential sensitive PII fields, CodeScan can identify and address security risks associated with handling sensitive PII data in Salesforce.
CodeScan Sensitive Data Scanning uses regular expression patterns to search for potential sensitive PII field names. It looks for common identifiers listed below and some custom objects/fields such as "name," "social_security_number," "credit_card," or "passport" and determines if they are being assigned string literals or used in an insecure way (exposed in debug).
NOTE: We implemented advanced logic to Ignore Violations on Dummy/Masked data as shown below:
Value/Purpose:
The purpose of this user story is to enhance data privacy and security within our Salesforce organization. By identifying potential sensitive PII fields, we can Improve data governance and minimize the chances of data breaches.
Acceptance Criteria
Name: Identify Potential Sensitive PII Fields Key: SecurePIIFields Description: Certain standard Salesforce objects (such as Contact, Lead, User, Account, Person Account, and Opportunity) contain fields that may hold PII, including names, addresses, phone numbers, emails, birthdates, and other identifiers. These fields must be treated as sensitive data and protected in compliance with privacy and security regulations (e.g., GDPR, CCPA, HIPAA).
Ensure these fields are handled securely through encryption, masking, and strict access controls to minimize the risk of data exposure or breaches. Type: Vulnerability Severity: Major Message: Potential sensitive PII field detected. Ensure that this field is handled securely. Tags: Security Parameters: Name: sensitiveFields Description: A comma-separated list of sensitive custom fields. Add any custom fields you would like to monitor with this rule.
Verified that sf:SecurePIIFields rules are being triggered in following scenarios:
Verified the sf:SecurePIIFields rules by activating these rules in a specified Quality Profile. The Project analysis should trigger the violation (Security Hotspot).
Verified by giving custom parameters (ssn, credit_card, passport) and validated that they are working as expected.
Verified by sending both string and integer value for credit_card.
1. Enhanced God Class Rule by adding parameters {Rule ID: sf:GodClass}
The sf:GodClass rule currently uses fixed threshold values to identify “God Class” design flaws:
WMC (Weighted Methods Count): > 47
ATFD (Access to Foreign Data): > 5
TCC (Tight Class Cohesion): < 1/3 (33%)
These thresholds are hard-coded and not configurable. We decided to introduce parameters to allow users to customize these values based on their project requirements. By making these thresholds configurable, users can fine-tune the rule according to their project’s code complexity and quality standards, reducing false positives and improving detection accuracy.
Value / Purpose:
Enables users to adjust thresholds to better match their codebase.
Improves usability and flexibility of the rule.
Increases adoption by making the rule adaptable to various team standards.Bottom of Form
Verified the sf:GodClass by validating that users are able to see the violations as expected for the below scenarios
When users provide the below Threshold values:
wmc=47, atfd=5, tcc=0.33 Result: Violation
wmc=10, atfd=5, tcc=0.50 Result: Violation
wmc=60, atfd=10, tcc=0.90 Result: Violation
wmc=30, atfd=2, tcc=0.8 Result: Violation
2. Updated the Rule Description and Example for rule “Check for Lightning Migration Issues for Salesforce.com and Force.com Links” {Rule ID: vf:LightningAvoidHardcodedSalesforceDomain}
This rule was updated with this new description and example:
“URL references may not work as expected in Lightning Experience or if you decide to swap to My Domain. If you decide to use My Domain, you have to replace hard-coded references to your original URL with references to your new domain. Using something like {!Site.BaseUrl} will avoid this hassle.
See: ”
Example:
Verified these rule updated by confirming that users are able to see the updated description and the example.
3. Updated the Rule Description for rule "em" Tags Should Be Used Instead of "i" {Rule ID: vf:ItalicTagsCheck}
We recognized that this description was out of date and determined it needed to change to: “The <strong>/<b> and <em>/<i> tags have exactly the same effect in most web browsers, but there is a fundamental difference between them: <strong> and <em> have a semantic meaning, whereas <b> and <i> only convey styling information like CSS.
When <b> can have simply no effect on a device with limited display or when a screen reader software is used by a visually impaired person, <strong> will:
Underline the characters on a phone or tablet
Speak with lower tone when using a screen reader
Display the text as bold in normal browsers
Consequently:
In order to convey semantics, the <b> and <i> tags shall never be used,
In order to convey styling information, the <b> and <i> should be avoided and CSS should be used instead.
Verified the rule description and confirmed that the updated description which is displayed as expected.
1. Deprecation of 2 rules for “disallow irregular whitespace outside of strings and comments” (one for Visualforce and one for JavaScript) {Rule ID: cs-vf:no-irregular-whitespace and Rule ID: cs-js:no-irregular-whitespace}
The reason these rules are being deprecated is because they do not fire before the parser catches the issue. These types of irregular white space are no longer even seen as parsing JavaScript.
Further, we have updated the descriptions for these rules to include: “This rule has been deprecated due to these types of white space being caught by the JavaScript parser before a rule can be fired. Please make sure you have the cs-js:exception rule in your javascript Quality Profile to be made aware of these errors.”
Verified the Rule Deprecations of cs-vf:no-irregular-whitespace and cs-js:no-irregular-whitespace and confirmed users are able to see the updated status as Deprecated and the updated description for these rules.
2. Deprecation of 2 rules for “disallow octal escape sequences in string literals” (one for Visualforce and one for JavaScript) {Rule ID: cs-vf:no-octal-escape and Rule ID: cs-js:no-octal-escape}
The reason these rules are being deprecated is because they do not fire before the parser catches the issue. These types of octal escapes are no longer even seen as parsing JavaScript.
Further, we have updated the descriptions for these rules to include:
“This rule has been deprecated due to these types of octal escapes being caught by the JavaScript parser before a rule can be fired. Please make sure you have the cs-js:exception rule in your javascript Quality Profile to be made aware of these errors.”
Verified the Rule Deprecation for cs-vf:no-octal-escape and cs-js:no-octal-escape and confirmed users are able to see the updated status as Deprecated and the updated description for these rules.
1. Fixed project deletion issues occurring on WEBHOOK type projects with SFDX/Sonar-Scanner
Several customers have reported unexpected issue under the specific circumstance of:
1. Create a WEBHOOK type empty project.
2. Run the analysis for the created empty type project using SFDX/Sonar-Scanner
3. The Analysis will be successful (as expected).
4. Then create a branch analysis for the same project type.
5. Switch the branch analysis to main branch analysis.
6. Then delete the project from Project settings.
Outcome:
Users are able to see that the project has been deleted successfully (expected behavior).
However, if users then search for projects, these users are able to see the project which was deleted previously. This is not expected behavior.
We have identified that the root cause of this issue is that the Project is not actually getting deleted when the default branch for a project is changed. This issue has been fully remediated with this fix.
Verified the fix via the following scenarios
Ran sonar-scanner analysis twice (one with branch) >> switch to other branch >> try deleting project >> user able to view successful message for deletion >> project deleted.
Verified with empty webhook project analysis as well.
Verified the below scenarios via the CodeScan APIs:
Verified Single project deletion and bulk project deletion
Verified Postman response - by giving security token and without security token
Verified deleting projects without having access
Verified deleting old projects.
2. Fixed issue where the bulk deletion of analyzed projects fails, while single project deletion works successfully
We have detected this issue under the following circumstance:
From the Project Management page, deleting a single project after a completed analysis works correctly. However, when multiple analyzed projects are selected and deleted in bulk, the deletion operation fails and throws error as "error": "org.hibernate.TransientPropertyValueException: object references an unsaved transient instance."
This issue has been remediated fully, so that all selected projects (analyzed) are deleted successfully (and the system shows proper confirmation messages (if required).
Verified the Bulk delete option for all project integrations, including comparison branches and regular branches. Confirmed via the following scenarios that users are now able to successfully delete multiple projects at once.
3. Fixed an issue in the rule “Immutable Field,” which was causing false positives {Rule ID: sf:ImmutableField}
Several customers have reported that the current rule logic incorrectly flags propertyVal as a candidate for final, even though its value can be modified indirectly through a property getter/setter. In the following example, the field propertyVal is updated within the getter of anotherPropertyVal via this.propertyVal = 'test' and subsequently returned:
Example code:
Expected Behavior: The rule should not raise a violation when the private field’s value can be modified through class property accessors (get/set methods) or other internal logic. Such fields are not immutable and marking them as final would cause compilation errors.
Verified that the “sf:ImmutableField” is getting triggered only when the private field’s value cannot be modified. Further, we verified the rule behavior using both mutable and immutable field patterns.
4. Fixed an issue in the rule “Type Reflection Is Security Sensitive” {Rule ID: sf:HotspotTypeReflection}
During our routine, internal rule evaluation process, we discovered that this rule wasn’t firing as expected. As such, we overhauled the rule logic to address this issue.
Verified the sf:HotspotTypeReflection rule by activating the rule in a specified Quality Profile. Then, in a subsequent project analysis, validated that the rule is now working as expected.
Release Date: 02 November 2025
CodeScan 25.1.13 is comprised of the following 5 components:
4 Rule Enhancements
1 Fix
Component details are listed in their corresponding sections within this document.
1. Enhanced rule “Field Level Security” {Rule ID: sf:FieldLevelSecurity}
Previously, CodeScan did not raise violations if a method matched the condition:
This exception was originally introduced to reduce noise and was added to our rule logic before Salesforce introduced USER_MODE. However, with Salesforce’s updated guidance requiring all database operations to consistently enforce permissions, the exemption is no longer valid. Getters can still expose data through bindings, so excluding them would not align with best practices.
Now, DML operations in getter methods that do not enforce permissions (e.g., without USER_MODE) will correctly raise violations.
We have verified the rule logic and validated that users are able to see the violations for the getter methods on SOQL, DML operations.
2. Enhanced rule “Aura Controller Naming Convention” {Rule ID: sf:AuraControllerNaming}
Previously, CodeScan Controller Suffix in the rule Aura Controller Naming Convention was incorrectly case-sensitive. This meant that a violation was not triggered (expected behavior) when the suffix to controller (lowercase). However, if the class name instead included "Controller" (uppercase), a violation was being thrown (i.e., when we set ControllerSuffix = Controller).
Verified the below scenarios and validated that both are working as expected:
ControllerSuffix = "Controller"
ControllerSuffix = "controller"
Further verified the sf:AuraControllerNaming rule by setting ControllerSuffix = “Controller” in first run of Project and then changed ControllerSuffix to “controller.” Both projects triggered the same number of violations based on the provided data.
3. Updated the rule description for “God Class Rule” {Rule ID: sf:GodClass}
Description:
The God Class rule detects the God Class design flaw using metrics. God classes do too many things and are very big and overly complex. They should be split apart to be more object-oriented. The rule uses the detection strategy described in "Object-Oriented Metrics in Practice".
The God Class rule evaluates classes using the following three key metrics to determine size, dependency, and cohesion:
WMC (Weighted Methods Count): Measures the number and complexity of methods in a class. A high WMC indicates that a class has too many methods or overly complex behavior.
ATFD (Access to Foreign Data): Counts how many times a class accesses data from other classes. A high ATFD means the class is overly dependent on external data, reducing modularity.
TCC (Tight Class Cohesion): Represents how closely the methods of a class are related to each other. A low TCC suggests poor internal cohesion, meaning the class handles unrelated responsibilities.
Every violation will include three metrics: (configurable):
WMC: default > 47
ATFD: default > 5
TCC: default < 1/3 (33%)
The violations are reported against the entire class.
Verified the Update God Class Rule Description and confirmed that users are able to see the updated description for the rule.
4. Updated the rule descriptions for “CodeScan Other Rules” {Rule ID: cs-vf:unknown and Rule ID: cs-js:unknown}
We have updated the rule description for the rule "CodeScan Other Rules" rule key.
Updated Description:
This rule detects ESLint rule references written in code comments that are not currently recognized by the plugin. It helps identify placeholder or upcoming rules that may be added in future updates.
We have verified the Rule Description Updates on “CodeScan Other Rules (cs-vf:unknown and cs-js:unknown) and confirmed that users are able to see the updated descriptions.
1. Fixed issue where issue page was not properly loading (under specific condition)
Several customers have reported that under the specific circumstance of:
Pull request > select any branch/pr > code > open any file and click on any issue message
Users are presented with a blank page instead of being redirected to the issue page.
This issue has been fully remediated with this fix.
Verified that users are now able to navigate to the Rule description page. Also verified that the “Why is this an issue link” (as well as other associated pages) are all working as expected.
Release Date: 19 October 2025
CodeScan 25.1.12 is comprised of the following 3 components:
1 New Feature
2 Fixes
Component details are listed in their corresponding sections within this document.
1. Better Management of CodeScan Orgs via Soft Deletion
Description
With this release, when an Admin performs an organization deletion, the org is maintained for an additional 30 days to allow for restoration (if needed).
However, please note that the org will immediately become inaccessible to all members, owners, and IDE users, and any tokens associated with it become expired. The deleted organization will remain in a disabled state for 30 days and can only be restored by an Instance-level Admin during this period.
We recognize that we can improve organization lifecycle management and data governance for our customers, while also reducing accidental data loss, by allowing Admins to restore orgs within 30 days.
Once an organization is deleted:
It will become immediately inaccessible to all non-admin users (members, owners, IDE users).
All API tokens and access credentials associated with the organization will be expired.
The deleted organization will be listed under a new "Deleted Orgs" section visible only to Instance-level Admins.
The deleted org is in a disabled state and cannot be accessed, modified, or used in any IDE integrations.
Value / Purpose
Ensures security and compliance by revoking access and expiring tokens immediately upon deletion.
Provides control and flexibility to Instance-level Admins with a grace period for restoration.
Prevents data loss from accidental deletions.
Improves auditability and accountability in organization management.
1. Fixed issue where the IDE usage was not being captured properly
Several customers have reported that Admins are not able to see any details in the IDE Usage screen in their Org, while others reported that while they see the records, they do not see the records in Order.
We have determined the root cause to be a JDBC exception and have fully remediated both of these issues with this fix.
We have verified the fix via the following scenarios and confirm that Admins are able to see the correct records without any errors.
Admins can view all relevant details on the IDE Usage page after selecting the Individual tab.
Admins can also view the records displayed in the correct order under the All tab.
When the user selects "All" and filters the data for 120 days in the IDE Usage screen, the "Show More" option appears, allowing them to scroll down and view additional records from the last 120 days.
2. Fix to AvoidAbsoluteURL Rule
We have witnessed that, periodically, this rule does not seem to pick up new Salesforce URLs. As such, we updated the rule logic to detect and violate URLs matching the following patterns: {{*.salesforce.com}} {{*.force.com}} {{*.site.com}} {{*.documentforce.com}} {{*.marketingcloudapis.com}}.
We have verified the fix of the AvoidAbsoluteURL rule via the following:
Updated the rule to detect and flag violations for URLs matching the following patterns:
*.salesforce.com
*.force.com
*.site.com
Release Date: 5 October 2025
CodeScan 25.1.11 is comprised of the following 5 components:
2 Application Enhancements
2 Rule Enhancements
1 Fix
Component details are listed in their corresponding sections within this document.
Update Project Analysis Subtitle Dynamically
Several customers have reported that, regardless of project analysis, each time a user attaches ANY analysis project to CodeScan, there’s a message that says, “Connects to your Salesforce instance.”
We recognize that when using *Project > Project Analysis*, the subtitle should dynamically update to display the text:
When the user selects *Salesforce* as ALM, the label updates to show: _“Connects to your Salesforce instance to execute a CodeScan analysis.”
When the user selects *Repository (GitHub, Bitbucket, GitLab)* as ALM for Project Analysis, the label updates to show: “Connects to your [ALM name] Repository to execute a CodeScan analysis.”
Further, the label must update in real time upon ALM selection, without requiring a page refresh.
This ensures the user clearly understands the connection purpose based on the selected ALM.
Verified the Update Project Analysis Subtitle Dynamically via the following scenarios:
Verified for the existing projects and newly created projects (all project integrations). The user is able to see the updated static description on the project analysis page as expected:
“Connects to your Salesforce instance or repository to execute a CodeScan analysis.”
New Version of CodeScan VS Code Extension (v 2.1.2)
Description
In the previous version of VS Code (2.1.1 and earlier), we had a reported bug: Issues that have been resolved in the UI are still showing in VS Code. In the past, these issues have been ignored and would be updated with a refresh of the connection.
In this updated extension, we have implemented improved synchronization of resolved issues from the CodeScan server, which addresses the reported issue.
Verified the VS Code plugin for the following file types: .cls, .page, .java, .js, .trigger, .css, .ts, .cmp.
Violations are appearing as expected in both the CodeScan environment and the VS Code plugin.
The resolution actions—Accept, False Positive, Confirm, and Fixed—are functioning correctly.
Verified the same functionality in the US PROD environment, which is working as expected and consistent with the TEST environments.
Enhancement to “sf:AvoidLogicInTrigger” Rule
Historically, this rule finds any blocks of code in a trigger and throws a violation.
In this enhancement, we added a parameter to the rule allowing users to add a comma separated list of trigger frameworks that are allowed.
The new parameter is “allowedTriggerFrameworks.”
Description: A comma separated list of Trigger frameworks to allow. Violations will still be reported if complex logic is present within the allowed parameters.
For more information, please review an overview of triggerframeworks:
Details of the new parameter:
Allow:
Trigger.is* checks
Direct calls to whitelisted methods/properties (including inside conditions or assignments).
Flag:
Verified the new parameter on the sf:AvoidLogicInTrigger rule to ensure compatibility with trigger frameworks via the following scenarios:
Any control statement with {} (e.g., if, for, switch) in trigger body → Violation.
Exception: if that uses Trigger.is… → No Violation. However, if Trigger.is… appears inside a for loop, it’s still a Violation.
If a method is added to the rule parameter (allow-list) (e.g., checkPermission), then an if using it → No Violation.
But: for, while, do-while, SOQL, DML → always Violation (allow-list does not suppress these).
Enhancement to “Use Annotation on Test Class” Rule
During our routine testing of our rules, we noted that this rule is outdated, as it only detects the testMethod keyword. It does not work with the newer @IsTest annotation, causing missed violations in modern Apex test classes.
Fix Updated the rule logic to support detection of @IsTest annotation on test classes, ensuring compliance with current Apex best practices.
Verified the enhanced rule logic in “Use Annotation on Test Class” in the following scenarios:
A non-test class or Utility class without test methods → Verified: No violation raised.
@IsTest annotated class with test methods (@IsTest and/or testMethod) → Verified: No violation raised.
Class containing only testMethod methods without @IsTest → Verified: Violation raised.
Class containing only @IsTest methods without class-level @IsTest → Verified: Violation raised.
Fixed Application Issue where the “Issues Filter” was not working as expected with CWE tags.
Several customers have reported that the Issues Filter does not work with CWE tags. Although individual issues correctly display their associated CWE ID, searching or filtering by a specific CWE ID in the Issues view will sometimes return no results.
We have identified that the root cause of the issue was that the CWE filter for Issues and Rules was limited to display and filter through only 10 items in the filter dropdown. Therefore, we expanded the filter limit to display up to 100 items and enabled input-based search across all options for enhanced usability and consistency.
After extensive research, we concluded:
Rules page – CWE search
In the Rules page, only the first ~10 CWE entries show up under the search. Beyond those, no additional rules appear when searching by CWE.
Issues page – CWE filter
Issues do show up for certain CWEs, but not consistently. Example: an issue mapped to CWE-470 appears, yet the same issue also mapped to CWE-80 does not appear when searching for 80.
When a rule/issue has multiple CWE values, the CWE filter on the Issues page sometimes returns results for only one of those CWE values, not all.
Filter/search behavior
The CWE filter search bar does not call an API while you type. It only searches within the already-fetched list from the backend.
An API request is made only after you click/select a specific CWE from that list to load rules/issues for that CWE.
Technical details (implementation)
standardfacet.tsx renders the CWE filter component; handleSearch manages the in-filter search behavior.
Standards.json lists CWE values and descriptions. Even after adding additional CWE entries into this file, those new values still don’t appear in the filter list.
Conclusion: The filter list is not driven solely by Standards.json, or it’s being constrained elsewhere.
Data/API status
Database: Contains all rules with their full set of CWE values.
API: Works as expected when calling with cwe=<value>; results return correctly. The inconsistency happens only in the filter UI, so we should inspect the UI-side response and check for any server or client-imposed limits on the number of CWE results returned.
We have remediated these issues with this fix.
Verified the fix for “Issues Filter is not working with CWE tags” via the following scenarios.
Searching or filtering by a specific CWE ID in the Issues page under Security Category is working as expected.
Verified that the Show More button under the CWE filter works correctly, with the default filter count set to 15.
Even when the CWE filter is limited to the default 15 entries, searching for an ID like CWE-16 still returns the correct result for the user.
Release Date: 21 September 2025
CodeScan 25.1.10 is comprised of the following 9 components:
1 New Feature
8 Rule Enhancements
Component details are listed in their corresponding sections within this document.
CodeScan now imposes verification logic on email signup to enhance security. Previously, users were able to register and log in without verifying their email. We recognize that this could potentially lead to the creation of fake or fraudulent accounts. In this release, we have implemented an email verification via unique links to a one-time verification link. Additionally, we have added logic that restricts access to functionalities for unverified accounts. Verified the Migrate email verification Rule to Action in Auth0 via the following scenarios: After signing up, the user receives a verification email. Only after successfully verifying the account, the user is able to log in to the instance as expected.
Enhancement to sf:ServerSideRequestForgery Rule As part of the CodeScan 25.1.2 release (June 2025), we added this new rule (Server Side Request Forgery). We have had several customers request an enhancement to this rule, as they reported that this rule was not catching all of the SSRF issues. As such, we have enhanced this rule to find all the sinks for these issues with concatenated URLs to all methods that take an HttpRequest as an input. This is the list of methods we have added as sinks (these are in addition to the issues that this rule is currently finding):
Http.send(HttpRequest)
HttpRequest.setEndpoint(String)
Continuation.addHttpRequest(HttpRequest)
PageReference.getContent() Verified that the rule ServerSideRequestForgery is throwing violations when the following methods are used in the code:
Enhancement to Resource Injection Rule As part of the CodeScan 25.1.2 release (June 2025), we added this new rule (Resource Injection). We have had several customers request an enhancement to this rule, as they reported that this rule was not catching all of the issues. As such, we have enhanced this rule to find all the sinks for these issues with concatenated URLs to all methods that take an HttpRequest as an input. This is the list of methods we have added as sinks (these are in addition to the issues that this rule is currently finding):
Http.send(HttpRequest)
HttpRequest.setEndpoint(String)
Continuation.addHttpRequest(HttpRequest)
PageReference.getContent() Verified that the rule Resource Injection is throwing violations when the following methods are used in the code:
Enhancement to “Switch Statements Should Have a When Else Case” Rule Currently, the rule is not working as expected, as it does not raise violations when a switch statement lacks a when-else block. We have modified that logic to correctly identify switch statements that are missing a when-else case so that users can ensure the code is more robust, future-proof, and does not miss handling unexpected cases. Example:
Verified that the updated rule now correctly flags switch statements without a when-else block, ensuring violations are raised consistently for missing default cases.
Enhancement to “Avoid Reversed Operators” Rule Modified the rule logic to correctly detect and report improper usage of reversed operators (=-, =+) in Apex code, so that users can avoid mistakes where variables are unexpectedly reassigned rather than incremented/decremented. Current Behavior:
Violations are not raised when using reversed operators like target =- num; or target =+ num;. Expected Behavior:
The rule should detect and flag cases of reversed operators (=-, =+) and provide a clear violation message.
The violation message should explain the confusion:
x =- y; assigns -y instead of subtracting.
Verified the new logic via the following scenarios: 1. Rule sf:AvoidReversedOperators raises violations for reversed operator cases (=-, =+).
2. Rule does not raise false positives on valid operator usage (+=, -=).
Enhancement to “CouplingBetweenObjects” Rule Modified the rule logic to correctly detect and report violations so that users can identify classes with excessive dependencies and reduce code complexity for better maintainability and testability. Verified that the violation is triggered when the number of classes used exceeds the defined threshold value in the rule parameter (for example, if the threshold is set to 4 and 5 classes are used, a violation will be raised).
Enhancement to “Avoid Insecure Digest Algorithms” Rule Enhanced the current rule logic to correctly raise violations when MD5 or SHA-1 algorithms are used. Since these algorithms are cryptographically broken and vulnerable to hash collision attacks, their continued use poses a security risk. The rule should:
Detect any instance or usage of MD5 or SHA-1 for hashing/digesting.
Report violations with clear remediation guidance.
Suggest secure alternatives such as SHA-256 or SHA-512. Verified the new logic via the following scenario: Validated that users are able to see a violation for the rule AvoidInsecureMessageDigests. This violation indicates the use of insecure message digest algorithms such as MD5 or SHA-1.
Enhancement to “Add Empty String” Rule Updated the rule logic to identify and flag expressions where literals are concatenated with an empty string (e.g., "" + 123 or 123 + ""). Also ensured that violations are reported with a clear message and that valid concatenations and type-specific toString() methods are not falsely flagged. Verified the below scenarios all are working as expected. 1. Empty string with numeric or Boolean literals Examples: '' + 123, 123 + '', '' + -42, '' + 3.14, false + '', '' + true 2. Empty string with string/char literals or inside chains Examples: '' + 'abc', 'abc' + '', 'A' + '' + 'B', 1 + '' + 2 3. Empty string literals inside parentheses Examples: ('' + 1) + 2, 1 + ('' + 2) 4. Empty string at start of long chain with literals and variables Example: '' + 123 + 987 + var1 + var2 5. Empty string used with - operator and literals Examples: '' - 123, 123 - '', '' - -42
Enhancement to “Avoid Hard-Coded Resource References” Rule Enhanced the rule logic to identify hard-coded file path references and raise violations with a clear issue message. Validated the logic by verifying that users are able to see the violations for the use of the attribute value that starts with '/resource/'.
Release Date: 07 September 2025
CodeScan 25.1.9 is comprised of the following 4 components:
2 Enhancements
2 Fixes
Component details are listed in their corresponding sections within this document.
Enhancement to Suppress Warnings Rule
Our rule TrackSuppressWarnings had logic to find @SuppressWarnings, but the logic didn’t include find @suppresswarnings.
This suppression tag works in any case and we recognized that our TrackSuppressWarnings rule needs to do the same (meaning the rule needs to be case insensitive.)
This logic was added to this rule in this enhancement.
Verified the SuppressWarnings Rule enhancement and validated that the suppression tag is working in all case-insensitive instances and our TrackSuppressWarnings rule is throwing violation for all cases.
Rule Enhancement for sf:UnusedFormalParameter
In this rule enhancement, we introduce a configuration flag (ignoreUnusedParametersInInterfaceOverrides) in the sf:UnusedFormalParameter rule so that unused parameters in valid interface implementations and method overrides can be conditionally suppressed. By default, violations will continue to be reported unless this flag is explicitly set to true.
How to Identify These Parameters for Suppression
When designing your rule improvement, the logic should:
1. Check if the method is implementing a known Salesforce interface method:
Use method signature matching (name, parameters, visibility).
Confirm the containing class uses implements keyword for one of the known Salesforce interfaces.
Ensure parameter types match exactly, e.g., SchedulableContext, Database.BatchableContext.
Visibility Enforcement
Only suppress violations if the method visibility is public or global, as required by the platform.
Private or protected methods should never be eligible for suppression under this rule.
This ensures that suppression only applies to methods actually callable by the platform or conforming to Apex interface rules.
3. Override Detection
If a method in a class overrides a method from a superclass or an abstract class:
Signature match is mandatory (same name, return type, and parameters).
Use of the override keyword confirms the intent, but even without it, structural matching should be enough.
In such cases, the parameter should not be flagged if unused, since it’s required by the parent contract.
Value / Purpose
Prevent misleading or incorrect violations in valid interface and override implementations (e.g., execute [SchedulableContext]).
Preserve backward compatibility by keeping the rule strict by default.
Additionally, we updated the Rule Description to “Avoid passing parameters to methods or constructors without actually referencing them in the method body. Use the ignoreUnusedParametersInInterfaceOverrides parameter to suppress violations for unused parameters in valid interface implementations and method overrides.”
Verified the rule sf:UnusedFormalParameter and validated the following conditions:
The method implements a known Salesforce interface method.
Method signature matches exactly in terms of:
Name
Parameters
Fixed issue with CodeScan rule detecting SOQL Injections, which was causing analyses to break.
Previously, while analyzing for SOQL Injection, if a local variable is declared using a class-level variable of same name, then CodeScan analyses were erroring with StackOverflowError as it was stuck in a loop while resolving the reference.
Example:
class Foo { private static String QUERY = 'Select '; public static List<Opportunity> getData(String stage) { String query = QUERY + 'Id FROM Opportunity WHERE StageName = :stage'; return Database.query(query); } }
With this fix, we added validation to detect and prevent such recursive reference resolution.
Verified the SOQL injection rule fix (which was causing stack overflow error) by validating that now users are not encountering the error, and their project analyses are working as expected.
Fixed an Error that was occurring when Deleting CodeScan Projects
Some customers have reported that when attempting to do a project deletion, the task sometimes fails. We have determined that the root cause is that the system is trying to fetch project details after the project has already been removed, which leads to missing information and, subsequently, unexpected errors.
This fix includes logic to delete projects properly.
We have verified the fix for Error When Deleting CodeScan Projects and validated that users are able to delete their projects without any errors.
Release Date: 31 August 2025
CodeScan 25.1.8 is comprised of the following 1 component:
1 Fix
Component details are listed in their corresponding sections within this document.
Fixed issue where CodeScan Project Analysis jobs getting stuck at "finalizing" stage.
Previously, CodeScan project analysis jobs were getting stuck at "finalizing" stage, and not returning the result to GitHub PR, thus blocking all PRs.
The root cause of the issue was that db-pool-limit-reached was occurring. This fix remediates this issue.
After applying the fix, we validated the fix by creating jobs with alternating pass/fail quality gate statuses. Once the fix had been applied, we observed all jobs completing successfully (without getting stuck) We also verified the below Audit log cases:
Verified the category "PROJECT_ANALYSIS" and checked the below details that are stored in the logs all are appearing as expected.
Project Names
Project Keys
Lines of code count - split by ncloc languages
Created date
Also, Verified the category Quality Gates and checked the below details which are stored in the logs all are appearing as expected.
operation": "UPDATE",
propertyValue": "Failed/Passed”
createdAt": “*****”
componentKey
CodeScan 25.1.7 is comprised of the following 5 components:
1 New Feature
4 Fixes
Component details are listed in their corresponding sections within this document.
Enable/Disable feature of Mapping to multiple orgs from one SAML Connection at instance level.
This new feature enables customers to map to multiple orgs from one SAML Connection at their instance level.
Verified the following scenarios for SAML users, and all scenarios are working as expected.
Verified the User when CodeScan idp-group-mapping is disabled, user is able to log in through SSO when the Group synchronization and IDP mapping is not used.
Verified the User when CodeScan idp-group-mapping is disabled, user is able to log in through SSO when the Group synchronization and IDP mapping are used.
Verified the User when CodeScan idp-group-mapping is enabled, user is able to log in through SSO when the Group synchronization and IDP mapping are used.
Verified the User when CodeScan idp-group-mapping is enabled, user is able to log in through SSO when the Group synchronization and IDP mapping are not used.
Fixed Broken Documentation Link in Status Module
It has been reported that the "Status" module in all CodeScan application contains a broken documentation link:
This link provides users with detailed information on the lifecycle of issue statuses but currently leads to a nonexistent page. The correct, working link should be:
This fix remediates this issue in full.
Verified the fix by confirming that the documentation link under the "Status" tab in the Issues module has been updated and now redirects to the correct Knowledge Base page. The link is updated to
URIs are not Valid in decorated SARIF output
It has been reported that the URLs are not valid in the SARIF file due to spaces. To remediate, we added logic to make certain that they are escaped.
Verified that users are now able to see valid URLs in the SARIF report even when the file names include underscores, numbers, hyphens, special characters, with spaces.
Fixed issue where scheduled analyses are not running for SF projects and its comparison branches
Several customers have reported that their daily scheduled analyses were not running for Salesforce integration projects and their corresponding comparison branches within the same project. We determined that the Scheduled Jobs were getting stuck, even though they were consuming memory and CPU. Further, we identified that the root cause of the issue stemmed from changes made in the previous release (25.1.6), and that scheduled jobs on our AWS infrastructure were running into “out-of-memory” issues.
This fix remediates this issue in full.
Verified the fix and validated that the scheduled jobs are now running without issue (as expected).
Fixed issue with deleting branches in projects using Salesforce Integration
We uncovered that if the following steps were performed…
1. Launch and log in to the CodeScan application and be on any org. 2. Create Salesforce project. 3. Create comparison and standard branch analysis. 4. Try deleting comparison branch.
…then users receive an error message indicating that an “unknown error occurred.”
This issue has been fully remediated in this release.
We have verified the fix and have validated that the following scenarios are all working as expected: 1. Verified salesforce comparison branch deletion. 2. Verified creation of project with user having (create and analyze project permissions). 3. Renaming of project branch. 4. ALM project tags working as expected.
Release Date: 3 August 2025
CodeScan 25.1.6 is comprised of the following 6 components:
1 New Feature
3 Enhancements
2 Fixes
Component details are listed in their corresponding sections within this document.
Categories for Project Types
Often, customers will have a lot of projects in CodeScan. Several customers have requested the ability to filter their projects by the type of integration including:
GitHub: github Bitbucket: bitbucket GitLab: gitlab Git: git Salesforce: salesforce
To deliver this feature, we created custom tags with the ability to add these tags when new projects are created.
Unlike most tags, we designed integration type tags to remain once assigned. If the user tries to remove it the following error will occur: “Integration type tags cannot be removed from projects.”
NOTE: Due to the change in permissions needed in the API for these tags to be added, we also adjusted the text in the API doc as well. For the endpoint api/project_tags/set the text now states:
“Requires the ‘Administer’ or ‘Create Project’ permissions on the specified project.”
Here are the tag API references:
Verified Categories for Project Types in the following scenarios, and have verified that all are working as expected:
Verify that the user is able to see the correct tag for the project on the Project Information page after completing the analysis. Example: For a Salesforce integration, the tag should display as “Salesforce.”
Verify that the user is able to see the correct tag for each project integration under the "Tags" column in the Projects tab of the organization. Example: For a Salesforce integration, the tag should display as “Salesforce.”
Verify that the user is able to see the correct tag for each project integration under the "Tags" column in the My Projects tab. Example: For a Salesforce integration, the tag should display as “Salesforce.”
Verify that the user is not able to remove an existing tag or add a tag of a different integration tag to the project.
Verified that clicking on a tag correctly displays the associated projects, with accurate project count and correct project listings.
1. Users getting error when trying to restore quality profiles.
Currently, when a Quality Profile import fails, CodeScan displays the following error: "An error occurred. Please contact your admin."
We recognize that it would be a better experience (and more helpful) to make this error more verbose to allow the customer to remediate the issue themselves. Mostly these errors are thrown because of a rule present in their Quality Profile which is not present in their organization. In these cases, the error message is now “An error occurred. A rule in your Quality Profile is not available in this organization.”
The second most common error occurs when the QP is corrupted or malformed. In these cases, the error message now states “An error occurred. The Quality Profile backup is malformed. Please export your Quality Profile again.”
We believe that these more verbose error messages will help our customers remediate their issue much more easily. However, if they require assistance, they can create a support ticket.
Verified this enhancement via validating the below scenarios
If a malformed QP (with no profile name/language) is imported, an error message is shown.
When importing a QP with custom rules from another instance, those custom rules are also created during import.
If the imported QP has no profile language, the error message says: "Profile language should be set."
2. Pagination in Projects and Previous Analysis
To provide a better experience, we have added separate pagination controls, allowing users to navigate Projects Analysis and Previous Analysis sections more easily. This enhancement includes Projects Analysis displaying 10 entries per page and Previous Analysis displaying 15 entries per page. This allows the user interface to remain responsive and readable even when there are many entries.
Verified the Pagination enhancement via validating the following scenarios:
The Projects Analysis section displays a maximum of 10 entries per page.
The Previous Analysis section displays a maximum of 15 entries per page.
Pagination controls (e.g., next, previous, specific result numbers) are present and functional in both sections independently.
3. Email Limit & Validation for Multi-User Invites
To improve the user experience for admins inviting users to their CodeScan org, we have implemented the ability to invite multiple users at once (up to 50) using the same user type (Standard User or Platform Integration User). Additionally, this enhancement ensures that only valid email addresses are accepted in the batch. This ensures that the invite experience remains consistent and controlled; additionally, user onboarding will be faster and more efficient. Further, Admins are still able to maintain control over user type classification, email validation, and system performance.
The main components of this enhancement are:
Added each email on a new line.
Text was added in UI beside Email option for multiple users invite option.
Add the following error during limit exceeded scenario: “Invite limit exceeded. Max 50 emails allowed.”
Value / Purpose:
Streamlines onboarding by allowing multiple users to be invited in one action.
Maintains role clarity by restricting each batch to a single user type (Standard or Platform Integration).
Improves system integrity and reliability by validating email format and capping batch size.
Prevents errors and abuse by limiting the invite size to a maximum of 50 and checking for valid emails only.
We have verified the enhancement for Email Limit & Validation for Multi-User Invites by validating the following scenarios:
Verified that if invite is sent to more than 50 members, then the following is thrown:
Invite sent successfully if invite is sent to less than or equal to 50 users.
Verified, if mail address is more than 100 characters, then an error is thrown; if it is less than 100 characters, then the invite is sent successfully.
1. Align CSV Export filter status with Latest SQ Issue status
This enhancement implements issue status values in the CSV export filters to reflect the latest status terminology introduced after CodeScan 25.1.0 release (which occurred in April 2025). Prior to this enhancement, the filters in CSV Issue Export were showing outdated statuses such as Opened, Confirmed, ReOpened, Resolved, and Closed. This was in contrast to the updated statuses including Open, Accepted, False Positive, Confirmed, and Fixed. This inconsistency was reported by several users who cited confusion and data integrity issues when analyzing or reporting exported results.
Value / Purpose:
Ensures consistency between issues UI and CSV exported data.
Improves user trust and understanding of exported scan results.
Acceptance Criteria
Status Values in Export:
Legacy Status Replacement:
Filter Cleanup:
UI-CSV Consistency:
Verified this enhancement by validating the following scenarios:
Status Values in Export:
The issue statuses in the exported CSV must match the latest values of Open, Accepted, Confirmed, False Positive, and Fixed Legacy Status Replacement:
Legacy status values such as Opened, Confirmed, ReOpened, Resolved, and Closed must no longer appear in the exported CSV.
These must be correctly mapped to the corresponding updated status where applicable.
Filter Cleanup:
The Resolutions filter should be completely removed from the CSV Export page.
The Is Resolved filter should be completely removed from the CSV Export page.
Only the Status filter should be visible and functional.
UI-CSV Consistency: The status shown in the exported CSV for each issue must exactly match what is shown for the same issue in the UI.
The type, statuses and severity shown in the exported CSV is exactly matching what is shown in the issues page and CSV export page.
Fixed an unclear error message displayed when invite is sent only to non-corporate email addresses
This fix addresses an unclear message that occurs when:
Admin clicks on "Invite user"
Admin enters only non-corporate email addresses (e.g., Gmail, Yahoo)
Admin clicks "Send Invitation"
After these steps, Admin receives the following unclear error message:
However, this issue does not occur when multiple users are invited, including at least one corporate email:
This issue has been fully remediated. We have verified the fix via the following scenario: Validated that the proper error message is displayed when invite is sent only to non-corporate email addresses.
Release Date: July 20, 2025
CodeScan 25.1.5 is comprised of the following 17 components:
· 4 New Features
· 2 Enhancements
· 4 Fixes
· 1 Revenue Org Improvement
· 6 Architecture Improvements
Component details are listed in their corresponding sections within this document.
Support Intelligent Prompts for A.I. LLMs
CodeScan can now generate prompts for LLMs including Agentforce, Copilot, ChatGPT, and Claude AI. This feature is a component of the CodeScan extension for VS Code.
Requirements:
Your CodeScan environment must be running version 25.1.5 (or higher). In addition, you need to be running the latest version of the CodeScan VS Code extension (v 2.1.1), which can be downloaded here:
What Problem Are We Solving?
Adoption of AI can be challenging for companies for several reasons. CodeScan can help catalyze your AI initiatives.
User Benefits
• Generate prompt in the IDE
• Directly update existing code with generated code
• Ensures security issues are addressed
Verified Intelligent Prompts for cls, page, component, trigger, and cmp files, all working as expected by validating the below scenarios:
1. Able to click generate prompt and copy it
Able to paste the generated prompt in the Agentforce search box
Able to receive the message prompt copied to clipboard after generating prompt.
Able to receive a message stating that the file is too long; please select the impacted lines of code and click "Generate Prompt" if the selected file has more than 1,000 characters.
Able to copy the code generated by Agentforce as expected
CVSS Implementation for Security Vulnerabilities
The Common Vulnerability Scoring System is a technical standard for assessing the severity of vulnerabilities in computing systems. Scores are calculated based on a formula with several metrics that approximate ease and impact of an exploit. Scores range from 0 to 10, with 10 being the most severe. In this release, CodeScan has applied this quantitative scoring to all security vulnerabilities, allowing organizations to more systematically prioritize the security remediations.
The following metrics were used to generate our CVSS scores:
Base Score Metrics
Attack Vector (AV) (specify)
Attack Complexity (AC) (specify)
Privileges Required (PR) (specify)
User Interaction (UI) (specify)
Temporal Score Metrics
Exploit Code Maturity (E) (specify)
Remediation Level (RL) (specify)
Report Confidence (RC) (specify)
Environmental Score Metrics
Modified Attack Vector (MAV) (specify)
Modified Attack Complexity (MAC) (specify)
Modified Privileges Required (MPR) (specify)
Modified User Interaction (MUI) (specify)
Verified the CVSS range from 0 to 10, where users are able to see the CVSS violations for the below rules as expected.
OpenRedirect
CustomFieldSecurityInStandardObject
SOQL Injection
FieldLevelSecurity
Verified the CVSS Category on RULES page, ISSUES page and also verified the CVSS issues for the specific analysis.
3. When encountering an Incorrect Custom XPath rule, CodeScan Analysis continues
Currently, if a customer’s Xpath Rule has incorrect XPath syntax, an error is shown in the analysis log and no further checks are run on the file that the custom rule was being applied to.
We decided to make this more visible to users, as there was no further explanation of skipping the file outside of reviewing the associated logs. Instead, users would see the issues disappearing from their files.
In this release, the following improvements were added:
one incorrectly formatted custom rule shouldn’t stop the processing of all rules on a file
created a project level rule that triggers a violation when this issue occurs
implemented the logic for a project level violation that appears when this issue occurs
created an associated message: “The custom XPath rule {rule key} failed to parse. Your {language} files were not able to display this issue. Please check your custom rule in the rule designer before your next analysis”
Define User Type While Inviting or Adding Member
CodeScan now allows admins to define the user type when inviting or adding a member (either "Standard User" or "Platform Integration User"). This ensures that each user is onboarded with the appropriate role, purpose, and permissions.
Since the system now allows for the designation of users as either Standard Users or Platform Integration Users during the invitation or member addition process, admins are now able to manage users more effectively (and thereby Ensuring Standard Users have the appropriate access (All the features of CodeScan), and Platform Integration Users are recognized distinctly for integration IDE purposes (or similar integration purposes).
Value / Purpose:
Improves access control by ensuring correct user roles at the point of entry.
Differentiates Standard Users from Platform Integration Users for better tracking and reporting.
Enhances audit logs, billing accuracy, and license management.
Reduces post-invite administrative tasks by setting the correct user type up front.
Verified the ability to define User Type While Inviting or Adding Member by validating the below scenarios:
Admin must be able to select the user type ("Standard User" or "Platform Integration User") when inviting or adding a member.
The user type selection must be a required field.
"Standard User" should be the default selection.
Selected user type must determine the role and permissions automatically:
Standard Users get full access to all CodeScan features.
Platform Integration Users get limited access scoped to integration IDE tasks.
User type must be clearly labeled in the member management.
“Platform user cannot be added to the Owner group.” — should be displayed when the Owners group is selected for a Platform user. Additionally, the Send Invite button should be disabled in this case.
For multi-user invites, the flow should be the same as for a single invite. Invites can be sent in batches, but only for one user type at a time.
Able to see the standard and platform user type while adding a member to the organization
Add ESLint rules from @lwc/eslint-plugin-lwc
CodeScan has traditionally provided ESLint rules within our rules library. Separately, Salesforce has an official ESLint plugin to analyze LWC code:.
The rules in this plugin are different to our current set and expand on it; expanding the rules in our LWC set is vital to support the needs of our customers using Lightning Web Components.
Our aim was to include all rules from the GitHub - salesforce/eslint-plugin-lwc:
Official ESLint rules for LWC repository added to our current list. However, there are a few rules from this plugin that were not included.
Rules that weren’t added as part of LWC set:
Disallow duplicate class members (no-dupe-class-members). This wasn’t added because it’s a Deprecated Rule
Additionally, we did not include these 3 rules because of the Complex Parameter Type:
Enforce wire adapters to be used with wire decorator (no-unexpected-wire-adapter-usages)
Disallow usage of unknown wire adapters (no-unknown-wire-adapters)
Disallow access to global browser APIs during SSR (no-restricted-browser-globals-during-ssr)
Note that all of these LWC rules were added to our Salesforce Lightning Quality Profile.
Verified the Add Eslint rules from @lwc/eslint-plugin-lwc for the below scenarios: 1. Verified the 21 rules from the repository added to our Salesforce Lightning Quality Profile of javascript language. 2. Verified the Description, Rule Details, Type of issue, Remediation function, Severity for all the rules. 3. Verified that new rules is not included in the default Quality Profile. 4. Verified that violation is thrown for all the 21 rules.
Enhancement to Apex rule “Unused Formal Parameter” {sf:UnusedFormalParameter}
CodeScan has offered this rule since Dec 2017. Recently a customer reported that Unused Formal parameter doesn’t find when variables used in SOQL. We replicated this issue where CodeScan flagged a variable as an unused variable even though it is used in the SOQL string.
We have enhanced this rule to detect additional cases where string parameters are part of SOQL. The rule now detects cases where string params are used as part of building soql query.
Verified the enhanced logic of rule “UnusedFormalParameter” via the following scenarios. 1. Previously, a parameter (e.g., encounterIds) used in a SOQL string (e.g., WHERE Id IN :encounterIds) was wrongly reported as unused. Now, this is correctly detected as usage — no violation.
Also verified below cases all are working as expected Verified: Parameter used in SOQL with bind variable (:encounterIds) — no violation Verified: Parameter used via clause string assembly — no violation Verified: Parameter incorrectly concatenated into SOQL string — violation Verified: Parameter declared but not used anywhere — violation
Fixed issue ARM users recieving an error: “Component can't be null” while running a CodeScan analysis from ARM.
The issue is occurring in the SFDX retrieval. From ARM, when the user commits only the fields (or, for example, lookup fields), the .object-meta.xml is not retrieved. As a result, the retrieved file structure differs from what was expected. After analysing the rule’s implementation, it was found that the rule does not check if the .object-meta.xml file exists first and forcibly tries to throw the violation on the file. Hence, the "component can't be null" error is thrown. This required an engineering fix in the rule.
Note: The issue lies in one of the common methods many rules use, so this error is not confined to these two rules.
Other rules that use this method include:
With this fix, users are now able to see the violations for all 7 rules when running a CodeScan analysis from the ARM side using the CodeScan plugin:
sfmeta:CrossObjectFormulaOveruse
sfmeta:ObjectLookupsOveruse
sfmeta:RelationShipOveruse
sfmeta:ExternalIdOveruse
sfmeta:RollUpOveruse
sfmeta:LimitCustomFields
sfmeta:nCinoFieldHistoryTracking
Verified by committing only specific fields and triggering SCA analysis — violations appeared as expected.
Ran analysis for the entire Salesforce org, including objects — violations were also detected."
Fixed issue where after a user is deactivated, the user is still displayed on Members page
Some users were reporting that after a user is deactivated, the user is still displayed on the Members page.
Detailed Solution
Made changes in the codebase to remove the user from members table when the user is deactivated.
Enusresd that using “search” on the Members page only active users are retrieved.
The user is no longer able to login via SAML
Verified the below scenarios regarding users being displayed in Members page, and all scenarios are working as expected.
Create and Activate New User- User appears under the Members list of the active organization
Add User to Inactive Organization- User is visible under the Members list of the inactive organization
Deactivate User from Instance- User no longer appears in the Members list. Behavior confirms that deactivated users are excluded from the UI display
Verify SAML Login for New User- Authentication via SAML was successful
Fixed issue with rule “Avoid running Soql and DML inside loops” {sf:AvoidSoqlInLoops}
Recently, some customers reported unexpected behavior in this rule, producing false positives.
The root cause of the false positives is that when a method of an object is invoked within another method, and both methods share the same name, the current rule implementation incorrectly interprets this as a recursive call and subsequently triggers a violation. Further, the Stack Loop trace is indefinite.
This had been remediated in a previous release (25.1.2 release in June 2025). The updated rule logic now handles these edge cases by checking for method image to be exactly the same (method != diffObj.method).
However, there’s more to this issue and fix! A scenario which was earlier covered stopped working as expected as a result of the fix made above. This new issue was reported to us, and has been fully remediated in this release by adding additional logic to the rule implementation was made to accommodate both scenarios (the pre-existing condition but also indefinite stack loop trace).
Verified the Fix for rule sf:AvoidSoqlInLoops via several scenarios, including:
Verified – SOQL inside a method (not directly in a loop) — no violation as expected
Violations Expected for the below scenarios
Verified SOQL directly inside a for loop — got violation as expected
Verified SOQL inside nested if blocks within a loop — got violation as expected
Verified SOQL inside a try/catch block within a loop — got violation as expected
Verified SOQL in a method (or recursive call) invoked from a loop — got violation as expected
Verified SOQL in static helper method called from a loop — got violation as expected
Verified SOQL inside a while loop — got violation as expected
Verified SOQL inside a do-while loop — got violation as expected
Verified SOQL directly inside System.debug() within a loop — got violation as expected
No Violations Expected for the below scenarios
Verified Bulkified SOQL outside the loop (e.g., IN :ids) — no violation as expected
Verified SOQL in deep conditional logic but not inside a loop — no violation as expected
Verified SOQL inside try/catch block, not inside a loop — no violation as expected
Verified SOQL in method not called from a loop — no violation as expected
14. Verified SOQL inside constructor called from a loop — no violation (as expected for shallow analyzers)
Fixed issue regarding restricted access for CodeScan Platform Integration Users
Some users were reporting that their platform integration users has the same accessibility to CodeScan as their standard users. This issue is remediated in this release.
As a PIU (Platform Integration User) with restricted access in the CodeScan platform, PIU should only be able to view the Account section after logging in. All other features like Project Analysis, Project View, Issues View, and Search etc. (All except Account Section) should be inaccessible. Within the Account section, PIU should see the following tabs:
Profile
Security
Notifications
Projects
Additionally, the Help and Profile sections in the header should remain accessible. When clicking on the Profile icon, a pop-up should appear displaying (As shown in attached images):
Username, Email
My Account
Logout Option
Verified Restricted Access for CodeScan Platform Integration User by validating the following scenarios:
Verified all integration project analysis and PR analysis as a Standard user.
Verified all IDEs as a Platform user.
Verified IntelliJ, VS Code, GitHub Actions, SFDX, Sonar Scanner, and Azure as a Standard user.
Platform users should have access only to the My Account page.
Platform users should only be able to view the Projects and Organizations tabs—no actions should be permitted.
Both Standard and Platform users should have:
The Help section is accessible in the header.
The Profile section is accessible in the header.
On clicking the Profile icon, the Platform user should be able to see:
Username
My Account
Logout option
8. Verified Billing & Revenue Compliance for both Standard and Platform users.
Users who are Standard users in some organizations and Platform Integration users in other organizations should be shown the homepage of the organizations where they are Standard users upon login.
If Standard users do not have any homepage, they should be shown the My Projects page (All Projects), which should only display projects from the organizations where they are Standard users.
User type and UI should be organization-specific. If a user switches between organizations, the UI corresponding to their user type in the selected organization should be displayed.
If Standard users do not have any homepage, they should be shown the My Issues page (All Issues), which should only display issues from the organizations where they are Standard users.
Release Date: 6 July 2025
CodeScan 25.1.4 is comprised of the following 6 components:
1 New Features
3 Enhancements
2 Fixes
Component details are listed in their corresponding sections within this document.
1. Support for Enterprise Git Connections / Configuring & Managing ALM Integrations
In CodeScan, Enterprise Git Connections enable organizations to securely integrate with self-hosted or enterprise instances of GitHub, GitLab, and Bitbucket. Admins can configure these connections at the organization level using OAuth credentials and define allowed IP ranges for secure access. Once connected, these integrations streamline project onboarding by allowing users to directly link Git repositories during project setup for automated analysis and CI/CD workflows.
More detailed info can be found in our Knowledge Base here:
1. Enhancement to CodeScan Rule “URL Redirection to Untrusted Site” {sf:OpenRedirect}
CodeScan has traditionally used this rule to check against redirects to user-controlled locations. This is important because untrusted input could cause an attacker to redirect the user to a malicious site, thereby allowing the attacker to launch a phishing scam and steal user credentials.
However, our existing rule did not specifically check for the use of Network.forwardToAuthPage.
This rule has now been enhanced with this logic, and we have verified that users are now able to see the violation for the use of both Network.forwardToAuthPage and PageReference.
More details regarding the Network class can be found here: .
1. Enhancement to CodeScan decorations of SARIF Reports
Since the 24.0.6 release (June 2024), CodeScan was enhanced to decorate standard SARIF output. While CodeScan had been able to generate SARIF output before the 24.0.6 release, it’s noteworthy to mention that the SARIF output in GitHub does not contain the severity. As such, we added severity to our SARIF output, thereby allowing CodeScan to provide a more verbose presentation of the issues in GitHub. This change has been providing a better experience for our customers working in GitHub Actions.
The way this feature was originally designed was:
When generateSarifFile: true, the generated SARIF file includes all issues, both open and resolved. Additionally, the report contains detailed metadata such as Type and Severity for each issue.
When generateSarifFile: false, the generated SARIF file includes only open issues, and it does not include the Type and Severity information for the issues.
This means that when generateSarifFile is set to false, the generated SARIF file includes only open issues, but omits important metadata such as Type and Severity for each issue.
However, to maintain consistency and support downstream analysis tools, the SARIF file should always include detailed metadata for each issue, regardless of the generateSarifFile setting.
Thus, this enhancement expands upon the existing capability and introduces much more robust functionality.
With this release, when generateSarifFile: false or generateReportFile: true, the SARIF file:
Contains only open issues respective to the branch and PR
Includes full metadata for each issue, including Type and Severity for rules and results
More detailed information can be found here:
Verified the below types of analyses with SARIF report all are working as expected:
Commit request analysis
PR analysis
Merge analysis
SARIF reports
Verified the SARIF report with the parameter generateSarifFile: false/true in the YML file user is able to see the open issues of the specific branch or pr and also able to see the issue TYPE and SEVERITY in the SARIF report.
2. On the Billing Page, a banner was added that details the level of access users have within the CodeScan UI based on user license type
Customers who are using a user-based license model will now have a banner on their Billing Page that provides additional clarity regarding the CodeScan features available to users based upon their license type. Standard users will have access to all CodeScan features (although access can be restricted by admin based on user privileges). Platform Integration Users will only have access to their Profile, along with access to the Security Tab and the Notifications Tab. Additionally, both types of users can fully use the CodeScan extension for VS Code and IntelliJ.
1. Fixed issue where after a user is deactivated, the user is still displayed on Members page
Some users were reporting that after a user is deactivated, the user is still displayed on the Members page.
Detailed Solution
Made changes in the codebase to remove the user from members table when the user is deactivated.
Ensured that using “search” on the Members page, only active users are retrieved.
The user is no longer able to login via SAML
Verified the below scenarios regarding users being displayed in Members page, and all scenarios are working as expected.
Create and Activate New User: User appears under the Members list of the active organization
Add User to Inactive Organization: User is visible under the Members list of the inactive organization
Deactivate User from Instance: User no longer appears in the Members list. Behavior confirms that deactivated users are excluded from the UI display
Verify SAML Login for New User: Authentication via SAML was successful
2. Fixed issue with codescan-scanner-action (occurring after CodeScan upgrade)
Some users were reporting that when their CodeScan project was upgraded to CodeScan 24.12.0.100206, it was incompatible with our codescan-io/codescan-scanner-action (and thus breaks customers’ GitHub Actions pipelines for pull request scanning).
This issue is remediated with this fix.
Validated that all below scenarios are working as expected.
Verified the GitHub Actions runner when using runs-on: ubuntu-latest
Verified the GitHub Actions runner when using runs-on: macos-latest
Verified the GitHub Actions runner when using runs-on: windows-latest
Verified the GitHub Actions if JRE and Sonar Scanner is not present in cache and also Verified the logs if JRE and Sonar Scanner are present in the cache.
Release Date: 22 June 2025
Summary:
CodeScan 25.1.3 is comprised of the following 5 components:
3 Enhancements
2 Fixes
Component details are listed in their corresponding sections within this document.
1. New Banner in billing when license entitlements exceeded
In this release, we created a new banner to inform admins when their licenses entitlements have been exceeded. It advises the admins to contact their account team to get their entitlements amended.
Separately, the AutoRABIT account team will be notified directly as well.
In the example shown, Customer X is licensed for 2 Platform Users, but currently have 4 Platform Users activated in their Org. As such, the banner appears to advise the admins of this discrepancy.
Additionally, this new banner is coupled with additional billing logic (detailed in the next note) aimed to ensure that user operations are not disrupted when license entitlements are exceeded, providing a better user experience for our customers.
2. New logic in billing allows users continued operations
In this release, we made an update so that users are not blocked when an organization exceeds their license entitlements. Instead, a new banner will appear on the billing page advising the admins that their license entitlements have been exceeded (see previous note above).
This feature also ensures that user operations are not disrupted when license entitlements are exceeded, providing a better user experience for our customers.
3. Project Report Status update in UI
Several customers had previously reported that on the Project Report page, the UI displays the Project Report as “stuck” in the queue. This status persists even after users receive the corresponding email notification in Outlook.
We have remediated this issue with this release by updating the status in the UI to "Your project report is currently being processed. You will receive it via email shortly."
Verified that the 4 scenarios below are working as expected
3.1 - "Verified: The updated message after enabling project reports and enabling the received scheduled reports in the CodeScan UI."
3.2 - "Verified: The updated message after enabling project reports and disabling the received scheduled reports in the CodeScan UI."
3.3 - "Verified: The updated message after disabling project reports in the CodeScan UI."
3.4 - Able to receive the project reports via email for all the above three case
1. Fixed issue with certain menus where users were unable to easily scroll down and choose a value from the menu
Some users were reporting that they were unable to scroll down in the quality profiles section in project settings.
This issue has been remediated in this release.
The dialog box was resized.
We have verified that with this fix, users are able to scroll down in the Quality Profiles section within the Project Settings. We also verified that the dialog box is resized.
2. Fixed Deprecation Warning associated with sonar.login
Some customers were reporting that they were
receiving deprecation warnings in their scans indicating that the use of sonar.login is deprecated, and that instead, going forward, authentication should be done using sonar.token.
This issue has been remediated in this release. CodeScan now supports both sonar.login and sonar.token for authentication during Codescan analyses.
Verified the below plugins by using sonar.token and sonar.login parameters in the sonar command and sfdx; both scenarios are working as expected.
SFDX -@salesforce/cli/2.61.8
Sonar-scanner - 5.0.1.3006V
Validate Project analysis through above plugins
Validate branch analysis.
Release Date: June 11, 2025
CodeScan 25.1.2 is comprised of the following 19 components:
· 3 New Features
· 3 Enhancements
· 2 New Rules
· 11 Fixes
Component details are listed in their corresponding sections within this document.
We have added CWE Number and additional CWE numbers (95 and 470) to the rule “Unescaped Value Could Cause XSS”
Verified the CWE number on the rule Unescaped Value Could Cause XSS by confirming that user is able to see the added CWE Number (along with additional CWE numbers 95 and 470)
Please note, these rules are only available for projects created with CodeScan's direct Salesforce integration due to being based on a direct query to a Salesforce Org.
2. Disable “Invite Members" option
Invite members is a feature in CodeScan designed for organizations using Auth0 for authentication. In contrast, it is not applicable for SSO enabled environments.
To date, SSO customers would have access to this feature, even though the functionality would not be enabled for them. We recognize that this can cause confusion and lessen the user experience. As such, we have added a new option in CodeScan allowing any organization to disable the “Invite Members” functionality in CodeScan.
Description
The "Disable Invite Members" option in Administration > Organization Settings of CodeScan allows Organization Admins to control the visibility of the "Invite Member" button. By default, the option is active or visible. When enabled, the "Invite Member" button is hidden for users, while disabling it keeps the button visible and functional.
Verified below scenarios, all are working as expected 1. An option/toggle called "Disable Invite Members" should be available in Administration > Organization Settings of CodeScan.
The default behavior of the invite member option should be active or visible.
When the toggle is enabled, the "Invite Member" button is hidden in administration module and members page
When the toggle is disabled, the "Invite Member" button remains visible and functional as usual in administration module and members page
Other functionalities related to member management (e.g., viewing members, editing permissions) should remain unaffected.
Able to invite users to the codescan organization
Restricting Platform Integration User Access for Standard Users
This feature ensures that standard users who manage user access cannot switch their role to a Platform Integration User, so that user permissions are maintained correctly.
Preventing Standard users with System Admin Permission from switching to a Platform Integration User role will reduce potential misconfigurations and ensure compliance with user access policies. To enforce this, we have implemented an alert and disabled the option in the UI. This will give administrators better control over role assignments and prevent unintended access changes.
On the Members page, the following alert "You are a System Admin. You are required to have a Standard User License.“ is displayed.
Verified the Restricting Platform Integration User Access for Standard Users via the following: 1. Verified admins are able to see the alert “You are a System Admin. You are required to have a Standard User License.“ if Standard users with System Admin Permission try switching to a Platform Integration User.
Verified admins are able to change users from standard to platform if standard user is without System Admin Permission
Verified admins are able to see the alert “You are a System Admin. You are required to have a Standard User License.“ if user is owner and trying to switch from standard to platform user
1. Enhanced rule “vf:AvoidJavaScriptScriptlets” by adding a new parameter to the rule
Historically, CodeScan has offered our “Avoid JavaScript Scriptlets” rule to inspect customer’s code and flag where there JavaScript Scriplets.
With this release, a new parameter was introduced to allow users to choose whether to include or ignore violations related to code supporting the Lightning functions within script.
Parameter Name: ignoreSupportingCode
Type: Boolean (true or false)
Default: false
Description: This option allows users to ignore violations related to code supporting the Lightning functions within script. By default, it is set to false.
Verified the below scenarios for rule vf:AvoidJavaScriptScriptlets and report that all scenarios are working as expected.
Validated the rule with LightningFunctions and set the default value false then user is able to see the violations.
Validated the rule with LightningFunctions and set the value true then user is not able to see the violations which is expected.
Validated the rule without LightningFunctions then user is able to see the violation which is expected.
Validated the rule by setting the parameter ignoreSupportingCode as false/true working as expected.
1. Enhanced rule “Controller Naming Convention” for Apex and Visualforce
Some customers are reporting that CodeScan is flagging violations on components that should not be flagged (i.e., SandboxRefreshAdminController)
This issue is remediated in this release.
We validated the fix by:
Creating a class file in salesforce org using UI and name the controller like in example.
Creating a vf page in salesforce org with the controller attribute like shown in the example.
Setting parameters for controller naming in CS, try the parameters with different cased letters ex: ConTroLLer etc.
After scanning false positives should not be visible
2. Updated description for Deprecated rules
Historically, CodeScan has deprecated rules over time. However, we recognize that we can be clearer about why the rule is being deprecated. In this release, we have initiated this practice (and plan to adhere to this practice in the future).
1.Update the description of deprecated Apex Rule “Use System.assertEquals instead of System.assert“ and key”sf:UseAssertEqualsInsteadOfAssertEquality” with the following:
This rule detects unit test assertions in object references equality. Instead of using System.assert combined with "==" as an equality operator, these assertions should be made by more specific methods, like assertEquals.
This rule has been deprecated, as Salesforce recommends using the Assert class for unit tests. Please remove this deprecated rule from your custom Quality Profile and instead add the rule sf:UseAreEqualInsteadOfAssertBoolean.
2.Update the description of deprecated Apex Rule “Use System.assertEquals instead of System.assert“ and key”sf:UseAssertEqualsInsteadOfAssert” with the following:
This rule detects Unit test assertions in object references equality. Instead of using System.assert combined with ".equals()" as an equality check, these assertions should be made by more specific methods, like assertEquals.
This rule has been deprecated, as Salesforce recommends using the Assert class for unit tests. Please remove this deprecated rule from your custom Quality Profile and instead add the rule sf:UseAreEqualInsteadOfIsTrue
3.Update the description of deprecated Apex Rule “Use System.Assert instead of System.assertEquals“ and key”sf:UseAssertInsteadOfAssertEquals” with the following:
When asserting a value is the same as a boolean literal, use System.assert, instead of System.assertEquals.
This rule has been deprecated, as Salesforce recommends using the Assert class for unit tests. Please remove this deprecated rule from your custom Quality Profile and instead add the rule sf:UseIsTrueInsteadOfAreEqual
4.Update the description of deprecated Apex Rule “Unnecessary Parentheses“ and key”sf:UnnecessaryParentheses” with the following:
Sometimes expressions are wrapped in unnecessary parentheses, making them look like function calls.
This rule has been deprecated. Please remove it from your custom Quality Profile and instead add the rule sf:UselessParentheses as a best practice for code styling.
1. Server Side Request Forgery
This is a rule that checks for any changeable inputs to a url string in a method that returns a PageReference.
Type: Vulnerability Severity: Critical Name: Server Side Request Forgery (SSRF) Key: ServerSideRequestForgery Message: Sanitize input to avoid possible SSRF Description: This rule identifies potential Server-Side Request Forgery (SSRF) vulnerabilities by detecting unsafe URL construction and external network requests that could allow an attacker to manipulate server-side network calls.
Server-Side Request Forgery (SSRF) occurs when an attacker can influence the server to make arbitrary network requests, potentially accessing internal resources, sensitive endpoints, or bypassing security controls.
Input can be cleansed by using Id.valueOf, Date.valueOf, etc. Or escaped using String.escapeSingleQuotes().
Parameters Name: sanitizationMethod Description: A comma separated list of custom methods that provide input sanitization.
CWE: 918
Test Cases with Violations 1.Validated direct embedding of user input into a URL without sanitization, resulting in a violation (SSRF) as expected
2.Validated unescaped dynamic input into URL, resulting in a violation (SSRF) as expected.
3.Validated that one parameter is sanitised but the other is not sanitised, still resulting in a violation (SSRF) as expected
4.Validated concatenated unsafe dynamic parameters in a URL, resulting in a violation (SSRF) as expected.
5.Validated the presence of a malicious SSRF-style payload embedded in the URL, resulting in a violation (SSRF) as expected.
6.Validated the attempt at "sanitization" using regex, which is not an approved method, resulting in a violation (Improper sanitization) as expected
Test Cases with No Violations
1. Validated input sanitized using Id.valueOf, resulting in no violation as expected.
Validated input escaped using String.escapeSingleQuotes, resulting in no violation as expected.
Validated that the URL starts with "/" ensuring an internal redirect, resulting in no violation as expected.
Validated date validated using Date.valueOf, resulting in no violation as expected.
Validated a static URL with no dynamic input, resulting in no violation as expected.
Validated fully escaped input and use of safe methods, resulting in no violation as expected.
NOTE: The implementation currently addresses the most common scenarios related to resource injection and SSRF vulnerabilities. However, due to the dynamic and context-dependent nature of these issues—especially when influenced by external inputs, indirect references, or complex backend behaviors—there may be edge cases that are not readily identifiable or testable. These may only surface under specific configurations or data conditions.
Resource Injection
Prior to this new rule, CodeScan did not catch resource injection in Apex.
This is very similar to (also included in this release)
However, there are some basic things that make it resource injection and not SSRF.
In this example:
public PageReference init(){
AccListString = 'INIT';
BaseObjId = system.label.MY_Label;
return null;
}
public PageReference prepareAccs(){
String newUrl = '/apex/maps__Maps?baseOjectId='+BaseObjId+'&recordIds='+AccListString;
PageReference p = new PageReference(newUrl);
p.setRedirect(true);
return p;
}
Here, we are looking at resource injection because the URL is internal (starts with / )
This rule should find any external variables that are used to create dynamic internal URLs.
Acceptance Criteria
Type: Vulnerability Severity: Critical Name: Resource Injection Key: ResourceInjection Message: Sanitize input to avoid possible resource injection Description: This rule identifies potential resource injection vulnerabilities by detecting unsafe URL construction for internal network requests.
Resource injection occurs when user-controllable data is used to specify a resource identifier without proper validation.
Input can be cleansed by using Id.valueOf, Date.valueOf, etc. Or escaped using String.escapeSingleQuotes().
See:
- Improper Control of Resource Identifiers ('Resource Injection')
Tags: cwe
Remediation Time: 10 minutes
Parameters: Name: sanitizationMethod Description: A comma separated list of custom methods that provide input sanitization.
CWE: 99
Verified the below scenarios are all working as expected
Verified that sanitizing both BaseObjId and AccListString before URL building prevents violations.
Verified that validating BaseObjId using Id.valueOf() ensures the ID is valid and safe to use in URLs.
Verified that input AccListString validated with regex and sanitized prevents violation.
Verified that using AccListString directly in URL without any sanitization or validation causes violations.
Verified that sanitizing only BaseObjId but not AccListString leads to a violation.
Verified that sanitizing the URL string after using variables has no effect, resulting in a violation.
Verified that URL encoding AccListString without further format validation leads to violation
Verified that replacing characters rather than proper sanitization leads to security violations.
NOTE: This implementation currently addresses the most common scenarios related to resource injection and SSRF vulnerabilities. However, due to the dynamic and context-dependent nature of these issues, specially when influenced by external inputs, indirect references, or complex backend behaviors—there may be edge cases that are not readily identifiable or testable. These may only surface under specific configurations or data conditions.
1. Fixed issue with the CSV Export not functioning properly with all nCino projects
We detected that some nCino projects are unable to export to CSV. The issue occurs after 500 records are returned (where the request does not contain the necessary data).
This issue is remediated in this release. We verified the fix and are now able to export the issues exceeding 500 records for all ncino projects (as expected)
2. Fixed 2 issues with our SOQL Injection rule
We have discovered that the issues flagged disappear on different lines; we have also discovered that CodeScan doesn’t find the fflib method escape.
These 2 issues are remediated in this release.
3. Fixed issue with the rule “Page layout name contains special characters” (sfmeta:PageLayoutNaming)
Some customers were reporting that CodeScan was flagging that their Page layout name contains special character even though they didn't add any special characters.
This issue has been remediated in this release.
4. Fixed issue with the rule “vf:UnescapedAttributes vulnerability” {where false positive violations were being flagged}
CodeScan suggests the remediation for this issue is to use JSENCODE() to escape values. However, some customers reported that when this is added to their code, the issue was still being flagged as a violation. We validated the fix by:
Verified the updated description and example under rule: vf:UnescapedAttributes vulnerability
• Verified that Rule is throwing violation as expected
This CodeScan rule was updated with the following changes:
1. Changed the description to the following:
Reflected Cross-site Scripting (XSS) occurs when an attacker injects browser executable code within a single HTTP response.
Using unescaped parameters can be a security risk. c:* and apex:* attributes are not checked unless they are known to cause problems. You can check other attributes by adding them to the configuration for this rule.
In Visualforce, escape methods such as JSENCODE can be used to sanitize variables as shown below.
For Aura components, sepcifically aura:unescapedHtml, make sure to sanitize variables in controllers before using them. This component is intended to output properly sanitized HTML from a trusted source. If properly handled, mark the issue as Resolved: False Positive/Won't Fix.
2. Added the following Aura Example Bad Scenario:
Example :
<aura:component>
<aura:unescapedHtml value="{!v.htmlstring}"/>. //Bad: not recommended.
</aura:component>
5. Fixed issue with the rule “Open Redirect” (sfmeta:PageLayoutNaming) {where false positive violations were being flagged}
Some customers reported that our current rule does not handle the use of “Network.forwardToAuthPage”
We remediated this issue and validated that CodeScan now throws a violation in both of these cases.
Verified the rule “Open Redirect” by validating:
Users are able to see the violation for the use of both Network.forwardToAuthPage and PageReference
More info regarding “Network class” can be found here:
Fixed issue with the rule “Field Level Security Vulnerabilities” (sfmeta:PageLayoutNaming) for classes using “Without Sharing” {where false positive violations were being flagged}
Some customers have reported an issue with CodeScan's reporting of "Permissions should be checked before accessing resource" vulnerabilities in our Apex codebase, specifically within classes that are declared without sharing.
The without sharing keyword in Apex classes causes the code to execute in system context, bypassing standard Salesforce sharing and field-level security checks. This is intentional for certain system-level operations and utility classes within our application.
However, CodeScan is flagging fields within these without sharing classes as vulnerabilities, stating "Permissions should be checked before accessing resource." This is creating an inflated number of false positives and incorrectly portraying our code's security posture.
CodeScan is designed to identify potential security issues; however, in the context of without sharing classes, these field-level security checks are redundant and misleading.
As such, the rule update in this release enables CodeScan to recognize that when a class is declared without sharing, field-level security checks are irrelevant, and the "Permissions should be checked before accessing resource" rule is suppressed for fields within without sharing classes.
Note that a new parameter has been added to this rule to Ignore Without Sharing
Name: ignoreWithoutSharing Message: When this parameter is true, this rule ignores Field Level Security issues in all without sharing classes. Default: false
Appropriately, CodeScan is flagging violations properly when “with sharing” is used.
Fixed issue with CodeScan’s APEX parser
Some customers reported that the CodeScan parser was incorrectly flagging valid Apex code using the UPDATE AS SYSTEM syntax as a parsing error. This was occurring because the parser doesn't recognize the AS SYSTEM portion of the UPDATE statement, leading to a ParseException and preventing accurate code analysis.
This issue has been remediated with this release.
We had previously verified the Parsing error in APEX Code for DML queries if user using UPDATE AS SYSTEM syntax would throw the parser exception. With this fix, users are now able to see the violations as expected for the file.
Verified the below queries in Apex code that users do not get any Parser errors; instead the updated CodeScan parser is working as expected.
INSERT AS SYSTEM
DELETE AS SYSTEM
UNDELETE AS SYSTEM
UPDATE AS SYSTEM
Fixed issue with rule “Avoid running Soql and DML inside loops” {sf:AvoidSoqlInLoops}
Some customers reported unexpected behavior in this rule, producing false positives.
The root cause of the false positives is that when a method of an object is invoked within another method, and both methods share the same name, the current rule implementation incorrectly interprets this as a recursive call and subsequently triggers a violation. Further, the Stack Loop trace is indefinite.
This has been remediated in this release. The updated rule logic now handles these edge cases by checking for method image to be exactly the same (method != diffObj.method).
We have verified the fix across related and existing test cases and edge conditions by confirming that if a method of an object is invoked within another method, and both methods share the same name, the user will not see the violation (as it is false positive).
Fixed issue with rule “RequireDescriptionComponent”
Some customers reported that the CodeScan rule “RequireDescriptionComponent” rule was not working for custom fields on standard objects.
This issue has been remediated in this release. Previously, CodeScan offered a rule “sfmeta:RequireDescriptionField” which had been deprecated for this updated rule. But the updated rule was not designed for standard objects. When we tested the logic of the deprecated rule, we found that it could be used for reference for this update to the new rule “RequireDescriptionComponent”
The rule enhancement was verified via the below scenarios 1. Verified Custom Field on Standard Object – Missing Description
Verified Custom Field on Custom Object – Missing Description
Verified Standard Fields on Standard Object – Missing Description
Verified Custom Field on Standard Object – With Description
Verified Custom Field( With Description) on Custom Object (Without description)
10. Fixed issue with rule “sf: FieldLevelSecurityRule”
During maintenance testing, we discovered that this rule was triggering the null pointer exception when parsed through the trigger files. In the rule logic it was searching for relevant ASTClassOrInterfaceBody to get all the constructors in that class. Since triggers don't have constructors, control flow proceeds further if we get a non-null node for ASTClassOrInterfaceBody. We updated this rule to parse the trigger files by adding extra logic to find the Trigger specific nodes (TriggerBodyDeclaration etc).
We tested the fix to the Null pointer Exception with sf: FieldLevelSecurityRule and verified we are now no longer able to see the Null pointer exception for the trigger files in the logs (as expected).
11. Fixed issue with Organization images displaying as large icons in the org list
CodeScan has historically allowed images to be added under Organization settings by our customers. These images are then displayed on the organization home page and in the Org list.
After we released CodeScan 25.1.0 (April 2025), customers org icon images could appear as large icons. This issue was remediated in this release by restricting the size of the image on the Org page to the size of a usual non-image icon (around 30px).
We have verified the Organization image is now restricted in size, and users are able to see the image as expected.
Release Date: May 11, 2025
CodeScan 25.1.1 is comprised of the following 3 components:
3 Fixes
Component details are listed in their corresponding sections within this document.
There are no New Features associated with this release
There are no Enhancements associated with this release
There are no New Rules associated with this release
Fixed an issue with rule tags blocking analyses
Several customers reported that, after the recent CodeScan upgrade to 25.1.0, some of their analyses were not properly executing. We uncovered that this was due to new logic added to a database table. This fix corrects this issue and will allow all blocked analyses to run properly.
We have verified the below scenarios and report that all are working as expected.
Tags which are system default
Tags which are not system default
Custom tags
Verified the vf:exception and sf:exception rule by adding tags in one organization and seeing the analysis working without any issue in that org or any other org.
Verified the analysis for the rule sf:exception by assigning the tags. Confirmed analysis was successful and that users are able to see the assigned tags in the issues page.
Verified the analysis when the tags are not assigned. If there are any new violations the user is unable to see any tags for the violations (which is expected).
Fixed Error: [CS] API GET status code: 404 when users try to generate Sarif File on their environment
Several customers reported the following error “Error: [CS] API GET status code: 404 “when users try to generate Sarif File on their environment.
This fix corrects this issue and will allow users to generate Sarif files on their environment.
We have verified the below scenarios for GitHub Actions SARIF report on TEST environment and are able to generate SARIF reports successfully.
Analysis is getting “success” and able to get the SARIF report where the results are same in the report and on CodeScan UI
Validated the Pull request analysis in GitHub actions we are able see that the PR analysis is happening for the changed files.
Validated the Commit request analysis.
Validated the PR analysis.
Validated Merge analysis.
Fixed Error: [CS] API GET status code: 404 when users try to generate Sarif File on their environment
After the upgrade to 25.1.0, we uncovered 2 minor issues:
The IDP group mapping feature flag was not working as expected.
If an ID user is member of org 1 and owner of org 2, then from org2 SAML connection she was able to make anyone an owner of org1.
This update remediates these 2 issues.
Verified the IDP Group Mapping flag by Enabling and Disabling the instance is now working as expected.
Release Date: 20 April 2025
CodeScan 25.1.0 is comprised of three main components / features:
Component details are listed in their corresponding sections within this document.
In this release, we have updated the CodeScan User Interface order to provide four key benefits:
Easier navigation, which provides both an improved, intuitive experience for more advanced users, while reducing the learning curve for new users
Consistency in screen layout, providing a more cohesive experience throughout the application
Enhanced performance and responsiveness within CodeScan
Brand modernization alignment with other AutoRABIT solutions
The CodeScan 25.1.0 contains various technical architecture improvements and upgrades to various libraries. We have also included several enhancements to CodeScan’s security architecture.
Fixed a false positive in the 'sf:AvoidGlobalModifier' rule. The violation is now ignored for global classes used as return types in any global static method.
123 Main Street, New York
123 Test Street, Test City
wmc=100, atfd=10, tcc=0.2 Result: No violation
wmc=9999, atfd=9999, tcc=0 Result: No violation
wmc=0, atfd=0, tcc=0 Result: No violation
wmc=0, atfd=0, tcc=1 Result: Everything violates
Instance-level Admins can restore the organization within 30 days of deletion.
After 30 days, the organization is permanently deleted unless restored.
Customers can notify us in writing to forgo the 30 days and have the instance deleted immediately, which we will perform at their request
Aligns with standard enterprise-grade administrative controls.
*.documentforce.com
*.marketingcloudapis.com
We also verified that usage of any of the below URLs in the code now triggers a violation after activating the AvoidAbsoluteURL rule.
Verified the VS Code plugin on the self-hosted environment. After the user refreshes the connection, the resolutions are displaying as expected.
Also verified on the Self-Hosted environments (SQ versions 25.1 and 25.2):
When the user sets an issue as False Positive or chooses to Accept the issue, the issue count is reduced on the UI as expected.
Any iteration (for, while, do) in a trigger is a violation, regardless of whitelist.
Any non-whitelisted method calls.
Any direct DML, SOQL, or field logic.
Variables assigned from whitelisted methods used later in invalid contexts (like while(var)).
HttpRequest.setEndpoint(String)
PageReference.getContent()
HttpRequest.setEndpoint(String)
PageReference.getContent()
x =+ y; assigns +y instead of adding.
This new logic will prevent developers from introducing subtle logic bugs caused by operator misuse. Further, we updated the rule example with the following:
Visibility
The containing class uses the implements keyword with one of the known Salesforce interfaces (e.g., Schedulable, Database.Batchable).
Parameter types match exactly, including types such as:
SchedulableContext
Database.BatchableContext
Validated the SAML connection creation and login through SSO in the created Org.
Validated the SAML connection creation and login through SSO with the other Org.
Created a new user and checked the login through SSO with the same above SAML config.
Verified the IDP group mapping where the user is mapped to the organization where SAML connection is created.
If the QP has no profile name, the error message says: "Profile name should be set."
If no file is selected during import, an error occurs.
If the repository key is missing, an import error is triggered.
If a QP with profile name CodeScan way/CodeScan strict way/CodeScan nCino way name is imported, an error is thrown.
If invite sent to non-corporate domains, the following error is thrown:
Existing historical issues should reflect the new status names in the export, even if their status was stored using legacy labels.
Confidentiality Impact (C) (specify)
Integrity Impact (I) (specify)
Availability Impact (A) (specify)
Modified Scope (MS) (specify)
Modified Confidentiality Impact (MC) (specify)
Modified Integrity Impact (MI) (specify)
Modified Availability Impact (MA) (specify)
Confidentiality Requirement (CR) (specify)
Integrity Requirement (IR) (specify)
Availability Requirement (AR) (specify)
Supports security and compliance needs by maintaining a clear separation between user types.
Billing Page User Count Verification- User count reflects the new user addition appropriately. Billing data is updated as per user assignments
Verified SOQL inside interface/abstract method (called via polymorphism from loop) — no violation as expected
Billing Page User Count Verification: User count reflects the new user addition appropriately. Billing data is updated as per user assignments
Verified the below type of analysis (with SARIF report) are all working as expected.
Commit request analysis.
PR analysis.
Merge analysis.
SARIF reports.
Verified the SFDX analysis (with SARIF report) the analysis is successful and able to generate the SARIF file locally where user is able to see the tags, rule text, results, type of the Bug and type of the Severity.
Verified the S3 integration the analysis is successful.
Verified the CodeScan extension in the Azure DEVOPS plugin on the TEST instance working as expected.
Verified the main/default analysis which is successful.
Verified the branch analysis which is successful.
Verified the below sonar scanner versions
sonar-scanner-5.0.1.3006 - Analysis is successful
sonar-scanner-6.0.0.4432 - Analysis is successful
sonar-scanner-6.2.1.4610 - Analysis is successful
sonar-scanner-7.1.0.4889 - Analysis is not successful (threw exception; nested exception is org.bouncycastle.crypto.fips.FipsOperationError: org.bouncycastle.crypto.fips.FipsOperationError: Module checksum failed: expected)
Object
Fields Likely to Contain PII
Contact
Birthdate, Department, Email, Fax, FirstName, HomePhone, LastName, MailingAddress, MiddleName, MobilePhone, Name, OtherAddress, OtherPhone, Phone, PhotoUrl, Title
Lead
Address, Company, Email, Fax, FirstName, Industry, LastName, MiddleName, MobilePhone, Name, Phone, PhotoUrl, Title, Website
User
Address, CompanyName, Department, Email, Fax, FederationIdentifier, FirstName, FullPhotoUrl, LastName, MiddleName, MobilePhone, Name, Phone, Title, Username
Account (Business)
BillingAddress, Fax, Name, Phone, PhotoUrl, ShippingAddress
Account (Person Account Fields)
FirstName, LastName, MiddleName, PersonBirthDate, PersonEmail, PersonHomePhone, PersonMailingAddress, PersonMobilePhone, PersonOtherPhone, PersonTitle
Data Type
Original/Real PII (Violation)
Dummy/Masked Data (Compliant)
Phone
9876543210
5551234567 or 0000000000
SSN
123-45-6789
000-00-0000 or null
Credit Card
4111111111111234
4111111111111111 (Visa test number)















































































































































































































Address








Release Date: 7th December 2025
Support Case: #160228
Resolved an issue where the IgnoreWarnings flag from the UI was not passed correctly, causing prevalidation to fail on warnings even when the checkbox was selected. Updated the UI request mapping so the correct value is stored and processed by the backend.
Support Case: #172715
"The issue preventing users from selecting the Release Label and other options in the Change Label module under VC has been resolved by updating the routing mechanism to router.go, restoring proper navigation from both the left menu and top bar"
Release Date: 30 November 2025 Fixed an issue where scheduled jobs could not be deleted through Environment Provisioning. The system now correctly validates permissions and job eligibility, enabling successful scheduled job removals from target environments. Support Case: #159287
A performance optimization was implemented to improve how UserVersionControl details are retrieved. Instead of fetching data individually for each user, the system now retrieves the required information in a single bulk operation and processes it efficiently. This significantly reduces load time and restores a responsive user experience in EZ-Merge. Support Case: #158633
Release Date: 23 November 2025 EZ-Merge report timestamps now adjust accurately to each user’s time-zone settings, ensuring Merge Submission, L1 Review, and L2 Review dates display consistently across regions. Support Case: #156046
CI Job validation behavior has been streamlined so that the Build Now option becomes available in the UI whenever the job’s deploy and overall status reach a completed state, providing a more consistent experience. Support Case: #158357
Backup-to-VC jobs now present the appropriate Git message during push scenarios, such as permission or hook restrictions, while clearly indicating “No modifications” only when no updates are present—offering more accurate visibility into job outcomes. Support Case: #159296
Delta commit results now reflect completion accurately, ensuring that the commit status aligns with the actual execution of the delta operation. Support Case: #150240
Release Date: 16 November 2025 Highlights: Improved downstream CI chaining, expanded Agentforce support, optimized EZ-Commit performance, and key platform upgrades.
Downstream CI job chaining enhancement AutoRABIT now allows downstream CI jobs to trigger even when a parent job completes without identifying artifacts during the delta build process. This removes unnecessary pipeline breaks, eliminates manual intervention, and ensures uninterrupted job chaining, especially for Vlocity and other metadata patterns where no-change builds are common. (This would be available basis only on feature flag). Expanded Agentforce metadata support ARM now supports a wider set of Agentforce metadata types across CI, Deployments, and Version Control flows.
Rollback failure fix for DX CI Jobs involving consecutive RecordTypes and StandardValueSets A rollback issue caused DX CI Jobs to fail when only RecordTypes and StandardValueSets were selected but CustomLabels were excluded, resulting in a “not found in package.xml” error. The rollback logic has been updated to respect user-selected members, ensuring successful rollback operations even when other components are omitted. Destructive rollback continues to exclude RecordTypes due to Salesforce API limitations. (Support Case: 155931)
EZ-Commit in-flight fetch optimization Introduced an in-flight check to prevent repeated fetch calls during EZ-Commit table data loading. The update adds a fetch-state tracker, improves the loading indicator, stabilizes table rendering to occur only after a successful fetch, and resets state cleanly on errors resulting in faster UI responsiveness and reduced redundant API calls. (Support Case: 155994)
Tomcat upgrade to version 11.0.13 ARM’s application runtime has been upgraded to Tomcat 11.0.13, delivering improved security, better performance, and alignment with the latest Java ecosystem standards. (Support Case: 158573)
Release Date: 9 November 2025 Highlights
Salesforce is deprecating the “username + password + security token” login method for SOAP API integrations, and ARM now supports OAuth (JWT) authentication to ensure uninterrupted connectivity from API 65. This release also adds support for Salesforce Metadata API version 65, introduces a CodeScan configuration wizard for easier setup, enhances audit visibility with CEF login logs, and fixes CaseTeamRole handling for multi-word names in environment templates. Salesforce SOAP Login Deprecation Notice Salesforce has deprecated the “username + password + security token” authentication method for integrations using the SOAP API starting with version 65. This legacy method will be completely disabled by Summer ’27 for API versions 31–64. Customers using this method in AutoRABIT connections (e.g., {{ConnectionName}}) must migrate to OAuth (JWT Bearer) authentication to ensure uninterrupted connectivity. The migration can be done through Connections → {{ConnectionName}} → Migrate to OAuth, followed by the on-screen steps to confirm the connection status as “OAuth (JWT)”. Salesforce Metadata API Version 65 Support ARM now supports Salesforce Metadata API version 65, ensuring full compatibility with the latest metadata structures introduced by Salesforce. As part of this release, ARM has validated several metadata types across both DX and Non-DX environments, enabling consistent retrieval, validation, deployment, and CI/CD operations.
CodeScan Configuration Wizard for Repository and Org Mapping Introduced a guided configuration wizard for CodeScan integration to simplify project and branch mappings across ARM repositories and Salesforce orgs. The system now intelligently pre-matches existing CodeScan projects and branches, allows users to persist mappings, and ensures consistent baseline comparisons across Commit, Merge, CI Jobs, Custom Deployment, and SCA modules. This minimizes redundant project creation and improves scan relevance. CEF Logger Added for Login Events ARM now logs both successful and failed user login attempts through the Common Event Format (CEF) logger, improving traceability and compliance visibility for system administrators. (Support Case: 156220)
Environment Provisioning Template – Multi-Word Case Team Role Names ARM now handles the creation and execution of environment provisioning templates containing multi-word CaseTeamRole names (e.g., “VMI Specialist”, “Supply Chain Finance”). The template execution correctly supports full role names and ensures accurate reflection in the target Salesforce org. (Support Case: 154640, 152188)
Release Date: 2 November 2025 Highlights: Improved validation visibility, enhanced deployment reliability, and Data Cloud DevOps support introduced.
Data Cloud DevOps Support Introduced full support for Salesforce Data Cloud metadata deployment using DevOps Data Kits. Users can now commit, validate, and deploy Data Cloud components such as Data Streams, Data Model Objects, Calculated Insights, and Data Packages through EZ-Commit, Deployments, and CI Jobs.
Key highlights include:
Deployment support for DataPackageKitDefinition, DataSourceBundleDefinition, DataStreamTemplate, and DataKitObjectDependency.
Strict separation between Data Cloud and standard Salesforce metadata for packaging.
Prerequisite checks for permissions and Data Cloud-specific access.
Recommended DX repository usage and manifest-based commit flow for Package.xml-dependent metadata.
Partial FlexiPage Commit Handling Fixed an issue where FlexiPage metadata was partially committed during Prevalidation Commits, resulting in missing content during CI Job deployment. Added schema validation checks to ensure full FlexiPage integrity and introduced detailed logging for file uploads on the Review Artifact screen. (Support Case: 155665)
App Deployment Failure in Profile Manager Addressed a “Malformed request detected” error encountered during “Apps” deployment using the Profile Manager process. Deployments now complete successfully, and changes are accurately reflected in the target Salesforce org. (Internal)
Validation Circle Color Accuracy During Code Coverage Failure Resolved an issue in EZ-Commit where both validation circles appeared green even when Salesforce validation failed due to insufficient code coverage. The circles now correctly turn red when code coverage fails, ensuring accurate validation feedback. (Support Case: 154962) Caching Issue in EZ-Commit AutoDraft Flow In version 25.4.4, a cache-related issue caused errors when expanding metadata components in the AutoDraft step of the EZ-Commit flow. Users encountered the message “Cannot invoke 'java.lang.Comparable.compareTo(Object)' because 'k1' is null.”This issue has been resolved in the current release. Metadata components now expand and display their contents correctly without any errors.
Release Date: 26 October 2025 Highlights: Improvements in EZ-Commit author handling, EZ-Merge responsiveness, and CI Job error reporting.
EZ-Commit Author-Specific Retrieval Resolved an issue where EZ-Commit was not correctly filtering metadata changes by the selected Salesforce Org Author. The process now accurately fetches only Author-related changes when a specific Author is chosen in both “Select Manually” and “Re-Use Previously Validated Commit Labels” modes. (Support Case: 151097)
EZ-Merge Screen Freeze After Target Branch Selection
Fixed a delay where the EZ-Merge screen froze for 14–17 seconds after selecting the target branch (“To” branch). The merge approver validation API (/mergerevieweremail) has been optimized with asynchronous handling to improve responsiveness during branch selection.
(Support Case: 155279)
CI Job Failure with No Error Displayed Addressed an issue where CI Jobs failed silently when component names contained dots and were misclassified under different component types (e.g., Profiles) in DX environments. The fix ensures accurate component handling and consistent error reporting for both DX and Non-DX CI Jobs initiated from Version Control to Deploy Org. (Support Case: 155649)
Release Date: 19 October 2025 Highlights: Enhancements to metadata handling for destructive commits, standard value set retrieval, CI Job status accuracy, and Quick Deploy validation behavior.
UserAccessPolicy Deletion in Destructive Commits Destructive commits containing the 'useraccesspolicy' metadata type failed during execution. The metadata type has now been added to the SfdxMetadataFolder to ensure it is recognized for deletion. (Support Case: 153113)
ContactPointUsageType Standard Value Set Retrieval ARM was unable to retrieve the "ContactPointUsageType" standard value set, which is associated with the "Contact Point Email" object. Since standard value sets cannot be fetched using describe calls, the metadata was added to the internal static list to ensure successful retrieval. (Support Case: 154150)
Quick Deploy Criteria Validation for PR-Triggered CI Jobs Quick Deploy was unavailable after a successful Pull Request–triggered validation due to incorrect variable binding of the "preventDeploy" setting. The logic has been corrected, ensuring Quick Deploy remains unavailable when "Prevent Deployment" is selected under "Validate Deployment," matching expected behavior. (Support Case: 153792)
Release Date: 15 October 2025 Highlights: Stability improvements across CI Jobs, Commit handling, and Scratch Org creation.
CI Job Email Notifications – Missing Error Details Fixed an issue where CI job email reports did not display deployment failure details for Apex Classes. The notification logic now correctly includes all error and failed test details in the email report. (Support Case: 154005)
Backup CI Jobs – Git Push Pre-Receive Hook Error Addressed a problem causing Backup CI Jobs to fail with the error “GIT Push remote update Result: pre-receive hook declined.” The exception is now taken care and the UI displays a simplified message: “No modifications exist.” (Support Case: 154837)
EZ-Commit Validation – File Copy Failure Resolved a FileNotFoundException that occurred during EZ-Commit validation when a metadata file was missing from the source folder. The updated logic now skips missing files and continues copying remaining files, allowing the commit process to complete successfully. (Support Case: 154753)
Release Date: 5 October 2025 Highlights: Fixes for Quick Deploy iteration visibility, CI post-deploy log accuracy with DataLoader Pro, and complete Jira sprint retrieval across ALM flows.
Quick Deploy iteration visibility A validated deployment could be quick-deployed from a later iteration while the Quick Deploy button remained visible and usable on earlier iterations, which diverged from Salesforce behavior; this affected deployment iteration handling in the Deployments UI. Quick Deploy is now correctly disabled for the current iteration and all previous iterations once an actual deployment is performed, matching Salesforce semantics and preventing accidental re-deploys of validated iterations. (Support Case: 150463)
CI job post-deploy logs and DataLoader Pro status accuracy CI jobs that triggered a post-deploy DataLoader Pro process sometimes showed a null error or incorrect "not yet run" status in post-activity logs even though the DataLoader Pro job executed and made changes in the org. We handled the null pointer and corrected status mapping between the DL module and CI logs; CI jobs now complete without the null error and post-activity logs reflect accurate in-progress and final statuses. The system also ensures the DataLoader Pro job is triggered and its final status is shown correctly. (Support Case: 153953)
Release Date: 28 September 2025
Wavedashboard deployment failure due to xmd conversion When customers uploaded a package.xml containing wavedashboard type and members, ARM converted them to wavexmd and the deployment failed because the wavexmd files were missing from the zip. Implemented backend logic to prune xmd metadata entries when corresponding xmd files are not retrieved from the source org, preventing missing-file deployment errors. (Support Case: 151073)
Email approvals bypassing branch access Users who had branch access removed could still approve merge requests via the merge validation email notification. Added an enforcement check for email-based approvals that validates destination branch permissions against the merge approval role; users without permission on the destination branch will no longer be shown as eligible approvers or be able to approve via email. (Support Case: 153126)
Jira Work Items Not Retrieved from Sprints Fixed an issue where customers were unable to select Jira work items during ALM flows in EZ-Commit and Merge, with the error “No work items found in this sprint.” Jira had deprecated the API (v2) used by ARM to fetch work items, causing sprint data retrieval failures. ARM now uses Jira API v3 for work item retrieval, restoring functionality across EZ-Commit, EZ-Merge, Merge Requests, and CI Jobs.
Release Date: 24 September 2025
Jira Work Items Not Retrieved from Sprints Fixed an issue where customers were unable to select Jira work items during ALM flows in EZ-Commit and Merge, with the error “No work items found in this sprint.”
Jira had deprecated the API (v2) used by ARM to fetch work items, causing sprint data retrieval failures.
ARM now uses Jira API v3 for work item retrieval, restoring functionality across EZ-Commit, EZ-Merge, Merge Requests, and CI Jobs. (Support Case: #150934 & #151385)
Release Date: 21 September 2025
Highlights: Fixes for EZ-Commit folder retrieval, branch registration, SCA validation, and webhook API token updates.
EZ-Commit – Report and Dashboard Folder Retrieval Fixed an issue where report and dashboard folders were not being retrieved when using a package.xml. Now, folders and their members are correctly retrieved during EZ-Commit, covering scenarios for both DX and non-DX repos, with and without Autodraft. (Support Case: 150181)
Branch Registration – Default Branch Change Resolved an issue where the main default branch was unintentionally updated when registering a new branch for the first time. The default branch is now updated only if the current default branch does not exist in the remote repository. (Support Case: 149845)
SCA Validation with Special Characters Fixed an error where SCA analysis failed when branch names or paths contained "/" or special characters. The fix covers EZ-Commit, EZ-Merge (including Pre-validation and Release Label merges), CI Jobs (Package from Version Control), Deployment (Version Control & Release Label), and Report Module.
Release Date: 20 September 2025
SCA Validation with Special Characters Fixed an error where SCA analysis failed when branch names or paths contained "/" or special characters. The fix covers EZ-Commit, EZ-Merge (including Pre-validation and Release Label merges), CI Jobs (Package from Version Control), Deployment (Version Control & Release Label), and Report Module. (Support Case: 152825)
Release Date: 14 September 2025
Highlights: Stability improvements across Custom Deployment, Release Labels, EZ-Commit, CI Jobs, and Salesforce ALM integration.
Custom Deployment – Full Profile Deployment Failure: Fixed an issue where Full Profile Deployment using Version Control failed with a size limit error because the .git folder was unintentionally included in the build preparation. Now, hidden folders (starting with ".") are excluded from the build process.
Custom Deployment – Deployment Fails with Ignore Installed Components: Resolved an issue where deployments failed silently on the UI when the Ignore Installed Components option was selected. The deployment now completes as expected.
Deployment Logs – UI Visibility Issue: Customers reported deployment logs not consistently showing in the UI. While the root cause is still under review, additional logging has been added to capture scenarios when logs fail to display.
Release Date: 7 September 2025
Revision Retrieval Error During Deployment: Fixed an error where retrieving revisions with a single revision or while creating a release label caused runtime exceptions from Git. Updated logic now ensures stable fetch during revision retrieval.
Intermittent Workspace Not Found Error in EZ-Merge: Resolved an issue where merges intermittently failed with “Workspace not found with id….” Logic was updated to handle the scenario reliably.
Sub-User Branch Visibility in Admin VC Repos: Addressed a problem where sub-users couldn’t see newly created branches unless permissions were manually updated. Sub-user visibility is now automatically enabled when a new branch is created.
Webhook Security Update As part of our ongoing security improvements, webhook security has been strengthened in this release.
Support for old webhook URLs was retired earlier in ARM v23.1.15.
With this release, it is now mandatory to use an API token with all webhook endpoints.
This change ensures stronger protection and prevents unauthorized access to your integrations.
Release Date: 31 August 2025
Highlights: Fixes and improvements across permission sets, profile comparison, reports accuracy, and SSO configuration.
Permission Set – Deleted Tags Displayed: Resolved an issue where deleted tags appeared under Permission Sets when committing with ServicePresenceStatus. Support for ServicePresenceStatusAccess has been added to Permission Sets, and necessary code changes were made to ensure correct behavior.
Profile Compare – Custom Permissions Not Visible: Fixed an issue where the Profile Compare feature in the Deployment module did not show custom permissions for orgs. Updated UI logic ensures that deltas for custom permissions now display correctly.
Reports – Discrepancy in Deployment Counts: Addressed a mismatch where reports displayed an incorrect deployment count when using custom range filters. Deployment counts are now consistent with actual values.
Release Date: 24 August 2025
Highlights: Fixes to EZ-Commit translations, webhook API token status, and rollback iterations.
EZ Commit – Case Values Removed from CustomObjectTranslation: Resolved an issue where case values were being removed from the CustomObjectTranslation file when performing multiple EZ-Commits under Japanese language. The problem was caused by unmarshalling and marshalling logic comparing values incorrectly. The comparison logic has been updated to rely on additional fields to properly support translations for different languages.
Webhooks – API Token Last Access Not Updating: Fixed an issue where webhook API tokens continued to display “Never Accessed” even after recent runs triggered by CI jobs. The back-end logic has been corrected to update and display the last access time accurately.
Rollback – Iteration and Components Not Available After Revert: Addressed an issue where rolling back a previously deployed iteration caused both the iteration and its components to disappear. A change event has been added to ensure iterations and components are available after a revert rollback.
Release Date: 17 August 2025
Highlights: Stability improvements and fixes for CI Jobs and Admin functionalities.
CI Jobs – Baseline Revision Update Issue: Resolved an issue where CI jobs were stuck and queued after a specific build. The problem was traced to a scenario where the baseline revision was not updating. The back end has been updated to address this case and additional logging has been added for better diagnostics.
Admin – Adding Released Users to Teams: Fixed an issue where adding a delegated or released user to a team displayed a success message but did not actually add the user. The root cause was an error in fetching released user details. Logic has been corrected to ensure the released user is properly added to the team.
CI Jobs – Rollback Failure for Selective Components: Addressed a rollback failure during CI job deployments when rolling back selective components, resulting in a “Not in Package.xml” error. Back-end logic has been updated to handle the workflow metadata type correctly.
Release date: 10 August 2025
Branching baseline now supports committing child metadata components for Sharing Rules, Workflow, and Managed Topics: This enhancement ensures these metadata types are correctly captured and pushed to the remote repository, addressing gaps identified in earlier releases.
Release Date: 3 August 2025 Highlights: Reliability and accuracy improvements across CI jobs, release labels, and EZ-Commit workflows.
CI job cleanup for Provar executions: Unused test-result folders in Provar job paths were not deleted after runs, slowly consuming disk space. A cleanup mechanism now removes temporary directories and report data immediately after each job completes.
Destructive change detection in remote branches: CI jobs missed destructive updates performed directly in GitHub, causing build failures. Backend logic has been corrected so that remote destructive changes are reliably detected and processed.
Release label revision count displayed inaccurately: When modifying an existing release label, the UI showed an incorrect number of selected revisions. Increment logic has been fixed so the description now reflects the true revision count.
Release Date: 27 July 2025
New ALM Support: ARM now links to the SaaS Tool Kit so EZ-Commit can update Salesforce ALM records automatically. After a simple one-time setup, developers select the User Story or Defect during an EZ-Commit, add notes or effort, and ARM pushes the commit details to Salesforce while advancing the record’s status from Unit Complete → Ready For SIT and SIT Complete → Ready For UAT—no manual edits needed.
Bug Fixes
QuickAction metadata deployments fail due to package.xml exclusion: Fixed the package-preparation logic so QuickAction files are included, allowing validation and deployment to succeed.
Environment-provisioning flow errors not displayed: Corrected run-time array handling so success and failure details are now shown when enabling flows via an environment-provisioning template.
Release Date: 20 July 2025 Highlights: UI fixes in conflict resolution, improved destructive change handling in DX/Non-DX, and artifact preparation reliability enhancements.
Merge Conflict Resolution – UI Handling: Improved the reliability of conflict resolution in the Merge Conflict screen. Resolved a UI issue where repeated lines were unintentionally removed after resolving conflicts using "Block from Source/Destination", leading to incorrect merges.
Destructive Changes in Commit (Non-DX): Enhanced support for Report, Dashboard, Document, and EmailTemplate components in the Deleted tab under EZ-Commit for Non-DX repositories. These were previously not triggering the proper validation and error messaging during component selection.
CI Job Deployment – Classic Manifest Support in DX: Fixed a bug where CI Jobs using DX repositories and Classic Package Manifest settings only packaged destructive changes, ignoring constructive ones. Validations and deployments now correctly handle all combinations of destructive and constructive changes.
Release Date: 13 July 2025
Highlights: Stability and accuracy improvements across EZ Commit, Branching Baseline, and CI Jobs.
EZ Commit – Deployment-validation reports older than 30 days were missing in EZ Commit. It's now available.
EZ Commit – Malformed XML errors when committing permission-set files are resolved by refining the copy logic.
Branching Baseline – UNKNOWN_EXCEPTION errors during batch processing eliminated by removing the parent Workflow entry and explicitly adding the child Workflow metadata types (WorkflowTask, WorkflowFieldUpdate, WorkflowAlert, WorkflowFlowAutomation, WorkflowKnowledgePublish, WorkflowOutboundMessage, WorkflowRule, WorkflowSend) to metadatatypes.json.
Release Date: 6 July 2025 Highlights: Key enhancements and fixes to CI jobs, VS Code integration, deployment modules, audit reports, and environment provisioning.
Audit Reports – Deployment Label & Metadata Fixes Added the Deployment Label column in the Audit Reports section. Fixed issues with Invalid Date in the created/modified date columns and removed special characters from downloaded CSV headers.
Env Provisioning – Apex Test Level Execution Support Improved the Enable/Disable Apex Trigger Migration Template by reintroducing the Test Level dropdown in the execution window. Now the execution status updates correctly based on test result outcomes.
CI Jobs – Sharing Rules Not Deployed Resolved an issue where Sharing Rules were skipped during deployment when linked to custom objects from installed packages.
Release Date: 29 June 2025
Highlights: Git Performance Optimization, Accurate CI Deployments, and Enhanced Reporting Visibility
Faster Git-Based Version Control Validations We’ve improved how ARM validates Git branches and revisions. These checks are now performed directly on the remote Git repository, eliminating the need for local workspace setup. This significantly boosts performance and reduces processing time during operations.
Installed Components Now Properly Excluded in CI Jobs The “Ignore Installed Components” option in CI jobs was previously not functioning as expected—installed components were still being deployed. This has been corrected. The selected option now effectively excludes these components from deployment.
Resolved Validation Error During Permission Set Commit Users encountered commit validation errors when working with permission sets and specific metadata selections. We've refined commit logic to ensure permission set files are filtered correctly based on selected options.
Permissionset Deployments No Longer Drop Object Permissions
Deploying a new permission set with “Ignore Missing Visibility” enabled previously removed DataStreamDefinition
Release date: 22 June 2025
This release delivers targeted improvements to Vlocity deployments, CI job processing, sandbox provisioning, permission settings, and EZ-Commit behavior. Key internal issues have been resolved to enhance reliability, reduce metadata deployment anomalies, and streamline configuration workflows.
1. Issue: After a commit, comma-separated Calculation Matrix Components were not being correctly committed to the branch. Only the YAML file was pushed, and that too in an incorrect format.
Fix: Introduced logic to backup the Calculation Matrix member name, fetch the correct member, and update the YAML file accordingly. Now, the Calculation Matrix Components are committed as expected, supporting direct commits, commit labels, and release labels.
Vlocity Version Control Deployments (including release, commit label, and AutoRABIT build) now retrieve and deploy comma-separated Calculation Matrix Components accurately.
Vlocity Org-to-Org Deployments are verified and working correctly.
CI Jobs now correctly retrieve and deploy comma-separated Calculation Matrix Components from source to target Salesforce org.
Module: Vlocity Commit, Deployments, and CI Jobs
2. Issue: Managed package components that were intended to be excluded were still being included during deployments.
Fix: Implemented proper filtering logic to ignore installed (managed) components during deployments and CI job executions, ensuring expected exclusion behavior.
Module: CI Jobs and Deployments
3. Issue: During a sandbox refresh, the template failed because the Sandbox Access field was missing for the production. Salesforce updates now require explicit configuration of access levels during the refresh process.
Fix: Introduced a new Sandbox Access field to the environment provisioning template. Users can now define the appropriate access level, enabling complete control during sandbox refresh.
Module: Environment Provisioning
4. Issue: During an EZ-Commit, the Diff view did not correctly reflect profile permission changes (field/object permissions), despite being configured under My Account > Salesforce Settings.
Fix: Applied backend logic to ensure that global profile and permission set rules apply only to the configured profiles/permissions. The Diff screen now accurately displays modifications relevant to the EZ-Commit context.
Module: EZ-Commit (Profile & Permission Set)
5. Issue: In the "Apply Global Profile / PermissionSets Settings" screen under My Account, unnecessary permission selections were displayed. This contradicted the help text stating that all field/object permissions would be universally set to true (grant) or false (revoke), making the checkbox list appear redundant.
Fix: Now, only explicitly granted or revoked object/field permissions are selected or deselected in the UI, making the configuration clearer and more accurate.
Module: Admin → My Account → Profile / Permission Set Configuration
6. Issue: An internal CI Job history API call was failing. Customers were unable to retrieve data via Postman due to an invalid filter applied to the DB query.
Fix: Corrected the filter logic in the DB query that powers the API. The API is now functioning as expected and can return CI job history details without failure.
Module: CI Job History API (Postman & DB Filter)
Release Date: 15 June 2025
This release introduces support for Salesforce API 64 (Summer ‘24) and adds compatibility for new metadata types. Key improvements include bug fixes for CI Job execution, Profile Compare deployments, permission retrieval, and DX-based destructive changes in EZ-Merge.
Module: Metadata Compatibility
Added support for the following new metadata types:
LightningTypeBundle (supported for Non-DX only)
ExtlClntAppMobileSettings
Issue: Newly created CI Jobs were not getting triggered upon pull request creation in a specific branch. CI jobs for other branches in the same repository were functioning correctly.
Fix: The logic was updated to properly retrieve the base branch name when fetching credentials from the database. This now ensures the correct CI job is triggered for all branches.
Module: CI Jobs
Issue: When updating object permissions using the Profile Compare feature, the changes appeared to reflect correctly in the UI but were not applied during deployment. The mismatch was due to inconsistent node names in the backend.
Fix: Standardized object permission node names across the UI and backend to align with Salesforce's profile XML structure, ensuring accurate deployment of user selections.
Module: Profile Compare
Issue: Profiles with special characters in their names were not being retrieved properly. This was due to URL decoding and formatting that altered the original profile name, preventing matching and retrieval.
Fix: Removed unnecessary decoding and now presents the profile name in the exact format received from Salesforce, ensuring such profiles are correctly processed.
Module: Admin → Salesforce Settings → Profiles and Permissions
Issue: Destructive changes related to static resources were not working properly for DX-format deployments in EZ-Merge.
Fix: Destructive change logic for static resource metadata was implemented for DX format, making it consistent with non-DX behavior and ensuring successful validation and deployment.
Module: EZ-Merge
Release Date: 8 June 2025
This release brings critical improvements and feature enhancements across multiple modules, including Environment Provisioning, CI Jobs, Admin, EZ-Merge, and Metadata handling. The updates aim to improve system flexibility, performance, and metadata deployment consistency.
Issue: In Environment Provisioning, the Remote Site Settings template was failing to update the URL in the destination org when the user applied alphabetical sorting. This caused deployment inconsistencies.
Fix: Now, the template can update remote site settings correctly regardless of alphabetical sorting. Sorting by Remote Site Name or Remote Site URL no longer blocks the update process. Validation has been completed in the integration branch.
Module: Environment Provisioning
Fix: Users can now update their SSO domain name via the SSO Configuration page. Once the domain name is changed, an automated email informing all users of the update is triggered.
Module: Admin → My Account → SSO Configuration
Issue: While attempting to delete static resources and their .meta files through EZ-Merge, no destructive changes package was being generated, even when the "Run Destructive Changes" checkbox was selected. This caused validation failure during merge.
Fix: Destructive logic has been implemented in EZ-Merge for both DX and non-DX formats, ensuring static resource deletions are correctly handled and packaged.
Module: EZ-Merge
Issue: CI Job deployments were failing with a 504 Gateway Timeout error, blocking staging environment activities and causing delays in deployment pipelines.
Fix: Optimized the CI Job execution logic by improving how API timeouts are handled. This ensures better performance and avoids timeout-related failures during large or slow deployments.
Module: CI Jobs
Issue: While running test classes in the Admin section, unrelated Apex test classes were being auto-populated.
Fix: The auto-population logic was revised to ensure only relevant Apex classes are retrieved and saved. Unrelated classes are now excluded from test jobs.
Module: Admin → My SF Org Management
Issue: During CI Job deployments involving Search and Substitute rules, changes were not being applied to the destination org, even though the deployment was marked successful.
Fix: Provided Fix and also Extended support to apply substitution logic to the following metadata types: AutoResponseRule, CustomLabel, CustomMetadata, CustomObject, CustomSite, Dashboard, DashboardFolderShare, Network, NamedCredential, PermissionSet, Portal, Queue, RemoteSiteSetting, Report, ReportFolderShare, SamlSsoConfig, SharingCriteriaRule, SharingOwnerRule, and Workflow.
Module: Search and Substitute
Issue: When performing a destructive change (e.g., deleting a ProfileSearchLayout) and deploying via Single Revision, the system failed to identify the change correctly, expecting the metadata to be present instead.
Fix: The Retrieve Metadata screen now correctly classifies added/modified ProfileSearchLayout changes under "ALL ITEMS" and does not falsely tag them as missing. For Non-DX Deployments and CI Jobs, ProfileSearchLayout changes now appear as constructive updates and deploy successfully.
Behavior Limitation: If a Custom Object contains only a single ProfileSearchLayout node and that node is deleted, the change will not be picked up during deployment, as ProfileSearchLayout is not a standalone metadata type.
Module: Deployment / CI Jobs
Release date: 1 June 2025
This release improves metadata handling and deployment type consistency and enhances support for Vlocity and Permission Set delta deployments. Several critical fixes have been addressed across the Deployment, CI Jobs, and EZ-Commit modules to improve reliability and reduce deployment anomalies.
Issue: When deploying a new profile search layout for the Case object, the deployment unintentionally removed all other existing profile search layouts in the org, causing a loss of metadata settings for other profiles.
Fix: The logic in the deployment backend (CustomObjectController.java) has been refactored. It now compares layout differences in an additive manner, ensuring that new layouts are added without deleting existing ones.
Impacted Module: Deployment
Issue: The “Enable Delta on Permission Sets” checkbox is designed to ensure only changed permissions are committed or deployed. While it did not work correctly for CI Jobs, object permissions were still getting removed even when the checkbox was enabled.
Fix: The delta behavior is now standardized across both CI Jobs and Deployments. A back-end code fix ensures that object permissions are preserved in deployments sourced from version control (SCM) and delta logic is honored properly.
Impacted Modules: CI Jobs, Deployment
Issue: During Vlocity SF Org-to-Org deployments, YAML files failed to handle Calculation Matrix fields with comma-separated values that included spaces. This broke deployments and made the downloaded DataPacks unusable.
Fix: The YAML generation process was enhanced to support such field values. Now, comma-separated Calculation Matrix components are parsed and deployed correctly to the target org. YAML downloads are also displayed properly.
Note: This fix currently applies only to Org-to-Org Vlocity deployments. Support for Vlocity deployments via Version Control is under R&D.
Issue: While configuring ScheduleApexClassesMonthly templates in the Environment Provisioning module, all default user fields were incorrectly set to Analytics Cloud Integration User, regardless of what the template intended.
Fix: The back-end logic for template value assignment was fixed. It now correctly pulls in the actual default values specified in the template configuration.
Impacted Module: Environment Provisioning
Issue: A customer was performing a merge using a commit that contained only destructive changes. Even though the "Destructive Changes" checkbox was enabled, the merge failed during the Validate Deploy stage.
Fix: Salesforce expects both a postdestructivechanges.xml and an empty package.xml file for validation to pass. The fix ensures that an empty package.xml file is now automatically added to the package folder, along with destructive changes, making the validation step successful.
Issue: While using a previously validated commit label to perform a new EZ-Commit, customers were unable to see the RecordType component under the “All Metadata Components” tab.
Fix: The component filtering logic was corrected to ensure that RecordType and similar metadata types are displayed when using commit templates, improving usability and completeness of the commit UI.
Impacted Module: EZ-Commit
Release Date: 25 May 2025
This release focuses on stability, reliability, and enhanced usability across core modules like CI Jobs, EZ-Commit, and Release Management. Key improvements address long-standing issues such as CI job queue blocks, premature status transitions during aborts, metadata filtering inconsistencies, and usability fixes in user management.
We’ve also added support for Provar v25.2.1, improved error handling and logging, and ensured a smoother experience for EZ-Commit users leveraging custom metadata and commit labels.
Issue: When a user aborts a release label, the system prematurely sets the release status to "Failed" while the abort request to the agent is still pending. If the abort request isn’t successfully sent, the status gets stuck, causing confusion in monitoring and troubleshooting.
Fix: The system now updates the release status to “Failed” only after the agent successfully triggers and acknowledges the abort request. Extra logging has been added to help trace abort scenarios and ensure proper state transitions.
Impacted Module: Release label Management
Issue: When performing an EZ-Commit using the SCA > CodeScan option and enabling “Only newly added supported metadata types,” the commit wasn’t functioning properly if the user reused a previously used commit label.
Fix: Metadata filtering logic has been updated to support commit label reuse, ensuring seamless functionality with Auto Draft.
Impacted Module: EZ-Commit
Issue: Some CI jobs were getting stuck in the queue due to:
Unhandled exceptions
Git commit failures where no revision was generated
Fixes:
Prevented downstream processes when Git fails to generate a revision
Improved handling for null messages and unexpected errors
Added enhanced logging to support better troubleshooting
Impacted Module: CI Jobs
Issue: Fields like Phone Number, Zip Code, and State were mandatory during user creation, restricting onboarding in certain cases.
Fix: These fields are now optional in the Admin module, streamlining user creation.
Impacted Module: Admin (User Management)
Issue: When committing CustomField and CustomObjectTranslations, valid Fieldset translation nodes were unintentionally removed.
Fix: Translation node handling has been refined to preserve valid entries and prevent data loss in multilingual configurations.
Impacted Module: EZ-Commit
Issue: CI Jobs were failing inconsistently when using existing credentials, with causes difficult to trace.
Fix: Improved logging at credential validation points to isolate issues and aid future debugging.
Impacted Module: CI Jobs
Request: Compatibility needed for Provar version 25.2.1 to support automated test execution.
Update: Provar v25.2.1 is now supported and available on demand for integration with ARM workflows.
Issue: Sub-users could not view their own release labels due to a mismatch in branch name casing logic.
Fix: The filtering logic now respects case sensitivity, ensuring correct visibility of release labels.
Impacted Module: Release Label Management
Release Date: 18 May 2025 Overview
This release includes key bug fixes and improvements focused on enhancing CI Job stability, deployment reliability, and metadata diff accuracy. It addresses critical issues encountered in Salesforce-to-Salesforce deployments, destructive change logic, permission set handling, and package creation workflows. Additionally, customer-requested upgrades such as Provar support enhancements have been implemented.
Issue: The “Prepare Destructive Changes” option was not selected during initial CI Job creation but was unexpectedly selected during re-runs.
Impacted Modules:
Deploy a package from Salesforce to Salesforce
Deploy a package from Salesforce to Salesforce and back up to Version Control
Fix: Resolved inconsistencies in destructive change logic. The system now retains the correct state of the “Prepare Destructive Changes” flag across CI Job executions.
Issue: When attempting to commit FLS changes for a new field within a permission set, the changes were not captured in the diff report, resulting in missing commits.
Fix:
Enhanced logic to correctly capture FLS changes by appending Task and Event objects for the Activity object when the Global Permissions option is selected in EZ-Commit.
Issue: When performing a Single Revision Deployment, even after aborting it (a confirmation popup showing a successful cancellation), the deployment continued and was marked as successful.
Fix: Fixed the abort logic within the deployment module to correctly halt execution and reflect the accurate status post-abortion.
Issue: Customer experienced failures when triggering a CI Job to create and install an unlocked managed package from a version control branch.
Fix: Improved JSON handling during CI Job execution, ensuring compatibility with both internal and customer-specific JSON structures. Now, even in case of exceptions during package creation, the system attempts fallback version creation instead of complete failure, similar to the existing SFDX module behavior.
Request: Customer requested support for Provar v25.2.1
Update: Support for Provar version 25.2.1 has been added to ensure compatibility with automated test execution workflows. This version will be available on a demand basis.
Release Date: 11 May 2025
This release introduces feature enhancements and key bug fixes to improve deployment flexibility, metadata handling, CI job stability, and user experience. The update includes enhanced error handling for CI and Apex jobs, metadata recognition updates, and refined UI behavior in merge and licensing workflows.
CI Job Includes Unsupported Metadata Despite Exclusion Configuration
A customer reported that certain metadata types (CallCenterRoutingMap, CallCtrAgentFavTrfrDest) were deployed despite being explicitly excluded in the deployment configuration.
Upon investigation, the data related to CallCenterRoutingMap was retrieved and verified successfully. However, data for CallCtrAgentFavTrfrDest could not be validated.
These metadata types are associated with Salesforce Service Voice features, which require full integration with a compatible telephone system. Currently, such an integration is unavailable in our environment, limiting our ability to validate the issue fully.
Fix: Few metadata types are officially supported and recognized correctly in deployments.
Impacted Module: CI Jobs
Repository URL Migration A customer-requested repository URL migration has been completed.
Fix: Migration was successful, and no further issues were reported.
Impacted Module: Repo Management
Profile Comparison Error: “Salesforce Org Doesn’t Exist” An error occurred when comparing profiles across 2 or 3 environments.
Fix: UI logic for diff loading has been refined to handle multi-org comparisons.
Impacted Module: Metadata Comparison
CI Job Fails When All Standard Value Sets Are Excluded CI Jobs failed to run if standard value sets were excluded from selection.
Fix: Job logic updated to handle scenarios where standard value sets are excluded.
Impacted Module: CI Jobs
Failure in Scheduled Apex Test Runs for Production Orgs Daily scheduled Apex test executions failed due to an issue handling multiple concurrent jobs.
Fix: Logic in ApexTestClassesSchedulerJob refined to support multiple scheduled jobs.
Impacted Module: Apex Test Scheduling
Text Change in Merge Screen UI The label was changed from “Skip all three prevalidation criteria” to “Skip all prevalidation criteria” for better clarity.
Impacted Module: Merge UI
License Upload Not Visible for Expired On-Premise Servers When the license expired, the option to upload a new key was not visible before login.
Fix: The pop-up visibility issue was resolved; users can now upload the license before logging in.
Impacted Module: Licensing (On-Prem)
Issue Type: UI Bug
Release Date: 4 May 2025
This release of AutoRABIT ARM introduces key bug fixes and stability improvements to deployment label handling, CI job webhook executions, and user management across regions. Notably, a critical internal issue affecting metadata filtering during full deployments has been addressed. Additionally, issues related to saving users for countries without state-level details and CI job webhook failures have been resolved.
Issue with Full Deployment - Previous Deployment Label Type
A defect was identified when performing a full deployment using the “Previous Deployment Label” type, which inadvertently included all metadata members from the source organization, rather than only those associated with the selected label.
Fix: Updated deployment logic now ensures that only metadata within the selected label is included in the deployment. Impacted Modules: Deployments
Webhook Execution Failures in CI Jobs
Webhooks were not being executed during CI job runs due to limitations in DynamoDB.
Fix: Webhook invocation logic has been revamped to ensure reliable webhook execution in CI pipelines. Impacted Modules: CI Jobs
User Creation Failure – Countries Without States
An issue was reported where creating or editing users with countries that do not have states (e.g., Singapore, American Samoa, Andorra) failed to save the user details.
Fix: Validation logic has been updated to treat the state field as optional for applicable countries, ensuring successful user creation. Impacted Modules: User Management
Release Date: 27 April 2025
This release introduces significant enhancements to AutoRABIT’s ARM platform, focusing on enhanced metadata support, improved deployment accuracy, and optimized performance across CI workflows. Previously unsupported metadata types are now fully recognized in DX-based branching and deployment. Issues with redundant code coverage reports and performance bottlenecks in ALM item loading have been resolved. Significant improvements also include full profile permission coverage in EZ-Commit and enhanced metadata exclusion logic.
Support for New Metadata Types in DX Repo CI Deployments
Previously unsupported metadata types are now included in deployments created through DX repo-based branching. These include: ApplicationSubtypeDefinition, BusinessProcessTypeDefinition, ConvIntelligenceSignalRule, ExplainabilityActionDefinition, ExpressionSetDefinitionVersion, ForecastingGroup, and PathAssistant.
Impacted Modules: CI Jobs (DX Branching & Deployments)
Code Coverage Report Duplication Fixed Resolved an issue where multiple code coverage reports were generated for the same sandbox. The back-end logic has been updated to ensure that only one report is created per sandbox. Impacted Modules: Code Coverage Reports
Improved ALM Item Load Time in Commit/Merge Modules Addressed severe performance lag when loading Azure ALM items after sprint selection. Switched to batch API calls for fetching work item data and states, reducing calls from thousands to single digits. Load time dropped from ~6 minutes to ~4 seconds for large sprints. Impacted Modules: Commit/Merge (ALM Integration with Azure)
Full Profile Commit – Object Permissions & Tab Visibility Fixes Fixed missing object permissions (Documents, Push Topics) and tab visibilities (Reports, Dashboards) in full profile commits during EZ-Commit. The package.xml generation logic now correctly includes all necessary metadata members. Impacted Modules: EZ-Commit, Profiles
Metadata Exclusion Logic Improved – ExpressionSetDefinitionVersion
Corrected behavior in which ExpressionSetDefinitionVersion metadata was included in deployments, even when excluded. This enhancement enables precise control over metadata exclusions, particularly for workflows that require separate deployment flows (e.g., OmniStudio jobs).
Impacted Modules: CI Jobs, Deployment
Release Date: 27 April 2025
Refer to the latest release notes published for nCino + Data Loader at .
Release Date: 20 April 2025
This release brings meaningful enhancements that improve reliability, accuracy, and visibility across ARM workflows. Backup CI jobs now consistently capture StandardValueSet changes, ensuring more complete metadata tracking. Improved metadata classification prevents deployment errors, while CustomObjectTranslation handling in EZ-Commit for DX repos is now more precise. Custom settings deploy smoothly through Environment Provisioning, reducing manual effort. File comparisons are clearer with restored full diff visibility, aiding better change reviews. Updates to Search and Substitute and managed package exclusions streamline CI deployments. Audit trails now display correct timestamps, enhancing reporting accuracy.
StandardValueSet Metadata in Backup Jobs Backup CI jobs now correctly detect and retrieve changes made to StandardValueSet metadata. Previously, these changes were not captured automatically, although manual commits through EZ-Commit functioned as expected. This enhancement ensures StandardValueSet changes are included in automated daily backups. Impacted Modules: CI Jobs backup to VC. Support Case: #132829
Metadata Type Detection for Custom Metadata Labels Improved handling of custom metadata with labels starting with "profile" or "permissionset" by validating based on their file paths instead of label names. The system now checks for profiles/ and permissionset/ in metadata paths to accurately categorize them during commit, merge CI jobs, and deployments. This resolves previous misclassification issues. Impacted Modules: All Modules.
CustomObjectTranslation Handling in DX Repositories Improved the EZ-Commit process to correctly handle CustomObjectTranslation metadata in DX repositories. Previously, some nodes were unintentionally removed, and unrelated changes like validation rules appeared in the compare changes section. The commit process now includes only selected components, matching the behavior of non-DX repositories. Impacted Modules: EZ-Commit while selecting 'customobjecttranslation' [DX/NonDX].
Custom Settings Deployment in Environment Provisioning Resolved an issue where custom settings were not being deployed through the Environment Provisioning module. Although no errors were shown on the history page, specified changes were not applied. This enhancement ensures that custom settings are now correctly deployed as part of the provisioning process. Impacted Modules: Env Pro -> migrate custom settings.
File Difference Display in Comparison Dialog Fixed an issue where the comparison dialog box did not consistently display full file differences for all metadata types. Previously, the UI showed only a limited number of lines without offering a "Load More" option, while the downloaded file revealed additional differences. The "Load More" functionality has been restored, now loading up to 200 lines per click to ensure complete visibility of metadata changes. Impacted Modules: Compare Metadata in Deployment Module.
Search and Substitute for Workflow Alerts in CI Jobs Resolved an issue where applying Search and Substitute rules on Workflow Alerts in SFDX repositories caused CI jobs to fail. The error was due to a logic fault, which has now been corrected. Common code has been refactored and moved to the pipeline to ensure consistent execution across jobs. Impacted Modules: CI Jobs, Deployment, and Pre-Validation Commit.
Exclusion of Managed Components in SFDX CI Job Deployments Fixed an issue where managed components were not properly excluded during SFDX CI job deployments, despite selecting "Ignore installed packages" and configuring exclusions under the Skip Members section. The deployment logic has been corrected to ensure managed components are now accurately excluded as intended. Impacted Modules: Deployments & CI Jobs.
Date and Time Accuracy in Audit Trails Corrected the logic used for date and time conversion in the UI of the Reports Audit Trail. Previously, the created and modified dates were displayed inaccurately. This enhancement ensures that audit timestamps now reflect the correct values. Impacted Modules: Audit Report.
Release Date: 17 April 2025
This release focuses on streamlining the deployment process and improving reliability across the platform. OmniStudio deployments now handle dependencies more intelligently with Max Depth -1, ensuring a smoother experience from retrieval to deployment. Conflict resolution has been made more precise, avoiding issues like content bleed between files, and users can now seamlessly retry failed merges without losing progress. Improvements to Org Sync and Admin settings make it easier to spot differences and manage roles in real time, while enhancements to file comparison and commit labeling bring greater clarity and control to the deployment workflow.
Max Depth -1 Support for OmniStudio Deployment Deployments using Max Depth -1 now correctly retrieve and include all dependent components such as IntegrationProcedure, DataRaptor, Document, and VlocityUiTemplate. The retrieved dependencies are now properly reflected in the UI and included in the deployment to the target org. Impacted Modules: Deployment (org → org).
Improved Conflict Resolution Accuracy Resolved an issue where content from previously resolved files was being incorrectly appended to other files during conflict resolution. This fix ensures each conflicted file is processed independently, preventing errors such as duplicate labels during deployment. Impacted Modules: EZ-Merge → Conflicts.
Retry Commit for EZ-Merge After Failure The "Retry Commit" option is now available when a merge fails due to incorrect or unmapped credentials. The system correctly updates the merge status to "CommitPending," enabling users to retry the commit. This fix applies to new merges created after this release.
Release Date: 06 April 2025 This release introduces significant new capabilities and key enhancements across the ARM platform. A major new feature enables multi-level deployment approvals by Org, offering structured release governance with customizable approval groups. Architecture improvements include enhanced global workspace management to handle deleted or missing branches more gracefully. The release also strengthens security with encrypted installation key handling. Core functionality has been optimized, including improved commit revision sorting and faster loading of standard value sets.
Multi-Level Deployment Approval by Org A two-level deployment approval process has been introduced to provide better control over releases. Each approval level supports group-based approval, allowing any member within the group to approve the deployment. Email notifications are sent to approvers with a link to ARM for approval actions. This approval process can be configured based on Org name. Admins can select applicable orgs and assign separate approvers or approver groups for each. Note: Approval Process support is now limited to Direct Custom Deployment only. It is not supported via Org Sync or Profile Management.
Secure Handling of Installation Key in Unlocked Packages CI Job The installation key used in the Unlocked Packages CI Job is now masked and encrypted for improved security. Additionally, a view/hide eye icon has been introduced to toggle the visibility of the installation key.
Clear Status Indicators for Merge Pre-validation Outcomes The "Merge Prevalidation Process" logs now provide clearer visual indicators based on the outcome of the validation. A green checkmark ( ✓) is shown only when the process completes successfully, while a red X clearly indicates when the pre-validation has failed or resulted in auto-rejection. This improvement ensures better visibility into validation outcomes for both merge and commit workflows.
3-Tier Architecture for ARM – Separate and Load the UI and Backend Services Individually The ARM UI can now be compiled and run independently from the backend. Based on configurable endpoints, the UI communicates with any designated backend server, defaulting to localhost. All UI components load locally, and API calls are routed according to the configured backend endpoint.
Resilience in Global Workspace Management for Optimized Workspaces A backend fix has been implemented to ensure stability in global workspace creation when the default branch is missing or deleted in the repository. When the default branch no longer exists in AutoRABIT or the remote repository, the system will now automatically update the global workspace and repository configuration to use the last valid branch. This prevents version control operations—such as commit, merge, or revision listing—from being blocked due to a broken global workspace.
A UI enhancement to allow users to change the default branch directly in the VC Repos module will be introduced in an upcoming release to fully resolve the issue.
Reliable CI Job Queue Handling Resolved an issue where CI jobs were stuck in the queue due to mismatched build numbers between CIJobInfo and CIJobHistory tables. The system now handles these cases correctly, ensuring jobs progress without blocking subsequent builds. Impacted Modules: CI Job abort and Queue flows, Release Label abort and Queue flows.
CustomNotificationType Support in Destructive Commits Destructive commits now support the CustomNotificationType metadata. Impacted Modules: Commits, Merges, Release Label Artifact execution, CI Jobs, Deployments while performing the Custom Notifications type destructive changes flow.
Package Key Handling in Deployment Module Resolved an issue where deployments failed due to a null package key during package version installation. The key preparation logic for dependent packages has been corrected, and a migration has been implemented to fix existing invalid keys.
Release Date: 6 April 2025
See the for nCino + Data Loader improvements.
Release Date: 09 March 2025
This release introduces Checkmarx One Integration, enabling users to perform security scans within ARM using Checkmarx One alongside existing Static Code Analysis tools.
Additionally, we have addressed multiple bug fixes and enhancements, including improved support for PLATFORMEVENTCHANNELMEMBER in destructive commits, enhanced merge conflict detection for layouts, and more reliable duplicate resolution for profiles. Security and stability improvements include fully hiding API tokens after creation, ensuring correct project mapping for CodeScan in CI jobs, and providing consistent permission set deployments in Commit Label deployments.
Checkmarx One Integration
Users can now integrate Checkmarx One as a Static Code Analysis tool within ARM. This allows security scans to be performed using Checkmarx One alongside other existing tools, providing a scalable and fully managed security solution for cloud-native and DevOps teams.
Improved Support for PLATFORMEVENTCHANNELMEMBER in Destructive Commits
ARM supports the destructive commit of PLATFORMEVENTCHANNELMEMBER metadata, ensuring seamless deletion and replacement of platform events without file diff errors. Impacted Modules: Destructive changes, VC, Deployments, CI Jobs.
Enhanced Merge Conflict Detection for Layouts
ARM reliably detects merge conflicts for layout metadata, including files with special characters in their names, ensuring a smoother and more accurate merge process. Impacted Module: EZ-Merge.
Release Date: 9 March 2025
See the for nCino + Data Loader improvements.
Release Date: 23 February 2025
The ARM Release 25.1.0 introduces key upgrades, new features, and critical fixes to enhance security, compatibility, and overall performance. This release includes updates to third-party libraries, improved error handling, and several bug fixes to ensure a seamless user experience.
Third-Party Library Updates: OpenJDK, Tomcat, Salesforce CLI, Sonar Scanner, and Local DynamoDB have been updated to their latest versions for improved performance, security, and compatibility.
Salesforce API Version 63.0 Support: ARM now fully supports Salesforce API version 63.0, ensuring compatibility with the latest Salesforce features and functionalities.
Picklist to ValueSet Migration: The Picklist feature in the VC Repo section is now deprecated, as Salesforce has discontinued support for it starting from API version 39.
Clearer Error Messages: Improved UI messages provide more precise and actionable feedback, making troubleshooting easier.
Tag Deployment Fix: Previously, deploying a tag would always result in the same changes, even when those changes were not present in the specified tag or branch. Tags now deploy the correct updates as expected. Impacted Modules: Custom Deployments.
Flow Access & LoginFlows Retrieval: Users can now retrieve and compare Flow Access and LoginFlows seamlessly. Previously, LoginFlows were not visible during change comparisons. Impacted Modules: EZ-Commit with validate deploy, Merge with validate deploy , Profile duplicates.
Third-Party Library Updates: OpenJDK, Tomcat, Salesforce CLI, Sonar Scanner, and Local DynamoDB have been updated to their latest versions for improved performance, security, and compatibility.
Linux Upgrade: The underlying Linux environment has been upgraded, strengthening security and optimizing system performance.
Release Date 23 February 2025
See the for nCino + Data Loader improvements.
Release Date: 19 January 2025
With this release, we have implemented the following enhancements and support fixes to improve features and functionality and streamline the user experience.
Email and Username Validation
Registration processes now enforce unique email addresses and usernames, ensuring each email is linked to only one active account. Added email verification confirms ownership, enhancing security and preventing duplication. Impacted Modules: Admin - User Registration, Subscription Management.
Enhanced XSS Protection
Implemented robust measures to prevent XSS risks, including validation of untrusted data, HTML sanitization, and Content Security Policy (CSP). These updates safeguard data and prevent script-based attacks. Impacted Modules: All Modules.
Improved Remote Site Settings Updates
URL updates now run seamlessly in the destination org. A new mechanism ensures tests proceed smoothly, even if individual cases fail. Impacted Modules: Environment Provisioning.
Consistent Merge Validation
The merge validation process now handles internal folder references accurately. Files in helper folders are fully validated, ensuring consistent results across merges and deployments. Impacted Modules: EZ-Merge with validate deployment.
SharingRules Metadata Visibility
SharingRules metadata is now visible and selectable for deployment and commit operations. Child metadata exclusions were adjusted to ensure proper visibility. Impacted Modules: All Modules.
Support for GenAiPromptTemplate
ARM now supports the GenAiPromptTemplate component, ensuring compatibility with Salesforce updates and enhancing functionality. Impacted Modules: VC, Deployment, CI Jobs.
Aligned Branching Baseline Behavior
Branching Baseline now matches EZ-commit behavior for Default manageable state metadata. Excluded Default metadata, such as Account.object-meta.xml, is no longer committed. Impacted Modules: Branching Baseline.
Faster CI Job Assignment
Agent assignment during CI jobs has been optimized, and a new feature flag allows streamlined verification using repository and username data, reducing delays. Impacted Modules: CI Jobs using Version Control.
Reliable Backup CI Jobs
Backup CI jobs now handle DX metadata exclusions and dashboard queries correctly, ensuring successful scheduled backups. Impacted Modules: CI Jobs, Deployments, EZ-Commits.
Merge Validation for Short Metadata Names
Merge validation now properly handles metadata names shorter than 9 characters. Improved logic ensures accurate validations without failures. Impacted Modules: EZ-Merge, EZ-Commit with validate deployment.
Commit Label Preservation
Commit labels are now retained even when associated pre-validation labels are removed, ensuring labels remain accessible and visible. Impacted Modules: EZ-Commit, Commit Label EZ-Merge, Commit Label Deployment.
Optimized Merge File Processing
The VALIDATINGSALESFORCEXML performs a single file check during branch-to-branch merges. Merged file data is stored uniquely, improving performance by preventing duplicate validations. Impacted Modules: EZ-Merge.
Release Date: 15 December 2024
With this release, we have implemented the following enhancements and support fixes to improve features and functionality and streamline the user experience.
We introduced a feature flag to support the gradual phase-out of TAF functionality in AutoRABIT. This flag allows controlled activation or deactivation of TAF at the customer account level, enabling a seamless transition without disrupting existing workflows. Automated testing and monitoring have been implemented to ensure functionality operates correctly and customer environments remain stable during the transition. Affected customers will be notified with detailed timelines, guidance, and alternative solutions to support their migration. Impacted Modules: TAF, CI Jobs, Reporting
We strengthened protection against the potential for a security vulnerability related to CSV injection, where malicious formulas embedded in CSV files could execute commands when opened in spreadsheet applications. User-generated data is now thoroughly sanitized, and special characters are omitted to prevent formula execution. This enhancement ensures that exported CSV files are safe to open, enhancing security against attempted cyberattacks. Impacted Modules: Org Sync History, Users, CI Job History, Reports, CI Job List
We eliminated the possibility for users to register using multiple email accounts for the same email ID, preventing potential confusion and security risks. The registration process now includes strict validation checks to ensure each email address is linked to only one active account. Email verification has also been implemented to confirm ownership and prevent unauthorized registrations, improving data privacy and system integrity.
We implemented an update to the deployMetadata SOAP service within the Deployment module, which now enables the process to run asynchronously in the background when initiating a Full Deployment. Previously, the service remained in a "pending" state until the deployment job completed. With this enhancement, the deployment process is more efficient, allowing the service to proceed without blocking user actions while the deployment completes in the background. Impacted Module: Deployments
AutoRABIT introduced a new API endpoint in the audit logs service to provide structured access to CEF audit logs. The API allows querying audit events based on a specified time range and maximum results, returning a detailed JSON response that includes event metadata, such as timestamps, event types, user actions, and outcomes. This enhancement replaces the previous plain-text log format with a structured system with query capabilities, enabling easier integration and analysis of audit data. Impacted Module: API Audit Log Event
We corrected an issue in which clicking "Here" in the Org Sync Report failed to redirect to the Unsupported Types Salesforce screen. The href attribute spelling has been corrected, ensuring users are properly redirected to the relevant page for unsupported metadata types. This fix improves navigation and user experience within the Org Sync Report. Impacted Module: Org Sync
We resolved an issue causing failures in commit and merge operations due to corrupted global workspaces. The global workspace handling mechanism has been enhanced to ensure stability, even when the OPTIMIZED_WORKSPACE feature flag is disabled. This fix eliminates runtime exceptions during clone operations, improving the reliability of EZ-Commit and EZ-Merge processes. Impacted Modules: EZ-Commit, EZ-Merge, Deployment & CI Jobs, Repo & Branch Registration.
Accurate Reporting for a CodeScan SCA with a Large Number of Violations
We corrected an error occurring in which a CodeScan code analysis with more than 500 violations displayed incorrect results in the UI and incomplete data in downloaded reports. The fix ensures that all scanned violations are accurately reflected in the UI and included in the downloaded Excel files, providing a complete and reliable report for large code scans. Impacted Modules: CodeScan SCA Execution Reports, CI Jobs, Deployments, Commits, and Merges.
We resolved a mismatch issue between Apex PMD and Salesforce Scanner results. Violations in bundle or static resource subfolders are now correctly grouped under their respective metadata types instead of being displayed as separate components. This fix ensures accurate and consistent results, improving the clarity of scanned violations across all file types, including .JS files. Impacted Modules: SCA Execution for both DX and Non-DX.
We fixed an issue in which the ToRevision parameter was missing in scheduled CI jobs. This issue caused jobs to fail by incorrectly using the baseline revision instead of the incremental revision. The fix ensures that ToRevision is consistently included, enabling accurate and reliable execution of CI jobs. Impacted Module: CI Jobs.
We resolved an issue in which AutoRABIT Build deployments failed to pick all metadata components when certain components were excluded. The deployment process now ensures that all remaining metadata is correctly included, even after exclusions. This fix addresses issues with missing data-table rows, ensuring complete and accurate metadata deployment. Impacted Module: Deployments.
Accurate Revision Handling in Incremental CI Jobs
We corrected an issue in which manually triggered incremental CI jobs were skipping the previous revision. The build process now ensures accurate handling of "From" and "To" revisions, preventing gaps in deployed commits. This enhancement guarantees that all relevant changes are included during incremental builds, maintaining consistency and reliability in deployment workflows. Impacted Module: CI Jobs.
We have resolved an issue causing CI job deployments to fail by including managed package components in destructive changes, despite the "Ignore Installed (Managed) Components" setting being enabled. Logic has been added to exclude installed components from destructive changes in both custom deployments and CI jobs. This enhancement ensures successful deployments without errors related to managed package components. Impacted Modules: CI Jobs, Deployments [DX, Non-DX, and Org-to-Org Deployments].
We corrected an issue during org-to-org deployments in which DigitalExperienceBundle components were not found in the zipped directory, resulting in deployment failure. The logic handling Digital Experience bundles has been corrected to account for scenarios where excluded components exceed 50. This enhancement ensures successful deployments are completed without errors related to missing DigitalExperienceBundle components. Impacted Module: Custom Deployments with Digital Experience bundles.
We resolved an issue where AutoRABIT failed to commit the latest package version to the sfdx-project.json file. When a new package version is created, it is now correctly updated and committed in the sfdx-project.json file, ensuring consistency between the project configuration and the deployed package versions. Impacted Module: CI Jobs.
Release Date: 22 December 2024
Patch to fix bugs in the nCino Query Validation module.
Release Date: 24 November 2024
The following enhancements and support fixes have been implemented with this release to improve features and functionality and streamline the user experience.
The EZ-Commit workflow now supports special characters in commit comments, including German characters (ä, ö, ü) and punctuation marks (colon [:], semicolon [;], slash [/]). These characters are correctly displayed in commit messages, and the commit process completes without errors when they are used. Impacted Module: EZ-Commit.
The system now supports duplicate detection for all subnodes in Layout metadata, ensuring consistent layout configurations and preventing errors during deployment. Duplicate detection functionality has been extended to include the following subnodes:
Header
RelatedLists
Sections
QuickActionList
Users will be prompted with clear, actionable messages when duplicates are detected in any of these subnodes, allowing them to resolve issues efficiently. This enhancement builds on existing duplicate detection for <layoutItems>, <layoutColumns>, and <layoutSections>. Impacted Module: Back End.
When deploying a profile via the CI Job build, only the selected profile is now included in the deployment. The issue in which Digital Experience metadata was incorrectly included has been resolved, ensuring that deployments contain only the metadata explicitly chosen by the user. Impacted Modules: Every module that uses Digital Experience Bundle Metadata type.
Users can now delete DigitalExperience metadata in the EZ-Commit module. Additionally, support for managing DigitalExperience metadata has been extended across all modules. Impacted Modules: EZ-Merge, Custom Deployment, CI Jobs, Prevalidation Deployments, and Release Labels.
Super Admin users can now successfully extend subscription counts for active accounts. The issue causing an empty notification pop-up when attempting to increase subscriptions has been resolved. Impacted Module: SuperAdmin - Extend Customer tab. Found in QA.
The Vlocity deployment process has been updated to address issues with visibility and interaction:
Deployment History Display:
Vlocity deployments now appear correctly in the deployment history, ensuring users can track and review their deployments without issues.
UI Interaction Fix:
These improvements enhance the usability and reliability of Vlocity deployments in ARM. Impacted Module: Vlocity Deployments.
The notification system for scheduled code coverage reports has been improved to accurately reflect changes in settings.
Test-Level Changes:
When the test level is altered for a scheduled code coverage report (e.g., weekly schedule), the notification now correctly indicates the change instead of displaying "no changes detected."
Other Configuration Changes:
This enhancement eliminates misleading messages, ensuring that users receive correct feedback on configuration updates. Impacted Module: Admin-Code coverage report → Reports.
The JIRA credentials mapping process has been improved to eliminate the need for manual workarounds. Credentials using application tokens are now automatically populated in the ALM Mapping section of the profile, without requiring modifications to the default credentials in the ALM Management admin section. This enhancement simplifies the mapping process and ensures seamless integration with JIRA. Impacted Modules: VC Repos, Modularization, EZ-Commit, My Account, SF Org Management.
The release label deployment process has been enhanced to prevent failures caused by empty metadata. When no deployable changes exist and the package.xml is empty, the system now accurately reflects the absence of metadata in both the UI and back end, ensuring consistency and preventing deployment errors. Impacted Module: Release Labels.
The issue in which notification emails were not being sent to new users upon creation in ARM has been resolved. New users now receive a notification email in their mailbox immediately after being created by an admin, ensuring consistent communication and a smoother onboarding process.
Release Date: 10 November 2024
ARM now supports Salesforce API Version 62 for all functions, allowing users to utilize the latest metadata types and capabilities introduced by Salesforce. This upgrade includes comprehensive integration across all ARM functions, including the Data Loader, ensuring alignment with Salesforce's Winter '25 release. ARM Admins can set the global API to version 62, ensuring consistent functionality across all features.
ARM now ensures accurate tracking of metadata counts across multiple deployments using previous deployment labels. The request node sent for deployment has been corrected in the front end, ensuring that when performing a follow-up deployment with a prior label, all specified components are included. This enhancement resolves issues in which subsequent deployments using previous labels reflected only a partial count of metadata components, providing a consistent and complete deployment experience across repeated operations.
A new confirmation prompt has been added to notify users when a deployment includes only destructive changes and no constructive changes. This enhancement helps clarify deployment contents, reducing potential confusion for users who may expect other metadata components to be included.
The backup.zip file now includes the destructiveChanges.xml file, allowing users to access destructive change data for potential rollback scenarios. This enhancement provides a more comprehensive backup package to support safer and more flexible deployment management.
Enhancements have been made to the commit label search feature to address two user concerns:
Accurate Filtering with Special Characters: The search functionality on the Commit Labels screen now retains all special characters in commit labels, allowing for precise search results even with special characters.
Consistent Label Retrieval Across Screens: The commit label creation and retrieval processes have been standardized across the EZ-Commit and Commit Labels screens. This ensures accurate search results by aligning label keys, resolving prior issues with locating commit labels by revision.
These improvements enhance usability and consistency within the Version Control module, providing a more reliable experience for commit label management.
An update has been made to ensure proper display of revision numbers in EZ-Merge confirmations. Previously, certain revision formats containing the character "e" were misinterpreted as exponential values, causing them to display incorrectly as "Infinity" or scientific notation.
This issue has been resolved by adjusting the response handling, allowing revisions to appear as intended without conversion errors. This enhancement improves the accuracy and reliability of revision details displayed during merges, especially for branches with specific revision formats.
An improvement has been made to the Quick Deploy feature to ensure the Deployment Label Name and Asynchronous ID fields auto-populate after a validated deployment. This update addresses issues in which these fields were previously blank, preventing users from completing Quick Deploy without manually reentering data.
This enhancement improves efficiency and consistency for custom deployments, particularly for users working with single revision DX deployments.
An update has been implemented to ensure stable loading of the Permissions View in the Admin module for newly created teams under Subscription Management. Previously, permissions were not displayed due to an incomplete setup for new users created via the "Create Team" option.
Now, the releaseNotify setting for new users defaults to "true," and additional checks have been added to handle null values during data conversion. This enhancement ensures permissions load reliably, enhancing usability for subscription-based team management.
A fix has been implemented to prevent blank pages from displaying when editing CI jobs. Previously, attempting to edit CI jobs with no rules configured for Checkmarx would result in an unresponsive, blank screen.
This enhancement includes a null check, ensuring CI jobs are editable even if no rules are set for Checkmarx configurations. This update improves stability and usability for managing CI jobs in ARM.
An update has been made to ensure successful deployments when using tags in the deployment module. Previously, deployments initiated with tags would sometimes fail with a "No Changes are found in the package" error due to issues with file copying during tag-based deployments.
This enhancement ensures accurate file handling for tag-based deployments, providing stable and reliable performance for both DX and non-DX branches.
An update has been implemented to improve the accuracy of error messages displayed in CI job logs and deployments. Previously, CI jobs that encountered baseline revision failures or exceeded file limits displayed misleading error messages. Additionally, deployment failures were showing unrelated errors, such as "Invalid Login," instead of indicating the true cause, such as reaching Salesforce file limits or the need for reauthentication.
This enhancement ensures that CI job and deployment errors reflect the actual underlying issues, providing users with clearer, more actionable information for troubleshooting.
An update has been applied to the direct commit process to ensure that both profiles and permission sets are committed together when selected. Previously, when committing Field-Level Security (FLS) for profiles and permission sets in a single direct commit, only profile FLS was committed, while permission sets were excluded.
This enhancement aligns direct commit functionality with pre-validation commits, allowing selected metadata types—including profiles, permission sets, and custom fields—to be consistently committed as intended. This update improves accuracy and flexibility for version control management within ARM.
Improved Merge Conflict Resolution Status
An update has been applied to ensure accurate status updates during merge conflict resolution in EZ-Merge. Previously, after resolving a conflict, the status was sometimes incorrectly set to "Commit," even when additional conflicts remained. This led to repeated merge conflict prompts after refreshing the page.
With this fix, the merge status will correctly display as "In Progress" when unresolved conflicts are pending, and actions will show as "Check Details" instead of "Commit." This enhancement ensures clearer guidance during conflict resolution, streamlining the merge process in EZ-Merge for better user experience.
An improvement has been made to reduce "Network Connection Interrupted" errors when expanding large files under the "Files Changed" tab in EZ-Merge. Previously, each line in files exceeding 3,000 lines triggered an individual API call to fetch inline comments, leading to network interruptions and interface freezes, particularly for files with 15,000 lines or more.
With this enhancement, a single API call now retrieves all inline comments at the file level, significantly improving performance and stability when working with large files. This update prevents excessive network calls and enhances usability during merge and commit actions.
An update has been made to the "Re-use Previously Validated Commit Labels" functionality to ensure that only selected components are included in the commit. Previously, when reusing a validated commit label, additional, unintended changes (such as Profiles and Permission Sets) could appear in the "Files Changed" tab during the approval stage, even if only specific components were selected initially.
This enhancement corrects the commit process so that only the selected components are retained and displayed in the commit, providing more reliable control and accuracy over component selection in EZ-Commit. This improvement applies to both DX and non-DX formats and supports all commit types, including manual selection, auto-draft, commit templates, and package uploads.
Release Date: 27 October 2024
Manageable-State Selection for Branching Baseline A new option has been added to select the Salesforce org's manageable state when initiating or re-running a branching baseline. This option is available only when the retrieval type is set to Salesforce, ensuring greater control over the data types included in the process.
Consistent Manageable-State Dropdown Across Modules The manageable-state dropdown is now consistently available across several modules, streamlining the user experience. It can be found in the following areas:
Branching Baseline
CI Job (Org to Org deployment)
EZ Commit
Conditional Abort Functionality for Branching Baseline The "Abort" button is now only clickable when the branching baseline process is actively in progress. The abort functionality behaves as follows:
If the process is in the retrieval stage, clicking "Abort" will stop the operation.
If the process is in the committing stage, clicking "Abort" will cancel the process.
If the revision has already been generated or committed, the "Abort" button will be disabled to prevent unnecessary actions.
Enhancement: Updated Actions in Branching Baseline The actions available for each branching baseline iteration now include "Run," "Abort," and "Delete," providing clear and accessible options based on the process state.
Enhancement: Combined Revision and Info Section in Iterations The "Revision" and "Info" columns in the branching baseline iterations section have been merged into a single "Revision Info" column. This section is now a clickable hyperlink, allowing users to view detailed information for each specific revision easily.
Improved Abort Functionality with Interrupt Method (Internal) The abort functionality has been enhanced across the application by implementing the recommended interrupt method, significantly improving reliability and preventing potential thread-related crashes. This update ensures a smoother and more stable abort process.
The enhanced abort functionality has been applied to the following areas:
Admin
CI Jobs
Version Control Release Labels
Thorough internal QA checks have been performed to ensure the stability of this new approach.
Enable the “Trigger Build On Commit” option when creating a CI Job Users can now enable the “Trigger Build On Commit” option when creating a CI Job, allowing automated builds triggered directly by commits. Upon selecting this option, a webhook setup will become available, ensuring that every new change in the version control system triggers an update to the CI Job. Builds will only initiate for commits made in the feature templates folder.
Accurate Merge Status Display
Customers reported receiving expiry email notifications with a misleading status of "MERGED," even though the merge was still pending approval or awaiting changes to be committed. This confusion has been addressed by updating the merge status in the expiry email. Now, the system retrieves the status from the SCM History table, ensuring the actual state of the merge is reflected. Users will no longer see "MERGED" unless the merge has been fully completed, providing clearer communication on the status of their merges.
Profile Comparison Layout and Behavior Fixes
The following issues in profile comparison have been resolved by adding the "Person Account" column dynamically when person accounts are enabled:
Record Type Column Fix: The Record Type section in new profile comparisons now displays only two columns, as expected. The third column, "Person Account Default," will only appear in the downloadable report if person accounts are enabled.
Layout Fix: The layout issue where five columns were displayed instead of six during profile comparisons has been addressed.
Default and Visible Field Fix: The issue where users could check 'Default' without checking 'Visible' and could not uncheck 'Default' once selected has been fixed.
These changes ensure a more accurate and dynamic display in profile comparisons, improving the overall user experience.
Select All Behavior Correction in Deployment Tab
A UI bug in the Deployment tab has been fixed where unchecking a metadata member under the "All Metadata" tab did not update the "Select All" option as expected. The condition for deselecting "Select All" has been corrected based on metadata types in the front end, ensuring that when individual metadata members are unchecked, the "Select All" option now responds accurately and reflects the correct selection status. This fix improves the consistency and usability of the deployment process.
Apex Test Class Live Status Fix
The issue where the Live status for the Apex Test Class was not populating under the SF Org Management section has been resolved. The fix involved changing the response data type from text to JSON, allowing the Live status to be fetched and displayed correctly for Apex Test Classes. This update ensures accurate status reporting for users.
Vlocity Deployment Failure Fix
A code fix has been implemented to resolve the issue where Vlocity deployments were failing during VC incremental deployments. The failure occurred because the CI job picked a different dependency, specifically the contentVersion dependency, which was not included in the release label deployment. The fix removes non-Vlocity components during CI deployments, ensuring that only relevant dependencies are picked, resulting in consistent and successful Vlocity deployments.
Board Type Selection Fix in Release Label Merge
An issue where the board type was automatically changing from Vlocity to Salesforce during release label merges has been resolved. The problem occurred because the board type was not being explicitly set to Vlocity during the merge operation, causing Salesforce to be selected by default. This fix ensures that the correct board type, Vlocity, is maintained during the merge process.
Unrelated Changes in EZ-Merges Fix
A fix has been implemented to address the issue of unrelated changes being pulled into EZ-Merges. To prevent this, the system now cross-checks the remote head revision against the local revision before allocating the workspace, ensuring the workspace is properly synced with the remote repository.
Additionally, loggers have been added to track and identify the root cause should this issue recur in the future. These updates ensure a more reliable and controlled merge process, reducing the chance of unintended changes being included in EZ-Merges.
Manual Deployment Destructive Changes Fix
An issue was identified during manual deployments using AutoRABIT Build, where clearing all pre-destructive changes did not exclude them as expected. This occurred when deploying via the Metadata.zip option in non-DX custom deployments, where destructive changes were still included despite being deselected.
A code fix has been implemented to ensure that when pre-destructive changes are cleared during deployment, they are properly excluded from the process. This update ensures that all selected components are correctly deployed, without any unwanted destructive changes being included.
Review Artifact Screen Icon Display Fix
An issue on the Review Artifact screen where icons were not displaying correctly during keyword searches (Ctrl + F) has been resolved. Users previously saw only box icons, leading to confusion about the functions of each icon.
The fix involved correcting the file path for font icons and updating the CSS to ensure proper loading. Icons now display correctly, providing clear visual guidance for each action on the screen. Support Case #123456
NamedCredential Search and Substitute Fix
An issue was identified where the "Search and Substitute" feature was not working for the NamedCredential metadata type. The problem occurred because the metadata type was misspelled as "NamedCrendential" in the configuration file.
The root cause has been addressed by correcting the spelling of "NamedCredential" in the JSON file that maintains supported metadata types and their subnodes.
Deactivated User Deletion Error Fix
An issue where an error pop-up appeared when attempting to delete deactivated users has been resolved. While the user was successfully deleted after a page refresh, the error caused confusion.
The fix involved correctly reading the JWT token during the deletion process, ensuring that inactive users can now be deleted without triggering an error message. This update streamlines the user deletion process and eliminates unnecessary pop-ups.
Validation Job NullPointerException Fix
An issue causing validation CI jobs to fail with a java.lang.NullPointerException has been identified. The problem occurred intermittently when the customer changed the baseline revision, with the workaround only providing temporary relief.
A fix has been implemented to address the root cause of the null pointer error. This ensures that validation jobs now run consistently without failure, eliminating the need for manual interventions or workarounds.
Workspace Error in EZ-Commit Delete Tab Fix
An issue where users encountered a "Workspace does not exist" error in the Delete tab of EZ-Commit has been resolved. The error occurred because the system did not check whether the workspace was optimized before throwing a custom exception when the workspace was not locked.
A fix has been implemented by adding a condition to ignore optimized workspaces when checking for locks. This ensures that users no longer see the error pop-up when navigating to the Delete tab in EZ-Commit, improving the overall functionality. Support Case #124537Improvements
Optimized Selective Deployments Selective deployments have been optimized to utilize pre-prepared artifacts, eliminating the need for additional Git operations. This enhancement allows users to perform component selection directly on the pre-prepared artifact, ensuring faster deployment times and reducing the risk of errors associated with manual Git interactions.
Lazy Loading for EZ Commit Data Tables The EZ Commit process now includes lazy loading for metadata components when using the Auto Draft functionality. Initially, only necessary data is loaded, with additional data fetched as the user scrolls or navigates through the table. This ensures a more efficient and responsive experience.
Lazy Loading in Package Manifest and Commit Template Lazy loading has also been implemented in the Package Manifest and Commit Template screens and the Selected and Deleted tabs, enhancing performance and responsiveness across these areas.
A visual indicator has been added during the loading process, ensuring users are informed while additional data loads, without any noticeable delays or interruptions to the user experience.
Third-Party Library Upgrades Third-party libraries have been upgraded to ensure the latest enhancements and fixes from external libraries, improving overall stability across the platform.
By streamlining the selective deployment process, this improvement enhances efficiency and contributes to a more reliable release management workflow.
Release Date: 25 August 2024
Improved Reporting Features and Enhancements
The new merge report is now included in the downloaded reports.
Failure/Auto-reject reasons have been added to the reports for merge, commits, deployment, and CI build jobs, ensuring that if any jobs fail, the reason is included in the reports.
Extra fields have been correctly added to the current report.
The name of "Latest Reports" has been changed to "Refresh Reports View."
Users are now restricted from downloading more than six months of data.
Post-download, headers, alignment, and naming conventions in Excel have been checked for readability and usability.
Exclude Metadata in the Branching Baseline Users can now customize their baselines by excluding specific metadata. When selecting the "New Branching Baseline" option, a pop-up appears with available fields. A new "Exclude Metadata" checkbox allows users to choose what metadata to include or exclude from a scrollable or searchable list, with individual checkboxes for each item. Options to "Check All" or "Uncheck All" are available in both sections. Once selections are made, users can click "OK" and then "Run" to execute the process.
Detailed Status Messages for Branching Baseline Process To improve transparency and usability, the branching baseline process now provides specific status messages for different failure scenarios. If some metadata members fail to commit, the status will display as "Partial Success" or "Failed." Users can download the files of the failed batch metadata XML files for better feasibility and view failure reasons, reducing troubleshooting time and improving overall efficiency.
Updated UI and Pagination The UI for EZ-commit, deployments, and commit template screens has been updated with pagination for metadata-type tables. Users can now adjust the number of entries displayed per page.
Pagination Availability:
VC Commit: Components selection screen.
Commit Template: Components selection screen.
Deployments: Retrieval screen and "Additional Metadata" section.
In this release, we revolutionized the system by converting all JSP pages into a RESTful API, enhancing modularity, scalability, and interoperability.
SOAP to REST services were upgraded.
Third-party libraries were upgraded.
Release Date: June 2024
Version 24.1 – Enhancements and Improvements
Perform Validation Deployment for Multiple Orgs In this release, we're thrilled to introduce an enhanced Validate Deployment feature, responding to a key user request. Users can now choose multiple orgs simultaneously, enabling a forward-looking validation process as they promote from one sandbox to the next and eventually to production. This time-saving enhancement allows users to select up to three organizations from a convenient multi-picklist, and the subsequent summary screen provides a consolidated view of the deployment results for each selected organization. The implementation ensures a seamless experience by allowing users to toggle between different org validations. The introduction of this feature in the EZ-Merge and EZ-Commit options streamlines deployment validations, contributing to a more efficient and informed deployment workflow.
Incorporated Checkbox to Skip Prevalidation Criteria In this release, we're excited to introduce the ability for developers to skip all prevalidation criteria specifically for back merges from designated branches. This enhancement offers a streamlined approach to the back merge process, empowering developers to improve efficiency and simplify code migration upstream. To leverage this feature, developers can configure the branch type in VC Repos → Branch settings, where a new checkbox option allows you to enable skipping prevalidation criteria for a particular branch during back merges. This capability enhances flexibility and productivity, reducing unnecessary steps in the code migration workflow. With the skip option, developers have greater control over the back merge process, ensuring a smoother and more agile development experience.
This update improves the tool's efficiency and responsiveness and leverages new technologies, collectively resulting in a smoother, faster user experience.
In this release, we revolutionized the system by converting all JSP pages into a RESTful API, enhancing modularity, scalability, and interoperability.
SF CLI Version upgrade to 2.41.8
SOAP to REST services upgrade: Upgrading from SOAP to REST services improves performance by reducing overhead with lightweight JSON payloads and enhances security through stateless communication and simplified implementation of HTTPS.
By merging SalesforceDxHub into SalesforceOrg, it effectively reduces redundancy in data storage. Users can now register once from SalesforceOrg, with the added capability to specify a registered org as a Dev hub. When a production org is registered as a Dev hub, it appears on both screens, streamlining data management and enhancing user workflow. This release optimizes data storage, improves user experience, and simplifies registration processes, ultimately enhancing overall system efficiency.
The following weekly fixes were implemented.
ARM 24.1.7
A code fix was applied to the CI Jobs module of version 24.1 related to a data error that caused a CI Job to be unable to be built manually. Support ticket #117587
A code fix was applied to the Admin module of version 24.1 due to a data error that caused Salesforce orgs to not be displayed as mapped to the repository even after enabling them under the profile. Support ticket #117542
A code fix was applied to the nCino module of version 24.1 due to a use-case error identified internally in which rollback failed for inserted records.
A code fix was applied to the nCino module of version 24.1 due to a use-case error in which Data Loader jobs were automatically being deleted. Support ticket #117577
ARM 24.1.6
A code fix was applied to the CI Jobs module of version 24.1 due to a typo in the ARM CI Jobs creation screen. Support ticket #116616
A code fix was applied to the Deployments module of version 24.1 due to a use-case error in which the 'add member' option was not working. Support tickets #116545, #117480
A code fix was applied to the Admin module of version 24.1 to correct a use-case error in which test class mappings were missing. Support tickets #116984, #117737
A code fix was applied to the Admin module of version 24.1 to correct a use-case issue with log visibility in the branching baseline for admin users. Support ticket #117485
ARM 24.1.5
A code fix was applied to version 24.1 as a result of a data error encountered in the CI Jobs module related to CI Jobs not triggering. Support ticket #116677
A code fix was applied to the Version Control module in version 24.1 related to a data error causing the WebLink deletion feature to not work. Support ticket #115994
A code fix was applied to the CI Jobs module in version 24.1 due to a data error identified internally with the CI Edit edit mode where the "Do you want us to update the test classes" feature is not saving.
A code fix was applied to the nCino module in version 24.1 related to a use-case error in which DataLoader Pro was not fetching the child object. Support ticket #116928
ARM 24.1.4
A use-case error identified in version 23.1 required a code fix applied in versions 23.1 and 24.1 to the Deployment and Version Control modules, to correct a scenario in an org-to-org full-profile deployment in which package visibility and permissions were not captured. Support ticket #110760
A code fix was applied to versions 23.1 and 24.1 due to a use-case error identified in version 23.1 in which commits were failing with a 'no credentials mapped' error in the Version Control module. Support ticket #116704
A code fix identified in version 24.1 was applied to the Admin module in version 24.1 due to a use-case error identified by internal ticket in which the on-premises server was not starting up after migrating from 23.1 to 24.1 build.
ARM 24.1.3
A use-case error identified in version 24.1 required a code fix to the CI Jobs module, applied in versions 23.1 and 24.1, to correct instances where configuration changes were not being saved to the CI job. Support ticket #116047
A code fix identified in version 24.1 by an internal ticket was implemented in version 24.1 to correct a use-case error in which the Version Control module’s Validate and Merge button was not being reflected immediately after changing the EZ-Merge validation criteria in MyAccounts.
A code fix identified in version 24.1 by an internal ticket was applied to version 24.1 due to the minimization feature not working in the Version Control module.
ARM 24.1.2
A data error reported in version 23.1 with the Version Control module that resulted in version control being deleted was resolved in both 23.1 and 24.1 through adding loggers. Support ticket #114503
A use-case error reported in version 23.1 with the Version Control module in which the user was unable to use an existing conflicted file, which resulted in reraising merge requests, was resolved in both 23.1 and 24.1 through a code fix. Support ticket #115084
A use-case error reported in version 23.1, which resulted in an issue with the Data Loader module in which the software was not inserting the correct record type, was resolved in both 23.1 and 24.1 through a code fix. Support ticket #114076
ARM 24.1.1
A code fix was applied to the Version Control module for a use-case error related to an EZ-Commit re-login issue identified. Support ticket #115664
A code fix was applied to the Version Control and Admin modules for a use-case error related to an issue in which Azure ADO connection and password were returning errors. Support tickets #115489, 115558
A code fix was applied to the Version Control module for a use-case error related to a validation org being requested when attempting to merge changes. Support ticket #115787
A code fix was applied to the Version Control module for a use-case error related to the create artifact button not being visible when attempting to create a release label.
See the recent updates to notes as well.
September 2023
Version 23.1 – New Features, Enhancements, and Improvements
Supports Provar Current Version: 2.10.1
Supports Apex PMD Current Version: 7.0.0
1. Automatic Merge after Successful CI Build We know that understanding and managing version control can sometimes be a challenge. ARM offers the flexibility to cherry-pick branch revisions for merge or deployment. Now you can automate this process of cherry-picking the revisions in CI Jobs as a post-deployment step.
The 'Run Merge process on successful deployment' feature keeps track of builds in source branches and merges them into a designated destination branch if they meet the configured criteria (for example, if the build is successful). Rather than requiring manual effort, upstream merges may now be automated by the Salesforce Release Manager using revision numbers that were determined as part of a build cycle in CI jobs.
Users will be notified via email of the success or failure of the automated merge process.
2. Create and Install an Unlocked Package Version from a Version Control Branch Use ARM CI intelligence to create a package version, build using the SFDX project structure in a Version Control branch, and install the same in the destination org of your choice—all from the same page.
You can now generate an unlocked package version automatically through the CI job, and as part of the deployment, it is deployed in the same build cycle. Until the 22.2 version, it picked the latest package version that was already successfully created in ARM.
When users create a CI job using this option, ARM checks the Version Control. If there is a change, it builds a new version on top of the packages. Once the package is created, then the deployment is triggered automatically.
3. Create Connected Apps ARM now gives access to users to create and maintain their OAuth credentials. Users can set up the Connected Apps for Jira OAuth and register the credentials with ARM.
You can add, edit, and delete your Jira login credentials instead of contacting AutoRABIT to manage the connected apps. Once created, simply provide us with the connected app details like Client ID and Secret Keys.
We use these details to connect as an ALM and test the connection.
4. RESTricted Emails The new RESTricted Emails section on the Notifications page of the Admin module helps ensure that ARM-related emails are not sent to deactivated users.
Admins can either add users to this list manually or deactivate the respective users from the Users page of the Admin module, and they will be automatically added to this list. These users will not receive ANY emails including deactivation, forgotten password, reset password, jobs executed in the application, etc. Admins can also use the same two methods to reactivate a user and remove them from this list.
There is also a provision for an Admin to remove all users from the RESTricted Emails list at once.
5. Dependency Analyzer Dependency Analyzer helps you understand the dependencies among various components in your Salesforce org. It allows you to analyze the relationships among objects, fields, classes, triggers, and other metadata components.
With Quality Gates, ARM helps Salesforce developers run multiple checks to understand if and how their commits can break a Salesforce org. Currently, we enforce the following gates:
SAST, SSPM, and AST (Static Code Analysis, Salesforce Security Posture Management, and Application Security Testing)
Deployment Validation
File Change Footprint
Peer-to-Peer Code Review
With the introduction of the Dependency Analyzer, we can offer a fourth gate, Dependency Check, which will allow users to see what they are missing due to Salesforce specificity.
We have introduced the Dependency Analyzer in CI Jobs for now, and this is just a start at bringing this functionality to the remaining modules soon.
Users now have the option to ‘Run Metadata Dependency on Failed Deployments’ to view the results of failed metadata components with their dependencies and download them in Manifest and XML formats.
6. ServiceNow – ALM Management The ARM–ServiceNow integration automatically posts updates to ServiceNow tickets. It makes tracking the status of your user stories and support tickets faster and easier. Tasks can be organized by project, allowing an organization to track issues within projects transparently.
ServiceNow will make information more easily accessible and workflows more streamlined, reducing the time and effort required to manage and resolve service requests. Additionally, the integration will allow teams to work more effectively, improving collaboration and communication.
Salesforce Spring (API 57.0) & Summer (API 58.0) Support AutoRABIT supports the most recent API 57.0 & API 58.0 versions in this release to keep our product updated with Salesforce updates. The most recent API version is intended for customizing and developing tools to manage the metadata model.
Exporting Selected User Details Users with Admin access can now choose the fields they want to include while exporting users' details to a CSV file. While selecting the Export option, the list of available fields is displayed. Admins can select and deselect the required fields by clicking the corresponding checkbox. Some of the fields are selected by default for ease of use. Admins can always deselect these fields if they are not required. Thus, based on the teams with whom they will be shared, Admins can customize the fields in the list.
More Info on CI Jobs and Info Users are now able to view the CI Jobs they created in the CI Job List screen to date inside ARM. The list is displayed in chronological order with the most recent jobs listed at the top.
This update has implemented significant performance upgrades to enhance the tool's efficiency and responsiveness. These enhancements encompass optimized queries and leverage new technologies, collectively resulting in a smoother, faster user experience.
ARM 23.1.40
A code fix was applied to the CI Jobs module of versions 23.1 and 24.1 related to a use-case error causing the CI Jobs History report to not generate. Support ticket #116943
ARM 23.1.39
A code fix was applied to the Version Control module in version 23.1 related to a use-case error in which the merge completion was taking too long. Support ticket #113102
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error in which an issue was occurring with the system administrator lite. Support ticket #117297
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error in which the user was not able to see the metadata through the single revision deployment. Support ticket #116919
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error in which the user was not able to deploy the Einstein Prediction builder. Support ticket #116909
ARM 23.1.38
A code fix was applied to the nCino module in version 23.1 related to a use-case error in which Data Loader Pro was not fetching the child object. Support ticket #115313
ARM 23.1.37
A use-case error identified in version 23.1 required a code fix, which was applied in versions 23.1 and 24.1 to the Deployment and Version Control modules, to correct a scenario in an org-to-org full-profile deployment where it was not capturing package visibility and permissions. Support ticket #110760
A use-case error identified a code fix needed to the Reports module of version 23.1 to fix a product test class in which the weekly scheduled job failed. Support ticket #115654
A code fix was applied to versions 23.1 and 24.1 due to a use-case error identified in version 23.1 where commits were failing with a 'no credentials mapped' error in the Version Control module. Support ticket #116704
ARM 23.1.36
A use-case scenario identified an error in version 23.1 with metadata retrieval from the repository failing in the Deployment module, which was resolved in versions 23.1 and 24.1. Support ticket #115818
A code fix identified in version 23.1 was applied to correct a use-case error in the Version Control module of version 23.1 related to commit templates. Support tickets #116124, #116138
A code fix identified in version 23.1 by internal request ticket was applied to the Admin and CI jobs modules in versions 23.1 and 24.1 to upgrade v61 (Beta) to v61.
A use-case error in version 23.1 required a code fix to version 23.1 Deployment and Version Control modules due to an org comparison not showing diff results. Support tickets #112752, #116025
ARM 23.1.35
A data error reported in version 23.1 with the Version Control module that resulted in version control being deleted was resolved in both 23.1 and 24.1 through adding loggers. Support ticket #114503
A use-case error reported in version 23.1 with the Version Control module in which the user was unable to use an existing conflicted file, which resulted in reraising merge requests, was resolved in both 23.1 and 24.1 through a code fix. Support ticket #115084
A use-case error reported in version 23.1, which resulted in an issue with the Data Loader module in which the software was not inserting the correct record type, was resolved in both 23.1 and 24.1 through a code fix. Support ticket #114076
ARM 23.1.34
A code fix was performed due to a use-case error related to the CI Jobs module in which nCino CI Jobs were not triggered by metadata CI Jobs on success. Support ticket #113887
A code fix was performed due to a use-case error related to the Version Control module in which the API response from CodeScan returned a page not found (404) error in ARM. Support tickets #108895, #115120, #114434
A code fix was performed due to a use-case error related to the Deployment module in which the Deployment button was not enabled in AutoRABIT after validation. Support ticket #107108
A code fix was performed due to a use-case error related to the Deployment module in which the user was unable to deploy a Bot from a Branch to a sandbox. Support ticket #11497
ARM 23.1.33
A code fix was applied to all modules prompted by an internal change request in preparation for support of the Salesforce Summer '24 release. This will require updates to internal documentation.
A code fix was applied to the Deployments module resulting from an internal request to correct a use-case error in which a deployment failure and document discrepancy were encountered, with subsequent deployment attempts unsuccessful.
A code fix was applied to the Version Control module initiated by a use-case error in which the team encountered an ALM commit issue related to the label name when testing a user story. Support ticket #113308
ARM 23.1.32
A code fix was applied to the Version Control module to resolve a use-case error in which the user cannot approve or reject a Merge Request when the label name contains a "+" symbol. When the merge label contains unsupported characters, the merge label is not submitted as expected and the validation message displays the supported characters. Support ticket #112715
A code fix was applied to the Admin module related to a use-case error occurring when modifying the Team Administrator, it created duplicate Teams, consuming existing licenses. Support ticket #109457
A code fix was applied to the CI Jobs module due to a use-case error in which a Checkmarx scan was not matching up and breaking the build. Support ticket #105217
(ARM 23.1.31)
A code fix was applied to the Version Control module due to a use-case error related to EZ-Commits and EZ-Merges not taking the master branch, even when Baseline Branch "master" is selected. #107151
A code fix was applied to the Version Control module due to a use-case error in which reverting a commit failed. #112094
A code fix was applied to the Version Control module due to a use-case error related to the system failing to select multiple reports. #112381, #112812
A code fix was applied to the Deployment module due to a data error in which the org sync was not completing. #111545
(ARM 23.1.30)
Code fix applied to Deployments module due to user receiving error message: INVALID_LOGIN: Invalid username or password or security token or API version or user locked out. #111008
Code fix applied to Version Control module due to user not being able to see the merge request label name in BitBucket after merging. This required a feature flag, MERGE_STRATEGY_ENABLE_NON_FF, which is not enabled by default and must be enabled. #110541
Code fix applied to the Deployments module related to user experiencing Redeploy/Promote hanging if previous deployment used specified tests. This requires a feature flag, AR_33697_ENABLE_APEX_TEST_GET_CALL, which is not enabled by default and must be enabled. #110764
(ARM 23.1.29)
(ARM 23.1.28)
(ARM 23.1.27)
(ARM 23.1.26)
(ARM 23.1.25)
(ARM 23.1.24)
(ARM v. 23.1.23)
(ARM v. 23.1.22)
(ARM v. 23.1.21)
(ARM v. 23.1.20)
(ARM v. 23.1.19)
(ARM v. 23.1.18)
(ARM v. 23.1.17)
(ARM v. 23.1.16)
(ARM v. 23.1.15)
(ARM v. 23.1.14)
(ARM v. 23.1.13)
17 December 2023
(ARM v. 23.1.12)
10 December 2023
(ARM v. 23.1.11)
(ARM v 23.1.10)
(ARM v 23.1.9)
(ARM v. 23.1.8)
(ARM v. 23.1.7)
(ARM v. 23.1.6)
(ARM v. 23.1.5)
This was a maintenance release. The following items were enhanced, fixed, or added:
Loggers were added to Reports and Dashboard modules in versions 22.3 and 23.1 due to a data error in which users were unable to fetch a Salesforce code coverage report.
An enhancement was made by a code fix applied to the Deployments and Org Synchronization modules in versions 22.3 and 23.1 enabling users to change deploy text for validations.
A code fix was applied to the CI Jobs module in version 23.1 identified by use case to enable validation CI Job comments
This was an interim maintenance release. The following items were enhanced, fixed, or added:
A Code Fix was applied to the Deployments module due to the Deployment initiated using Org Synchronization failing caused by a use case with a fix applied to versions 22.3 and 23.1.
A Code Fix was applied to the Version control module due to a Validation Error requiring Feature Flag: VALIDATE_DEPLOY_PICK_FILECHANGES_FROM_DIFF caused by a use case with a fix applied to versions 22.3 and 23.1.
A Code Fix was applied to the Reports module due to the Weekly Code/ Test Coverage Report taking a long time caused by a use case with a fix applied to versions 22.3 and 23.1.
22 October 2023
(ARM v. 23.1.4)
This is a maintenance release. The following items were enhanced, fixed, or added.
Performed a code fix to version 23.1 affecting the Reports module resulting from a use-case error with code coverage report emails missing test class errors in the subject.
Applied a code fix to version 23.1 for the Deployments module resulting from a use-case scenario with user unable to see deployment history.
Instituted a code fix to version 23.1 for the CI Jobs module resulting from a use-case error with the org management page.
This interim release consisted of the following:
Performed a code fix to versions 22.3 and 23.1 affecting the Version Control module for a use-case issue with a custom label translation file.
(ARM v23.1.3)
AutoRABIT provided the API 59.0 changes as part of its weekly fixes on both 22.3 and 23.1. This is available only for ARM modules, not for Dataloader or nCino. For DL and nCino, API 59.0 changes will be available next week as part of the Wednesday fixes deployment.
This is a maintenance release. The following items were enhanced, fixed, or added.
Instituted an enhancement via code fix to versions 22.3 and 23.1 affecting all ARM modules, applying Salesforce v.59 upgrade for Winter 2024.
Performed a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the CI Jobs module concerning a package directory issue.
Applied a code fix to versions 22.3 and 23.1 due to a use-case scenario pertaining to the Environmental Provisioning module with users not able to generate a migration template using the migrate custom setting data module
Performed a code fix to versions 22.3 and 23.1 related to a use case scenario affecting the Version Control module related to ALM tickets being bugged after using the ALM sync refresh.
Performed a code fix to version 23.1 related to the Deployments and CI Jobs modules affecting a use-case error being issued during CI Deployment for property 'userLicense' not valid in version 57.0.
This is a maintenance release. The following items were enhanced, fixed, or added.
Performed a code fix to versions 22.3 and 23.1 for a use-case error affecting the Admin module relating to code coverage issues.
Applied a code fix to versions 22.3 and 23.1 related to a use-case error in the Deployments module concerning a flow component missed in the deployment.
Implemented a code fix to versions 22.3 and 23.1 for a use-case error related to a specific customer’s fields for redeployment.
(ARM v23.1.1)
This is a maintenance release. The following items were enhanced, fixed, or added.
A code fix was applied to the version control module in releases 22.3 and 23.1 due to a use-case error with a user being unable to create a new commit.
A code fix was performed in the 23.1 release to the version control module for a use-case error when merging destructive changes.
A code fix was instituted to the CI Jobs module in version 23.1 to address when a CI job has two different package directories. Changes were failing under one package when the analysis was completed in CodeScan.
(ARM v23.1) This is a maintenance release. The following items were enhanced, fixed, or added:
A code fix was applied to the Deployment module due to a data error concerning an Org difference pulling changes from the managed packages.
We would like to inform you about the End of Life (EOL) for ARM version 22.3. Per our support agreement, this version is now more than 365 days old and is no longer supported. As part of our ongoing commitment to providing the best possible experience for our users and maintaining the highest standards of security and performance, we have made the decision to discontinue support for ARM 22.3.
End of Life Date: April 1, 2024
What Does This Mean?
End of Support: As of April 1, 2024, we will no longer provide maintenance updates, bug fixes, or technical support for ARM 22.3. This includes both security and non-security updates.
Security Risks: Continuing to use ARM 22.3 after the end of support date may expose your system to potential security vulnerabilities, as we will no longer release security patches.
Upgrade Recommendations: We strongly recommend migrating to a supported version of ARM to ensure continued reliability, security, and performance. Our team is available to assist you with this transition process and provide guidance on your upgrade.
Action Required:
To mitigate any potential risks associated with the EOL of 22.3, we urge you to take proactive steps towards upgrade immediately. Our customer success and support team are here to assist you every step of the way. Please reach out to your CSM to plan this work.
We understand that this transition may present challenges, and we sincerely apologize for any inconvenience it may cause. However, we believe that focusing our efforts on our latest offerings will ultimately benefit you with enhanced features, improved performance, and better security.
Thank you for your understanding and continued support.
December 2022 - Version 22.3 - New Features, Enhancements, Improvements and Changelogs
Date of release: 18 December 2022 Article last updated: 31 July 2023
You can now define a data Retention Policy and choose how much data should be stored for how long. ARM will now be considerably quicker by eliminating outdated data. Clearing out old and useless data from the database and moving it to the archives keeps the application from underperforming and improves speed across all modules.
A weekly clean-up will ensure that the application runs smoothly. The default data retention period is set as 12 months which will be implemented with the release of ARM version 22.3. Admins can specify the duration of data retention in the history tables from the My Account section and change the retention period from 12 months to 6 months or 3 months.
Finding a CI Job has never been easier. Instead of scrolling through endless pages, you can search for a job or a group by simply typing the name in the new dropdown lists. You can further narrow the search results by combining these two options to look for a particular job within a group.
Additionally, the filter feature provides further options to narrow the search results by source type, date range, and more.
We just included new functionality to the ARM 22.3 version that allows users to terminate an ongoing Vlocity deployment process or abort it if get stuck. The Deployment History screen contains the Abort option, which allows you to terminate the deployment process.
The revamp of the Release Label page is the feature of version 22.3 that stands out the most. This enhancement is actually a collection of multiple smaller enhancements, each of which is briefly discussed in this section.
While creating a release label, you can choose the specific period for which you want to retrieve the commit history instead of loading the entire commit history, which could take a really long time.
You can also create a release label while simultaneously creating a package simply by selecting a conveniently located checkbox on the same screen.
The selected revisions are also displayed on the same screen and updated dynamically as you select/unselect revisions.
Additional metadata types are now compatible with the Search and Substitute rule, allowing the application to use them for Deployments and Commits.
Until now, the Search and Substitute functionality only had the ability to select a metadata type and then perform the search for substrings across all members in that type. But now, you can select specific metadata members in a type and substitute values for that member(s).
This enhancement is also helpful when users want to add object permissions only to the production and not to the lower sandboxes.
It is also beneficial to have this feature so that the rules can be created and used in CI Jobs to do the replacements automatically, depending on the deployment settings in the CI Job.
Export List is a comprehensive list of all registered users with an organization. This list can be downloaded from the Users module. It includes details like the users' name, email, and title; and information about user accounts created, modified, deactivated, and deleted.
With the recent release, the Export List will include a few additional details related to the last login to ensure security and compliance. Details like the location, login type, IP address, coordinates, and the browser used.
The access level of users is not mentioned in the export list for security reasons, i.e., if any users are Admin or Super Admin, this will not be specified. The company can share this list, if required, with people both inside and outside their organization without jeopardizing the confidentiality of the access granted to the users.
In addition to providing a new name, Dataloader users can now specify a different Salesforce org as a source or destination for the operation while cloning an existing job. This helps the users to reuse the same job configuration with a different Salesforce org without going through the entire process again.
For the Extract operation, users have the option to edit the query corresponding to the new org selected. For Insert/Update/Upsert/Delete operations, users have the option to upload a different .CSV file instead of the original one. Validation is done to verify whether the object is available in the new org and also if the user edits the query for the cloned process.
The /syncbranchcommits service is no longer supported. The users will no longer require Auto-sync functionality to create a release label. This simplifies the function's use and gets rid of unnecessary steps.
For improved user experience, the metadata.zip file upload option has been added to the New Deployment page itself. When uploading large files, this is extremely useful.
The password policy is reduced from 13 previously used passwords not being allowed to 5 previously used passwords. This gives users more options while resetting their passwords after the three months
(ARM v. 22.3.55)
(ARM v. 22.3.54)
(ARM v. 22.3.53)
(ARM v. 22.3.52)
10 December 2023
(ARM 22.3.51)
(ARM v. 22.3.50)
(ARM v. 22.3.49)
(ARM v. 22.3.48)
(ARM v. 22.3.47)
(ARM v. 22.3.46)
(ARM v. 22.3.45)
This was a maintenance release. The following items were enhanced, fixed, or added:
Loggers were added to Reports and Dashboard modules in versions 22.3 and 23.1 due to a data error in which users were unable to fetch a Salesforce code coverage report.
An enhancement was made by a code fix applied to the Environment Provisioning module in version 22.3 to enable users to view Environment Provisioning templates.
An enhancement was made by a code fix applied to the Deployments and Org Synchronization
This was a maintenance release. The following items were enhanced, fixed, or added by code fixes resulting from use-case scenarios:
A Code Fix was applied to the Deployments module due to the Deployment initiated using Org Synchronization failing caused by a use case with a fix applied to versions 22.3 and 23.1.
A Code Fix was applied to the Version control module due to a Validation Error requiring Feature Flag: VALIDATE_DEPLOY_PICK_FILECHANGES_FROM_DIFF caused by a use case with a fix applied to versions 22.3 and 23.1.
A Code Fix was applied to the Reports module due to the Weekly Code/ Test Coverage Report taking a long time caused by a use case with a fix applied to versions 22.3 and 23.1.
22 October 2023
(ARM v. 22.3.44)
This is a maintenance release. The following items were enhanced, fixed, or added.
Implemented an enhancement to version 22.3 identified as part of a use-case issue affecting the Deployments and Org Synchronization modules requiring changing deploy text for validations.
Implemented a code fix to versions 22.3 and 23.1 affecting the CI Jobs module due to a use-case issue to SFDX/CI jobs with package version installation key.
Performed a code fix to versions 22.3 and 23.1 affecting the Version Control module for a use-case issue related to custom label translation file.
This interim release consisted of the following:
Performed a code fix to versions 22.3 and 23.1 affecting the Version Control module for a use-case issue with a custom label translation file.
(ARM v22.3.43)
AutoRABIT provided the API 59.0 changes as part of its weekly fixes on both 22.3 and 23.1. This is available only for ARM modules, not for Dataloader or nCino. For DL and nCino, API 59.0 changes will be available next week as part of the Wednesday fixes deployment.
This is a maintenance release. The following items were enhanced, fixed, or added.
Instituted an enhancement via code fix to versions 22.3 and 23.1 affecting all ARM modules, applying Salesforce v.59 upgrade for Winter 2024.
Performed a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the CI Jobs module concerning a package directory issue.
Applied a code fix to versions 22.3 and 23.1 due to a use-case scenario pertaining to the Environmental Provisioning module with users not able to generate a migration template using the migrate custom setting data module.
Performed a code fix to versions 22.3 and 23.1 related to a use case scenario affecting the Version Control module related to ALM tickets being bugged after using the ALM sync refresh.
This is a maintenance release. The following items were enhanced, fixed, or added.
Performed a code fix to versions 22.3 and 23.1 for a use-case error affecting the Admin module relating to code coverage issues.
Applied a code fix to versions 22.3 and 23.1 related to a use-case error in the Deployments module concerning a flow component missed in the deployment.
Implemented a code fix to versions 22.3 and 23.1 for a use-case error related to a specific customer’s fields for redeployment.
(ARM v22.3.41)
This is a maintenance release. The following items were enhanced, fixed, or added.
A code fix was applied to the version control module in releases 22.3 and 23.1 due to a use-case error with a user being unable to create a new commit.
A code fix was performed for release versions 22.3 and 23.1 to the Deployments module for a use-case error resulting in a buggy deployment with multi packages and the static resources being bugged as well.
A code fix was applied to the version control module in releases 22.3 and 23.1 concerning a use-case error for an EZ-Commit, where the user was unable to view the 'deleted components' tab for the commit template when unchecking the 'skip mappings' checkbox.
(ARM v22.3.40) This is a maintenance release. The following items were enhanced, fixed, or added:
A code fix was implemented due to a use-case error to the Version Control module regarding an issue with merging destructive changes.
A code fix was applied to the Deployment module due to a data error concerning an Org difference pulling changes from the managed packages.
A code fix was applied due to a use-case error relating to the Deployments module with a user unable to deploy components via Org Sync.
A code fix was applied pertaining to the CI Jobs module relating to a use-case error in which the CI Job has two different package directories and changes fall under one package when an analysis is completed on CodeScan
(ARM v22.3.39) This is a maintenance release. The following items were enhanced, fixed, or added.
A code fix was implemented to the Deployment module related to a use-case error encountered when deploying Vlocity components from a Git branch.
A code fix was implemented related to the CI Jobs module to institute best practices following a user session.
A code fix was implemented to the Version Control module related to a use-case error pertaining to [integration_EZ-commit]. User was getting a "no package .xml found to retrieve the members" through package manifest when selecting 'all users or the respective SF org user.'
(ARM v22.3.38)
This is a maintenance release. The following items were enhanced, fixed, or added:
As part of this fix deployment, one of the feature flags, 'RUN_PACKAGE_JOB_ENTIRE_BRANCH_78757,' has been provided. Enabling this feature flag only applies to one specific customer.
Implemented a code fix associated with the version control module for a use-case error in which ALM working items were not loading.
Implemented a code fix for a use-case error pertaining to the version control module for an approval email notification error.
(ARM v22.3.37)
This is a maintenance release. The following items were enhanced, fixed, or added:
Implemented a code fix associated with the version control module related to a use-case scenario in which a review artifact was not working.
Implemented a code fix to the nCino module resulting from a user product suggestion to the deployment history filter.
Implemented a code fix to the nCino module related to an instance in which the org name was not displayed for the destination org value field.
(ARM v22.3.36)
This is a maintenance release. The following items were enhanced, fixed, or added:
Error: "Merging from Devint branch to Developer branch (Back merge) is getting Auto Rejected": Code fix to Version Control module on user merging from Devint branch to Developer branch (Back merge) getting Auto Rejected.
Implemented a UI change to include the “Ignore Warnings” option in both the prevalidation commit and merge flows. This requires a documentation change. See ticket for more details.
Error: “[Client] getting frequent page unresponsive errors in ARM": Introduced a UI change to support Salesforce orgs and the previous label deployment type in the deployment module.
(ARM v22.3.35) This is a maintenance release. The following items were fixed and/or added:
Performed a code fix impacting the Deployments and CI Jobs modules related to use cases in which selected test classes for production were not running and users were having code coverage issues.
Performed a code fix for the Admin module related to a specific user having difficulty with PWD policy.
Performed a code fix to the CI Jobs and Deployment modules relating to users unable to deploy changes to production orgs due to a CI Jobs coding issue.
(ARM v22.3.34)
This is a maintenance release. The following items were fixed and/or added:
Performed a code fix pertaining to all modules relating to an SFDX to SF CLI Hotfix.
Performed a code fix relating to version control, CI jobs, and deployment modules initiated via change request due to ALM working items not loading, resolved by enabling the customer domain name.
Performed a code fix for a data error with feature flag name, ‘Disable_Merge_Rename_Detection’ after a merge was failing and took hours to complete.
(ARM v22.3.33) This is a maintenance release. The following items were fixed and/or added:
Fixed an error under reports where code coverage emails were missing information.
Fixed an error related to a second deployment starting in the middle of a deployment.
Fixed an error in version control module related to not being able to commit or Repush changes in the Training Branch.
(ARM v22.3.32) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with duplicate not working on EZ-merge requests related to version control.
Fixed EZ deployments from a single revision with profiles comp-specific changes pulling all comps during deployments.
Fixed an error related to CI Jobs not running the pipeline.
(ARM v22.3.31) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with a merge use case of handling deleted files in both source and target branches by using git rm command.
Fixed an issue where screen redirects to login page on clicking on User activation email.
Fixed an issue where Commit stuck in InProgress.
Fixed an issue where we receive
(ARM v22.3.26) This is a maintenance release. The following items were fixed and/or added:
Enhanced ARM by allowing PAT Authentication for Jira.
Fixed an issue where user ran an Org Synchronization history job and tried to access the Diff report to see the metadata difference, but the page kept loading indefinitely without the required diff.
Upgraded Provar to version 2.10.1.
(ARM v22.3.25) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where deployment failed with the error message File cannot be loaded.
Fixed an issue where the SharingCriteriaRule component was not deployed to Production even though the user had selected it ().
Fixed an issue where the SharingReasons component was ignored when the deployment/validation was done using Commit Label as source, but the same component was processed using Single Revision deployment or CI Job deployment ().
(ARM v22.3.24) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where a CI job failed to pick the external commit revision which was added to an ALM Label as part of Smart Commits sync ().
Fixed an issue where Class Coverage Report generated was empty for one of the Salesforce orgs, and it was intermittent. The same behavior was observed for RunSpecified and RunLocal test levels ().
Fixed an issue where deploying test classes from manual deployment was throwing an out of memory error ().
(ARM v22.3.23) This is a maintenance release. The following items were fixed and/or added:
Fixed a compliance issue with Apache Commons by removing the text dependency ().
Fixed an issue where CI Jobs were failing due to empty JSON file(s) in the remote repository, and throwing the following error: Failed to initiate deployment. Unexpected end of JSON input ().
Improved the UI by removing the Validate Deployment option if Vlocity is selected, and hiding the whole Board Type option if Vlocity is not enabled ().
(ARM v22.3.22) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where wrong timezone region was displaying for users ().
Fixed an issue where the EZ-Commits report file displayed the file count but not the components count ().
Fixed an issue where clone build jobs were taking between 10 and 25 minutes, which is much longer than expected ().
Fixed an issue where CI job build failed to show changes in the org after deployment (
(ARM v22.3.21) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was having trouble while deploying LighteningMessageChannel components ().
Fixed an issue where Destructive Changes wasn't working as expected while performing an Entire Branch merge ().
Enhanced the ALM management feature by adding an option to sync Smart Commits ().
(ARM v22.3.20) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was getting a validation deployment error while performing release label deployment ().
Fixed an issue where Branching Baseline was taking longer than expected ().
Fixed an issue where using the AutoDraft functionality in EZ-Commit was resulting in a malformed exception in the UI ().
(ARM v22.3.19) This is a maintenance release. The following items were fixed and/or added:
Enhanced the Version Control module by adding SSH Certificate for Git authentication while creating user credentials ().
Fixed an issue where CI Job was picking changes one build but not for the other, and the logs weren't capturing this ().
Fixed an issue where Ignore missing visibility settings function was not working as expected and Record type visibility on the profile was not getting deployed using CI Job ().
(ARM v22.3.18) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the SCA Report failed to run using Codescan plugin with the below Salesforce error: UNKNOWN_EXCEPTION: An unexpected error occurred. ( and ).
Enhanced the VC Repos page by introducing a feature that allows users to sync external smart commits ().
Updated the UI on the External pull request creation page to reflect the Source and Target fields clearly so users can trace which one is the source and destination branches (
(ARM v22.3.17) This is a maintenance release. The following items were fixed and/or added:
Enhanced the SCA report options by removing the 10,000 limit for exporting issues using CodeScan ().
Enhanced Vlocity CI jobs by allowing Local Compilation for Omniscript and Flexcard objects ( and ).
Fixed an issue where user was unable to use the Redeploy/Promote option after ten iterations of an existing Deployment label ().
(ARM v22.3.16) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where validation jobs on Pull Requests weren't getting triggered (, , and ).
Fixed an issue where Salesforce components were showing under the Apex Test Success tab in the Deployment module, which is not expected behavior ().
Enhanced the Branching Baseline feature by allowing admin to define default baseline branches, making it easier for developers to choose the default branch for each project ().
(ARM v22.3.15) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Custom Metadata type access changes were not detected in version control Diff. There was no diff generated even there were changes in metadata access ().
Fixed an issue where user performed a CI job deployment that had 8 destructive change items in the merge PR, but ARM is displaying only 2 destructive changes ().
Fixed an issue where Git backup job was failing due to unsupported metadata ().
(ARM v22.3.14) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Quick action was not picked for destructive changes ().
Fixed an issue where CI job deployment was failing due to the following error:
Error: Cannot set sharingModel to ControlledByParent on a CustomObject without a MasterDetail relationship field (line 0, column 0) ( and ).
Fixed an issue where WebStoreTemplates object was not available for deployment ().
(ARM v22.3.13) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where CI job deployments were failing with the error, Error 405 Only POST allowed ().
Fixed an issue where multiple deployment requests were being generated while performing Org Sync if the user selected all components instead of a few ().
Fixed an issue where Rollback API threw a 200 response but the Rollback immediately failed in the ARM UI ().
(ARM v22.3.12) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Static Code Anaysis was failing due to missing property tag in Apex PMD rules file, but the UI log wasn't displaying this error ().
Fixed an issue where when there was no results generated, the report displayed an error that there are zero metrics instead of displaying the results as zero in all the places when there is no change ().
Fixed an issue where user was unable to deploy a CI job with the RelationshipGraphDefinition components ().
(ARM v22.3.11) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where ARM was displaying incorrect installation settings and package version information in the deployment log while installing the package version from a CI job ().
Fixed an issue where user chose Exclude Metadata Type for a particular metadata type during a CI Job, but it was still deployed ().
Fixed an issue where user was unable to perform Destructive Commit with PermissionSetGroups metadata type ().
(ARM v22.3.10) This is a maintenance release. The following items were fixed and/or added:
Fixed a UI bug in Profile Manager where User Permissions differences are shown in the report but not in the UI ().
Enhanced the Release Label creation by increasing the range of retrievable commit history ().
Fixed an issue where user was unable to use Release Labels to perform Deployment, and it failed while trying to Create Artifact ().
(ARM v22.3.9) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was deploying single revision deployment with only report folder but sub-reports were also getting fetched, and the deployment was failing due to field dependency error ().
Fixed an issue where after deployment with single revision merge, user permission appears to be removed in target org but in the Salesforce target org the user permission is not removed, and an incorrect layout is displayed in UI ().
Fixed an issue where user performed a pre-validation commit and each process like file diff, validate deploy happened thrice as per the logs ().
(ARM v22.3.8) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was unable to download success/failure reports in Single Dataloader ().
Fixed an issue where when multiple CI Jobs are triggered, jobs are moved into the queue as expected, but new jobs are not starting automatically getting processed once the existing jobs is cleared from the CI Job results page ().
Fixed an issue where Dependency order defined in json file was being changed on every commit but it was not supposed to ().
(ARM v22.3.7) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where SFDX module creation log shows that deployment is successful but the module creation had failed ().
Fixed an issue with Backup from Org CI Jobs where PermissionSet User Permissions were being deleted ().
Fixed an issue where Org to Org Deployment for Profiles including Deploy Profile Access Settings for selected components only was not working as expected ().
(ARM v22.3.6) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the deployment was failing with the following error when user was deploying Permissionset with a user-permission Manage Public Documents: Permission Manage Public Documents depends on permission(s): Create Document, Delete Document, Edit Document, Read Document ().
Fixed an issue where CI jobs were failing intermittently with the following error: Getting access token failed from refresh tokenHTTP/1.1 400 Bad Request ().
Fixed an issue where Reports deployment validation failed in
(ARM v22.3.5) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user changed the permissions to list view from visible to all users to visible only for me while using the previous commit label, it is added under the Deleted tab ().
Fixed an issue where commit was running for longer and remained in-progress and validation check log is also in progress ().
Fixed an issue where commits with SFDX metadata structure are failing in metadata retrieval stage ().
(ARM v22.3.4) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Merge validation failed to process when there was a Flow metadata ().
Fixed an issue with user received 6 notifications for a failed CI Job instead of 1 ().
Fixed an issue where user was trying to register branches to AutoRABIT through GitHub, but was getting the following error: Lower Region ().
(ARM v22.3.3) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Admin was able to see the Teams field under ALM Integration but the same field was unavailable for sub-users ().
Fixed an issue where Environment provisioning processes were failing to update when user was trying to change the email deliverability access level from No access to All email ().
Fixed a build bug where CI Job Build was failing during package preparation step 5 failing while commiting DecisionMatrixDefinition and throwing an error ().
(ARM v22.3.2) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was unable to create Environment Provisioning templates for multiple component types ().
Fixed an issue where user was creating an EZ-Commit, mapping the ALM Project (VersionOne) but received the following error: JSONObject["Assets"] is not a string ().
Fixed an issue where AutoRABIT SSH credentials were failing with an error Auth failed while trying to connect with AWS CodeCommit (
(ARM v22.3.1) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Provar jobs were failing due to incorrect files being copied from customer repository branch to Provar project directory ().
Fixed an issue where user triggered a CI Job but it deployed with many more components than expected ().
Fixed an issue where user was performing a single Merge with only two approval process, but while selecting SCA, process is auto rejected ().
(ARM v22.3.0) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with DataLoader Pro where jobs executed in the last 6 months were not showing in the database process table and in the Reports module ().
Fixed an issue with Deploy SFDX Source With ALM Mapping where CI job with ALM Mapping was not working as expected for Team which is not default ().
Fixed an issue where Profile Diff is working as expected for Selective Deployment, but not while using the same profile in the profile manager ().
Date of release: 9 October 2022 Article last updated: 15 May 2023
Mail Settings module in the Admin section is relabeled as Notifications. Through this module, you can choose to send notifications about specific events triggered in ARM to specific groups or channels within your organization through Teams or Slack. For whichever messaging app you use, you can configure a webhook connection for each of the groups or channels, and then integrate them with ARM. You can customize and select which group(s) to notify when events like build failure, build success, deployment failure, merge reports, etc. are triggered.
In addition to the existing static code analysis tools, ARM now provides the ability to choose the Salesforce Scanner CLI plugin.
Most static code analysis tools specialize in one language or a set of languages. Many applications (including typical Salesforce packages), however, contain an assortment of components created using different languages. A single static analyzer is insufficient to address all aspects of such applications, and managing multiple static analyzer tools could prove unfeasible.
This is where the Salesforce CLI Scanner plugin shines. This plugin aggregates the results of static analyzers that are most relevant to Salesforce developers while providing a unified experience.
With the Salesforce CLI Scanner plugin, you can look forward to a:
Single installation process
A single set of commands to interact with multiple rule engines
A unified set of rules that are checked by their respective rule engines
Unified rule violation report that includes all issues identified by the engines.
We’ve added the ability to view and review datasets corresponding to each version of the nCino feature template before using it for deployment. Prior to this release, the capability was available only for the latest version of the template.
With this release, PMD has been upgraded to version 6.49. If you have not uploaded a rules file, ARM will use the default Apex PMD rules file. However, you can add new rules to the default ruleset.
Click to view the list of currently deprecated rules available on GitHub.
We have moved one step closer to automating the flow by adding an option to choose if an EZ-Commit or an EZ-Merge should be approved automatically if the SCA validation is successful. Combined with the existing option to auto-commit on approval, this leads to a true CI/CD experience.
While adding HashiCorp credentials to ARM, you can now choose the AWS Authentication method so that the Vault Token will be generated automatically whenever the existing token expires. Now the user will not have to update the token manually from the application when it expires.
The SFDX CLI has been upgraded to the latest stable 7.169 version.
Key characteristics to look for:
Support for the quick deploy functionality for SFDX jobs.
Use CLI commands to generate the package manifest and rollbacks.
To keep our product up to date with the most recent Salesforce updates, AutoRABIT supports the most recent API 56.0 version in this release. The most recent API version is intended for customizing the metadata model and developing tools to manage it.
With this release, you can choose to merge from one source branch to multiple destination branches upon successful deployment.
In addition to the Standard access type, users can now set up SSO as authentication for Jira using the OAuth access type while registering an ALM. You can also switch between Standard and OAuth access types for already registered ALMs.
Users with Admin access can now turn off the Jira comments and notifications created by AR. This ensures a cleaner workspace. These comments and notifications are very development centric, so the end users who use Jira cannot make sense of our technical comments from AR, and this may create confusion for them.
(ARM v22.2.28) This is a maintenance release. The following items were fixed and/or added:
Fixed a compliance issue with Apache Commons by removing the text dependency ().
Fixed an issue where CI Jobs were failing due to empty JSON file(s) in the remote repository, and throwing the following error: Failed to initiate deployment. Unexpected end of JSON input ().
Improved the UI by removing the Validate Deployment option if Vlocity is selected, and hiding the whole Board Type option if Vlocity is not enabled ().
(ARM v22.2.27) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where wrong timezone region was displaying for users ().
Fixed an issue where the EZ-Commits report file displayed the file count but not the components count ().
Fixed an issue where clone build jobs were taking between 10 and 25 minutes, which is much longer than expected ().
Fixed an issue where CI job build failed to show changes in the org after deployment (
(ARM v22.2.26) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was having trouble while deploying LighteningMessageChannel components ().
Fixed an issue where Destructive Changes wasn't working as expected while performing an Entire Branch merge ().
Enhanced the ALM management feature by adding an option to sync Smart Commits ().
(ARM v22.2.25) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was getting a validation deployment error while performing release label deployment ().
Fixed an issue where Branching Baseline was taking longer than expected ().
Fixed an issue where using the AutoDraft functionality in EZ-Commit was resulting in a malformed exception in the UI ().
(ARM v22.2.23) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where validation jobs on Pull Requests weren't getting triggered (, , and ).
Fixed an issue where Salesforce components were showing under the Apex Test Success tab in the Deployment module, which is not expected behavior ().
Enhanced the Branching Baseline feature by allowing admin to define default baseline branches, making it easier for developers to choose the default branch for each project ().
(ARM v22.2.22) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where CI job deployments were failing with the error, Error 405 Only POST allowed ().
Fixed an issue where multiple deployment requests were being generated while performing Org Sync if the user selected all components instead of a few ().
Fixed an issue where Rollback API threw a 200 response but the Rollback immediately failed in the ARM UI ().
(ARM v22.2.21) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Static Code Anaysis was failing due to missing property tag in Apex PMD rules file, but the UI log wasn't displaying this error ().
Fixed an issue where when there was no results generated, the report displayed an error that there are zero metrics instead of displaying the results as zero in all the places when there is no change ().
Fixed an issue where user was unable to deploy a CI job with the RelationshipGraphDefinition components ().
(ARM v22.2.20) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where ARM was displaying incorrect installation settings and package version information in the deployment log while installing the package version from a CI job ().
Fixed an issue where user chose Exclude Metadata Type for a particular metadata type during a CI Job, but it was still deployed ().
Fixed an issue where user was unable to perform Destructive Commit with PermissionSetGroups metadata type ().
(ARM v22.2.19) This is a maintenance release. The following items were fixed and/or added:
Fixed a UI bug in Profile Manager where User Permissions differences are shown in the report but not in the UI ().
Enhanced the Release Label creation by increasing the range of retrievable commit history ().
Fixed an issue where user was unable to use Release Labels to perform Deployment, and it failed while trying to Create Artifact ().
(ARM v22.2.18) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was deploying single revision deployment with only report folder but sub-reports were also getting fetched, and the deployment was failing due to field dependency error ().
Fixed an issue where after deployment with single revision merge, user permission appears to be removed in target org but in the Salesforce target org the user permission is not removed, and an incorrect layout is displayed in UI ().
Fixed an issue where user performed a pre-validation commit and each process like file diff, validate deploy happened thrice as per the logs ().
(ARM v22.2.17) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was unable to download success/failure reports in Single Dataloader ().
Fixed an issue where when multiple CI Jobs are triggered, jobs are moved into the queue as expected, but new jobs are not starting automatically getting processed once the existing jobs is cleared from the CI Job results page ().
Fixed an issue where Dependency order defined in json file was being changed on every commit but it was not supposed to ().
(ARM v22.2.16) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where SFDX module creation log shows that deployment is successful but the module creation had failed ().
Fixed an issue with Backup from Org CI Jobs where PermissionSet User Permissions were being deleted ().
Fixed an issue where Org to Org Deployment for Profiles including Deploy Profile Access Settings for selected components only was not working as expected ().
(ARM v22.2.15) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the deployment was failing with the following error when user was deploying Permissionset with a user-permission Manage Public Documents: Permission Manage Public Documents depends on permission(s): Create Document, Delete Document, Edit Document, Read Document ().
Fixed an issue where CI jobs were failing intermittently with the following error: Getting access token failed from refresh tokenHTTP/1.1 400 Bad Request ().
Fixed an issue where Reports deployment validation failed in
(ARM v22.2.14) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user changed the permissions to list view from visible to all users to visible only for me while using the previous commit label, it is added under the Deleted tab ().
Fixed an issue where commit was running for longer and remained in-progress and validation check log is also in progress ().
Fixed an issue where commits with SFDX metadata structure are failing in metadata retrieval stage ().
(ARM v22.2.13) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Merge validation failed to process when there was a Flow metadata ().
Fixed an issue with user received 6 notifications for a failed CI Job instead of 1 ().
Fixed an issue where user was trying to register branches to AutoRABIT through GitHub, but was getting the following error: Lower Region ().
(ARM v22.2.12) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Admin was able to see the Teams field under ALM Integration but the same field was unavailable for sub-users ().
Fixed an issue where Environment provisioning processes were failing to update when user was trying to change the email deliverability access level from No access to All email ().
Fixed a build bug where CI Job Build was failing during package preparation step 5 failing while commiting DecisionMatrixDefinition and throwing an error ().
(ARM v22.2.11) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Deployment was failing with no changes in the package (internal ticket).
Fixed an issue where user was unable to create Environment Provisioning templates for multiple component types ().
Fixed an issue where user was creating an EZ-Commit, mapping the ALM Project (VersionOne) but received the following error: JSONObject["Assets"] is not a string ().
(ARM v22.2.10) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Provar jobs were failing due to incorrect files being copied from customer repository branch to Provar project directory ().
Fixed an issue where user triggered a CI Job but it deployed with many more components than expected ().
Fixed an issue where user was performing a single Merge with only two approval process, but while selecting SCA, process is auto rejected ().
(ARM v22.2.9) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with DataLoader Pro where jobs executed in the last 6 months were not showing in the database process table and in the Reports module ().
Fixed an issue with Deploy SFDX Source With ALM Mapping where CI job with ALM Mapping was not working as expected for Team which is not default ().
Fixed an issue where Profile Diff is working as expected for Selective Deployment, but not while using the same profile in the profile manager ().
(ARM v22.2.8) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where SFI components were not getting fetched in Commit and Deployment module ().
Fixed an issue where multiple metadata types where not able to retrieve ().
Fixed an issue where Commit Label is not Auto rejected when the validation criteria is not met ().
(ARM v22.2.7) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Flexi pages were not picked up in a CI Job even after the commit with same set of metadata was excluded by user ().
Fixed an issue where Abort function to stop Provar jobs was not working as expected ().
Fixed an issue where production backup CI Job was not picking all the changes, and when user modified the job configuration and retriggered the job, the application was throwing the following error java.lang.NullPointerException: null ().
(ARM v22.2.6) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was trying to migrate Products, Pricebooks, and its entries but the Deploy was failing for Pricebook and throwing the following error: INSUFFICIENT_ACCESS_ON_CROSS_REFERENCE_ENTITY: insufficient access rights on cross-reference id:-- ().
Fixed an issue with nCino where user was trying to create a custom feature template including product objects as well as product line but the deployment was failing with the following error: Required fields are missing: [LLC_BI_Product_Line_c] ().
(ARM v22.2.5) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was performing Prevalidation Commit but commits in the repository have different components than the ones shown in Diff before the commit ().
Fixed an issue with Install an Unlocked or Managed Package from a Version Control Branch where CI job getting an exception and the build status was showing as successful but the Scratch Org was not being created ().
Fixed an issue where CI Job shows that the ALM status has been updated successfully but on Azure ALM it is not updated ().
(ARM v22.2.4) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the user was trying to create an Extract process in DataLoader but after validating the query the application was throwing an error: not supported; requires @DynamoDBTyped or @DynamoDBTypeConverted ().
Fixed an issue with CI Jobs where External Credential metadata was not identified during Deployment ().
Fixed a UI bug where user was performing an org to org deployment using package.xml file and the components were successfully deployed and also verified on Salesforce target, but the status on ARM was still
(ARM v22.2.3) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with DX CI Job where user selected Do Not Include Skip Members but the respective mapper reports were not skipped (internal ticket).
Fixed an issue where the Deployment module page was loading very slowly and then throwing an error: Page Unresponsive ().
Fixed the following issues in CI and Reports modules (internal ticket):
(ARM v22.2.2) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where triggering a CI Job in Objects was resulting in an ambiguous error in the CI Job Build (, , ).
Fixed an issue where all CI Jobs were failing and throwing the error: Validation Checking failed Version Control Mappings not found for Repo: SA Repo and Branch: bugfix/Bugfix_PQT_Rel_Validation (, , ).
Fixed a UI bug on the CI Jobs page for Install an Unlocked or Managed Package from a Version Control Branch
(ARM v22.2.1) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where CI Job was successful but was including components from GIT revisions from old deleted branches ().
Fixed an issue where user was performing a production deployment using CI job for an object, but it failed with the following error: Cannot set sharingModel to ControlledByParent on a CustomObject without a MasterDetail relationship field ().
Fixed an issue where CI Job was getting an exception, Build status was showing as successful, but Scratch Org not getting created (
(ARM v22.2.0) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where skipped members were present in many components but only Report Metadata was failing during Deployment ().
Fixed an issue where CI Job was getting stuck in In Progress status but the log showed that the deployment was successful ().
Fixed an issue where GitHub login credentials were not working when user triggered a CI Job for the second time ().
Date of release: 20 March 2022 Article last updated: 23 October 2022
We have added the Squash and Merge feature in this release. Sometimes, when merging a long list of changes from a development branch into the master, it's helpful to squash those commits into one change for ease of review and declutter the repo's commit history. AutoRABIT offers an option to squash all commits in a merge request into one commit after the merge is approved and completed.
Packages
The users could previously build a new package (unlocked or managed) and update the package's version in Salesforce DX. With this release, you may now import packages and update the version of packages created outside of AutoRABIT.
Dev Hub management
With this update, users will see all of the packages in their dev hub in the record view. You may expand each package to show the package's versions in order and package data such as version name, version number, ancestor version, ancestor dependencies, etc.
The option to list the API-supported and unsupported API components is added to the CI job/deployment rollback. If such components may be deployed to the target environment but do not have API support to delete them, ARM will display them individually as unsupported API types. Take, for example, RecordType.
The RecordType component may be deployed to the target environment, but it cannot be removed; instead, we need to connect to the target Salesforce environment to deactivate the component.
Checkmarx has been updated to version 9.4.1. Earlier, Checkmarx used a username/password-based authentication method. Now, the user will be able to use token-based authentication with the Checkmarx upgrade.
The Export All Users feature allows the org admins to export a CSV file of all the users currently in their account. We now have added the following fields to the existing CSV file:
CreatedDate
CreatedByName
DeativatedDate
LastLoginDate
We have extended the support of having the pull request support in the CI Job for the Azure repository. This feature was previously available for Github cloud/Enterprise and Bitbucket cloud/Enterprise; however, we've added support for Azure cloud repositories (DX and non-DX repositories) with this release.
If you want to make sure one or more people approve every commit or merge, you can enforce this workflow by using merge/commit approvals. These approvals allow you to set the number of necessary approvals to approve every commit/ merge in a project.
The org admins' eligibility level has been enhanced with the ARM 22.1 version. If you're an administrator, you will have the privilege to approve self-merge even if the criteria to self-approve a merge is set to FALSE. This permission will be denied to all members of your team except the org admin. To put it another way, no criteria can restrict an org administrator from approving any EZ-commit/ EZ-Merge.
We have enhanced the scope for analysis of what CodeScan does by adding support for additional metadata and rules. For our ARM users who want to incorporate the SCA tool into their subscriptions, CodeScan would be their first choice as it now supports more robust integrations.
Below is the list of CodeScan supported metadata types:
The SFDX CLI has been upgraded to the latest stable 7.134 version.
Key characteristics to look for:
Single deployment request for constructive and destructive changes
Quick deploy and rollbacks work for both constructive and destructive changes
Package preparation has been improved.
The jquery-UI version has been upgraded to v1.13.0 to fix security issues. Upgrading to the most recent version of jquery makes our application more secure and potentially faster in script execution and loading.
Minor performance, bug fixes, and security improvements can also be observed in the ARM portal.
(ARM v22.1.48) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where wrong timezone region was displaying for users ().
Fixed an issue where the EZ-Commits report file displayed the file count but not the components count ().
Fixed an issue where clone build jobs were taking between 10 and 25 minutes, which is much longer than expected ().
Fixed an issue where CI job build failed to show changes in the org after deployment (
(ARM v22.1.46) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where validation jobs on Pull Requests weren't getting triggered (, , and ).
Fixed an issue where Salesforce components were showing under the Apex Test Success tab in the Deployment module, which is not expected behavior ().
Enhanced the Branching Baseline feature by allowing admin to define default baseline branches, making it easier for developers to choose the default branch for each project ().
(ARM v22.1.38) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Provar jobs were failing due to incorrect files being copied from customer repository branch to Provar project directory ().
Fixed an issue where user triggered a CI Job but it deployed with many more components than expected ().
Fixed an issue where user was performing a single Merge with only two approval process, but while selecting SCA, process is auto rejected ().
(ARM v22.1.37) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where SFI components were not getting fetched in Commit and Deployment module ().
Fixed an issue where multiple metadata types where not able to retrieve ().
Fixed an issue where Commit Label is not Auto rejected when the validation criteria is not met ().
(ARM v22.1.36) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Flexi pages were not picked up in a CI Job even after the commit with same set of metadata was excluded by user ().
Fixed an issue where Abort function to stop Provar jobs was not working as expected ().
Fixed an issue where production backup CI Job was not picking all the changes, and when user modified the job configuration and retriggered the job, the application was throwing the following error java.lang.NullPointerException: null ().
(ARM v22.1.35) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was trying to migrate Products, Pricebooks, and its entries but the Deploy was failing for Pricebook and throwing the following error: INSUFFICIENT_ACCESS_ON_CROSS_REFERENCE_ENTITY: insufficient access rights on cross-reference id:-- ().
Fixed an issue with nCino where user was trying to create a custom feature template including product objects as well as product line but the deployment was failing with the following error: Required fields are missing: [LLC_BI_Product_Line_c] ().
(ARM v22.1.34) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was performing Prevalidation Commit but commits in the repository have different components than the ones shown in Diff before the commit ().
Fixed an issue with Install an Unlocked or Managed Package from a Version Control Branch where CI job getting an exception and the build status was showing as successful but the Scratch Org was not being created ().
Fixed an issue where CI Job shows that the ALM status has been updated successfully but on Azure ALM it is not updated ().
(ARM v22.1.33) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the user was trying to create an Extract process in DataLoader but after validating the query the application was throwing an error: not supported; requires @DynamoDBTyped or @DynamoDBTypeConverted ().
Fixed an issue with CI Jobs where External Credential metadata was not identified during Deployment ().
Fixed a UI bug where user was performing an org to org deployment using package.xml file and the components were successfully deployed and also verified on Salesforce target, but the status on ARM was still
(ARM v22.1.32) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with DX CI Job where user selected Do Not Include Skip Members but the respective mapper reports were not skipped (internal ticket).
Fixed an issue where the Deployment module page was loading very slowly and then thrwing an error: Page Unresponsive ().
Fixed the following issues in CI and Reports modules (internal ticket):
(ARM v22.1.31) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where triggering a CI Job in Objects was resulting in an ambiguous error in the CI Job Build (, , ).
Fixed an issue where all CI Jobs were failing and throwing the error: Validation Checking failed Version Control Mappings not found for Repo: SA Repo and Branch: bugfix/Bugfix_PQT_Rel_Validation (, , ).
Fixed a UI bug on the CI Jobs page for Install an Unlocked or Managed Package from a Version Control Branch
(ARM v22.1.30) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where CI Job was successful but was including components from GIT revisions from old deleted branches ().
Fixed an issue where user was performing a production deployment using CI job for an object, but it failed with the following error: Cannot set sharingModel to ControlledByParent on a CustomObject without a MasterDetail relationship field ().
Fixed an issue where CI Job was getting an exception, Build status was showing as successful, but Scratch Org not getting created (
(ARM v22.1.29) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where skipped members were present in many components but only Report Metadata was failing during Deployment ().
Fixed an issue where CI Job was getting stuck in In Progress status but the log showed that the deployment was successful ().
Fixed an issue where GitHub login credentials were not working when user triggered a CI Job for the second time ().
(ARM v22.1.28) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with nCino where user was getting errors with Standard Screen and UI Templates ().
Fixed an issue where user noticed discrepancy in the Conflict Resolution Log ().
(ARM v22.1.27) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where components were successfully deployed, but deployment status was still showing In-Progress in ARM (, ).
Fixed an issue where CI Jobs were getting stuck and throwing the following error: Too many open files (, ).
Fixed an issue where email notification wasn't sent for some of the CI Jobs ().
(ARM v22.1.26) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Provar test job was throwing an error while in queue ().
Fixed an issue where scheduled auto-sync of external commits was not working (internal ticket).
Fixed an issue with the New EZ-Commit screen where ALM Types are changing to old ALM type names after resaving details on the ALM Management screen (internal ticket).
(ARM v22.1.25) This is a maintenance release. The following items were fixed and/or added:
Fixed multiple issues with CodeScan<>ARM Integration (internal ticket).
Fixed an issue where CI Jobs and Deployments were both failing for Reports and Dashboards because the folder could not be found (internal ticket).
Fixed an issue with New Commit screen where the Select All checkbox was getting unselected when navigating from the DELETED tab to the ADDED/MODIFIED METADATA COMPONENTS tab and back to the DELETED tab (internal ticket).
(ARM v22.1.24) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was selecting a single package to import, but all available package versions were being imported ().
Fixed an issue with Profile Manager where user was comparing a profile but the deployment was not starting ().
Fixed an issue where deploying components with profiles was not working as expected and throws the following error: Duplicate layoutAssignment:PersonAccount (PersonAccount.Person_Prospect) ().
(ARM v22.1.23) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where user was performing a new deployment but getting an error when using the Compare Orgs & Deploy button (, , , ).
Fixed an issue where the CI job was not working as expected and throws the following error: java.lang.NullPointerException: null ().
Fixed an issue where few fields were not being analyzed in CodeScan SFDX. User was selecting Custom Fields, Apex Classes, and Record Types in E-Z Commit, but Static Code Analysis was only Apex Classes ().
(ARM v22.1.22) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where Unpackaged Packages Directory folder was being created in the Deployment Promotion zip package when deploying Static Resource Metadata type using Single revision DX Deployment (internal ticket).
Fixed an issue where after upgrading the AR instance, deployment jobs kept removing the custom metadata access on the Permission Sets ().
Fixed an issue where Org difference jobs were running for more than 24 hours ().
(ARM v22.1.21) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the CI job build was getting stuck in In-progress status ().
Fixed an issue where RunSpecifiedTest level execution was failing with Test classes dependency errors ().
Fixed an issue where DX CI Job build failed if document metaxml change commit revision includes in the build [Including Email templates and Static Resources types] (internal ticket).
(ARM v22.1.20) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue with the Profile Manager where the user were unable to select the default app permission during the profile deployment ().
Fixed an issue where the merge revisions were missing from the CI jobs ().
Fixed an issue where the users were unable to commit Vlocity card from one org to another org in ARM ().
Fixed an issue where for both CI Jobs and Deloyments (Non-DX and DX), the deployment was getting failed with the below error although the
(ARM v22.1.19) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the package URL was not visible for the SFDX modules successfully configured in ARM (internal ticket).
Fixed an issue where our internal team members got the undefined error while creating a new scratch org and selecting the module (internal ticket).
Fixed an issue where after triggering the CI job, the File Changes and Check-ins results mismatched ().
Fixed an issue where the package created to deploy ExperienceBundle misses some of the folder and metadata files contained in it (
(ARM v22.1.18) This is a maintenance release. The following items were fixed and/or added:
Upgraded the Spring and AWS libraries on ARM for addressing the Spring vulnerability ().
Fixed an issue where the users were unable to login to ARM via SSO (internal ticket).
Fixed an issue where the ARM is not able to fetch any component using the release label ().
Fixed an issue where the baselining of branches has wiped out the records types for many records, and the users were forced to do manual changes to the Record types ().
(ARM v22.1.17) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where when user triggers a code coverage run in the production environment, the action takes more time than expected. Also, the total time taken for the task completion is shown inaccurate in the log report (, ).
Fixed an issue where the CI job was not working as expected and throws the following error: java.lang.OutOfMemoryError: Java heap space (, , , ).
Fixed an issue where the Rollback settings were not getting saved in the My Account page (internal ticket).
(ARM v22.1.16) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the Execute Anonymous Apex metadata is not working as expected when configured as Environment Provisioning template ().
Fixed a bug where our internal team were able to use the perform the prevalidation commit and direct commit without giving the prevalidation commit label name and without commit comment, which are mandatory fields (internal ticket).
Fixed an issue where the ALM workitems are not retrieved in CI job through merge (internal ticket).
Fixed a bug where our internal team were able to save the
(ARM v22.1.15) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users failed to enable the pull request support for their version control repositories ().
Fixed an issue where the re-use previously validated commit label takes more time to load ().
Fixed an issue where the constructive changes are picked in the CI build, although no constructive changes are in-between From and To revisions (internal ticket).
(ARM v22.1.14) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the deployment via CI job picked unnecessary components for deletion ().
Fixed the issue where the user when trying to delete a component in Community metadata type, deletes the whole Community rather than its components ().
Fixed an issue where DevHub registration in ARM was failing ().
Fixed a bug where our internal team members were not able to view the Salesforce Org URLs in the
(ARM v22.1.13) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the Spread Template in the nCino module was not working as expected ().
Fixed an issue where the user was getting "field integrity exception: unknown (CreatedByID(0051X00000BbMIR) is not in org" for the records that were available in the destination org.
Fixed the issue where the Disable Workflow template in the Environment Provisioning module was not working as expected ().
(ARM v22.1.12) This is a maintenance release. The following items were fixed and/or added:
Fixed a minor bug where the child members checkboxes remained checked even when the parent metadata type was unchecked (internal ticket).
Fixed an issue where CI job build ToRevision number was mismatched in the CI Job Results and the CI Build Info page ().
Fixed an issue where the request parameters were empty in the nCino Feature Commit History screen ().
(ARM v22.1.11) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the branching baseline feature for profile was not working as expected (, ).
Fixed an issue where the Dataloader Pro jobs were failing with no error message (, ).
Fixed the issue where the Dataloader Pro jobs was not working as expected ().
Fixed an issue where the users while performing org to org migration of nCino record based configurations, all the related items are getting carried over except the
(ARM v22.1.10) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the picklist values failed to retrieve while preparing the CI job build (, ).
Fixed the issue for the SFDX jobs where the user permissions were picked up for the deployment even if the user opts for "Remove User Permissions" ().
Fixed an issue where new tags gets automatically added for the sharing rules after the ARM 22.1 upgrade ()
(ARM v22.1.9) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the branching baseline feature for profile was not working as expected (, ).
Fixed an issue where the Dataloader Pro jobs were failing with no error message (, ).
Fixed the issue where the Dataloader Pro jobs was not working as expected ().
Fixed an issue where the users while performing org to org migration of nCino record based configurations, all the related items are getting carried over except the
(ARM v22.1.8) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where performing a validation merge on the Azure repository branch creates the merge label and an external commit label with the same name and the same revision number ().
Fixed an issue where the package deployment job was not triggered automatically once the validation was successful (, ).
Fixed the issue where the DiscoveryAIModel metadata type was unsupported, which caused the CI jobs to fail ().
(ARM v22.1.7) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where performing a validation merge on the Azure repository branch creates the merge label and an external commit label with the same name and the same revision number ().
Fixed an issue where the package deployment job was not triggered automatically once the validation was successful (, ).
Fixed the issue where the DiscoveryAIModel metadata type was unsupported, which caused the CI jobs to fail ().
(ARM v22.1.6) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where performing a validation merge on the Azure repository branch creates the merge label and an external commit label with the same name and the same revision number ().
Fixed an issue where the package deployment job was not triggered automatically once the validation was successful (, ).
Fixed the issue where the DiscoveryAIModel metadata type was unsupported, which caused the CI jobs to fail ().
(ARM v22.1.5) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the picklist values failed to retrieve while preparing the CI job build (, ).
Fixed the issue for the SFDX jobs where the user permissions were picked up for the deployment even if the user opts for "Remove User Permissions" ().
Fixed an issue where new tags gets automatically added for the sharing rules after the ARM 22.1 upgrade ()
(ARM v22.1.4) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where performing a validation merge on the Azure repository branch creates the merge label and an external commit label with the same name and the same revision number ().
Fixed an issue where the package deployment job was not triggered automatically once the validation was successful (, ).
Fixed the issue where the DiscoveryAIModel metadata type was unsupported, which caused the CI jobs to fail ().
(ARM v22.1.3) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue for the Chrome browser where the ApexPMD ruleset was not uploading incorrectly (under the Plugins section). For other browsers, it was working as expected ().
Fixed the issue with the merge where the changes present in the source branches were not picked up, and therefore latest changes did not reflect on the destination branch (, , , , , , ).
Fixed an issue where the Salesforce-DX deployment and rollback mismatches ()
(ARM v22.1.2) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the Abort option was showing for completed CI jobs (, , , ).
Fixed the issue where the SFDX deployment is getting failed even though the user uploaded the correct file.
Fixed a bug where the static code analysis (SCA) status shows as in progress for a failed execution.
(ARM v22.1.1) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the skip members feature was not working for the Version Control, Deployments, and CI Job module ().
Fixed an issue where the users were receiving layout permissions errors when using Prevalidation Commit.
The SCA option where not working when users use the EZ commit/ Merge operation. The issue has now been fixed ().
Fixed an issue where the users were unable to generate the deployment report and received validations errors for EZ-Merge operation (
(ARM v22.1.0) This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to switch the tab from the Test Coverage to the Class Coverage in the Apex test results page ().
Fixed an issue where the users were unable to save Salesforce settings in the My Account screen ().
Fixed an issue where the users were not able to save the exclude metadata types in the My Account page ().
Date of Release: 21 November 2021
On this page:
Pull request is a feature that allows you to review code and provide feedback before merging it into the master branch. Previously, we had GitHub and Bitbucket support. We've included support for Azure DevOps in this release. ()
During Ez-Commit and new Pull Requests, you can now create a Pull Request in Azure with the assignee.
You should be able to choose the repository, the base branch, and another branch to compare during the creation of a pull request.
A link to the Azure DevOps application will be included in each pull request created in AutoRABIT. The pull request can also be approved directly from the AutoRABIT application.
AutoRABIT had an audit report feature that gave you a comprehensive view of your business operations by fostering a collaborative operational audit environment. In this release, we've made some enhancements and added a button called "Audit Log Report" on the CI job page, which allows you to generate a report in PDF format for a specific period.
We've improved the CI Job Result screen by giving users the option to generate an Audit log report for internal auditing purposes. This is a report of CI jobs deployments and the commits associated with each deployment, including commit details such as Author, Commit Time Stamp, and so on.
We changed the timestamp in the Audit log report from 12-Hour format to 24-hour UTC format by default to comply with ISO 8601 notation, which is a commonly recommended format for representing date and time.
Added support for custom “keynames”, “Salesforce Org type“ and “AR SF Org type” in the Audit trail report wherever Salesforce org name details are applicable.
Salesforce CLI is a command-line interface for working with your Salesforce org that makes development and build automation easier. It can be used to create and manage organizations, synchronize sources to and from organizations, create and install packages, and more. In this version of ARM, Salesforce-DX CLI is upgraded to the latest 7.129 version.
In order to keep our product up to date with the most recent Salesforce updates. AutoRABIT now supports the most recent API version 53 in this release. Now our Salesforce developers will begin using API 53 on their Sandboxes for development. The most recent API version is intended for customizing the metadata model and developing tools to manage it.
We've been working hard over the last few weeks to improve our platform's stability, performance, query optimizations, code smells, security vulnerabilities, and reliability. With this release, you will notice significant improvements in our application, such as faster page load times, improved performance, and faster search functionality, among other things.
JQuery Upgrade: JQuery was updated from version 1.8.3 to version 3.6. Upgrading to the most recent version of jQuery makes our application more secure, as well as potentially faster in terms of script execution and loading.
Across the CI Job module, "Load More" buttons have been replaced with "Previous" and "Next" buttons. This new feature will allow our users to display 25, 50, 75, or 100 records on a single page and navigate between pages using the Previous and Next buttons. This feature was previously limited to the Version Control module, but it has recently been expanded to include the CI Job module as well.
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to deploy release labels ().
Fixed the following SSO errors:
Unable to use SSO for AutoRABIT authentication ().
Unable to log in via SSO in the chrome and the firefox browser.
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the skip members feature was not working for the Version Control, Deployments, and CI Job module ().
Fixed an issue where the users were receiving layout permissions errors when using Prevalidation Commit.
The SCA option was not working when users use the EZ-Commit/merge operation. The issue has now been fixed ().
Fixed an issue where the users were unable to generate the deployment report and received validations errors for the EZ-Merge operation (
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to switch the tab from the Test Coverage to the Class Coverage on the Apex test results page ().
Fixed an issue where the users were unable to save Salesforce settings in the My Account screen ().
Fixed an issue where the users were not able to save the excluded metadata types on the My Account page ().
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to see the commits ID in the release label ().
Fixed an issue where the users were unable to view their permission details in the Users and Roles tab ().
Fixed an issue where users were not able to delete the changes made in the source branch using AutoRABIT ().
Fixed an issue where the branching baseline for a profile and branch to branch merge was not working ().
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the "Group By" functionality was not fetching the correct CI job results ().
Fixed an issue where the deployment status of CI Job has failed in logs but the process is still in-progress stage ().
Fixed an issue where the users were unable to use the SCA for LWC components unlike apex class, triggers, and aura bundle ().
When a pull request is in progress, the job is not triggered for additional changes committed before the work is completed. This is now fixed (
Limitations identified in this release:RestrictionRule metadata type is not supported for the SFDX deployment.
This is a maintenance release. The following items were fixed and/or added:
Fixed the below UI issues:
The "Commit" button was not available for the merge request label job. ().
For the entire deployment, the "To Revision" radio button was disabled, and users were unable to select revisions from the list provided.
Although the field
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the commit approvers were not receiving email notifications due to the commit prevalidation being stuck in-progress. ().
Fixed an issue where the users were not able to select the master branch as their parent branch while registering existing branches from the repository in AutoRABIT ().
Fixed an issue where the users were receiving an error message saying "Please select the date" even though the date was selected when registering the SVN Branch.
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to close the diff report file in the Org Synchronization History screen ().
Fixed an issue for the SFDX CI Jobs where the metadata types were not excluded without the baseline revision.
Fixed an issue where the release label deployment is adding unselected components in the deployment package ().
Fixed a bug where the users were unable to delete unwanted Dataloader Pro jobs from AutoRABIT (
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to generate the code coverage log report from the Report Module ().
Fixed an issue where the users were unable to upload the package.xml file to resolve the merge conflict ().
Fixed an issue where the users were able to commit the changes although the validation got failed. ().
Fixed an issue where the user was unable to perform the
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the users were unable to close the diff report file in the Org Synchronization History screen ().
Fixed an issue for the SFDX CI Jobs where the metadata types were not excluded without the baseline revision.
Fixed an issue where the release label deployment is adding unselected components in the deployment package ().
Fixed a bug where the users were unable to delete unwanted Dataloader Pro jobs from AutoRABIT (
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the commit approvers were not receiving email notifications due to the commit prevalidation being stuck in-progress. ().
Fixed an issue where the users were not able to select the master branch as their parent branch while registering existing branches from the repository in AutoRABIT ().
Fixed an issue where the users were receiving an error message saying "Please select the date" even though the date was selected when registering the SVN Branch.
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the CI Job builds are getting stuck and no log information was displayed (, , ).
Fixed an issue where the conflicted files downloaded were incorrect during the merge process ().
Fixed an issue where the aura components were not getting retrieved while carrying out the branching baseline operation ().
Fixed a bug that restricted users from entering the credential name on the
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the commit approvers were not receiving email notifications due to the commit prevalidation being stuck in-progress. ().
Fixed an issue where the users were not able to select the master branch as the parent branch while registering existing branches from the repository in AutoRABIT ().
Fixed an issue where the users were receiving an error message saying "Please select the date" even though the date was selected when registering the SVN Branch.
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the user was unable to close the diff report file in the Org Synchronization History screen ().
Fixed an issue for the SFDX CI Jobs where the metadata types were not excluded without the baseline revision.
Fixed an issue where the release label deployment is adding unselected components in the deployment package ().
Fixed a bug where the users were unable to delete unwanted Dataloader Pro jobs from AutoRABIT (
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where when the user is trying to perform pre-validation commit for report metadata, it is getting added under emailservice functions in diff report (, , , ).
Fixed an issue where the case entitlementProcess-meta.xml files were not picked up during deployment (, ).
Fixed an issue where the deployment report is getting failed while doing prevalidation merge with the report folder.
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where when pre- and post-destructive changes were added to the process, it caused the deployment to fail (, ).
Fixed a bug where for fewer CI jobs, the Older button was disabled. This has now been enabled and is working as expected ().
Fixed an issue in the SFDX module that prevented commits from being executed using scratch org ().
This is a maintenance release. The following items were fixed and/or added:
Fixed nCino objects deployment issue during using nCino CI Jobs ().
Fixed an issue where the custom object is being listed during CI Job operation but not during Ez-commit ().
Fixed Ez-merge issue which shows different results in AutoRABIT when compared to the production environment ().
Fixed an issue where the users were unable to extract deleted records and threw "Malformed Query Fault"
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the quick deployment feature was not working as expected and was throwing "Invalid Login" error ().
Fixed a bug where the merge request validation was getting failed ().
Fixed an issue where the commit search was not working as expected in the Version Control module ().
Fixed an issue where the users were facing invalid credentials issue while updating the src as metadata folder path in-branch settings
Date of Release: 29 August 2021
On this page:
In keeping with our dedication to continual improvement, the August-21 (AR 21.5) release delivers a plethora of exciting upgrades and improvements to our AutoRABIT application.
UI/UX Improvements: Focused on application performance and user experience. Try it out for yourself and let us know how to feel:
Page Navigation: When working with several records, breaking data into multiple pages is always a good idea. You can now view 25, 50, 75, or 100 records on a single page, and use the Previous and Next buttons to switch to the previous or next page. This feature is now only available in the Version Control module, but it will be expanded to other modules in future releases.
Never miss a required field: You will be prompted to fill in all the required fields before you proceed. Follow the UI highlights to minimize rework.
This is a maintenance release. The following items were fixed and/or added:
Fixed deployment issues
Fixed an issue where no metadata was found while validating the components from the master branch to the production environment (, , , , , )
Fixed revision based deployment issue ()
This is a maintenance release. The following items were fixed and/or added:
Fixed an issue where the user couldn't delete a job with special characters in its name ()
Fixed SFDX deployment and rollback mismatches issue ().
Fixed a bug where when attempting to commit the deletion of 19 profiles, a Diff Report listing of 20 profiles was generated. ().
Fixed code coverage report discrepancy issue ().
This is a maintenance release. The following items were fixed and/or added:
The deleted sharing rules were not showing up in the EZ-Commit Deleted tab, which was fixed ()
Fixed a bug where the older commits were not accessible for merge ().
Fixed an issue where when deploying a new custom object, an error "Profile Search Layout: - System Administrator - not appropriate for object XXXXXX" was thrown ().
Fixed a merge conflict issue(
Yes
Yes
GenAiPlannerBundle (API 64 and Above)
Yes
Yes
Bot
Yes
Yes
BotVersion
Yes
Yes
Custom Apex invoked by agents (ApexClass)
Yes
Yes
Flows used by agents (Flow)
Yes
Yes
Permission Sets assigned to the Agent User
Yes
No
CustomSite
Yes
Yes
Network
Yes
Yes
DigitalExperienceBundle
Yes
Yes
EmbeddedServiceConfig
Yes
Yes
MessagingChannel
Yes
Yes
Flow (specifically the Omnichannel flow for routing)
Yes
Yes
Queue
Yes
Yes
QueueRoutingConfig
Yes
Yes
Yes
Yes
DuplicateRule
Yes
Yes
AnalyticsVisualization
Yes
No
SrvcMgmtObjCollabAppCnfg
Yes
No
DgtAssetMgmtProvider
Yes
No
DgtAssetMgmtPrvdLghtCpnt
Yes
No
Support for both constructive and destructive changes across DX and non-DX repositories.
Validated Merge, Release Label, and Branching Baseline flows for all Data Cloud metadata types. Learn more https://knowledgebase.autorabit.com/product-guides/arm/salesforce-extensions/arm-for-salesforce-data-cloud
ManagedContentType Destructive Commit Failure Destructive commits for MANAGEDCONTENTTYPE metadata were failing due to unrecognized metadata classification. This metadata type has now been added to the SfdxMetadataFolder, ensuring it is properly recognized and deletable. (Support Case: 154888)
CI Job Status Stuck in Progress After Completion Some CI Jobs continued showing as “In Progress” even after build and validation completion, blocking new runs on the same target org. A blocking wait mechanism was implemented to continuously check CIJobInfo until the deploy status updates to “Completed.” (Support Case: 154818)
Scratch Org Creation – Salesforce Org Validation Resolved an issue where users received a “Salesforce Org Doesn’t Exist” error while attempting to retrieve data for Scratch Org creation. The system now correctly validates the selected Salesforce org and proceeds with successful data retrieval.
Webhook API Token Status Corrected an issue where the webhook API token’s last status always showed as "Never Accessed," even after being used in CI Job triggers. The last access status now updates correctly when tokens are used. (Support Case: 153909)
Release Label – Deployment with Apex Meta Files: Fixed an issue where Release Label deployments failed when changes existed only in the Apex -meta.xml file and not in the corresponding .cls file. Such changes are now correctly included in the manifest.
Communication: For existing Release Labels, customers must re-run artifact preparation to apply this fix. New Release Labels will work as expected.
EZ Commit – Pre-Validation Error: Addressed a parsing error ("XML document structures must start and end within the same entity") that caused pre-validation EZ-Commits to fail. A new file copy library has been implemented to resolve this in EZ-Commit (Validate Deploy), CI Jobs, and Deployments.
Salesforce ALM Integration – Status Updates: Fixed an issue where ALM work items failed to update if the status field’s API name differed from the picklist label. Updates now correctly use the API name for mapping.
CI Jobs – Missing Debug Information in Failed Builds: Fixed an issue where failed builds did not display detailed error logs. The UI now shows schema validation errors with file and line details, helping users quickly identify and resolve issues.
File Upload Error in EZ-Merge Conflict Resolution: Customers reported being unable to re-upload modified files after downloading the conflict resolution zip in EZ-Merge. The issue was caused by restrictive file size limits. Fix: Increased the maximum supported file upload size to 100MB, ensuring smoother conflict resolution workflows.
CI Job Stuck Issue in Abort Functionality: Fixed a corner case where a CI job could get stuck, preventing new builds from being triggered. The abort functionality has been refined to avoid such blocking scenarios.
Deployment Trigger Date Accuracy: The deployment date recorded in the Reports module and Audit Tab now reflects the exact trigger time instead of relying on package creation time. This ensures more accurate tracking for all new deployments.
SSO Configuration – Empty Metadata File: Corrected an issue where downloading the AutoRABIT SSO Metadata XML returned an empty file. The file now downloads with the correct default content.
Static resources misidentified during destructive EZ-Commit: Deleting one static resource while another with a similar name remained caused the diff view to include both files. Selection logic has been refined so only the intended destructive file is picked up, even when naming conventions overlap.
Release Label Creation – Git SSH Response Handling: Addressed an issue where release label creation failed due to invalid credentials. The system now properly handles Git responses when fetching branches via SSH, ensuring artifact preparation continues smoothly.
VS Code Plugin – File Diff Undefined Error Fixed an undefined error in EZ Commit via VS Code when accessing file diffs post-commit. The file diff generation model is now available.
Destructive Changes – Entitlement Process Commit Fail Addressed commit failures during the Entitlement Process, destructive changes by updating the logic for DX Repositories.
Deployment – Missing Permissions in Profile Deployments Corrected permission deployment for profiles with “Ignore Missing Visibility” enabled. This included handling for PushTopic permissions.
Audit Reports – Triggered Date Incorrect Fixed the mismatch in deployment-triggered date display under the Audit tab.
CI Jobs – Abort Doesn’t Terminate Background Process Improved CI job abort handling to ensure background processes are completely stopped. Now, aborted jobs no longer get stuck, and subsequent jobs queue and execute as expected.
DataStreamDataStreamDefinitionDeployment Reports Display Accurate Results for All Years Reports for years like 2023 and 2024 were previously showing incorrect data due to a mismatch in attribute formatting. We’ve added compatibility for both older and newer report formats, ensuring accurate data display on the dashboard.
ExtlClntAppMobileConfigurablePoliciesExtlClntAppNotificationSettings
ExtlClntAppPushSettings
ExtlClntAppPushConfigurablePolicies
Also validated existing metadata types (e.g., Objects, Fields, Profiles, Permission Sets) with API 64, and confirmed that they work as expected.
Impacted Module: Deployment (Vlocity SF Org-to-Org)
Impacted Module: EZ-Merge with Validate Deploy
Enhancement: Accurate Filtering in Org Sync The 'Exists in Source Only' filter in Org Sync now accurately reflects the actual number of differing metadata groups. With this fix, both the group count and displayed results are consistent and reliable. Impacted Modules: Org Sync.
Immediate Visibility of 'Skip Org Mapping' Option The 'Skip Org Mapping' permission is now immediately visible in the Roles tab after enabling 'Skip Mappings' on a user’s profile. Previously, a page refresh was required for the option to appear. This enhancement ensures the setting is saved and reflected instantly without additional user actions. Impacted Modules: Admin.
Whitespace Differences in File Diff View The File Diff tab now displays whitespace-only changes when comparing Apex Class files. Previously undetected space differences are now identified and shown, ensuring accurate comparison between source and destination files. Impacted Modules: Org Sync and Deployments.
Vlocity Commit Label Filtering Commit labels associated with Vlocity metadata can now be filtered correctly using the commit label name in the merge screen. Previously created labels without commit type are also supported following a back-end migration fix. Impacted Modules: VC → Change labels → Commit labels.
Support for Initial Commit in Revision Range Deployment Salesforce metadata changes from the initial commit are now included in the retrieve metadata screen when selected as the "From Revision" in a revision range deployment. This ensures changes from both the initial and target revisions are accurately reflected and deployed. Impacted Modules: Custom Deployments - Revision range, single revision.
LWC API Check Support in CodeScan Analysis
Files with .js-meta.xml suffixes are now included in the CodeScan analysis, enabling proper API checks on Lightning Web Components (LWC) from ARM. This ensures more accurate validation during the scan process. Impacted Modules: ARM CodeScan integration.
Accurate File Name Display in Review Artifact The Review Artifact UI now correctly updates the file name when switching files, ensuring clarity while reviewing changes. Impacted Modules: EZ Commit -> Review-Artifact -> Edit In IDE -> File Names in editor view.
Commit Revisions Sorted by Committed Timestamp Commit revisions in the Commit module are now displayed based on the committed timestamp, aligning with GitHub's behavior. Previously, revisions were shown using the author timestamp, causing confusion. The backend logic has been updated to ensure commits are sorted and displayed consistently. Impacted Modules: New Deployment, New CI Jobs, New Merge, VC Repositories, Release Labels.
Support for Special Characters and Extended Name Lengths in User Profiles User profile fields now support special characters in first and last names. Additionally, the character limits have been extended—first names now allow 3 to 40 characters, and last names allow 1 to 80 characters. Impacted Modules: Admin, My Profile.
Support for Priority 4 Rules in Apex PMD Static Code Analysis Static Code Analysis now includes Priority 4 rule violations in Apex PMD reports. The minimum PMD priority has been updated from Medium (3) to Low (5), allowing visibility into lower-priority issues without affecting CI Job validations configured to fail only on higher priority errors. Impacted Modules: All static code analysis running with Apex PMD.
Optimized Loading of Standard Value Sets in Commit Improved performance and visibility of Standard Value Sets in the EZ-Commit module by minimizing repeated Salesforce API calls. The system now retrieves enabled services during org registration and stores the cloud org type in the database. For existing orgs, the cloud type is updated during retrieval and used for subsequent requests, significantly reducing load times and ensuring correct metadata visibility—especially for Financial Services Cloud orgs. Impacted Modules: EZ-Commit, Commit Templates, Branching Baseline, Deployments, CI Jobs.
Provar Plugin Name Edit Handling Editing the Provar name in the Admin module no longer triggers an invalid notification pop-up when a key file is already uploaded. A response check ensures smoother and more accurate user feedback. Impacted Modules: My Account plugins (Provar).
ARM ensures stable conflict resolution for profiles by preventing errors caused by commented code on a new line. Users can click on files in the resolve duplicate screen without encountering IndexOutOfBounds exceptions. Impacted Module: EZ-Merge duplicates resolution scenario.
Improved Security for API Tokens
API tokens are now fully hidden after their initial creation and display, ensuring they are no longer exposed in network requests. This enhances security by preventing unauthorized access through browser developer tools. Impacted Module: API Token creation.
Correct Project Mapping for CodeScan in CI Jobs
ARM ensures that CodeScan projects are correctly linked to the scanned Salesforce org in CI jobs. The mapping issue causing a null project name has been resolved, ensuring accurate project creation and association. Impacted Module: CI Job Build Logs.
Improved Commit Label Deployment for Permission Sets
ARM ensures consistent and accurate deployment of permission sets during Commit Label deployments. The Ignore Missing Visibility setting behaves as expected, and redeployments correctly generate a new deployment package instead of reusing the initial one. Impacted Module: Commit Label.
EZ-Merge Report Accuracy: The EZ-Merge report CSV now includes missing details, such as dates and L1/L2 review statuses, improving tracking and transparency. Impacted Modules: Weekly Report, EZ-Merge report.
CI Job Stability: Resolved issues causing CI job failures and deployment errors for AccelQ tests. Test results now display the correct status and test counts in the Test Summary Report. Impacted Modules: AccelQ CI Jobs.
Deployment Rules Visibility: Deployment rules are now consistently displayed in the Deployment Submit popup window across all deployment types. Impacted Modules: Custom Deployments.
Lightning Email Templates Retrieval: Fixed an issue where Lightning Email Templates were not retrievable across multiple ARM modules, including EZ-Commit, EZ-Merge, Release Label Artifact Preparation, Org-to-Org Deployment, Org Sync, Auto-draft, Commit Template, and Branching Baseline. Impacted Modules: EZ-Commit.
Review Artifact Enhancement: The "Review Artifact" option now correctly displays the package.xml and its corresponding data for commits, deployments, and merges. Additionally, SearchCustomization now functions as expected for both SFDX and non-DX environments, supporting merging, CI jobs, and deployments. Impacted Modules: EZ-Commit, Merge.
SFDX Package Naming Support: Special characters such as @ and . can now be used in SFDX package version names, resolving previous naming limitations. Impacted Modules: SFDX, Unlocked Packages.
RelatedContent
EmailDefault
MiniLayout
PlatformActionList
My Account (Save Global Settings for Admins)
Static Code Analysis
Org Synchronization History
Global Settings Migration for Manageable State Global settings for manageable state, previously configured in the "My Account → Admin" section, are now automatically retrieved and applied across relevant modules, ensuring consistency across the platform.
Database Support for Manageable State The database schema has been updated to support the manageable-state dropdown in CI Job, EZ-Commit, and Branching Baseline modules. This ensures that user selections are properly saved and retrieved, maintaining data integrity across sessions.
Revamped Static Code Analysis View We’ve revamped our static code analysis UI to enhance the user experience. Now, errors are conveniently displayed under selected files, streamlining issue identification and resolution across various tools.
Streamlined EZ-Commit Editing This release significantly enhanced the EZ-Commit workflow to empower developers. The introduction of an integrated Compare Changes option in the Review Artifact screen allows for seamless viewing, editing, and visualizing of Salesforce metadata changes in a single, user-friendly interface. Developers can now effortlessly navigate and understand their code edits with color-coded differences, eliminating the need to toggle between multiple screens. This streamlined process enhances the user experience and addresses a crucial blocker in the journey towards CI/CD, providing a more efficient and intuitive path for developers.
Enhanced SCA Label Scheduling In this release, users can now enjoy enhanced control over SCA label scheduling with the introduction of the ability to edit/update schedules. This feature provides greater flexibility, allowing users to modify scheduled times for SCA labels, contributing to a more seamless and user-friendly experience in managing job schedules.
New Email Templates Implementation In this release, a significant enhancement has been made by implementing new email templates that align with current visualization standards. This update reflects our commitment to maintaining high standards in user interface design and enhancing overall user engagement.
Upgrade of third-party libraries
Salesforce integration credentials (Client ID & Secret) are now encrypted for improved security. Existing tokens are also migrated to the new format. This enhances protection against unauthorized access.
Log-leveling: Dynamically modify log levels for specific logger categories to enhance monitoring and troubleshooting.
A code fix was applied to the CI Jobs module of versions 23.1 and 24.1 due to a use-case error causing the CI Job History report to not generate. #116943
A code fix was applied to the Admin module of version 24.1 from an internal ticket identifying a use case in which the user was getting an 'unauthorized 401' error during a new account signup registration.
A code fix was applied to the Admin module of version 24.1 identified by internal ticket a use case in which the user was unable to log in via the default SSO login page; also, the build version and revision information were not displaying.
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error in which an issue was occurring with the system administrator lite. Support ticket #117297
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error in which the user was not able to see the metadata through the single revision deployment. Support ticket #116919
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error in which the user was not able to deploy the Einstein Prediction builder. Support ticket #116909
A code fix was applied to the Admin module of versions 23.1 and 24.1 due to a use-case error with users losing access. Support ticket #111830
A code fix was applied to the Version Control module of versions 23.1 and 24.1 due to a use-case error requiring multiple revisions on an ALM work item. Support ticket #117810
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error with the new profile compare feature. Support ticket #117309
A code fix was applied to the nCino module of version 24.1 due to a use-case error in which Data Loader jobs were being automatically deleted. Support ticket #117577
A code fix was applied to the CI Jobs and Deployment modules of version 24.1 due to a use-case error causing the rollback functionality to not work properly. Support tickets #117512, #118316
A code fix was applied to the CI Jobs module of version 24.1 due to a use-case error in which CI Jobs were experiencing a build issue, which is awaiting QA verification from the customer. Support ticket #118301
A code fix was applied to the CI Jobs module of version 24.1 due to a use-case error identified by internal ticket in which a CI Unlocked package installed CI build failing with Hub connection failure, even though Hub connection was successful.
An internal ticket identified an EBR change request required to the EBR module of version 24.1 to correct EBR plugins.
A code fix identified in version 24.1 by an internal ticket was initiated to the EBR Change module in version 24.1, prompted by a change to the EBR plugin info.
A use-case error identified in version 24.1 by an internal ticket required a code fix to the Version Control module in version 24.1 due to the commit history screen getting stuck loading when the repo name has a special character in it (e.g., plus sign [+]).
A use-case scenario identified in version 24.1 by an internal ticket required a code fix to the CI Jobs module in version 24.1 for the time-frame window to be added for the ARM admin API to fetch data.
A use-case error identified in version 24.1 by an internal ticket required a code fix applied to the nCino module in version 24.1 to correct where the option "automap user/owner data" is disabled by default for CI jobs created in 23.1.x versions.
A use-case scenario identified in version 24.1 required a code fix to the Version Control module in version 24.1 due to release labels not showing. Support ticket #116413
A use-case error identified in version 24.1 required a code fix to the Version Control module in version 24.1 due to an issue with choosing the Level 1 approver when performing a merge. Support ticket #116417, #116692
A use-case error was identified in version 24.1 that required a code fix to the nCino module due to the RBC filters not working on commits. Support ticket #116291
A use-case scenario identified in version 24.1 via an internal ticket required a code fix to the nCino module to correct an error in which the Data Loader clone process is not identifying the new CSV file.
A use-case error identified in version 24.1 required a code fix to the Version Control module to correct an error in which user is unable to create an EZ-Merge. Support ticket #116700
A code fix was applied to the Deployment and Version Control modules to correct a use-case error identified in version 24.1 in which the org comparison is not showing diff results. Support ticket #116039
A use-case scenario required a code fix to the version 24.1 Admin module to correct an error that caused the branching baseline to keep running for 24 hours. Support ticket #114734
A code fix was applied to the Version Control module to correct a use-case error identified in version 24.1 that caused commits to be failing with an 'no credentials mapped' error. Support ticket #116704
A use-case error identified in version 23.1 required a code fix to the Deployment module, applied in versions 23.1 and 24.1, to correct the metadata retrieval in the repository from failing. Support ticket #115818
A code fix identified in version 23.1 by an internal request ticket was applied to the Admin and CI jobs modules in versions 23.1 and 24.1 to upgrade v61 (Beta) to v61.
A use-case error in version 24.1 with the Version Control module in which commits were remaining in progress was resolved through a code fix. Support ticket #115691
A use-case error in version 24.1 with the Version Control module with commit CI Job deployment errors was resolved in 24.1 through a code fix. Support ticket #115817
A use-case error reported in version 24.1 required an update to the Admin module to properly reflect X rather than Twitter along with revised copyright information, which was resolved through a code fix. Support ticket #115756
A code fix was applied to the Reports module for a use-case error related to an alignment issue in the weekly reports filter for no deployments.
A code fix was applied to the Admin module for a use-case error in which the user is unable to create a search and substitute rule.
A code fix was applied to the Admin module for a use-case error related to being unable to register a branch.
'Created and Requested by' in Deployment UI Users are now able to view the ‘Created by’ and ‘Triggered by’ fields in the Deployment home screen without scrolling through multiple screens for this info, enabling monitoring of the deployment’s real-time progress. Read more
Self-Service Connected App Setup for Jira OAuth in ARM We've introduced a self-service feature allowing users to set up Jira OAuth-connected apps in ARM autonomously. With guidance from our user manual's Connected App guide, users can effortlessly create and register their app credentials, eliminating the need for support team assistance. Users can quickly establish a robust connection by inputting the generated Client ID and Server Key into ARM's settings.
Unified Admin Roles We’re excited to introduce a streamlined and more efficient Admin experience. We’ve consolidated the roles of Super Admin and Registered Admin into a single empowered Admin role. This change means Admins now have a unified set of tools and permissions, streamlining tasks and creating a more user-friendly Admin experience.
CI Jobs List and Results: Filter and Export Option We've enhanced the platform with a user-friendly quick filter and export feature in response to user feedback. This functionality empowers administrators, release managers, and users to efficiently organize and analyze data by alphabet or date, facilitating faster insights and informed decision-making.
Create Artifact: Release label more than 180 days In the Create Artifact section, users can now generate a Release Label and have the flexibility to choose an extended timeframe of over 180 days for retrieving comprehensive commit history data. This enhancement offers users a broader historical perspective, facilitating more in-depth analysis and tracking of commits for their projects.
Enhanced security and user experience. (NEW) The new features focus on enhancing security and user experience. They include a single-user session control to prevent multiple active sessions under the same username, automatic logout for inactivity to bolster security, and support for multiple tabs or pages in the same browser, improving user productivity and maintaining the environment's integrity.
A code fix was applied to the Admin module of versions 23.1 and 24.1 due to a use-case error with users losing access. Support ticket #111830
A code fix was applied to the Version Control module of versions 23.1 and 24.1 due to a use-case error requiring multiple revisions on an ALM work item. Support ticket #117810
A code fix was applied to the Deployments module of versions 23.1 and 24.1 due to a use-case error with the new profile compare feature. Support ticket #117309
A code fix was applied to the Deployments module of version 23.1 due to a use-case error with 'add additional member' showing duplicates when expanding the toggle. Internal request.
A code fix was applied to the Version Control module of version 23.1 due to a use-case error with users getting an error for a commits tab external pull request using Bit bucket repo. Internal request.
A code fix was applied to the Deployment module in version 23.1 due to a use-case error in which the user was unable to get the popup while deploying using package.xml as the source. Support ticket #116967
A code fix was performed due to a use-case error related to the Version Control module in which an ALM work item was not displaying in the merge. Support ticket #113626
A code fix was performed due to a use-case error related to the Admin module in which a user was unable to implement ARM and Zoho desk integration with JWT.
A code fix was performed due to a use-case error related to the Version Control module in which a user was unable to perform EZ-Commits. Support ticket #114441
A code fix was performed due to a use-case error related to the Version Control module in which the previously validated commit label showed to add a date instead of the label dropdown. Support ticket #115249
A code fix was performed due to a use-case error related to the Reports module that required us to fix recursive errors.
A code fix was performed due to a use-case error related to the Data Loader module in which the master-child relationships were not being applied when loaded through Data Loader Pro. Support ticket #111780
A code fix was performed due to a use-case error related to the nCino module in which the CI job was not updating templated objects and object record count when the checkout was not taken from version control. Support ticket #112704
A code fix was performed due to a use-case error related to the nCino module wherein CI Jobs for nCino RBC feature migrations were failing. Support ticket #114991
A code fix was performed to the Admin module as a result of a change request related to users being unable to log in to AutoRABIT. Support tickets #115392, #113300
A code fix was applied to the Admin module related to a data error in which the branching baseline was not updating the LWCs in the branch. Support ticket #113174
A code fix was applied to the Data Loader module related to a configuration error causing Data Loader to not work as expected. Support ticket #113575
A code fix was applied to the ARM module related to a use-case audit logging API error with start time and end time issues occurring when fetching logs. #113739
A code fix was applied to the Version Control module related to a use-case error in which Mock Deployment criteria check lines were not logged in the UI during the Prevalidation Deployment refresh, but they do appear after auto-rejection and subsequent refresh.
A code fix was applied to the Deployment module to correct a use-case error occurring when selecting and deselecting ApexClass and CustomField metadata types, the Deploy pop-up incorrectly displayed "All components are selected" for ApexClass instead of the list of selected components.
A code fix was applied to the Version Control module to correct a use-case error displaying unwanted characters, such as different language letters, like “— in the message: "Please wait†when a compare and commit is in progress."
A code fix was applied to the Version Control module due to a use-case PrevalidationMerge error occurring when the user was trying to approve a Merge Label through an API with an auto-rejected label, the status changed from "Auto-reject" to "Commit."
A code fix was applied to the Version Control module after a user observed three gaps/issues in Commit Templates: 1) Data Table Change in the Commit Template under the 'All Metadata' tab should also sync across all three places, like Deployments, VC Commit, and Commit Template under the 'All Metadata' tab for data table changes. 2) Folder-Related Members Visibility: Folder-related all members are not visible when selecting the folder. This does not sync with EZ Commit All Metadata, from new commit all members. When selecting the folder, all respective folder-related members are visible but not included in the Commit Template when selecting the same Salesforce org. 3) Input Search Dropdown Missing for selecting Folders.
A code fix was applied to the Data Loader module concerning a use-case error in which the user was unable to create a project journey with a BIC__c field using "LookUp via" feature. Support ticket #110111
A code fix was applied to the Deployment module due to a data error in which there was a problem in component selection during deployment. #111892
A code fix was applied to the Deployment module due to a data error in which the selected items tab was now showing the selected components, as well as the search filter not always being visible. #112095
Internal - Code fix applied to Version Control module due to DX Package Directory Selection lists not being visible when configuration changes from Vlocity SF org and Vlocity repo to DX Repo.
Code fix applied to Version Control module related to an auto-rejected merge label being pushed to a remote repository. #112244
Code fix
Use case
Version Control
Commit Issue with Custom Page Web Links Deletions
QA Passed
23.1
Code fix
Use case
Version Control
Configure Gated Check-Ins Report for Deployment Validation
QA Passed
23.1
Code fix
Use case
Version Control
Improve Performance of All Metadata Components Screen
QA Passed
23.1
Code fix
Use case
Administration
EBR User Metrics
Done
23.1
Code fix
EBR Change Request
Data Loader
Data Loader Pro jobs not picking up Records
Customer Coordination
23.1
Added Loggers
Use case
Code fix
Use case
Version Control
EZ-Commits failing
QA Passed
23.1
Code fix
Use case
Version Control
Static resources not identified by ARM SCA
QA Passed
23.1
Code fix
Use case
Version Control
Merge showing as no modifications
QA Passed
23.1
Code fix
Use case
Version Control
Error occurred when the user attempted to upload the conflicted zip file from the local system after manual modifications
QA Passed
23.1
Code fix
Use case
Reports
Inquiries regarding report module
QA Passed
23.1
Code fix
Use case
Deployments
Deployment from Dev Sandbox to B2C2 QA Org by using feature - New Deployment
QA Passed
23.1
Code fix
Use case
CI Jobs
Build did not include second revision
Requires Customer Coordination
Loggers added
Loggers added
CI Jobs
Run test based on changes, noticed issues
Requires Customer Coordination
Loggers added
Loggers added
nCino
IDs of parents/children and records not resolving
QA Passed
23.1
Code fix
Use case
Deployments
Backups not being created for user
Code fix
Use case
Version Control
Code Scan Analysis not showing in AR ARM tool - UI
Code fix
Use case
Version Control
setting default repository
Code fix
Use case
Deployments
ExternalCredentialPrincipalAccess (permissionSet) is ignored on a git revision deployment
Code fix
Use case
Version Control
Unknow error while merging site components
Code fix
Use case
CI Jobs
CI Job does not deploy all components
Code fix
Use case
Admin
SSH connectivity issue
Code fix
Use case
Version Control
request_closure_duration_mins mismatch for the merges
Code fix
Use case
Reports
B2C Prod Code Scan report
Code fix
Use case
nCino
AR issues
Added Loggers
Use case
Dataloader
User Object Requiring ALL Fields for Uploads
Added Loggers
Use case
Code fix
Use case
CI Jobs, Deployments
Einstein Chatbot Deployments Failing
QA Passed
23.1
Code fix
Use case
Admin
log files are not present
QA Passed
23.1
Code fix
Use case
Deployments
Deployments are not working
QA Passed
23.1
Code fix
Use case
CI Jobs, Deployments
Failed to initiate the deployment
QA Passed
23.1
Code fix
Use case
Version control
Profile commit progress delay
QA Passed
23.1
Code fix
Use case
Admin
Team Administrator modifications creating duplicate Teams and consuming existing licenses
QA Passed
23.1
Code fix
Use case
Version control
Issue Retrieving Components
QA Passed
23.1
Code fix
Use case
Version control
Release Label Stuck while building Artifact
Requires Customer Coordination
Loggers added
Deployments
utils.js was not deployed as part of package
Requires Customer Coordination
Loggers added
nCino
Version control record deployments to Salesforce Environments falling off
QA Passed
23.1
Code Fix
Use case
nCino
Lack of Consistency in Filter Functionality Across Feature Management, Deployment History, Commit History, and CI Jobs
QA Passed
23.1
Code Fix
Use case
Version control
Unable to view the Autodraft date and managed package changes dropdown
QA Passed
23.1
Code Fix
Use case
Admin
Super Admin EBR Token Security Enhancement
Done
23.1
Code fix
Internal change request
Version Control
Getting empty revision when performing single revision merge with no modifications
Code Fix
Use Case
Version Control
Unable to create branch with branch name containing "&" through EZ-commit and Modularization
Code Fix
Use Case
nCino
Failure to Display Jobs in Deployment History for Version Control using Salesforce with Single Revision of initial commit
Code Fix
Use Case
nCino
Feature Deployment issue with Salesforce Org Version Control when selecting initial commit as Revision
Code Fix
Use Case
nCino
Version control record deployments to Salesforce environments dropping off
Code Fix
Use Case
QA Passed
23.1
23.1
Code Fix
Use Case
Reports
Problem with scheduled code coverage reports
QA Passed
23.1
23.1
Code Fix
Use Case
Deployments
Profile Comparer - Taking too long to deploy
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
Issue in Merging
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
Incorrect merge status issue
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
The page is taking longer time to load the metadata when selecting to show metadata members.
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
Vlocity DataPacks not being baselined
QA Passed
23.1
23.1
Code Fix
Use Case
Admin
Getting stuck in loading when trying to Expand ALM mappings
QA Passed
23.1
23.1
Code Fix
Use Case
CI Jobs
CI Deploy job link throwing pop-up error message
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
Loggers added in the SCA log to display whether the baseline branch was selected during the commit and merge process
Customer Coordination
23.1
NA
No Code Fix
Loggers Added
nCino
Data Loader Pro jobs failing for Lead
QA Passed
23.1
23.1
Code Fix
Use Case
nCino
nCino Deployment History - search filter criteria is not working
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
Unnecessary select all checkbox is showing in added and modified tab
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
Unable to view created credentials
QA Passed
23.1
23.1
Code Fix
Use Case
CI Jobs
Returns all CI Jobs History to EBR Data irrespective of active
Done
23.1
23.1
Code Fix
Internal change request in EBR Data Visibility
nCino
Feature Deployment Issue with Salesforce Org Version Control
QA Passed
23.1
23.1
Code Fix
Use Case
Data Loader Pro
Issue with Audit Fields
QA Passed
23.1
23.1
Code Fix
Use Case
Admin, Version Control
Unable to register the same repository twice * REQUIRES FEATURE FLAG: SKIP_DUPLICATE_REPOSITORY_REGISTRATION_CHECK
QA Passed
23.1
23.1
Code Fix
Use Case
CI Jobs
Error Message: Cannot invoke "String.startsWith(String)" because the return value of "com.autorabit.entity.admin.UserProject.getProjectType()" is null. Support ticket # 109042
QA Passed
23.1
23.1
Code Fix
Use Case
Code Fix
Use Case
Version Control
Very slow commits
QA Passed
23.1
Code Fix
Use Case
Version Control
Unable to create branch with '&' character getting Exception Error
QA Passed
23.1
Code Fix
Use Case
Version Control
Issues after Branching Baseline
Requires Customer Coordination
Added Loggers
No Code Fix
Reports
Static Code Analysis fails with timeout error
Requires Customer Coordination
Post fix awaiting customer confirmation.
Code Fix for SF CL timeout configuration.
Admin
Observing that after the 7th file, RabitCS and Agent logs are not being created or generated. From the 8th file, they are being overridden from Existing files 1 to 7.
QA Passed
23.1
Code Fix
Use Case
CI Jobs, Deployments
Identified below nCino CI Job "related to VC Source job type" displaying issue in CI jobs and Deployments
QA Passed
23.1
Code Fix
Use Case
Flow Center
Enable SSL for the Kafka used to communicate with FlowCenter.
QA Passed
23.1
Code Fix
Use Case
nCino
nCino Feature deployment failed with a “malformed query” error, Feature deployment and Ci Job. nCino CI jobs the customer has run failed with an exception, and the failed records column shows zero.
QA Passed
23.1
Code Fix
Use Case
Data Loader Pro
[ARM-QAN5,7] The job is currently running in progress, but the Success Record Count is showing in the Failure Count.
QA Passed
23.1
Code Fix
Use Case
Signup account creation email not received by respective created-by owner
23.1
Code Fix
Use Case
Deployments
packExport is not failing when selecting data packs
23.1
Code Fix
Use Case
CI Jobs
Status Check API working incorrectly on UI
23.1
Code Fix
Use Case
CI Jobs
Issue when deploying the release to the master branch
23.1
Code Fix
Use Case
Version Control
Issue when creating commit labels with dots (.) post upgrade * Feature Flag required (not enabled by default): INCLUDE_DOT_IN_SFDX_COMMITLABEL_NAME
23.1
Code Fix
Use Case
Version Control
Intermittent issue with the Merge screen
23.1
Code Fix
Use Case
Version Control
Commit Labels within EZ-Merge no longer sorted by latest Commits
23.1
Code Fix
Use Case
Reports
CodeScan analysis discrepancies in APAC Prod * Requires documentation update
23.1
Code Fix
Use Case
Version Control
Territory metadata type is not fetched as destructive changes during EZ-Commit.
23.1
Code Fix
Use Case
Dataloader
Dataloader Pro was not copying over Contact fields when migrating data
23.1
Code Fix
Use Case
Dataloader
When updating the data using a CSV file, the update operation in Dataloader was failing with the error MISSING_ARGUMENT: ID is not specified
23.1
Code Fix
Use Case
Dataloader
The latest record was not being fetched in the single Dataloader
23.1
Code Fix
Use Case
nCino
Deployment History - search filter criteria was not working
23.1
Code Fix
Use Case
Dataloader
Problem loading ContentVersion object
23.1
Code Fix
Use Case
CI Jobs
Deployment stuck
23.1
Code Fix
Use Case
Unable to Log in to AutoRABIT via Okta
23.1
Code Fix
Use Case
Version Control
EZ-Merge - User Approval Setting is not working as expected
23.1
Code Fix
Use Case
Version Control
EZ-Commit Salesforce Org Authors not completed
23.1
Code Fix
Use Case
CI Jobs
Dashboards and reports were overwritten after the deployment to PROD
23.1
Code Fix
Use Case
Admin
Suggestion-SF org UI
23.1
Code Fix
Use Case
Reports
Suggestion to display a notification if a label has already been created for the same branch previously.
23.1
Code Fix
Use Case
Admin
Expose API for Super Admin Token Authentication to Test Registered Agents' Connections
23.1
Code Fix
Use Case
Version Control
Added metrics in ARM DB
23.1
Code Fix
Use Case
nCino
Post Deployment Org Details need to be displayed on CI Job Info pop-up
23.1
Code Fix
Use Case
nCino
CI Jobs Build Page - Pagination displayed as "undefined"
23.1
Code Fix
Use Case
nCino
nCino CI jobs - Date Literals Value not being populated
23.1
Code Fix
Use Case
nCino
When the Source Org is deleted, scheduled CI Job is not triggered from the queue
23.1
Code Fix
Use Case
nCino
[API Upgrade v59.0] Attachments Object Failed due to "Index 1 out of bounds for length 1" error
23.1
Code Fix
Use Case
Dataloader
Unable to migrate related EmailMessage records of Case
23.1
Code Fix
Use Case
CI Jobs
Unable to view API 59 version in CI configuration under API version dropdown.
23.1
Code Fix
Use Case
SF CLI version upgrade to 2.28.6 for ARM 23.1 instances
Code Fix
Change Request
Version Control
Able to approve auto-rejected merge from email
Code Fix
Use Case
Version Control
PersonAccount AutoRABIT bug
Code Fix
Use Case
CI Jobs
It is not possible to run several CI Jobs in parallel when jobs are scheduled.
Code Fix
Use Case
SFDX
Error on create package version and install type of job.
Code Fix
Use Case
AR_33235_SKIP_UPDATE_PACKAGE_COMMAND
Dataloader
CPQ Dataload in Developer Sandbox - Errors
Code Fix
Use Case
nCino
nCino CI Job issue
Code Fix
Use Case
Dataloader
Invalid CSV file. Please check for blank columns.
Code Fix
Use Case
Dataloader
CSV file does not reset when you go back to the previous step in a single data loader
Code Fix
Use Case
Version Control
Getting Undefined Error for target branch in External Pull request
Code Fix
Use Case
Version Control
Unable to resolve conflicts in release label merge.
Code Fix
Use Case
Flow Center
Search & Substitute rules are not applied in the pipelines.
Code Fix
Use Case
All Modules
Support for Salesforce Spring ‘24 * Requires Documentation
Code Fix
Change Request
Version Control
Unable to commit the action overrides in service appointment object.
Code Fix
Use Case
Version Control
Quick Merge shows below pop-up
Code Fix
Use Case
Version Control
Unable to add the reviewer's name when using an external pull request
Code Fix
Use Case
Version Control
EZ-Merge Validation Failing: "Metadata package is empty"
Code Fix
Use Case
Admin
Branching baseline for main branch not bringing all components from production. * Feature Flag: METADATA_API_TO_DX_CONVERSION
Code Fix
Use Case
Version Control
Unable to commit a profile
Code Fix
Use Case
Version Control
Release label throwing InvalidFilterExpression error
Code Fix
Use Case
nCino
Error message when attempting to clone a feature template: ‘Request parameters are empty/null.'
Code Fix
Use Case
Dataloader
Dataloader Pro issue while triggering the job
Code Fix
Use Case
Version Control
Add additional metrics in ARM DB.
Code Fix
Use Case
nCino & Dataloader
nCino - Support for Salesforce Spring ‘24
Code Fix
Use Case
FC, Deployments
Flow Center API: Create a metadata bundle from an org
Code Fix
Use Case
Deployments
"Experience container" metadata type component deployment is failed for org-to-org deployment
Code Fix
Use Case
Version Control
Unable to view the revision number when clicking on prevalidation merge details.
Code Fix
Use Case
Version Control
Unable to fetch date from Auto-Draft when selecting DX branch in sub-user with no mappings.
Code Fix
Use Case
Deployments
Deployment failed with error: ‘Cannot invoke "java.util.Map.clear()" because "this.relatedLayoutRecordTypeIdsMap" is null’
Code Fix
Use Case
nCino
CI Jobs: date filter not selectable or enter date value.
Code Fix
Use Case
Dashboards
ARM dashboard
QA Passed
23.1
Code Fix
Use Case
NO
NO
Deployments
Org sync - Scheduler not working
QA Passed
23.1
Code Fix
Use Case
NO
NO
Version Control
Commit failing without any logs
QA Passed
23.1
Code Fix
Use Case
NO
NO
Version Control
Single-revision merge taking a long time
Customer Coordination [Added Loggers]
No Code Fix - Added Loggers
No Code Fix - Added Loggers
Data
NO
NO
Version Control
Package.xml fetching the Excluded components during Commit
QA Passed
23.1
Code Fix
Use Case
NO
NO
Deployments
Smart checkbox redeployment
QA Passed
23.1
Code Fix
Change Request
NO
NO
Version Control
PG and ARM instances not working as expected
QA Passed
23.1
Code Fix
Use Case
NO
FILE_SYNC_WITH_OPTIMISTIC_LOCK
Version Control
Commit not getting detected
QA Passed
23.1
Code Fix
Use Case
NO
NO
Version Control
Error while trying to select the revision from branch
QA Passed
23.1
Code Fix
Use Case
NO
NO
Code Fix
Use Case
Deployment
Need a feature to save metadata selection before deployment
QA Passed
23.1
Code Fix
Use Case
Deployment
Page unresponsive in new deployment using Previous Deployment as a source type
QA Passed
23.1
Code Fix
Use Case
Administration, CI Jobs
Upgrade v59 (Beta) to v59
QA Passed
23.1
Code Fix
Use Case
Administration
CI Job and Code Coverage Not Running at Correct Times
Customer Coordination
Customer Coordination
Dataloader
Configuration job failure
QA Passed
23.1
Code Fix
Use Case
Version Control
In the MergeRequest, CI Job View Screen under Build title, the Merge Request comment alignment is not displaying properly; it is not getting trimmed and appears larger than expected.
QA Passed
23.1
Code Fix
Use Case
Administration
Unable to view ‘Should pass validation criteria for Static Code Analysis’ checkbox under commit validation settings when Salesforce API version is not mapped
QA Passed
23.1
Code Fix
Use Case
Administration
Release Label artifact execution is not working.
QA Passed
23.1
Code Fix
Use Case
nCino
Partial error on CI Job - nCino-Fee Template
QA Passed
23.1
Code Fix
Use Case
QA Passed
23.1
Code Fix
Use Case
Deployment
‘Not a well-formed XML.' error when attempting org-to-org deployments in UAT
QA Passed
23.1
Code Fix
Use Case
CI Jobs
Package CI Job Issue
QA Passed
23.1
Code Fix
Use Case
Deployment
Vlocity Deployment issue
QA Passed
22.3, 23.1
Code Fix
Use Case
Version Control
Vlocity Release label issue
QA Passed
23.1
Code Fix
Use Case
Version Control
EZ-Commit not creating a branch
QA Passed
23.1
Code Fix
Use Case
Version Control
ARM failed to auto-reject EZ-Merge request that has Apex class with less than 90% code coverage. Merge setting enforcing 90% code coverage in mock deployment.
QA Passed
23.1
Code Fix
Use Case
Version Control
CodeScan – Delta scan
QA Passed
23.1
Code Fix [Added Loggers for customer understanding,]
CI Jobs
Ignore warnings option in CI jobs is not working properly
QA Passed
23.1
Code Fix
Use Case
Version Control
Commit failing without any logs
QA Passed
23.1
Code Fix
Use Case
Environment Provisioning
Apex Anonymous Template not downloadable
QA Passed
23.1
Code Fix
Use Case
Version Control
‘File can't be loaded’ error
QA Passed
23.1
Code Fix
Use Case
Deployment
During Profile Manger Deployment, "NULL MSG: NULL" is displaying in the log
QA Passed
23.1
Code Fix
Use Case
Deployment
Using Package XML: Document XML files are not being listed in the Org compare screen
QA Passed
23.1
Code Fix
Use Case
CI Jobs
CI Job build is failing without printing reason in logs for BY SELECTING LAST TILE: install unlock package/managed tile.
QA Passed
23.1
Code Fix
Use Case
Dataloader Pro
Multiple issues during data masking
Customer Coordination – Added Loggers
23.1
No Code Fix – Added Loggers
Data
QA Passed
23.1
Code Fix
Use Case
Version Control
Package.xml generated from release label is other components that are not in the commits
QA Passed
23.1
Code Fix
Use Case
Version Control
Finding WaveDataflow components for commit
QA Passed
23.1
Code Fix
Use Case
Admin
Error: Access token as failed while doing a branching baseline
QA Passed
23.1
Code Fix
Use Case
CI Jobs
Provar version upgrade
QA Passed
23.1
No Code Fix – Only Configuration change for specific customer
Customer-specific
Version Control
Initial commit failing
Customer Coordination
No Code Fix – Added Loggers
Data
Admin
Users’ permissions are being reset.
Customer Coordination
No Code Fix – Added Loggers
Data
CI Jobs, Version Control, Admin, Deployments
Adding authentication check on web hook APIs
QA Passed
23.1
Code Fix
Change Request
Dataloader Pro
Issue while deploying promotions from QAT to PRD the rule set criteria is compressing the value while deploying it to RD
QA Passed
22.3 23.1
Code Fix
Use Case
Dataloader Pro
Issue on Feature Deployments
QA Passed
22.3 23.1
Code Fix
Use Case
Version Control
Missing Component in Package: PROD
23.1
Code Fix
Use Case
Deployments
Release Label not appearing in Deployment tab
23.1
Code Fix
Use Case
CI Jobs
API broken for job history
23.1
Code Fix
Use Case
CI Jobs
Deploying Flow - Property 'customErrors' not valid in version 58.0
23.1
Code Fix
Use Case
Deployments
Deployment status failed when deploying Vlocity components
22.3, 23.1
Code Fix
Use Case
Version Control
On Prevalidation Commit, the SonarQube SCA process is auto-rejected, even for unsupported metadata types.
23.1
Code Fix
Use Case
Deployments
Brazil Prod to UAT deployment issue
23.1
Code Fix
Use Case
nCino
Metadata update is failing
23.1
Code Fix
Use Case
Version Control
Commit not progressing
23.1
No Code Fix - Loggers Added
Data
Use Case
CI jobs
Provar CI Job run takes a very long time and stops at status "Timed-Out"
23.1
Code fix
Use Case
Deployments
ARM API to perform a deployment (or a validation, or a quick deploy)
23.1
Code fix
Use Case
nCino
Issue with Regex on Feature Deployments
23.1
Code fix
Use Case
CI jobs
Team/Slack in CI job post activity notification, users should not have email dependency in email notification. Suggestion.
23.1
Code fix
Use Case
CI jobs
Package creation CI job
23.1
Code fix
Use Case
CI jobs
On both CI Results and CI Lists, user getting the “Invalid FilterExpression: Expression size has exceeded the maximum allowed size;(Service: DynamoDb“error) when selecting the “Ungrouped” value under “group by “ filter dropdown
23.1
Code fix
Use Case
Version Control
CodeScan – EZ-Commit Auto Rejected
23.1
Code fix
Use Case
Admin
Client login error
23.1
Code fix
Use Case
Admin
Unable to edit and save changes for Exclude Baseline Managed Package Changes
23.1
Code fix
Use Case
nCino
Deployment getting failed for queued jobs
23.1
Code fix
Use Case
Change Request
Version Control
A non admin user cannot access the repository under the VC module.
23.1
Code Fix
Use Case
Deployment
Help investigating deployment errors
23.1
Code Fix
Use Case
CI Jobs
Not receiving post activity notifications
23.1
Code Fix
Use Case
Admin
Feedback option change to message. Will require updated documentation.
23.1
Code Fix
Change Request
Admin
[On-premises – Signup for Demo] The registration screen opens when clicking on 'Signup for Demo,' even if the account is already registered.
23.1
Code Fix
Use Case
Admin
[On-premises] Service registration tab, alignment tab not visible properly and, when clicking on the tab, redirects to the logout page.
23.1
Code Fix
Use Case
Admin
Unable to view ‘Credential already exists’ popup under ‘My profile.’
23.1
Code Fix
Use Case
Reports
Previously deleted log showing on other label if created Static Code Analysis label previously deleted SCA label name.
23.1
Code Fix
Use Case
SFDX
When creating the package on a new module for the first time through modularization, Package creation failed with the error ["SaiJun19thprofile: An object 'SaiJun19thprofile' of type Profile was named in package.xml.'] Will require updated documentation.
23.1
Code Fix
Use Case
Version Control
Unable to view committed files in direct EZ revert commit using DX repository.
23.1
Code Fix
Use Case
Deployment
[On-Premises] Getting 'Malformed Id: Null' error displaying for a few seconds when performing a rollback operation for Org-to-Org deployment.
23.1
Code Fix
Use Case
Deployment
[Org Synchronization] ‘SourceOrg,’ ‘Created date,’ and ‘Created by’ filters are not working properly.
23.1
Code Fix
Use Case
nCino
[On-Premise Testing] CI Job with template option failed due to "Data and Metadata retrieval Failed” error.
23.1
Code Fix
Use Case
Deployments
ARM API to perform a deployment (or validation or quick deploy)
23.1
Code Fix
Use Case
Version Control
[ARM-SIT] Unable to view branches in SCM history screen
23.1
Code Fix
Use Case
Use Case
SFDX
Error creating unlocked package
23.1
Code fix
Use Case
Version Control
CI Job report for Master-to-BackMerge Org Sync_13-Deployment Failed
23.1
Code fix
Use Case
Version Control
Merge shows no modification, but a CI job is triggered
23.1
Code fix
Use Case
nCino
* User is unable to do nCino Feature Deployments * Requires documentation
23.1, 22.3
Code Fix
Use Case
Dataloader
Getting error when clicking on Dataloader configured filter
23.1
Code Fix
Use Case
CI Jobs and Deployments
ARM API to perform a deployment (or validation or quick deploy)
23.1
Code Fix
Enchancement
Version Control
Unable to perform merge for sub-user, getting error to re-login
23.1
Code Fix
Use Case
Admin
On-premise: ‘Proxy Configuration settings,’ ‘Audit logs’ section, and ‘Pool Mgnt" screen tab are missing.
23.1
Code Fix
Use Case
Admin
On-premise: When trying to save the ‘Audit Logs’ section in ‘My Account’ screen, the error “Uncaught TypeError: Cannot read properties of undefined (reading 'showMessage')” is encountered in the console.
23.1
Code Fix
Use Case
CI Jobs
For the 'Create and Install Package' job, when selecting 'Deploy Using Create a Scratch Org and Install Package,' after successfully completing the build, an error is displayed in the log: “this.salesForceOrgDAO” is null.
23.1
Code Fix
Use Case
Admin
Getting ‘null parameters’ error when clicking on save in the user’s section.
23.1, 22.3
Code Fix
Use Case
Version Control
Unable to perform merge request for sub-user getting error to re-login.
23.1
Code Fix
Use Case
Version
Control
Unable to perform branching baseline on sub-user, getting error to re-login
23.1
Code Fix
Use Case
Use Case
Admin
Issue with registering new branch in the repository
23.1
Code Fix
Use Case
Reports
ARM and CodeScan integration EZ-Commit validation issue
23.1
Code Fix
Change Request
Reports
New branch created CodeScan issue
23.1
Code Fix
Use Case
Deployments
Destructive package is not generated properly when deploying from git revisions
23.1
Code Fix
Use Case
Admin
nCino View Object Failing
NA
No Code Fix - Added Loggers
Data
Deployments
Org sync not completing
NA
No Code Fix - Added Loggers
Data
Dataloader
Corrected a spelling mistake in ARM steps.
23.1, 22.3
Code Fix
Use Case
Dataloader
Corrected data seeding error preventing upsert
23.1, 22.3
Code Fix
Use Case
Reports
Getting ‘cannot invoke "String.length()" because of "text" is “null”’ error when performing the ‘Get latest reports’ in Weekly reports
23.1
Code Fix
Use Case
Reports
When navigating to Static Code Analysis screen from Reports module, getting the “comparison method violates its general contract!” error.
23.1
Code Fix
Data
Version Control
On DX branch release label artifact execution, on deleted components, the destructive changes artifact preparation is not generated.
23.1
Code Fix
Use Case
nCino
On-premise testing: CI Job with template option failed due to "data and metadata retrieval failed” error
23.1, 22.3
Code Fix
Use Case
CI Jobs
Failed to deploy destructive changes though CI jobs.
23.1
Code Fix
Use Case
Use Case
CI Jobs
CI job filter not working properly
23.1
Code Fix
Use Case
Version Control
Commit not getting detected
23.1
Code Fix
Use Case
Version Control
Rejecting a commit is merging the changes
23.1
Code Fix
Use Case
Admin
Unable to save Pull Request Plugin config
23.1
Code Fix
Use Case
Version Control
AR commit File Diff process is failing with errors
23.1
Code Fix
Use Case
Version Control
Merge auto-rejected but CI job triggered
23.1
Code Fix
Use Case
Admin
Changing role from Dev to Admin shows orgs and branches in New EZ- Commit without mapping under profile
23.1
Code Fix
Use Case
Version Control and Deployment
Release Label Artifact not including code for a commit
23.1
Loggers Added
Data
Dataloader
Dataloader Pro jobs causing huge threads pileup
23.1
Enhancement
Use Case
CI Jobs
Data Retention – CI Jobs - Observing 'java.lang.NumberFormatException' error in the CI Retention process log when processing the string '2023-08-26.' Please check the date formatting to ensure it is being treated as a string and not causing the exception.
23.1
Code Fix
Use Case
Version Control
While submitting the ALM commit with these “<ALM Issue ID>“, “{ALM Issue ID}” ALM patterns, unable to submit the commit
23.1
Code Fix
Use Case
Deployments
Sub-user - Deployment History - While changing the date range filter, getting "Cannot invoke "String.equalsIgnoreCase(String)" because the return value of "com.autorabit.entity.deployment.DeploymentHistory.getCreatedBy()" is null" error
23.1
Code Fix
Use Case
Version Control
With Release label deployment, the flow-meta.xml retrieval issue both constructive and destructive
23.1
Code Fix
Use Case
Version Control
Issue while creating feature branches in EZ - Commit screen
23.1
Code Fix
Use Case
Version Control
Upload File option not available during EZ- commit with Option package manifest
23.1
Code Fix
Use Case
Use Case
nCino
Unable to create Feature Migration Template on Debt Schedule object
22.3, 23.1
Code Fix
Use Case
All Modules
Invalid Email ID
22.3, 23.1
Code Fix
Use Case
CI Jobs, Deployments, Version Control, Admin
Org Sync diff report differs for the same source org compared to different orgs.
23.1
Code Fix
Use Case *
Dataloader
Urgent: AutoRABIT is down
23.1
Code Fix
Use Case
Version Control
Issue with Block button during Merge Conflict
23.1
Code Fix
Use Case
CI Jobs
CI job deployment failing: Restriction rules deployed as moderation rule and made the deployment bugged
23.1
Code Fix
Use Case
CI Jobs
Urgent: Rollback of specific components - Issue
23.1
Code Fix
Use Case
CI Jobs
Unexpected behavior when disabling component category on rollback destructive changes.
23.1
Code Fix
Use Case
SFDX
Error while using Scratch Org Management tab
23.1
Code Fix
Use Case
All Modules
ARM<>ULP Integration Issues
23.1
Code Fix
Use Case
Version Control
Auto-reject on commit validation for SCA & Auto-reject setting in Merge
23.1
Code Fix
Use Case
Use Case
Admin
Sync error between ARM and GIT
23.1
Code Fix
Use Case
Version Control
Deployment validation not working correctly during new EZ-Merge
23.1
Code Fix
Use Case
CI Jobs
Merging only revision in the CI job build not working
23.1
Code Fix
Use Case
Use Case
CI Jobs & Deployments
User is unable to deploy static resource.
23.1
Code Fix
Use Case
Reports
Scheduled Code Coverage Reports are running at the wrong time.
23.1
Code Fix
Use Case
nCino
User is unable to create Feature Migration Template on Debt Schedule object.
22.3, 23.1
Code Fix
Use Case
Dataloader
User is unable to upload files and update records; system logs user out instead.
23.1
Code Fix
Use Case
Version Control
User is getting timeouts in merge screen.
23.1
Code Fix
Use Case
Enhancement
Admin
Branching baseline is not picking all components from production
22.3 & 23.1
Code Fix
Use Case
Deployments
Help with destructive change
22.3 & 23.1
Code Fix
Use Case
Version Control
Merge request is failing due to validation credentials
22.3 & 23.1
Code Fix
Use Case
CI Jobs, Deployments
Issues with a release – related to Feature Flag - not automatically deployed: STANDARD_VALUE_SET_DELTA
22.3 & 23.1
Code Fix
Data
Version Control
Approval button is not visible after successful merge validation
22.3 & 23.1
Code Fix
Data
Version Control
Create artifact: not completed
23.1
Code Fix
Data
Admin
AutoRABIT login not working
23.1
Code Fix
Use Case
Version Control
Error pop-up during merge type selection as Commit Label in EZ-Merge
23.1
Code Fix
Data
CI Jobs
AutoRABIT AccelQ Integration/ bhg-inc.com
23.1
Code Fix
Use Case
CI Jobs
Developer API for CI Jobs History not returning latest results.
23.1
Code Fix
Use Case
nCino
Ability to trigger nCino CI jobs using REST API
23.1
Code Fix
Customer Request
CI Jobs
For run test automation scripts job: More than one cycle is not displayed in the individual job history
23.1
Code Fix
Use Case
Version Control
Unable to delete feature branch under merge request, getting internal server error
23.1
Code Fix
Use Case
Version Control
Unable to view the entry of recently created merge request in the merge request history screen
23.1
Code Fix
Use Case
Version Control
Criteria met ALM's not getting fetched under merge request
23.1
Code Fix
Use Case
nCino
Instead of POST methods need to change the GET
23.1
Code Fix
Customer Request
A code fix was applied to the Admin module of version 23.1 due to a use case in which modification logs were needed for Version Control mapping setup.
A code fix was applied to the Version Control module of version 23.1 related to a use-case error in which External Pull Requests, when expanding the files in the diff, content was not visible and showing as undefined.
A code fix was applied to the Version Control module of version 23.1 related to a use-case error in which External Pull Requests, when expanding files in the diff, show duplicate content.
A code fix was applied to the nCino module of versions 22.3 and 23.1 due to a use-case scenario during dataset creation with saving only user info in Json that is relevant to current dataset.
A code fix was applied to the Version Control module of versions 22.3 and 23.1 due to a use-case error with an AR merge failing.
A code fix was applied to the Version Control module of versions 22.3 and 23.1 due to a use-case error in which the incorrect removal of Custom Application type in package.xml on EZ-Commit via AR occurred.
A code fix was applied to the Version Control module of versions 22.3 and 23.1 in which two external pull request issues were occurring.
A Code Fix was applied to the Admin module due to an SSO Error as of Sept 25 caused by a use case with a fix applied to versions 23.1.
A Code Fix was applied to the Admin module due to an AutoRABIT Login Issue caused by a use case with a fix applied to versions 23.1.
A Code Fix was applied to the Version Control module due to validation/merge errors after latest release caused by a use case with a fix applied to versions 23.1.
A Code Fix was applied to the Dataloader module due to the download button not working caused by a use case with a fix applied to versions 23.1.
Implemented a code fix to versions 22.3 and 23.1 affecting the CI Jobs module due to a use-case issue to SFDX/CI jobs with package version installation key.
Performed a code fix to versions 22.3 and 23.1 affecting the Version Control module for a use-case issue related to custom label translation file.
Applied a code fix to versions 22.3 and 23.1 related to the Deployments module for a use-case error with previous deployment label 'add members' option not working.
Performed a code fix to version 23.1 affecting the Admin module due to a use-case error with MyProfile not redirecting properly and showing the profile icon after clicking on the 'profile' button.
Implemented a flow center change to versions 22.3 and 23.1 for the Dataloader module due to a use-case error with the download button not working.
Issued a code fix to versions 22.3 and 23.1 for a use-case error in the Version Control module with a custom label translation file.
Performed a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the Deployments module concerning bugs in deployment with multi-packages and static resource.
Applied a code fix to version 22.3 resulting from a use-case error affecting Dataloader returning an 'invalid cross reference id' error for ProcessInput and ProcessingInputCondition objects.
Implemented a code fix to version 23.1 for a use-case error to the Version Control module, in which duplicate commits were being created.
Performed a code fix to version 23.1 for a use-case error to the Version Control module pertaining to Deployment history, with the deployment status not being visible.
Performed a code fix to version 23.1 relating to a use-case error affecting the nCino module in which users are unable to deploy nCino feature (RBC), instead returning a 'malformed query' result.
Performed a code fix to version 23.1 relating to a use-case error to the Version Control module with users unable to perform new pull request commit due to commit template permission.
Executed a code fix to version 23.1 relating to a use-case error affecting the Version Control module with users continually getting a login redirect error when trying to create a branch through an EZ-Commit.
Performed a code fix to version 23.1 relating to a use-case error in the Version Control module with users unable to create a commit label, continually getting a login redirect error.
Performed a code fix to version 23.1 relating to a use-case error affecting the Admin module, particularly a SuperAdmin user, not getting any response to the scheduler's service registration button without expanding the selection.
Initiated a code fix related to a use-case scenario in version 23.1 affecting the Version Control module with release labels getting failed after restarting the agent.
Applied a code fix related to a use-case scenario affecting version 23.1 in the nCino module, when parallel CI jobs limit was reached, the job was not added to the queue.
Performed a code fix to correct a use-case error in version 23.1 related to the nCino module for a merge missing changes.
Performed a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the Version Control module, in which users were unable to create/append a revision to an existing label for a sub-user.
Implemented a code fix to version 22.3 relating to a use-case error in the Version Control module in which the user was getting empty error pop-ups under the ALM management screen for a sub-user, not displaying the ALM items.
Performed a code fix to version 23.1 relating to a use-case error affecting the nCino module with a job deployment issue.
Applied a code fix to version 23.1 relating to a use-case error affecting the nCino module for a CI job build getting failed.
Initiated a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the nCino module for a 'no modifications status' displayed for a version control BR job.
Integrated a code fix to version 23.1 affecting the Deployments and CI Jobs modules for a deployment issue running all test classes.
Performed a code fix to the nCino module in version 23.1 pertaining to Salesforce Orgs not showing as source orgs for nCino feature management deployments.
Applied a code fix to the nCino module in versions 22.3 and 23.1 pertaining to [arm-qan] no modification status displayed for version control BR job.
Added loggers to versions 22.3 and 23.1 to correct a use-case error in the Deployments module pertaining to a deployment bug occurring with multi packages and static resources.
A code fix was applied to the version control module in releases 22.3 and 23.1 concerning a use-case error for an EZ-Commit, where the user was unable to view the 'deleted components' tab for the commit template when unchecking the 'skip mappings' checkbox.
A code fix was implemented to versions 22.3 and 23.1 to correct an error with the deployments module due to a deployment initiated using org synchronization failing.
A code fix was applied to releases 22.3 and 23.1 due to a use-case error in which the registration date of the repository was not correct in the version control repository (created date in AutoRABIT).
A code fix was performed to versions 22.3 and 23.1 due to a data error in the version control module preventing ALM working items from loading.
A code fix was initiated for versions 22.3 and 23.1 due to a data error affecting the reports module, which occurred when executing a static code analysis (CodeScan) report.
A code fix was performed to version 23.1 in the version control module resulting from a data error on the commit history screen.
A code fix was implemented in versions 22.3 and 23.1 to the version control module related to a use-case error wherein the baseline job has modified the Salesforce folder structure in GitHub.
Loggers were added in the version 23.1 release due to a data error in the version control module causing duplicate commits to be created.
A code fix was implemented to the nCino module for versions 22.3 and 23.1 for a data error in which the records count was not being updated in the object sidebar for the version control baseline revision job.
Improvements have been made to VC Repo flow as well as to Salesforce Org flow. You can now run scans on a repo or an org to be tagged to the same project and run comparisons so that you have traceability across the scans. The comparison feature allows for every delta scanned to be compared with the baseline. Scans are run on the source, and the results are available in the Reports module. Users can trace the jobs run using the unique identifier. Click HERE to see a few points to note about these improvements.
Super Admin and the user currently logged in are disabled for ALL actions. They cannot be added, deleted, suspended, activated, deactivated, edited, or their roles delegated to other users. Super Admin is displayed at the top of the users' list for easy identification.
The Users module now displays the last login date and time of the users instead of the phone number, and the first and last names appear under the single Name column for better monitoring and tracking.
Super Admin can now enter the desired thread pool count while registering an ARM agent.
Customers can now request for Pendo and Full Story to be enabled or disabled for their instance. Simple toggle buttons to do this are added under the Product Analytics section on the Super User Accounts page. Only Super Admin will have access to this section.
In DataLoader,
The number of records that are going to be impacted by the specific operation (Extract, Insert, Update, Upsert, or Delete) is displayed as a message before the operation begins and also on the Summary screen as Records.
Filters have been added to differentiate between the mapped and unmapped fields when auto-map is selected.
Success and error count of records is displayed while the job is still in progress. Click to read more about these improvements for each of the operations.
QA Passed
22.3
Code Fix
Use Case
QA Passed
22.3 23.1
Code Fix
Use Case
Use Case
Data
Deployments
Org sync not completing
NA
No Code Fix - Added Loggers
Data
Dataloader
Corrected a spelling mistake in ARM steps.
23.1, 22.3
Code Fix
Use Case
Dataloader
Corrected data seeding error preventing upsert
23.1, 22.3
Code Fix
Use Case
nCino
On-premise testing: CI Job with template option failed due to "data and metadata retrieval failed” error
23.1, 22.3
Code Fix
Use Case
Use Case
Admin
Able to view empty role under permissions
22.3
Code Fix
Use Case
Data
nCino
Unable to create Feature Migration Template on Debt Schedule object
22.3, 23.1
Code Fix
Use Case
All Modules
Invalid Email ID
22.3, 23.1
Code Fix
Use Case
Enhancement
Admin
Branching baseline is not picking all components from production
22.3 & 23.1
Code Fix
Use Case
Deployments
Help with destructive change
22.3 & 23.1
Code Fix
Use Case
Version Control
Merge request is failing due to validation credentials
22.3 & 23.1
Code Fix
Use Case
CI Jobs, Deployments
Issues with a release – related to Feature Flag not automatically set: STANDARD_VALUE_SET_DELTA
22.3 & 23.1
Code Fix
Data
Version Control
Approval button is not visible after successful merge validation
22.3 & 23.1
Code Fix
Data
A code fix was applied to the nCino module of versions 22.3 and 23.1 due to a use-case scenario during dataset creation with saving only user info in Json that is relevant to current dataset.
A code fix was applied to the Version Control module of versions 22.3 and 23.1 due to a use-case error with an AR merge failing.
A code fix was applied to the Version Control module of versions 22.3 and 23.1 due to a use-case error in which the incorrect removal of Custom Application type in package.xml on EZ-Commit via AR occurred.
A code fix was applied to the Version Control module of versions 22.3 and 23.1 in which two external pull request issues were occurring.
Applied a code fix to versions 22.3 and 23.1 related to the Deployments module for a use-case error with previous deployment label 'add members' option not working.
Added loggers to version 22.3 affecting the Version Control module due to a use-case error with user roles missing.
Added loggers to version 22.3 affecting the CI Jobs module resulting from a use-case with automated package generation CI job AR server exception error.
Implemented a flow center change to versions 22.3 and 23.1 for the Dataloader module due to a use-case error with the download button not working.
Issued a code fix to versions 22.3 and 23.1 for a use-case error in the Version Control module with a custom label translation file.
Performed a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the Deployments module concerning bugs in deployment with multi-packages and static resource.
Applied a code fix to version 22.3 resulting from a use-case error affecting Dataloader returning an 'invalid cross reference id' error for ProcessInput and ProcessingInputCondition objects.
Performed a code fix to version 23.1 relating to a use-case error to the Version Control module with users unable to perform new pull request commit due to commit template permission.
Performed a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the Version Control module, in which users were unable to create/append a revision to an existing label for a sub-user.
Implemented a code fix to version 22.3 relating to a use-case error in the Version Control module in which the user was getting empty error pop-ups under the ALM management screen for a sub-user, not displaying the ALM items.
Initiated a code fix to versions 22.3 and 23.1 relating to a use-case error affecting the nCino module for a 'no modifications status' displayed for a version control BR job.
Added loggers to versions 22.3 and 23.1 to correct a use-case error in the Deployments module pertaining to a deployment bug occurring with multi packages and static resources.
A code fix was implemented to versions 22.3 and 23.1 to correct an error with the Deployments module due to a deployment initiated using Org Synchronization failing.
A code fix was applied to releases 22.3 and 23.1 due to a use-case error in which the registration date of the repository was not correct in the version control repository (created date in AutoRABIT).
A code fix was performed to versions 22.3 and 23.1 due to a data error in the version control module preventing ALM working items from loading.
A code fix was initiated to versions 22.3 and 23.1 due to a data error affecting the reports module, in which a user was getting an error message when executing a static code analysis (CodeScan) report.
A code fix was applied to version 22.3 in the version control module pertaining to a use-case error with changes not getting fetched via autodraft after reverting a commit.
A code fix was implemented in versions 22.3 and 23.1 to the version control module related to a use-case error wherein the baseline job has modified the Salesforce folder structure in GitHub.
A code fix was integrated to the version control module in version 22.3 after a data error caused by a feature template migration issue. The feature flag is MERGE_SKIP_AUTORESOLVE_CONFIGURATION_FILES.
A code fix to version 22.3 was implemented affecting all modules from a data error when setting up SFDX deployment.
A code fix was applied to the version control module in version 22.3 resulting from a use-case error with an ARM commit comment label error.
A code fix was implemented to the nCino module for versions 22.3 and 23.1 for a data error in which the records count was not being updated in the object sidebar for the version control baseline revision job.
Performed a code fix relating to a use-case error in on the Deployments module in which a deployment bug with multi packags and static resource was bugged.
Implemented a code fix related to a use-case error where the AutoRABIT deployment initiated using Org Synchronization fails. This error pertains to the Version Control module.
Implemented a code fix related to the CI Jobs module related to setting up SFDX deployment, with the Feature Flag:
RUN_PACKAGE_JOB_ENTIRE_BRANCH_78757
Regarding one ticket, 'Setting up SFDX Deployment': Only for the 'Create and Install an Unlocked/Managed Package Version from a Version Control Branch' CI, type in the CI Job configuration. When selecting the 'Trigger build on commit' option, we have hidden the 'Process commit revision received via hook only' sub-option. This change will be incorporated into our documentation. Further details are available in the ticket itself.
Implemented a code fix related to the nCino module error:
LLC_BI__Schedule_Section__c migration issue#1
Implemented a code fix related to an internal ticket in ARM, in which the user was not able to migrate related data using the Dataloader test environment setup module.
Implemented a code fix related to the Deployment module for an EBR Manual Asyncid XML Copy Automation error.
Performed a code fix affecting the Deployments module related to a use-case error with the client getting frequent page unresponsive errors in ARM. This also requires an update in our documentation. Further information is in the ticket.
Error: “Branching baseline is not picking all components from production": Based on the customer-confirmed downtime window, it was necessary to enable the "METADATA_API_TO_DX_CONVERSION" feature flag for this fix deployment.
Performed a code fix concerning the Admin module due to an error with a branching baseline not picking all components from production with feature flag error: ‘METADATA_API_TO_DX_CONVERSION’.
Error in CodeScan Plugin pop-up window where the user was unable to type text in Org key drop-down selection field, which required a code fix to the Admin module. (Internal ticket)
Performed a code fix related to a use-case error during Vlocity deployments showing "NoOrgFoung" after activation of LWC components. Fix applied to the CI Jobs and Deployment modules.
Code fix applied to SFDX module for the user receiving an error message showing login failed. Also related to CI Jobs, scratch org creation was being struck in progress and not able to be deleted.
Applied a code fix for the Version Control module related to a user being unable to select the ALM side, getting a JAVA error.
Initiated a code fix to the Deployments module related to an error during an EZ deployment from a single revision with profiles and comp-specific changes pulling all comps.
Executed a code fix to the Deployments module on a use-case error affecting an AR deployment initiated using Org Synchronization failing.
Applied a code fix related to the following use-case error: [Cijobs-DXModulePckagecreation] facing the "["An unexpected error occurred while preparing endpoint: null. Please contact Salesforce Support and provide the following error code: 795089467-5806 (-1215335089)"].
Initiated a code fix to the nCino module for a client use-case error concerning spread template issues.
Performed a code fix for a customer use-case scenario regarding an error related to an nCino CI job deployment issue.
Performed a code fix to the CI Jobs module related to an error message as login failed.
Performed a code fix on the CI Jobs module pertaining to Vlocity SFI components not compiling LWC on destination orgs when deploying via CI Jobs.
Performed a code fix related to the CI Jobs module for CI Job not starting according to schedule.
Performed a code fix related to the CI Jobs module to resolve an error related to setting up SFDX deployment and CI Job configuration.
Performed a code fix to the nCino module for an error in which the screen template failed with a malformed query exception.
Performed a code fix related to a use-case error in the version control module pertaining to a commit showing a “no modification” error.
Performed a code fix related to a use-case error affecting the version control, CI jobs, and deployment modules caused by an error merging a commit from the dev environment to the INT environment.
Performed a code fix to the version control module resulting from a use-case error where the commit was incorrectly showing “no modification”.
Performed a code fix related to a data error pertaining to the version control module, when Jira integration stories redeploy post sandbox refresh.
Performed a code fix for a use-case error in the deployment module related to filter-based retrievals not working when applying the ‘created by,’ ‘modified by,’ ‘created date,’ and ‘modified date’ filters.
Performed a code fix related to a performance issue in the nCino module pertaining to Spread Template issues.
Fixed an error in the deployment module when ‘Run Specified Tests’ is selected from the Apex Test Level dropdown.
Rather than a code fix, a customer-specific utility was provided to address SSO login issues in the admin module. This particular utility only works in versions 22.3.9 or lower for one individual customer.
Fixed an error for CI Job module where ALM-enabled failed due to Unparsable date error.
Fixed an error concerning multiple CI Jobs failing due to data error.
Fixed an error related to the Deployment, CI Jobs, and Version Control modules occurring when merging a commit from dev environment to INT environment.
Fixed an error related to deployments getting frequent page unresponsive errors in ARM.
Fixed an error under the Admin module relating to being unable to select the revision number while creating the Tag.
Fixed an error for Create and Install Package CI job deployment failing if having multiple package directories on the branch.
Fixed an error under the Admin module, My Account >> Merge Settings: Not visible Border for "Notify All Criteria Overwrites To" field.
Fixed an error under the Admin module, which enabled Domain names to be visible in the inspect mode.
Fixed an error in the nCino module related to [ARM-QAN] attachments’ deployment Failed with Bulk API.
Fixed an error in the nCino module related to a Pricebook entry.
Fixed an error related to the nCino module with scheduled Job not showing up in UI after completion due to Deploy Status Not Updated.
Fixed an error related to the nCino module with a CI Job Edit not populating with scheduled time details.
Helped generate the reports for CI/CD pipelines for nCino reports.
Performed Jira integration story’s redeploy post-sandbox refresh in version control.
Fixed a specified metadata type is unsupported: [processflowmigration] error in CI Jobs.
Set up the SFDX Deployment in CI Jobs.
Fixed an error with a CI Job not identifying changes.
Fixed an error related to BHG with CI Job webhooks failing to trigger.
Performed nCino AR template updates.
Fixed an issue where Release labels are taking 30 minutes or more to be available for repository in Version control.
Fixed an issue where Merges are taking a long time to complete in version control.
Fixed an issue where components selected on review component pages were being repeated in the next category in Version Control.
Fixed an issue where same name should be reflected instead of Commit showing a different name in Bitbucket in Version Control.
Fixed an issue where JIRA ALM Filter mappings not working in My profile & Version Control.
Fixed an issue where the Login rate exceeded error on the Salesforce Integration user.
Fixed an issue where Backup to Version Control is not backing up Matching Rules in Salesforce in CI jobs.
Fixed an issue where the shared server with common DB creates another customer weekly report in another server.
Fixed an issue where Custom field property didn’t deploy in CI Jobs and Deployment.
Fixed an issue where Diff report is not generated in New Deployment Module.
Fixed an issue where Unsupported metadata template execution is failing in Sandbox Refresh in Environment Provisioning module.
Enhanced DataLoader uber jar upgrade to 58.0.3.
Fixed an issue where we are facing Record Configuration Time Out in nCino.
Enhanced UI in Post Deployment activities result page in CI Job – nCino.
Enhanced the View details page not being visible unless post-deployment activities are completed – nCino.
Fixed an issue with nCino where user created a Feature deployment task, but the jobs were stuck the queue.
Introduced a new feature in DataLoader called Hard Delete which can be used to delete the data completely and permanently instead of sending it to the Recycle Bin of the org.
Fixed an issue where CI Job build history was not displaying the results and throwing a blank page instead.
Fixed a UI bug where Abort option for CI job was displaying even after the build was successful.
Fixed an issue where duplicate ALM Commit entries were Displaying while performing ALM Commit with Vlocity repository.
Fixed an issue where the CI edit configuration screen was taking longer to load than expected before throwing Page Unresponsive alert.
Fixed an issue with DataLoader Pro where user created a new job and applied filter, but the source and destination orgs are taken from history page.
Fixed an issue with DataLoader where Insert operation bulk API selection was resulting in console error message serializeToString.
Fixed an issue where Vlocity metadata components were getting expanded on the Finish page.
Fixed an issue where user was trying to create an connect an Active Directory but it kept failing (#73582).
Fixed a UI bug where Deployment Failed line was displayed twice in the logs for failed deployments (internal ticket).
Fixed an issue where admin was unable to release a user from a team (internal ticket).
Fixed an issue where Null Values were displayed on the ALM Labels screen as well as the ALM Details tab on the respective ALM Commit Label Details screen (internal ticket).
Fixed an issue where selected files for DX Commits were not displayed in the File Changes tab, and after the commit it was showing as No Modifications (internal ticket).
Fixed an issue where BackUp to Version Control CI Job was failing due to too many retrieval error messages even though the Bulk API option was enabled (#72181).
Fixed an issue where while performing any commit, Pull Request enabled CI Job was triggering as expected; but its Build and Deployment status was not added in the Comments in Bitbucket (#72811).
Fixed an issue where EZ-Commits were stuck with In-progress status for a few hours before failing. But the commit revisions were generated at the repository level and updated in ARM database (#72817).
Fixed an issue where the Git author was overridden by ARM (#71393).
Fixed an issue with DataLoader where user was unable to create an Update job because the functionality prompoted user to select the Required field within the Mapping Fields (#73515).
Fixed an issue with DataLoader where user was getting a script error in the console while editing an existing old job (internal ticket).
Fixed an issue where Destructive commit for DX was not working as expected for Documents, Reports, and Dashboards types (internal ticket).
Fixed an issue where the Layout file was not displayed in the Review Artifact screen after resolving the layout duplicates (internal ticket).
Fixed an issue where 4 CI jobs were running parallelly even though the parallel process limit was 1 on the external agent (internal ticket).
Fixed an issue where user was performing CI jobs for Validate and Deploy for a successful commit, but only validation was performed but not the deployment (#72751).
Fixed an issue where CI job deployment was failing because the build was picking duplicate Layout values (#71214).
Fixed an issue where Branching Baseline was not picking all the components from production (#70720).
Fixed an issue with nCino where CI jobs that used a Deployment from Version Control were failing when the build was triggered (#71914).
Improved the New Merge screen by adding Layouts text in the Skip Flow /Profile/ Perm.Set Access-Setting Duplicity Check option (internal ticket).
Fixed a UI bug where SF Org Test Connection notification message was displayed on an unrelated module (internal ticket).
Removed the option to sign up for a 30-day Salesforce trial while registering a DevHub as the trial offer is no longer applicable (internal ticket).
Fixed an issue where CI job to generate Code Coverage Report was not reflected in the org or in the e-mail notification (#72042).
Fixed an issue where merge status is displayed as completed but no revision is generated, and the merge is not available in the UAT branch (#71266).
Enhanced DataLoader by adding the ability to field mapping through the lookup fields (#58480).
Fixed an issue with DataLoader where while running an Extract job on the PUBLISHER object, the job was failing with the following error Publisher: column id is not supported in ORDER BY clause (#71303).
Enhanced the nCino filter criteria by adding the ability to search and filter labels using the whole or partial name (#71826).
Enhanced ARM by using known vulnerable components through the DataTables 1.10.12 plugin for advanced data table functionalities such as sorting, filtering, pagination, and more. This allows users to easily display and manipulate large sets of data on their web pages in a user-friendly manner (internal ticket).
Fixed an issue with Prevalidation Merge where users were unable to deploy the ApexClass Tests related to ApexClasses and Apex Triggers (internal ticket).
Fixed a UI bug where the date column in the EZ-Commit Weekly report was displaying incorrect values (internal ticket).
Fixed an issue where user could not disable the Smart Commits-Sync option for a repository branch in the VC repos section (#70854).
Improved the New Merge screen by removing the Validate Deployment option from the UI if Vlocity is selected (#70993).
Enhanced the Credentials module by adding SSH Cetificate option for Git Authentication (#67725).
Improved Release label creation by requiring at least two revisions to be selected (internal ticket).
Fixed an issue where Classic SF Org URL with a slash at the end of the URL redirects to the 400 error page, and for a Lightning SF Org URL without a slash gives an OAuth Authentication Failed error message (internal ticket).
Fixed an issue with nCino where user was getting a NullPointerException on Saving Permissions using Bulk Assignment (internal ticket).
Fixed an issue with CI Jobs where all the scheduled timings were not displayed in the Preview & Save page (internal ticket).
Fixed an issue with Dataloader where user was able to upload a 900 MB file despite the limit being 100 MB, causing the process to hang (internal ticket).
Fixed an issue with Dataloader where sever crashed after user performed an Extract operation from an SF org which had Account Object with 2 million records (internal ticket).
Fixed an issue where prevalidation merge failed with empty metadata package even though there were changes in File Diff (#32256).
Fixed an issue where entire ARM application was down temporarily (#70658).
Fixed an issue where Merge was auto-rejected due to an empty package because the metadata folder path not being specified under branch settings (#69788).
Fixed an issue where user was using the Bulk Assignment feature to assign Sandbox permissions on the Permissions page but encountered the following error: Java.lang.NullPointerException (#70868).
Fixed an issue where users weren't receiving SCA reports by email even though the reports were running (#70751).
Fixed an issue where while performing new EZ-Commit, user edited one line using review artifact option but Diff did not capture the same (#70270).
Fixed an issue where if CI Jobs were added in a queue with Scheduled jobs, then not all jobs were displayed in the queue (internal ticket).
Fixed an issue where existing revision file related delta still existed in agent even after uploading to rabitserver (internal ticket).
Fixed an issue where release label creation was failing when user tried to create package manifest and aborted and refreshed the label for DX repo (internal ticket).
Fixed an issue where Super admin user was getting a blank popup screen while trying to click on the Register Agent button from the Pool Mgmt screen (internal ticket).
Fixed an issue where user merged a new component using a single revision merge but the merge missed to perform a CodeScan analysis (#70391).
Fixed an issue where user was unable to commit the destructive Email Template files as part of commit in SFDX format and getting auto failure (#70351).
Fixed a UI issue where OK button to reject an EZ-Merge was not working (#70041).
Fixed an issue where a field was available in the package but still Validation was throwing error that the field was missing (#69831).
Fixed an issue with DataLoader where multiple jobs were not processing parallelly when user loaded a large number of jobs to the queue (#62559).
Fixed an issue with nCino where user created more than 100 jobs with sub-user but was still getting the following error: No jobs exist to load (#69831).
Fixed an issue where Release Label artifact was not displaying metadata types in the Destructive changes tab for DX repos, but was working as expected for non-DX repos (internal ticket).
Fixed an issue where new jobs are getting added to the queue but not getting triggered, and later throwing NullPointer Exception (internal ticket).
Fixed an issue where Rollback button was not enabled for the first job if that job is came from a queued list (internal ticket).
Fixed an issue where ALM CI Job and Release artifact execution was happening at the same time, and the CI Job build was failing (internal ticket).
Fixed an issue where an empty pop-up was displayed when user tried to edit the existing CI jobs label for Sub-User (internal ticket).
Fixed an issue where if Validate only CI job came from the queue, then direct deployment was executing for that job instead of validate deployment (internal ticket).
Fixed an issue where duplicates revisions were being added to the list while creating the release label when user unselected and reselected the same revisions. (internal ticket).
Fixed an issue where Vlocity revisions were not displaying while user was trying to edit a release label (internal ticket).
Enhanced the Release Label creation page by adding options to the Vlocity label type which were only available for Salesforce revisions before (internal ticket).
Fixed an issue where duplicate entries were created in different lines during the Merge process and user wasn't able to remove the duplicate field without clearing the layout tag as well (#68012).
Fixed an issue where the baseline branch is not displayed during Static Code Analysis job creation if the branch name contains spaces in the Reports module (#69614).
Enhanced deployment in ARM by providing a new option Rollback on error in merge pre-validation. This checkbox allows users to choose if deployment should proceed with remaining components in case of errors (#47794).
Fixed an issue with nCino where CI job filter changes on templates were not taking effect after saving (#66956).
Fixed an issue where user created a baseline revision job with the Automation Sanity repo and triggered the build but it failed without any error (internal ticket).
Fixed an issue where user could not fetch the ApexClass Tests related to ApexTriggers upon selecting Run Tests Based On Changes as an option (internal ticket).
Fixed an issue where error 405 in the build and deployment logs didn't display further details in the UI log (internal ticket).
Fixed a UI bug where dropdown selection in Reports > CodeCoverage Reports was not working after refreshing the page (internal ticket).
Fixed an issue where Release Label artifact was not displaying metadata types in the Destructive changes tab for DX repos, but was working as expected for non-DX repos (internal ticket).
Fixed an issue where user was unable to revert the commit if a previously reverted commit was deleted while in Conflict state (internal ticket).
Fixed an issue where user was trying to commit System Permissions which were enabled in Salesforce org, but while performing EZ-Commit, file Diff is not getting generated and the system permissions are not getting committed (#67826).
Fixed an issue where ALM label merge option was not working in EZ-Merge feature. This happened only when the ALM Label contained / in it (#67818).
Fixed an issue where EZ-Merge was failing with NullPointerException (#67502).
Fixed a recurring issue of ARM overwriting the Salesforce Org - Default Apex Test Class Configuration by adding a checkbox Do you want us to update the test classes? (#65565).
Fixed an issue where Revert commits were failing without any error messages (#68771).
Fixed an issue where user created a Release label with multiple commit revisions, each with dependency components, but the revisions were not displaying in the right order in UI (#68939).
Fixed a UI bug where when user unchecked Validate deployment option in EZ-Merge, the Run destructive changes checkbox was hidden (#68750).
Fixed an issue where when user had files in conflicted state, selecting the ALL checkbox was not working and user had to click on each file to resolve conflicts (#65680).
Fixed an issue where the NPM repository Access Key wasn't saving after clicking Save, causing the Local Compilation to fail (internal ticket).
Fixed an issue where comments lines were not executed in Metadata when there were spaces in the comment line in merge flow (internal ticket).
Fixed an issue where an empty popup screen is displayed while resolving conflicts in case of malformed file (internal ticket).
Fixed an issue where improper validation message is displayed after clicking on Resolve Duplicates without selecting any files to resolve (internal ticket).
Fixed an issue where SSO user's org was not deleted from the Security-Context XML (internal ticket).
Fixed an issue where the API Token status was marked as Never Accessed, despite the API being in use already (internal ticket).
Fixed an issue where user was unable to register a branch even though Test Connection was successful (#67023).
Fixed an issue where ARM wasn't fetching the ApexClass Tests related to ApexTriggers upon selecting Run Tests Based On Changes option (#67503).
Fixed an issue where triggered CI jobs were taking too long to build, and also slowing down ARM altogether (#66846).
Fixed an issue where if the file name contained spaces, Commit Validation via VS Code plugin was unable to detect the file (#63518).
Fixed an issue where Search & Substitute was not updating the value for a custom label in the SF org (#66809).
Fixed an issue where there was a discrepancy between the changes captured in the ARM Diff and the repos in BitBucket (#60596).
Fixed an issue where the SF org URL is not displaying the updated one under Profile (#67718).
Fixed an issue with nCino where CI job filter changes on templates are not reflecting after saving (#66956).
Fixed an issue with Dataloader Pro where user tried to migrate Account Object Data with Attachments Object, but the logs verify that there is a Null Pointer Exception. (internal ticket).
Improved nCino by adding additional loggers for Branching baseline for user to view the status in the UI (internal ticket).
Fixed an issue where user was unable to filter while trying to select a job which had spaces in the job name (internal ticket).
Fixed an issue where scheduled CI jobs were getting queued or not getting triggered as per schedule (#57749).
Fixed an issue where Quick action was not picked for destructive changes (#65058).
Fixed an issue where while running the scan from ARM for the version control branches are failing because .java files were present in the current repository (#63234).
Fixed an issue where user using non-SFDX repo with Custom API enabled failed to pick the changes in the CI job (#64497).
Fixed an issue where Release label displayed commit revisions older than 30 days even when the No. of days filter was set as 30 (#63845).
Fixed an issue where a user had trouble creating artifact for a release label (#65557).
Fixed an issue where there are Vlocity components in Merge Validation, and the validation deployment should bypass and process the merge; instead it is Auto-rejecting as criteria were not met (#65625).
Fixed an issue with Dataloader where a job completes with No records status whenever attachment and content version are selected as child objects in the parent cccount object (#66655).
Fixed an issue with nCino where CI job build status is displayed as Completed for a failed job (#64479).
Fixed an issue with nCino where attachements to nFORMS__Form_Template__c failed to get deployed (#65242).
Fixed an issue where user was unable to initiate static code analysis on a Salesforce Org (#51559).
Fixed an issue with New EZ- Commit where while using Custom YAML file the page was taking much longer to load than usual (#65742).
Fixed an issue where Merge was happening on incorrect files (#64485).
Fixed an issue where for DX repo, Custom field destructive Deployment was failing with the error Package generation without a valid package directory cannot be processed (internal ticket).
Fixed an issue from the VS Code where Static Code Analysis report was not getting executed on the selected files and report generated (internal ticket).
Fixed an issue where Release Label creation with SVN Repo was not successful, and throwing the following errors (internal ticket):
Supplied AttributeValue is empty, must contain exactly one of the supported datatypes (Service: AmazonDynamoDBv2; Status Code: 400; Error Code: ValidationException; Request ID: a59c77cb-67ad-4a58-80b4-364feb5a4d6c; Proxy: null)
No Version Control Mappings found for Repo: {} and Branch: {}. Please update it in My Profile
Fixed an issue where Merge was not Auto-rejected after UI logs displayed Mock deployment is failed, so auto rejecting the merge (internal ticket).
Fixed an issue where Revision in Vlocity release label was not getting selected after you clicked save (internal ticket).
Fixed an issue with nCino where user was getting an exception while creating a CI job, and user was selecting the same VC Repo/Branch for multiple times (internal ticket).
Fixed an issue where Merge Request XML file was conflicting with an error No conflict data found for this block (#65164).
Fixed an issue where Release label failed while creating the artifact (#64491).
Fixed an issue where Prevalidation EZ-Commit shows that Diff does not exist even when there are changes. If user tries multiple times, then Diff is displayed sometimes (#64612).
Fixed an issue where user was unable to merge the code from one branch to another branch. (#65570).
Fixed an issue where Ignore Missing Visibility settings not working on EZ-Merge validation (#65162).
Fixed an issue where user was loading multiple DataLoader jobs but it was not processing parallelly (#62559).
Fixed a UI bug in nCino where the header in template details section was missing in Feature Deployment (internal ticket).
Fixed an issue with nCino where Deployment Logs were not displayed when the CI Job failed (internal ticket).
Fixed an issue where SCA report Failed to run using the Codescan Plugin with the following Salesforce error 384187622-16951 (-673032061) (#61676).
Fixed an issue where after upgrading to ARM version 22.3 user was unable to approve EZ-Commits that were pending approval in the 22.2 (#64094).
Fixed an issue where user was trying to resolve a conflict in EZ-Merge but was getting a message on the UI that there are no conflicts (#64185).
Fixed an issue where Branching Baseline job does not delete files in static resources sub directories even though the user has selected the Delete existing metadata and commit new changes option (#64150).
Fixed an issue where user was unable to retrieve MutingPermissionSet using the SFDX repository (#64141).
Fixed an issue where the Release Label failed while creating the artifact (#64491).
Fixed an issue where Sharing Rule Set metadata type was found in the Deployment module but not in the Version Control module (#65060).
Fixed an issue where the user performed a merge and approved both level 1 and level 2 reviews but was unable to approve the merge (#65091).
Fixed an issue where errors were occuring while performing Delete Org (internal ticket).
Fixed an issue where for Build only job source from VC with DX repo, if Master Details Object Change is included in the build, we're getting No Modifications even if changes exist (internal ticket).
Fixed an issue with Review Artifact where similar custom fields from different objects were not populating correctly and switching to other fields (#63676).
Fixed an issue where multiple fields of the respective custom objects were getting selected parallelly while performing edit or save or exit operations on the Review Artifact screen (internal ticket).
Enhanced ARM by adding an option for multiple ARM instances to share a single database cluster (internal ticket).
Fixed an issue where users weren't receiving emails after setting up Mail Settings (#55070).
Fixed an issue where there was a discrepancy between EZ-Commit and Commit templates while retrieving Email Template metadata members (#61696).
Fixed an issue where Merge Labels were taking much longer than expected (#62625).
Fixed an issue where user tried to commit the changes without validation and UI displayed an error Another commit is in progress (#61930).
Fixed a UI bug where there was a discrepancy in the timestamp displayed for a commit in the Commits History page (#61672).
Fixed an issue where Merge was not auto-rejected when validation criteria was not met (#62287).
Enhanced nCino by allowing users to deploy nCino CI build to multiple target sandboxes (#41763).
Fixed a UI bug where incorrect notification was displayed in certain components pages when template was created using one org and was used by another org (internal ticket).
Fixed an issue where Baseline Managed Package Changes option was not displayed on the UI when navigating from Package xml to select manually (internal ticket).
Fixed an issue where there was a discrepancy between the Attachments Records Success/Failure Count and the Retrieved Count when BULK API was enabled for Deployment (internal ticket).
Fixed an issue where Release Artifact execution was failing when rabit home did not exist with an external agent (internal ticket).
Fixed a UI bug on the Profile screen where the expand option for the My Projects and My Roles sections was not working (internal ticket).
Fixed an issue where triggering Data Retention for Audit Tables was throwing the following error: Unable to execute HTTP request: Read timed out (internal ticket).
Fixed an issue where extra characters are seen in the Fetch Commit History results while creating a Release Label with Vlocity label type (internal ticket).
Fixed an issue where user was unable to delete Apex test class on the SF Org Management page (internal ticket).
Enhanced nCino by introducing New Spreads Schedule tile in the Feature Creation screen (internal ticket).
Fixed an issue where if the fields did not load for Applied Mappings during deployment, no error was thrown by the application (internal ticket).
Fixed an issue where user was customer trying to register a Salesforce Org with Custom URL but it was failing with an error (#62192).
Fixed an issue where user user uploaded a YAML file to retrieve the Vlocity components but ALL metadata types were retrieved and displayed (#61181).
Fixed an issue where the same merge could be approved and rejected by different users simultaneously (#60859).
Fixed an issue where branch creation was faileing for sub-users in the EZ-Commit screen for Non-DX Repo (internal ticket).
Fixed an issue where Null Pointer was seen in Create Branch in EZ-Commit flow (internal ticket).
Fixed an issue where all credentials were listed twice in the Credentials dropdown in Create Branch in EZ-Commit flow (internal ticket).
Fixed an issue where branch creation was failing for sub-users in VC repos when the credential scope was private while Admin credentials were fetched (internal ticket).
Fixed an issue where user was unable to delete the Apex Test class under the SF org Apex default config (internal ticket).
Fixed an issue where the Add manually checkbox under Apex class config was selected by default (internal ticket).
Fixed an issue with nCino where user created a feature Deployment for Credit memo template with attachments, but Attachments Objects Data was not fetched, and the deployment failed with the following error: Data file not fetched for object: Attachment (internal ticket).
Fixed an issue with nCino where Standard Features were not loaded in the Feature Management page (internal ticket).
Fixed an issue where Create Artifact was not working as expected while using Release Label (#61607).
Fixed an issue where user was performing an EZ-Commit with Review Artifact option and download the .zip file to make some changes, but was unable to upload it afterwards (#61751).
Fixed an issue where meta.xml file was not deleted from the repository after committing the destructive changes (#61736).
Fixed an issue where File Diff was empty in case of modified Uploaded via Review Artifact in PV Commit Flow (internal ticket).
Fixed an issue where Review Artifact Tree was not responding after uploading the modified file in Commit Flow (internal ticket).
Fixed an issue where User Permissions and Ip Ranges are completly removed from the branch after commiting the Permission Sets and Profiles (internal ticket).
Fixed an issue where Super Admin was getting an error while trying to activate newly signed up users (internal ticket).
Fixed an issue where Post Destruct fields were also added to Pre Destruct despite the user setting it to post (#61162).
Fixed an issue where user set the Max depth value as '0' under Vlocity Configuration Settings but it was retrieving all level dependancy components (#57501).
Fixed an issue with DataLoader where the Credit Memo Template migration was not deploying after user upgraded their instance (#57676).
Fixed an issue where user selected Custom Metadata members (records), but EZ-Commit was failing to generate File Diff with Null error (#59709).
Fixed an issue where Merge was taking longer than usual, and then failing with Null Exception (#60757).
Fixed an issue where EZ-Commits and EZ-Merges were taking much longer than usual (#58098).
Fixed an issue where user performed a merge and sent it for approval, but it was not available under the Commit history tab (#53759).
Fixed an issue where user initiated the prevalidation commit by enabling the destructive type but the deployment failed with an error null at Diff (#59919).
Fixed an issue where Validate Deploy failed in QuickMerge and displayed the following message: This folder unique name already exists for this folder type or has been previously used. Please choose a different name (internal ticket).
Fixed an issue where CI job wasn't considering the metadata changes, so the destructive changes were not being prepared or displayed on the build. (internal ticket).
Fixed an issue where user couldn't create a managed package with the selected ancestor (#59044).
Fixed an issue where CI Job was occasionally failing with the error BUILD FAILED (#57647).
Fixed an issue where CI job was taking the last modified user name if trigger through API instated of taking API token user (#55438).
Salesforce API version 57 (Beta support) is upgraded. The label is modified throughout ARM application including DataLoader and nCino (internal ticket).
Fixed an issue where nCino CI job was stuck in Build Success status for more than a week (#59040).
Fixed an issue where user was trying to deploy RBC (nCino Screens) and the deployment was failing for some of the objects, but there were no error messages shown on the UI (#58044).
Fixed an issue where user was using SSH credential in AutoRABIT but it was throwing the following error: Invalid Private Key (#59244).
Fixed an issue where user has created a Commit label but it was not available while trying to perform an EZ-Merge (#55176).
Fixed an issue where user was not getting file Diff to commit the previously validated commit label and getting an error in the Diff (#59114).
Fixed an issue where user could not create an xml package for deployment because artifact creation and package manifest preparation were failing with an invalid credentials error (#59402).
Fixed an issue where user was trying to perform single revision merge but validation deployment was failing with the following error Metadata package is empty (#59028).
Fixed an issue where when there are special characters in Layout metadata then the user was not able to add it manually in Skip Members section (#58998).
Fixed an issue where user wanted to choose commit revision in a release label based on its comment but if the comment was not in text, it was not completely visible in the UI (#59014).
Fixed a UI bug where an incorrect validation message was seen while adding Skip Members manually (internal ticket).
Fixed an issue where the selected tab checkbox in the metadata components page in the EZ-Commit was not functioning as expected (internal ticket).
Fixed an issue where the EZ-Commit validation screen was displaying incorrect notification when name of the template was empty (internal ticket).
Fixed a recurring issue where Commits and Merges were slowing down at a particular step, and EZ-Merge was failing with an error at commit phase (#51268).
Fixed an issue where while performing destructive changes in EZ-Commit, it was creating package.xml in root path folder in SFDX structure (#57868).
Fixed a UI bug on CI List and CI Results pages where when pagination was changed, the first 25 records were repeated (internal ticket).
Fixed an UI bug where the LastUsedDate column was not displayed in the Branch Table (internal ticket).
Fixed an issue with Branching Baseline where the developers were migrating the changes from dev branch to INT, but Diff was showing 100% addition which is incorrect (#58478).
Fixed an issue where generating Diff for a Commit Label was taking much longer than expected (#55220).
Fixed an issue where Code coverage job was running 4 hours earlier than scheduled every time services were restarted (#54837).
Fixed an issue where SFDX scratch org was failing during data deployment but without any errors on UI, and the logs did not capture the failure either (#54837).
Fixed an issue where CheckMarx is executed successfully, but when trying to open the file user is the following error popup: Result file not exists (internal ticket).
Fixed an issue where ActionCall and Decision Nodes were not shown in the Duplicate Resolving screen (internal ticket).
Fixed an issue where EZ-Commit Diff was taking approximately 4 hours while Refactoring CustomField, which is much longer than expected (#56650).
Fixed an issue where ExternalCredential metadata type was not getting excluded even when user added it in the excluded lists in CI Configuration (internal ticket).
Fixed an issue where after triggering Branching baseline, standard value set metadata type was getting displayed under the deleted components through Autodraft for Non-DX repo (internal ticket).
Fixed an issue where Destructive Components are not seen in case of PV-DX-Destructive Merge for Report metadata type. Instead, it displaying a message: Package is empty (internal ticket).
Fixed an issue where Deployment was failing with certain Permission set metadatatypes that were not selected (internal ticket).
Fixed an issue where non-admin users were unable to select Branch Type while trying to create a new branch from New EZ-Commit Branch (#57732).
Fixed an issue where CI jobs are failing intermittently with the following error: Getting access token failed from refresh tokenHTTP/1.1 400 Bad Request (#57371).
Fixed an issue where user was trying to deploy only the Documents from the branch to Org, but deployment failed and Asynch ID is not generating (#57263).
Fixed an issue where user was trying to deploy login hours. First they merged it to target branch, then once CI job triggers login hours are not getting deployed to target org (#57359).
Fixed multiple issues where user was having trouble creating new package version from previous ancestor version (#55707).
Fixed an issue where Merge is failing with the following error: failed to push some refs to 'https://github.com/salesforce-align/SFDX.git' (#55939).
Fixed an issue where the Standard Field Account.name is displayed in the deleted components list (#57396).
Fixed an issue where the prevalidation commit failed at delta stage (#55763).
Fixed an issue where user was unable to create commit label for the same repository second time, and branches were not displayed (internal ticket).
Fixed an issue where Provar jobs were failing due to incorrect files being copied from customer repository branch to Provar project directory (#56662).
Fixed an issue where user triggered a CI Job but it deployed with many more components than expected (#46983).
Fixed an issue where user was creating an EZ-Commit, mapping the ALM Project (VersionOne) but received the following error: JSONObject["Assets"] is not a string (#57238).
Fixed an issue where user was performing CI jobs for Validate and Deploy for a successful commit, but only validation was performed but not the deployment (#72751).
Fixed an issue where CI job deployment was failing because the build was picking duplicate Layout values (#71214).
Fixed an issue where Branching Baseline was not picking all the components from production (#70720).
Fixed an issue with nCino where CI jobs that used a Deployment from Version Control were failing when the build was triggered (#71914).
Improved the New Merge screen by adding Layouts text in the Skip Flow /Profile/ Perm.Set Access-Setting Duplicity Check option (internal ticket).
Fixed a UI bug where SF Org Test Connection notification message was displayed on an unrelated module (internal ticket).
Removed the option to sign up for a 30-day Salesforce trial while registering a DevHub as the trial offer is no longer applicable (internal ticket).
Fixed an issue where CI job to generate Code Coverage Report was not reflected in the org or in the e-mail notification (#72042).
Fixed an issue where merge status is displayed as completed but no revision is generated, and the merge is not available in the UAT branch (#71266).
Enhanced DataLoader by adding the ability to field mapping through the lookup fields (#58480).
Fixed an issue with DataLoader where while running an Extract job on the PUBLISHER object, the job was failing with the following error Publisher: column id is not supported in ORDER BY clause (#71303).
Enhanced the nCino filter criteria by adding the ability to search and filter labels using the whole or partial name (#71826).
Enhanced ARM by using known vulnerable components through the DataTables 1.10.12 plugin for advanced data table functionalities such as sorting, filtering, pagination, and more. This allows users to easily display and manipulate large sets of data on their web pages in a user-friendly manner (internal ticket).
Fixed an issue with Prevalidation Merge where users were unable to deploy the ApexClass Tests related to ApexClasses and Apex Triggers (internal ticket).
Fixed a UI bug where the date column in the EZ-Commit Weekly report was displaying incorrect values (internal ticket).
Fixed an issue where user could not disable the Smart Commits-Sync option for a repository branch in the VC repos section (#70854).
Improved the New Merge screen by removing the Validate Deployment option from the UI if Vlocity is selected (#70993).
Enhanced the Credentials module by adding SSH Cetificate option for Git Authentication (#67725).
Improved Release label creation by requiring at least two revisions to be selected (internal ticket).
Fixed an issue where Classic SF Org URL with a slash at the end of the URL redirects to the 400 error page, and for a Lightning SF Org URL without a slash gives an OAuth Authentication Failed error message (internal ticket).
Fixed an issue with nCino where user was getting a NullPointerException on Saving Permissions using Bulk Assignment (internal ticket).
Fixed an issue with CI Jobs where all the scheduled timings were not displayed in the Preview & Save page (internal ticket).
Fixed an issue with Dataloader where user was able to upload a 900 MB file despite the limit being 100 MB, causing the process to hang (internal ticket).
Fixed an issue with Dataloader where sever crashed after user performed an Extract operation from an SF org which had Account Object with 2 million records (internal ticket).
Fixed an issue where prevalidation merge failed with empty metadata package even though there were changes in File Diff (#32256).
Fixed an issue where entire ARM application was down temporarily (#70658).
Fixed an issue where Merge was auto-rejected due to an empty package because the metadata folder path not being specified under branch settings (#69788).
Fixed an issue where user was using the Bulk Assignment feature to assign Sandbox permissions on the Permissions page but encountered the following error: Java.lang.NullPointerException (#70868).
Fixed an issue where users weren't receiving SCA reports by email even though the reports were running (#70751).
Fixed an issue where while performing new EZ-Commit, user edited one line using review artifact option but Diff did not capture the same (#70270).
Fixed an issue where if CI Jobs were added in a queue with Scheduled jobs, then not all jobs were displayed in the queue (internal ticket).
Fixed an issue where existing revision file related delta still existed in agent even after uploading to rabitserver (internal ticket).
Fixed an issue where release label creation was failing when user tried to create package manifest and aborted and refreshed the label for DX repo (internal ticket).
Fixed an issue where Super admin user was getting a blank popup screen while trying to click on the Register Agent button from the Pool Mgmt screen (internal ticket).
Fixed an issue where user was unable to register a branch even though Test Connection was successful (#67023).
Fixed an issue where ARM wasn't fetching the ApexClass Tests related to ApexTriggers upon selecting Run Tests Based On Changes option (#67503).
Fixed an issue where triggered CI jobs were taking too long to build, and also slowing down ARM altogether (#66846).
Fixed an issue where if the file name contained spaces, Commit Validation via VS Code plugin was unable to detect the file (#63518).
Fixed an issue where Search & Substitute was not updating the value for a custom label in the SF org (#66809).
Fixed an issue where there was a discrepancy between the changes captured in the ARM Diff and the repos in BitBucket (#60596).
Fixed an issue where the SF org URL is not displaying the updated one under Profile (#67718).
Fixed an issue with nCino where CI job filter changes on templates are not reflecting after saving (#66956).
Fixed an issue with Dataloader Pro where user tried to migrate Account Object Data with Attachments Object, but the logs verify that there is a Null Pointer Exception. (internal ticket).
Improved nCino by adding additional loggers for Branching baseline for user to view the status in the UI (internal ticket).
Fixed an issue where user was unable to filter while trying to select a job which had spaces in the job name (internal ticket).
Fixed an issue where SCA report Failed to run using the Codescan Plugin with the following Salesforce error 384187622-16951 (-673032061) (#61676).
Fixed an issue where after upgrading to ARM version 22.3 user was unable to approve EZ-Commits that were pending approval in the 22.2 (#64094).
Fixed an issue where user was trying to resolve a conflict in EZ-Merge but was getting a message on the UI that there are no conflicts (#64185).
Fixed an issue where Branching Baseline job does not delete files in static resources sub directories even though the user has selected the Delete existing metadata and commit new changes option (#64150).
Fixed an issue where user was unable to retrieve MutingPermissionSet using the SFDX repository (#64141).
Fixed an issue where the Release Label failed while creating the artifact (#64491).
Fixed an issue where Sharing Rule Set metadata type was found in the Deployment module but not in the Version Control module (#65060).
Fixed an issue where the user performed a merge and approved both level 1 and level 2 reviews but was unable to approve the merge (#65091).
Fixed an issue where errors were occuring while performing Delete Org (internal ticket).
Fixed an issue where for Build only job source from VC with DX repo, if Master Details Object Change is included in the build, we're getting No Modifications even if changes exist (internal ticket).
Fixed an issue with Review Artifact where similar custom fields from different objects were not populating correctly and switching to other fields (#63676).
Fixed an issue where multiple fields of the respective custom objects were getting selected parallelly while performing edit or save or exit operations on the Review Artifact screen (internal ticket).
Enhanced ARM by adding an option for multiple ARM instances to share a single database cluster (internal ticket).
Fixed an issue where users weren't receiving emails after setting up Mail Settings (#55070).
Fixed an issue where there was a discrepancy between EZ-Commit and Commit templates while retrieving Email Template metadata members (#61696).
Fixed an issue where Merge Labels were taking much longer than expected (#62625).
Fixed an issue where user tried to commit the changes without validation and UI displayed an error Another commit is in progress (#61930).
Fixed a UI bug where there was a discrepancy in the timestamp displayed for a commit in the Commits History page (#61672).
Fixed an issue where Merge was not auto-rejected when validation criteria was not met (#62287).
Enhanced nCino by allowing users to deploy nCino CI build to multiple target sandboxes (#41763).
Fixed a UI bug where incorrect notification was displayed in certain components pages when template was created using one org and was used by another org (internal ticket).
Fixed an issue where Baseline Managed Package Changes option was not displayed on the UI when navigating from Package xml to select manually (internal ticket).
Fixed an issue where there was a discrepancy between the Attachments Records Success/Failure Count and the Retrieved Count when BULK API was enabled for Deployment (internal ticket).
Fixed an issue where Release Artifact execution was failing when rabit home did not exist with an external agent (internal ticket).
Fixed a UI bug on the Profile screen where the expand option for the My Projects and My Roles sections was not working (internal ticket).
Fixed an issue where triggering Data Retention for Audit Tables was throwing the following error: Unable to execute HTTP request: Read timed out (internal ticket).
Fixed an issue where extra characters are seen in the Fetch Commit History results while creating a Release Label with Vlocity label type (internal ticket).
Fixed an issue where user was unable to delete Apex test class on the SF Org Management page (internal ticket).
Enhanced nCino by introducing New Spreads Schedule tile in the Feature Creation screen (internal ticket).
Fixed an issue where if the fields did not load for Applied Mappings during deployment, no error was thrown by the application (internal ticket).
Fixed an issue where user was customer trying to register a Salesforce Org with Custom URL but it was failing with an error (#62192).
Fixed an issue where user user uploaded a YAML file to retrieve the Vlocity components but ALL metadata types were retrieved and displayed (#61181).
Fixed an issue where the same merge could be approved and rejected by different users simultaneously (#60859).
Fixed an issue where branch creation was faileing for sub-users in the EZ-Commit screen for Non-DX Repo (internal ticket).
Fixed an issue where Null Pointer was seen in Create Branch in EZ-Commit flow (internal ticket).
Fixed an issue where all credentials were listed twice in the Credentials dropdown in Create Branch in EZ-Commit flow (internal ticket).
Fixed an issue where branch creation was failing for sub-users in VC repos when the credential scope was private while Admin credentials were fetched (internal ticket).
Fixed an issue where user was unable to delete the Apex Test class under the SF org Apex default config (internal ticket).
Fixed an issue where the Add manually checkbox under Apex class config was selected by default (internal ticket).
Fixed an issue with nCino where user created a feature Deployment for Credit memo template with attachments, but Attachments Objects Data was not fetched, and the deployment failed with the following error: Data file not fetched for object: Attachment (internal ticket).
Fixed an issue with nCino where Standard Features were not loaded in the Feature Management page (internal ticket).
Fixed an issue where Create Artifact was not working as expected while using Release Label (#61607).
Fixed an issue where user was performing an EZ-Commit with Review Artifact option and download the .zip file to make some changes, but was unable to upload it afterwards (#61751).
Fixed an issue where meta.xml file was not deleted from the repository after committing the destructive changes (#61736).
Fixed an issue where File Diff was empty in case of modified Uploaded via Review Artifact in PV Commit Flow (internal ticket).
Fixed an issue where Review Artifact Tree was not responding after uploading the modified file in Commit Flow (internal ticket).
Fixed an issue where User Permissions and Ip Ranges are completly removed from the branch after commiting the Permission Sets and Profiles (internal ticket).
Fixed an issue where Super Admin was getting an error while trying to activate newly signed up users (internal ticket).
Fixed an issue where Post Destruct fields were also added to Pre Destruct despite the user setting it to post (#61162).
Fixed an issue where user set the Max depth value as '0' under Vlocity Configuration Settings but it was retrieving all level dependancy components (#57501).
Fixed an issue with DataLoader where the Credit Memo Template migration was not deploying after user upgraded their instance (#57676).
Fixed an issue where user selected Custom Metadata members (records), but EZ-Commit was failing to generate File Diff with Null error (#59709).
Fixed an issue where Merge was taking longer than usual, and then failing with Null Exception (#60757).
Fixed an issue where EZ-Commits and EZ-Merges were taking much longer than usual (#58098).
Fixed an issue where user performed a merge and sent it for approval, but it was not available under the Commit history tab (#53759).
Fixed an issue where user initiated the prevalidation commit by enabling the destructive type but the deployment failed with an error null at Diff (#59919).
Fixed an issue where Validate Deploy failed in QuickMerge and displayed the following message: This folder unique name already exists for this folder type or has been previously used. Please choose a different name (internal ticket).
Fixed an issue where CI job wasn't considering the metadata changes, so the destructive changes were not being prepared or displayed on the build. (internal ticket).
Fixed an issue where user couldn't create a managed package with the selected ancestor (#59044).
Fixed an issue where CI Job was occasionally failing with the error BUILD FAILED (#57647).
Fixed an issue where CI job was taking the last modified user name if trigger through API instated of taking API token user (#55438).
Salesforce API version 57 (Beta support) is upgraded. The label is modified throughout ARM application including DataLoader and nCino (internal ticket).
Fixed an issue where nCino CI job was stuck in Build Success status for more than a week (#59040).
Fixed an issue where user was trying to deploy RBC (nCino Screens) and the deployment was failing for some of the objects, but there were no error messages shown on the UI (#58044).
Fixed an issue where user was using SSH credential in AutoRABIT but it was throwing the following error: Invalid Private Key (#59244).
Fixed an issue where user has created a Commit label but it was not available while trying to perform an EZ-Merge (#55176).
Fixed an issue where user was not getting file Diff to commit the previously validated commit label and getting an error in the Diff (#59114).
Fixed an issue where user could not create an xml package for deployment because artifact creation and package manifest preparation were failing with an invalid credentials error (#59402).
Fixed an issue where user was trying to perform single revision merge but validation deployment was failing with the following error Metadata package is empty (#59028).
Fixed an issue where when there are special characters in Layout metadata then the user was not able to add it manually in Skip Members section (#58998).
Fixed an issue where user wanted to choose commit revision in a release label based on its comment but if the comment was not in text, it was not completely visible in the UI (#59014).
Fixed a UI bug where an incorrect validation message was seen while adding Skip Members manually (internal ticket).
Fixed an issue where the selected tab checkbox in the metadata components page in the EZ-Commit was not functioning as expected (internal ticket).
Fixed an issue where the EZ-Commit validation screen was displaying incorrect notification when name of the template was empty (internal ticket).
Fixed a recurring issue where Commits and Merges were slowing down at a particular step, and EZ-Merge was failing with an error at commit phase (#51268).
Fixed an issue where while performing destructive changes in EZ-Commit, it was creating package.xml in root path folder in SFDX structure (#57868).
Fixed a UI bug on CI List and CI Results pages where when pagination was changed, the first 25 records were repeated (internal ticket).
Fixed an UI bug where the LastUsedDate column was not displayed in the Branch Table (internal ticket).
Fixed an issue with Branching Baseline where the developers were migrating the changes from dev branch to INT, but Diff was showing 100% addition which is incorrect (#58478).
Fixed an issue where generating Diff for a Commit Label was taking much longer than expected (#55220).
Fixed an issue where Code coverage job was running 4 hours earlier than scheduled every time services were restarted (#54837).
Fixed a UI bug where scrollbar and pagination were not visible on the Org Sync History page (internal ticket).
Fixed an issue where AutoRABIT SSH credentials were failing with an error Auth failed while trying to connect with AWS CodeCommit (#53694).
Fixed an issue where EZ-Commit Diff was taking approximately 4 hours while Refactoring CustomField, which is much longer than expected (#56650).
Fixed an issue where ExternalCredential metadata type was not getting excluded even when user added it in the excluded lists in CI Configuration (internal ticket).
Fixed an issue where after triggering Branching baseline, standard value set metadata type was getting displayed under the deleted components through Autodraft for Non-DX repo (internal ticket).
Fixed an issue where Destructive Components are not seen in case of PV-DX-Destructive Merge for Report metadata type. Instead, it displaying a message: Package is empty (internal ticket).
Fixed an issue where non-admin users were unable to select Branch Type while trying to create a new branch from New EZ-Commit Branch (#57732).
Fixed an issue where CI jobs are failing intermittently with the following error: Getting access token failed from refresh tokenHTTP/1.1 400 Bad Request (#57371).
Fixed an issue where user was trying to deploy only the Documents from the branch to Org, but deployment failed and Asynch ID is not generating (#57263).
Fixed an issue where user was trying to deploy login hours. First they merged it to target branch, then once CI job triggers login hours are not getting deployed to target org (#57359).
Fixed multiple issues where user was having trouble creating new package version from previous ancestor version (#55707).
Fixed an issue where Merge is failing with the following error: failed to push some refs to 'https://github.com/salesforce-align/SFDX.git' (#55939).
Fixed an issue where the Standard Field Account.name is displayed in the deleted components list (#57396).
Fixed an issue where the prevalidation commit failed at delta stage (#55763).
Fixed an issue where user was unable to create commit label for the same repository second time, and branches were not displayed (internal ticket).
Fixed an issue where Provar jobs were failing due to incorrect files being copied from customer repository branch to Provar project directory (#56662).
Fixed an issue where user triggered a CI Job but it deployed with many more components than expected (#46983).
Fixed an issue where user was creating an EZ-Commit, mapping the ALM Project (VersionOne) but received the following error: JSONObject["Assets"] is not a string (#57238).
Fixed an issue where user performed a merge and sent it for approval, but it was not available under the Commit history tab (#53759).
Enhanced the Conflict Resolution Log by adding additional loggers like strategy chosen to resolve the conflict and which user did the resolution (#47559).
Fixed an issue where Commits added from non-nCino Repositories were not cleared from the Workspace causing the Commit to either not be visible in the UI or it is added to the queue but not deployed to the Destination Org (internal ticket).
Fixed an issue where user was creating the feature template for some of the nCino objects but it was taking too long to retrieve the objects from Source Org (#53915).
Enhanced nCino to:
Modify notification messages for null checks on request parameters (internal ticket).
Display only nCino revisions for Version Control in nCino feature deployment (internal ticket).
Fixed an issue where all Slack Notifications were selected by default and user was unable to unselect all at once (#55817).
Fixed an issue where SFI components were not being fetched both in Commit and Deployment modules (#55139).
Fixed an issue with DataLoader Pro where user selected a field as External ID in a job and saved it, but the saved entry was lost and user was unable to map it (#55011).
Fixed an issue where Deployment validation in Prevalidation Commit fails because profile validation automatically picks User Permissions even though Remove User Permissions option is selected (#54941).
Fixed an issue where user was performing a single Merge with only two approval process, but while selecting SCA, process is auto rejected (#55671).
Fixed an issue where Commit Label is not Auto rejected when the validation criteria is not met (#55670).
Fixed an issue where Release Label Merge was failing and throwing the following error: fatal: bad revision (#55000).
Fixed an issue with EZ-Commit where user was unable to upload a Custom YAML file (#55826).
Fixed an issue where the Vlocity Component option under Fetch Changes is not populating for sub-users with roles that have all permissions and access (#54962).
Fixed an issue where Commits added from non-nCino Repositories were not cleared from the Workspace causing the Commit to either not be visible in the UI or it is added to the queue but not deployed to the Destination Org (internal ticket).
Fixed an issue where user was performing a merge operation and validating the package on the target org but the validation was failing with multiple errors (#55541).
Fixed an issue with nCino where CI Job was stuck in Build Success status (#53605).
Fixed an issue where CI Job build was failing with a NullPointerException (#55204).
Fixed an issue where the Repository Branch was unavailable to select to run the Merge process after selecting On successful deployment option (#55537).
Fixed an issue where Admin was able to see the Teams field under ALM Integration but the same field was unavailable for sub-users (#55153).
Fixed an issue where user was getting a NullPointerException when trying to resolve a Merge conflict (#55137).
Fixed an issue with nCino where the UTF-8 Encoding Flag was not displayed in the pop-up during Re-Deployments (internal ticket).
Fixed an issue where during an EZ-Commit, complete information about some of the members of WaveDataflow metadata type was not retreived from the Salesforce Org (#49753).
Fixed an issue where Quick Merge was throwing the following error after clicking Validate & Merge: Please Select Valid revision (#53932 ).
Fixed an issue with EZ-Commit where Autodraft feature was taking too long and eventually failing when user was trying to retrieve components (#48257).
Fixed an issue where user was able to create a Delegated Group but was unable to add a Delegated Admin user to the group using Environment Provisioning (#55266).
Fixed an issue where Test Automation CI Jobs were failing due to InitializeDriver & quit methods (#45878).
Fixed a bug where user was able to access certain branches in the Deployment module to which he did not have access under Profile Settings (#54879).
Fixed an issue with CI Jobs where the build failed with Checkout conflict for an .svg file (#54172).
Fixed an issue with nCino where Record Classification and Classification Objects were missing in the template (internal ticket).
Fixed an issue with nCino where user was creating a CI Job and observed that Use UTF-8 file encoding for the file read and write operations flag was displayed at the bottom below the Commit Details section (internal ticket).
Fixed an issue with nCino where the UTF-8 Encoding Flag was not displayed in the pop-up during Re-Deployments (internal ticket).
Fixed an issue where during an EZ-Commit, complete information about some of the members of WaveDataflow metadata type was not retreived from the Salesforce Org (#49753).
Fixed an issue where Quick Merge was throwing the following error after clicking Validate & Merge: Please Select Valid revision (#53932 ).
Fixed an issue with EZ-Commit where Autodraft feature was taking too long and eventually failing when user was trying to retrieve components (#48257).
Fixed an issue where user was unable to add another branch to Azure in the ALM MGMT Repository mappings (#55133).
Fixed an issue where the Destructive commit Diff was including more components than selected (#54795).
Fixed an issue where a merge got stuck for a long time and the Commit ID was reflected in BitBucket but unavailable to select for release label deployment (#52964).
Fixed an issue with DX CI Jobs where user is not getting details of faulty commit revisions in the notification (#54063).
Fixed an issue with Profile Manager where the deployment is not showing any progress in the logger detail in front end. It was updated only after completion of the deployment job at backend (#53706).
Enhanced the Conflict Resolution Log by adding additional loggers like strategy chosen to resolve the conflict and which user did the resolution (#47559).
Fixed a bug where Merge Commit validation was not considering special characters like %,#, etc. as a value and throwing the following error: Merge comment should not contain an empty space (#54512).
Fixed an issue where ARM was slowing at different phases in the EZ-Commit module (#50503).
Fixed an issue where Git check response was not delivered for validation CI Job even though user has added the comment for a Pull request in the remote repository (#53036).
Build With NULL ERROR (issue exists both with Proxy and without Proxy)
SF Org Code coverage Execution is failing (issue exists both with Proxy and without Proxy)
Jenkins Build is updated with FAILED status even after it is successfully completed (issue exists only without Proxy)
Checkmarx text is not displaying the Proxy Configuration note (Only With Proxy)
Fixed an issue with QA Environments where user was unable to create and delete the SFDX module because of the Apache config CACHE settings (internal ticket).
Fixed an issue with the Deployment module where user initiated a Deployment without selecting the Do not Include Skip Members option, but this option was auto-enabled and skipped the member at the time of deployment (#53747).
Fixed an issue with Modularization where user creating a module and selected the Ignore installed components check box but the installed components were not ignored causing the deployment to fail (#53703).
Fixed an issue with AccelQ Test Automation where test case fails but the error details pop-up is not showing the details of the error that caused the failure (#54224).
Fixed an issue where user is setting up the Apex PMD rules as Priority 1 & Priority 2 in the CI Job but the SCA Report is showing the Priority 3, P4 & P5 which wasn't selected (#54017).
Fixed an issue where the Git check response was not delivered for a validation CI Job (#53036).
Fixed an issue where the Deleted Report metadata components were not found in the EZ-Commit (#53119).
Fixed an issue where user was trying to perform a Quick Merge but was getting an Undefined error for all labels (internal ticket).
Fixed an issue with AccelQ where running a test execution was successful even before the jobs were completed in AccelQ, but the status was always showing as Not Run instead of Success or Failure even if the jobs have been successfully completed (#50181).
Fixed a Page Unresponsive issue while creating a new Release Label by adding a feature to list limited results on each page (#48563).
Fixed an issue where user created a Release Label, performed a Merge operation, committed changes to the target branch, and created two revisions in the Github branch. But ARM was throwing an error while applying merge stage and only on the revision generated (#51364).
Fixed an issue where EZ-Commit initiation was stuck with the error: Unable to fetch Salesforce Org users. Reason: Invalid login: invalid user name or password or security token or api version or user locked out (#52550).
Fixed an issue where Page Size value on the Edit Release Label screen is defaulting to the previous value instead of the set value (internal ticket).
Fixed a UI bug where OK Button in Automation is not visible in the Create Release Label pop-up when opened in 100% zoom (internal ticket).
Fixed an issue where Managed Package was picking the wrong ancestor by adding a feature to manually select the preferred ancestor while creating a package version (#48311).
Fixed an issue where user was adding URLs to the Proxy Configuration Settings but the URL List was not reflecting the same (internal ticket).
Fixed an issue where Custom Template Creation failed and the Logs did not record the reason for failure (#52147).
Fixed an issue where the Created By value was not visible in Dataloader, Dataloader Pro DL Config, and the TestEnv History page (internal ticket).
Fixed an issue where the Comment Box was not accepting more than 100 characters while rejecting a Commit, but was working as expected while approving a commit (#51384).
Fixed an issue where user set Commit validation Criteria to Auto reject after 7 days but the older Pre-validation commits are not auto rejected after 7 days (#49874).
Fixed an issue where user cannot add Skip members manually and it is failing due to special characters being included (#53139).
Fixed an issue where user raised a Pull request on a branch and was getting a webhook response, but CI Job build was not triggered (#51592).
Fixed a UI bug where Add to dashboard button was unavailable for widgets (#52333).
Fixed an issue where a new database file is created and overwritten with an existing database file whenever the server was restarted (internal ticket).
Fixed an issue where user was trying to resolve conflicts on Merge Request Labels created more than 7 days ago, but application was throwing an error: undefined (internal ticket).
Fixed an issue where Custom Email Template was not working for Email notifications (#47484).
Fixed an issue where user was testing SSH Connection but the application was throwing an error: invalid privateKey (#50940).
Fixed an issue with nCino where UI Log was not generated for failed CI Jobs (#50442).
Fixed an issue where New EZ-Merge was throwing an error (#46754).
Fixed an issue where Audit Logs were not generating via Postman Services (#50221).
Fixed an issue where Commits were getting stuck and throwing the following error: No credential have been found with Name:git, but was not reflecting in the UI log (#51713).
Fixed an issue with Workspace Settings where unused workspaces were not being cleared despite selecting Clear all workspaces which are not used in last 7 days (#50164).
Fixed an issue where user was performing a Prevalidation EZ-Commit and found that some Layout Assignments were deleted though those layouts were not part of the commit (#50945).
Fixed an issue with nCino where migration was failing due to errors with Standard Screen and UI Templates (#50432).
LastModifiedDate
LastModifiedByName.
Permission Sets
Fixed an issue where CI job to generate Code Coverage Report was not reflected in the org or in the e-mail notification (#72042).
Fixed an issue where merge status is displayed as completed but no revision is generated, and the merge is not available in the UAT branch (#71266).
Enhanced DataLoader by adding the ability to field mapping through the lookup fields (#58480).
Fixed an issue with DataLoader where while running an Extract job on the PUBLISHER object, the job was failing with the following error Publisher: column id is not supported in ORDER BY clause (#71303).
Enhanced the nCino filter criteria by adding the ability to search and filter labels using the whole or partial name (#71826).
Enhanced ARM by using known vulnerable components through the DataTables 1.10.12 plugin for advanced data table functionalities such as sorting, filtering, pagination, and more. This allows users to easily display and manipulate large sets of data on their web pages in a user-friendly manner (internal ticket).
Fixed an issue with Prevalidation Merge where users were unable to deploy the ApexClass Tests related to ApexClasses and Apex Triggers (internal ticket).
Fixed a UI bug where the date column in the EZ-Commit Weekly report was displaying incorrect values (internal ticket).
Fixed an issue where user was unable to register a branch even though Test Connection was successful (#67023).
Fixed an issue where ARM wasn't fetching the ApexClass Tests related to ApexTriggers upon selecting Run Tests Based On Changes option (#67503).
Fixed an issue where triggered CI jobs were taking too long to build, and also slowing down ARM altogether (#66846).
Fixed an issue where if the file name contained spaces, Commit Validation via VS Code plugin was unable to detect the file (#63518).
Fixed an issue where Search & Substitute was not updating the value for a custom label in the SF org (#66809).
Fixed an issue where there was a discrepancy between the changes captured in the ARM Diff and the repos in BitBucket (#60596).
Fixed an issue where the SF org URL is not displaying the updated one under Profile (#67718).
Fixed an issue with nCino where CI job filter changes on templates are not reflecting after saving (#66956).
Fixed an issue with Dataloader Pro where user tried to migrate Account Object Data with Attachments Object, but the logs verify that there is a Null Pointer Exception. (internal ticket).
Improved nCino by adding additional loggers for Branching baseline for user to view the status in the UI (internal ticket).
Fixed an issue where user was unable to filter while trying to select a job which had spaces in the job name (internal ticket).
Fixed an issue where non-admin users were unable to select Branch Type while trying to create a new branch from New EZ-Commit Branch (#57732).
Fixed an issue where CI jobs are failing intermittently with the following error: Getting access token failed from refresh tokenHTTP/1.1 400 Bad Request (#57371).
Fixed an issue where user was trying to deploy only the Documents from the branch to Org, but deployment failed and Asynch ID is not generating (#57263).
Fixed an issue where user was trying to deploy login hours. First they merged it to target branch, then once CI job triggers login hours are not getting deployed to target org (#57359).
Fixed multiple issues where user was having trouble creating new package version from previous ancestor version (#55707).
Fixed an issue where Merge is failing with the following error: failed to push some refs to 'https://github.com/salesforce-align/SFDX.git' (#55939).
Fixed an issue where the Standard Field Account.name is displayed in the deleted components list (#57396).
Fixed an issue where the prevalidation commit failed at delta stage (#55763).
Fixed an issue where user was unable to create commit label for the same repository second time, and branches were not displayed (internal ticket).
Fixed an issue where user performed a merge and sent it for approval, but it was not available under the Commit history tab (#53759).
Enhanced the Conflict Resolution Log by adding additional loggers like strategy chosen to resolve the conflict and which user did the resolution (#47559).
Fixed an issue where Commits added from non-nCino Repositories were not cleared from the Workspace causing the Commit to either not be visible in the UI or it is added to the queue but not deployed to the Destination Org (internal ticket).
Fixed an issue where user was creating the feature template for some of the nCino objects but it was taking too long to retrieve the objects from Source Org (#53915).
Enhanced nCino to:
Modify notification messages for null checks on request parameters (internal ticket).
Display only nCino revisions for Version Control in nCino feature deployment (internal ticket).
Fixed an issue where all Slack Notifications were selected by default and user was unable to unselect all at once (#55817).
Fixed an issue where SFI components were not being fetched both in Commit and Deployment modules (#55139).
Fixed an issue with DataLoader Pro where user selected a field as External ID in a job and saved it, but the saved entry was lost and user was unable to map it (#55011).
Fixed an issue where Deployment validation in Prevalidation Commit fails because profile validation automatically picks User Permissions even though Remove User Permissions option is selected (#54941).
Fixed an issue where user was performing a single Merge with only two approval process, but while selecting SCA, process is auto rejected (#55671).
Fixed an issue where Commit Label is not Auto rejected when the validation criteria is not met (#55670).
Fixed an issue where Release Label Merge was failing and throwing the following error: fatal: bad revision (#55000).
Fixed an issue with EZ-Commit where user was unable to upload a Custom YAML file (#55826).
Fixed an issue where the Vlocity Component option under Fetch Changes is not populating for sub-users with roles that have all permissions and access (#54962).
Fixed an issue where Commits added from non-nCino Repositories were not cleared from the Workspace causing the Commit to either not be visible in the UI or it is added to the queue but not deployed to the Destination Org (internal ticket).
Fixed an issue where user was performing a merge operation and validating the package on the target org but the validation was failing with multiple errors (#55541).
Fixed an issue with nCino where CI Job was stuck in Build Success status (#53605).
Fixed an issue where CI Job build was failing with a NullPointerException (#55204).
Fixed an issue where the Repository Branch was unavailable to select to run the Merge process after selecting On successful deployment option (#55537).
Fixed an issue where Admin was able to see the Teams field under ALM Integration but the same field was unavailable for sub-users (#55153).
Fixed an issue where user was getting a NullPointerException when trying to resolve a Merge conflict (#55137).
Fixed an issue with nCino where the UTF-8 Encoding Flag was not displayed in the pop-up during Re-Deployments (internal ticket).
Fixed an issue where during an EZ-Commit, complete information about some of the members of WaveDataflow metadata type was not retreived from the Salesforce Org (#49753).
Fixed an issue where Quick Merge was throwing the following error after clicking Validate & Merge: Please Select Valid revision (#53932 ).
Fixed an issue with EZ-Commit where Autodraft feature was taking too long and eventually failing when user was trying to retrieve components (#48257).
Fixed an issue where user was able to create a Delegated Group but was unable to add a Delegated Admin user to the group using Environment Provisioning (#55266).
Fixed an issue where Test Automation CI Jobs were failing due to InitializeDriver & quit methods (#45878).
Fixed a bug where user was able to access certain branches in the Deployment module to which he did not have access under Profile Settings (#54879).
Fixed an issue with CI Jobs where the build failed with Checkout conflict for an .svg file (#54172).
Fixed an issue with nCino where Record Classification and Classification Objects were missing in the template (internal ticket).
Fixed an issue with nCino where user was creating a CI Job and observed that Use UTF-8 file encoding for the file read and write operations flag was displayed at the bottom below the Commit Details section (internal ticket).
Fixed an issue with nCino where the UTF-8 Encoding Flag was not displayed in the pop-up during Re-Deployments (internal ticket).
Fixed an issue where during an EZ-Commit, complete information about some of the members of WaveDataflow metadata type was not retreived from the Salesforce Org (#49753).
Fixed an issue where Quick Merge was throwing the following error after clicking Validate & Merge: Please Select Valid revision (#53932 ).
Fixed an issue with EZ-Commit where Autodraft feature was taking too long and eventually failing when user was trying to retrieve components (#48257).
Fixed an issue where user was unable to add another branch to Azure in the ALM MGMT Repository mappings (#55133).
Fixed an issue where the Destructive commit Diff was including more components than selected (#54795).
Fixed an issue where a merge got stuck for a long time and the Commit ID was reflected in BitBucket but unavailable to select for release label deployment (#52964).
Fixed an issue with DX CI Jobs where user is not getting details of faulty commit revisions in the notification (#54063).
Fixed an issue with Profile Manager where the deployment is not showing any progress in the logger detail in front end. It was updated only after completion of the deployment job at backend (#53706).
Enhanced the Conflict Resolution Log by adding additional loggers like strategy chosen to resolve the conflict and which user did the resolution (#47559).
Fixed a bug where Merge Commit validation was not considering special characters like %,#, etc. as a value and throwing the following error: Merge comment should not contain an empty space (#54512).
Fixed an issue where ARM was slowing at different phases in the EZ-Commit module (#50503).
Fixed an issue where Git check response was not delivered for validation CI Job even though user has added the comment for a Pull request in the remote repository (#53036).
Build With NULL ERROR (issue exists both with Proxy and without Proxy)
SF Org Code coverage Execution is failing (issue exists both with Proxy and without Proxy)
Jenkins Build is updated with FAILED status even after it is successfully completed (issue exists only without Proxy)
Checkmarx text is not displaying the Proxy Configuration note (Only With Proxy)
Fixed an issue with QA Environments where user was unable to create and delete the SFDX module because of the Apache config CACHE settings (internal ticket).
Fixed an issue with the Deployment module where user initiated a Deployment without selecting the Do not Include Skip Members option, but this option was auto-enabled and skipped the member at the time of deployment (#53747).
Fixed an issue with Modularization where user creating a module and selected the Ignore installed components check box but the installed components were not ignored causing the deployment to fail (#53703).
Fixed an issue with AccelQ Test Automation where test case fails but the error details pop-up is not showing the details of the error that caused the failure (#54224).
Fixed an issue where user is setting up the Apex PMD rules as Priority 1 & Priority 2 in the CI Job but the SCA Report is showing the Priority 3, P4 & P5 which wasn't selected (#54017).
Fixed an issue where the Git check response was not delivered for a validation CI Job (#53036).
Fixed an issue where the Deleted Report metadata components were not found in the EZ-Commit (#53119).
Fixed an issue where user was trying to perform a Quick Merge but was getting an Undefined error for all labels (internal ticket).
Fixed an issue with AccelQ where running a test execution was successful even before the jobs were completed in AccelQ, but the status was always showing as Not Run instead of Success or Failure even if the jobs have been successfully completed (#50181).
Fixed a Page Unresponsive issue while creating a new Release Label by adding a feature to list limited results on each page (#48563).
Fixed an issue where user created a Release Label, performed a Merge operation, committed changes to the target branch, and created two revisions in the Github branch. But ARM was throwing an error while applying merge stage and only on the revision generated (#51364).
Fixed an issue where EZ-Commit initiation was stuck with the error: Unable to fetch Salesforce Org users. Reason: Invalid login: invalid user name or password or security token or api version or user locked out (#52550).
Fixed an issue where Page Size value on the Edit Release Label screen is defaulting to the previous value instead of the set value (internal ticket).
Fixed a UI bug where OK Button in Automation is not visible in the Create Release Label pop-up when opened in 100% zoom (internal ticket).
Fixed an issue where Managed Package was picking the wrong ancestor by adding a feature to manually select the preferred ancestor while creating a package version (#48311).
Fixed an issue where user was adding URLs to the Proxy Configuration Settings but the URL List was not reflecting the same (internal ticket).
Fixed an issue where Custom Template Creation failed and the Logs did not record the reason for failure (#52147).
Fixed an issue where the Created By value was not visible in Dataloader, Dataloader Pro DL Config, and the TestEnv History page (internal ticket).
Fixed an issue where the Comment Box was not accepting more than 100 characters while rejecting a Commit, but was working as expected while approving a commit (#51384).
Fixed an issue where user set Commit validation Criteria to Auto reject after 7 days but the older Pre-validation commits are not auto rejected after 7 days (#49874).
Fixed an issue where user cannot add Skip members manually and it is failing due to special characters being included (#53139).
Fixed an issue where user raised a Pull request on a branch and was getting a webhook response, but CI Job build was not triggered (#51592).
Fixed a UI bug where Add to dashboard button was unavailable for widgets (#52333).
Fixed an issue where a new database file is created and overwritten with an existing database file whenever the server was restarted (internal ticket).
Fixed an issue where user was trying to resolve conflicts on Merge Request Labels created more than 7 days ago, but application was throwing an error: undefined (internal ticket).
Fixed an issue where Custom Email Template was not working for Email notifications (#47484).
Fixed an issue where user was testing SSH Connection but the application was throwing an error: invalid privateKey (#50940).
Fixed an issue with nCino where UI Log was not generated for failed CI Jobs (#50442).
Fixed an issue where New EZ-Merge was throwing an error (#46754).
Fixed an issue where Audit Logs were not generating via Postman Services (#50221).
Fixed an issue where Commits were getting stuck and throwing the following error: No credential have been found with Name:git, but was not reflecting in the UI log (#51713).
Fixed an issue with Workspace Settings where unused workspaces were not being cleared despite selecting Clear all workspaces which are not used in last 7 days (#50164).
Fixed an issue where user was performing a Prevalidation EZ-Commit and found that some Layout Assignments were deleted though those layouts were not part of the commit (#50945).
Fixed an issue with nCino where migration was failing due to errors with Standard Screen and UI Templates (#50432).
Fixed an issue where the Custom label and remote site setting URLs were not getting updated by ARM through Environmental Provisioning (#49612).
Fixed an issue with Vlocity where selecting one component from a GIT repository was causing all the components from the category to get selected (#49806).
Fixed an issue with ALM Mgmt. where item status was not retrieved properly for Merge Request, but was working as expected for EZ-Merge (#50628).
Fixed a UI bug where Release Labels were showing duplicate Time Stamps (#51205).
Fixed an issue where old Commit Labels were not getting auto-rejected after 7 days as the user had configured under Commit Validation Criteria (#49874).
Fixed an issue where user was getting an error pop-up on the Permissions and the SF ORG MGMNT pages, and the SF org and VC repo mappings were lost in the profile section of a role (#49108).
Fixed an issue with EZ-Merge where Diff was not being generated even though there were file changes between the source branch and the destination branch (#50323).
Fixed a UI bug in DataLoader where user was switching from Graphical View to Grid View but Graphical View options were still being displayed (#50431).
Fixed an issue with nCino where the Insert/Update With Null Values option was not getting updated for CI jobs (#50259).
Fixed an issue where users were unable to re-authenticate the Salesforce Org after refreshing their personal sandboxes (#48533).
Fixed an issue where Environment Provisioning Template was not functioning as expected for Custom Labels containing URL (#47892).
Fixed an issue with EZ-Commit where user was trying to deploy Permission Sets and Profiles together, and the pre-validation process was stuck in In-Progress status (#49340).
Fixed an issue where old Commit Labels were not getting auto-rejected as configured (#49874).
Fixed an issue with Version Control Prevalidation Commit where for the selected Custom Metadata and Permission Set, Diff was being generated as expected but the Deployment was failing (internal ticket).
Fixed an issue with Version Control Prevalidation Merge where SCA report was empty, and throwing the following error in the console: Uncaught TypeError: Cannot read properties of undefined (reading 'length') (internal ticket).
Fixed an issue where user was unable to reset the AutoRABIT password, and was getting an error: getAttribute: Session already invalidated (#50145).
Fixed an issue where the user tried to merge to the Dev branch but the CI Job failed and was throwing a Duplicate error (#49661).
Fixed an issue where user was trying to install Unlocked Package via CI Job but it was failing and throwing the following error: ERROR 178928269770891:275 - For input string: "0-2" java.lang.NumberFormatException: For input string: "0-2" (#50093).
Enhanced Vlocity loggers for Branching Baseline by displaying to the user Status Count of Remaining, Success, Error and Ignored (internal ticket).
Fixed an issue where Test Connection was failing on the Version Control Summary page under the Admin module (#49299).
Fixed an issue with Prevalidation Merge by increasing the SCA Response timeout from 50 minutes to 5 hours (#48613).
Fixed an issue where merging Master Branch with the Production branch was throwing the following error: No merge head specified (#46594).
Fixed a bug where New A-Z Merge was throwing an error (#46754).
Fixed an issue with Autorabit Commit Label related to Permission Sets Deployment (#48709).
Fixed an issue where custom metadata records were not being selected during deployment (#49167).
Fixed an issue in Version Control Commit Labels history where Created By and Created Date values were exchanged (internal ticket).
Fixed an issue where user was getting an error while trying to deploy Vlocity Metadata using CI Jobs (#47568).
Fixed an issue where Branching Baseline was not retrieving Workflow Metadata types (#49403).
Fixed an issue where Release Label failed to load revisions from a particular branch and the browser was hanging and throwing an Out of memory error (#48563).
Fixed an issue where EZ-Commit was not getting auto-rejected when CodeScan analysis failed, even though user select the option to run Static Code Analysis (#47155).
Fixed an issue where merge was failing at the Validate Deploy step even before selecting the org to validate (#49724).
Fixed an issue where Layout was being removed from the Diff while deploying Profile changes with related Layouts and RecordTypes (#48268).
Fixed multiple issues with CodeScan<>ARM Integration (#49605).
Fixed an issue where dashboards and reports were changing to Destructive and getting deleted (#48119).
Fixed an issue where discrepancies for Document, Assignment Rule and AutoResponseRule metadata types content was observed in package.xml for SFDX and non-SFDX CI Jobs (#47017).
Fixed an issue where nCino CI Jobs via RBC were failing during parallel deployment. Instead of falling in queue, the first job was failing while the other succeeded, and the user had to retrigger the failed job (#47335).
Fixed an issue where creating multiple deployment jobs from the same source org to the same destination org for different templates, the jobs were failing with Null Pointer Exception error (internal ticket).
Fixed an issue with DX Pre-validation merge where Destructive Deployment for custom labels failed without any errors (internal ticket).
Fixed an issue where Environment provisioning template was not working when trying to update custom label values that contain URL, and the incorrect value was being updated in the org (#47892).
Fixed an issue where choosing the Select Manually option while doing a commit was resulting in a blank screen for the Deleted tab (internal ticket).
Fixed an issue where while doing Prevalidation commit in AR, Commit Only Permissionsets For The Selected Metadata functionality was not working properly for both DX and Non-DX cases (internal ticket).
Fixed an issue in Dataloader where an Undefined Error was displayed when user was trying to create and save the Screens Template (internal ticket).
Fixed an issue where user was trying to validate the commit using single revision, but was getting an Empty Package error even though there were changed files in the commit (#47530).
Fixed an issue where DataLoader Pro jobs were failing with an error duplicate value found: SetupOwnerId duplicates value on record with id for the custom setting Multichannel_Settings_vod__c, even though there is no field mapped with name SetupOwnerId (#48230).
Fixed an issue where the search functionality was not working in Dataloader Configuration as well as Dataloader Test Environment Setup (internal ticket).
Fixed an issue where EZ Commit Logs and Change Labels were not displaying for some of the commit labels (#45364).
Fixed an issue where the user was not able to see the deployment report because the build was failing when only custom fields were being selected without the related object (#45663).
Fixed an issue where merge request was being auto rejected if the selected approver was no longer with AR (#48084).
Fixed a bug where user had enabled Squash and Merge while performing a new merge, but the Squash and Merge option was not displayed after the Merge Request was approved (#48246).
Fixed an issue in CI Jobs deployments where Bulk API option for Attachments was throwing an error (internal ticket).
Fixed an issue where nCino CI Jobs were failing the first time and completing the second time successfully (#46545).
Enhanced the Dataloader history screen (internal ticket):
Column mover added to table column alignment for text view.
Moved Last Run details to the Date/Time column.
Fixed an issue where Standard fields are not retreiving when included in package.xml, and retrieving through E-Z Commit (Package Manifest) option (#47961).
Fixed an issue for the nCino CI Jobs were failing due to default selection of AutorabitExtId__c in Mappings (internal ticket).
Fixed an issue for the nCino Deployments where even if LookupKey is available, by default Name is selected in External ID Mapping (internal ticket).
Fixed an issue for the nCino CI Jobs where Attachments were failing due to External Mappings not being set to the NAME field (internal ticket).
Added the feature to dynamically handle the respective nCino Prefix rather than depending on the JSON file to identify the External Id field
permissionset error--- Error in field: customPermission not foundFixed an UI bug where while performing test connection for any successful Salesforce org registered, the messasge is displayed as "Success" instead of "Testconnection was successful" (internal ticket).
Fixed an issue where the ALM integration was not working when the files are pushed with special characters in their name (#47414).
Fixed an issue where the commit labels was getting auto-rejected while committing Profile FLS (#46844).
Fixed the below deployment-related issues:
Fixed an issue where the deployment failed to initiate when search and substitute rules are selected (#47802).
Fixed an issue where the status log .csv files are inconsistent for deployment via CI jobs (internal ticket).
Fixed an issue where the users were unable to process the migration of RBC object (nForce__Views__c) using the nCino CI jobs, feature template migration, or the Dataloader Pro jobs (#47098).
Fixed an issue where while deploying a nCino-User Interface template, only partial records are deployed and no deployment logs are generated (#47494).
Fixed an issue where the users, while performing an EZ-Commit by enabling the run SCA option, the CodeScan analysis is getting failed, but EZ-Commit is not getting auto-rejected (#47155).
Fixed an issue where the ARM allows to associate only one branch to one package, and not able to build beta package versions from various branches. This is now fixed (#46841).
Fixed an issue where the CI job, while deploying manage packages, is installing all the manage packages instead of installing a single package (#46832).
Fixed an issue where the links on the CI Job log screen are redirected to the user's login page instead of redirecting to user's Salesforce org screen (#47151).
Salesforce API version 55 (Beta support) is upgraded. The label is modified throughout ARM application to Salesforce API version 55.0 (#47404).
Duplicate classes from the ARM repo has been removed (internal ticket).
Fixed an issue with the Profile Manager where the user were unable to select the default app permission during the profile deployment (#47462).
Fixed an issue where the merge revisions were missing from the CI jobs (#46862).
Fixed an issue where the users were unable to commit Vlocity card from one org to another org in ARM (#44938).
Fixed an issue where for both CI Jobs and Deloyments (Non-DX and DX), the deployment was getting failed with the below error although the Ignore missing visibility settings is checked: permissionset error--- Error in field: customPermission not found (internal ticket).
Fixed an UI bug where while performing test connection for any successful Salesforce org registered, the messasge is displayed as "Success" instead of "Testconnection was successful" (internal ticket).
Fixed an issue where the ALM integration was not working when the files are pushedwith special characters in their name (#47414).
Fixed an issue where the commit labels was getting auto-rejected while committing Profile FLS (#46844).
Fixed an issue where the merge was getting failed with the following error: Fetch operation is failed due to some runtime exceptions from Git (#46773).
Fixed an issue where the username and passwords fields were not editable for users registered in ARM with basic authentication (#47099).
Fixed a bug where the users could not edit/modify their CI jobs when the build was in progress (#43538).
Fixed an issue with the permissionsets where instead of delta changes, the Permissionset retrieving entire file from the branch and causing dependency issues (#46846).
Fixed an UI bug where the ARM application displays unwanted scrollbar when "Exclude Installed (Managed) components" is selected in the My Account page (internal ticket).
Enhanced the ARM workspace feature to automatically unlock the workspace after sufficient time to run the workspace operations.
Added the feature to set Limit 0 option for the Dataloader Pro jobs. This limit will allow users to skip migrating child or Ancestors objects.
Fixed an issue where while editing an existing nCino CI Job, the version control is not automatically choosing the previous repository set. This is causing the selected nCino Templates to reset (#46952).
Fixed an issue where the ALM labels were missing from the ALM Label lists page (#44410).
Fixed an issue where the settings related with user permissions were erased (#46472).
Fixed an issue where the users when performed EZ-Commit using a package manifest file, doesn't include managed components that are in the package.xml file (#47083).
[Enhancement] Added the Salesforce versions information in the logs for all Dataloader related jobs activities.
[Enhancement] Added the ability to delete a commit before it is pushed to your remote repository so that you have a choice to redo incorrect commits/ merges.
Fixed an issue where the Delete Commit button was not seen after approving an EZ-Commit label (internal ticket).
Fixed an issue where the toggle button for the dashboard metadata type in the commit label screen is not working as expected (internal ticket).
Fixed an issue for the nCino Feature Deployments where the users were getting audit field issue when trying to deploy with Insert/Update with Null Values option (internal ticket).
Fixed an issue for the nCino CI jobs using Spreads Templates where the users were getting NullPointerException error when trying to deploy with Insert/Update with Null Values option (internal ticket).
Fixed an issue with the SFDX job, where for the Report metadata type, the rollback feature was working weirdly (internal ticket).
Fixed a bug where the users could not edit/modify their CI jobs when the build was in progress (#43538).
Fixed an issue where entering the package installation key in Install an Unlocked or Managed Package from Version Control Branch CI Job gets altered when manually entered or pasted (#46836).
Fixed an issue where the user could not run the static code scan report on GitHub with APEX PMD Lint Scanner metadata type (#46781).
Fixed an issue with the CodeScan analysis report that failed when running from ARM (#44404).
Fixed an issue where the user could not fetch the latest CI job weekly reports (#42587).
Enhanced the Dataloader Pro, where the attachments are now supported (#41077).
Fixed a bug where editing the Dataloader job shows "Job Group" as null or empty (internal ticket).
Vlocity has been upgraded to v1.15.5.
Fixed an issue with the CI job where the version control using Salesforce with attachments was not picking the attachments during CI build (internal ticket).
Fixed an issue with the EZ-Merge, where merging the main branch to the dev branch failed with a No merge head specified error (#46594).
Fixed an issue that throws Schema as invalid error while running the branching baseline operation (#46593).
Fixed an issue where our internal team members could not create a new role from the Admin section (internal ticket).
Fixed a bug where the Invalid Schema error is seen for non-SFDX prevalidation merge (internal ticket).
Fixed an EZ-Commit issue where additional permissions were removed from Profiles metadata type, which is not a part of the commit (#44543).
Fixed an issue where the deployment using Commit/Release Label was not working (#46419).
Fixed an issue where the Compact Layout were not getting deployed and throws undefined error(#46592).
Fixed an issue where the ALM statuses were not updated/rolled back post CI job rollback completion (#45945).
Fixed an issue where the destructive changes were not working as expected for the CI jobs (#46216).
Fixed an issue where the ARM failed to update the Audit fields when trying to run nCino feature deployment (#46356).
Fixed an issue where our internal team were not able to register their credentials on one of the ARM SAAS instances (#46315).
Fixed a bug where the deleted components were tagged as UC (UnChanged) instead of D (Deleted) in the EZ-Commit (#46087).
Fixed an issue where the metaXML file were not retrieved for the ContentAsset metadata type for the SFDX "Entire Branch" merge case (internal ticket).
Fixed an issue where the deployment validation were failing for the prevaildation merge with the error: No source backed components present in the package (internal ticket).
Fixed an issue where the merge using single revision (baseline revision) receives the metadata schema error (#46570).
Fixed an issue where the merges were getting failed and throws the Schema is invalid for the file error (#45768).
Fixed an issue where the exported users list contained inaccurate information (#44782).
Fixed an issue where the creation of a scratch org were getting failed. The fix has been deployed to in this weekly release (#46021).
Fixed an issue where the users were unable to use the release label for deployment (#45415).
Fixed an issue where the users were not able to register same DevHub with two different usernames (#46208).
Fixed an issue where the CI Job was picking the deleted components from GitHub branch although the Prepare Destructive Changes checkbox was not selected. This caused the deployment to fail (#42553).
Fixed an issue where the CI Job for backing up from org to the version control branch was failing with null pointer exception error (#45646).
Fixed an issue where the EZ-Commits, when included Profile, was not working as expected (#45902).
Fixed an issue where the commits were getting stuck at the delta stage (#45101).
Fixed an issue where the Git tags were being added to the queue but not being processed (internal ticket).
Fixed an isse where the delta was getting failed in the EZ-Commit flow (internal ticket).
Fixed an issue where the Dalaloader Pro job is failing with Required field missing on "nCino_Screen__c" object, however the user were able to view the Screen__c object has a value in their source org (#45139).
Fixed an issue where the user were not able to save the Dataloader Pro jobs and throws the JAVA.NullPointerException error (#46385).
Fixed a bug where the users were not able to view the log reports after registering Tags via ARM (internal ticket).
Fixed an issue where the tags creation got failed when the tag name contains 'error' with custom API flow (internal ticket).
Request parameters are empty/null error (internal ticket).Fixed an issue where the users when accessing the Commit History page throws Invalid FilterExpression error (internal ticket).
Fixed an issue where the user were unable to fetch the latest CI job weekly reports (#42587).
Fixed an issue where the Diff report in the Merge Request was not working as expected (#45315).
Fixed an issue where the user ran the branching baseline operation by excluding the Managed package components, however, the Package.xml file still had all the managed package components listed in it (#45125).
Fixed an issue where the code coverage report was being generated at a different time than what was scheduled (#45703).
Fixed an issue where the exported users list contained inaccurate information (#44782).
Fixed an issue where the TAF execution were getting failed (internal ticket).
Fixed an issue where the From Revision was not visible when user access their CI job from CI Job History page (internal ticket).
Fixed an issue that caused Chrome to crash anytime a user attempted to view the functional test results for the task of running a Selenium Maven test. The functional test results screen enters a continuous cycle of requests, which crashes the browser (internal ticket).
Fixed an issue where the skip members feature of ARM was not working as expected (internal ticket).
Fixed an issue where the user while performing EZ-Commit with SonarQube code analysis was getting failed with Failed to run the sonar-scanner: null error (#46070).
Fixed an issue where the Jenkins builds were failing during the CI/CD process (internal ticket).
Fixed an issue where the quick deployment functionality was not working as expected (#42521).
Fixed an issue where the users could not view the commits list to merge them into a release label (#43718).
Fixed an issue where the Jenkins builds were failing during the CI/CD process (internal ticket).
Fixed an issue where the ARM user interface gets distorted when the zoom is 100% (#43735).
Fixed an issue where the ALM workflow was mismatched (#43775).
Fixed Spring4Shell vulnerability by upgrading the Spring Boot version to 2.6.6 for the AR Agent (#43584).
Fixed an issue where the "invalid session" error occurs when the user tries to delete and resave the cloned CI job.
Fixed an issue where the Conflict Resolution screen was not showing all the merge conflicts (#43663).
Fixed an issue where the CI job build status fails with "java.util.ConcurrentModificationException" error when running the nCino feature migration templates (#40752).
Fixed an issue with the Dataloader Pro job where the users, when trying to migrate the case object along with feed item & feed comment, the ARM application throws the "invalid cross reference id" error (#43703).
Fixed an issue where the merge process, after being sucessful, did not display the code coverage report (#42079).
Fixed an issue where the ARM user interface gets distorted when the zoom is 100% (#43735).
Fixed an issue where the ALM workflow was mismatched (#43775).
Fixed an issue where the ARM user interface gets distorted when the zoom is 100% (#43735).
Fixed an issue where the ALM workflow was mismatched (#43775).
Fixed Spring4Shell vulnerability by upgrading the Spring Boot version to 2.6.6 for the AR Agent (#43584).
Fixed an issue where the "invalid session" error occurs when the user tries to delete and resave the cloned CI job.
Fixed an issue where the Conflict Resolution screen was not showing all the merge conflicts (#43663).
Fixed an issue where the CI job build status fails with "java.util.ConcurrentModificationException" error when running the nCino feature migration templates (#40752).
Fixed an issue with the Dataloader Pro job where the users, when trying to migrate the case object along with feed item & feed comment, the ARM application throws the "invalid cross reference id" error (#43703).
Fixed an issue where the merge process, after being sucessful, did not display the code coverage report (#42079).
Fixed an issue where the quick deployment functionality was not working as expected (#42521).
Fixed an issue where the users could not view the commits list to merge them into a release label (#43718).
Fixed a bug where selecting the "Deployment" icon after signing in to the ARM application caused the user to log off and on and return to the home page (#44040).
Fixed a bug where the check-ins display the wrong number of files changed during commit (#40119).
Fixed an issue where the users while accessing the help center from ARM application, receiving the ({"result":"failure","cause":"E105 - Request Delayed"}) error (#43579).
Fixed a bug where the commits was getting failed due to SCM (Software Configuration Management) authentication failure (#42276).
Fixed an issue where extra metadata members are picked up for the profile component during the EZ-Commit process (#41361).
Fixed an issue where the ARM user interface gets distorted when the zoom is 100% (#43735).
Fixed an issue where the ALM workflow was mismatched (#43775).
Fixed Spring4Shell vulnerability by upgrading the Spring Boot version to 2.6.6 for the AR Agent (#43584).
Fixed an issue where the "invalid session" error occurs when the user tries to delete and resave the cloned CI job.
Fixed an issue where the Conflict Resolution screen was not showing all the merge conflicts (#43663).
Fixed an issue where the CI job build status fails with "java.util.ConcurrentModificationException" error when running the nCino feature migration templates (#40752).
Fixed an issue with the Dataloader Pro job where the users, when trying to migrate the case object along with feed item & feed comment, the ARM application throws the "invalid cross reference id" error (#43703).
Fixed an issue where the merge process, after being sucessful, did not display the code coverage report (#42079).
Added the criteria to trigger the callout URL post-deployment. If you set it to success, the callout URL is activated if the salesforce deployment is successful (#38990).
Enabled feature flag settings to select between classic ARM and Salesforce CLI process to generate package manifest.
Fixed an issue where the commit validation is successful for an empty field, whereas the CI job fails (#43324).
Fixed an issue where the deleted metadata components were showing under the "File Changes" tab but did not appear under the "Destructive Changes" column while carrying out a manual deployment (#41670).
Fixed Dataloader Pro job issue where the job is completed successfully without loading all ancestors/master objects data to the destination environment (#43276).
Fixed the below nCino issues:
Unable to proceed with feature deployment using an existing community feature migration template due to the following error: "No External Id field exist in source org." This is now fixed and working as expected (#43263).
Non-template records were being picked up during nCino deployment.
Non-template records are fetched in the dataset.
Spread Statement Record failing with the error “Missing Statement Types.” This is now fixed.
Fixed a bug where the users were not able to view specific values under the standard value sets in the New EZ-Commit screen (#41773).
Fixed a bug where the New EZ-Commit > Deleted Component tab throws a null error on expanding the metadata types.
Fixed a bug where the deploying records via record based configurations (RBC) was throwing error: "No external Id field exists in the source org" (#43263).
Fixed an issue where creating a new nCino feature migration template takes longer than expected (#41855).
Addressed out of memory (OOM) and other performance issues in this weekly release.
Fixed an issue where the users were unable to update any changes in the permission section.
Fixed an issue where the non-licensed users were receiving the deployment email failure notification for the unsuccessful deployment (#41705).
Fixed an issue where the users were unable to use the nCino feature after the ARM was upgraded to v21.6 (#41108).
Fixed an issue where the users were not able to create a new ALM project for Azure repository (#41554, #41630).
Fixed an issue where the users having difficulty with the datamigration.properties file while creating a new instance (#41510).
Fixed "domain name does not exist" error (#41853).
Fixed a bug where users were getting an undefined error for the standard templates while editing the CI job.
Fixed an issue where the status of the AutoRABIT ExternalId field was showing as processing, but it was marked as completed in the log report (#40669).
Fixed a bug that restricted users from using Dataloader Pro's Auditable Standard field feature (#40794).
Fixed an issue where the users were unable to replace attachment records in the destination org.
Fixed an issue where the attachments were not completely deployed in the target environment (#41208).
Fixed an issue where users were unable to deploy the nCino feature from org to org using the nCino-Forms standard template (#38764).
Fixed an issue where the users were unable to stop/delete the data loader running jobs (#39556).
Fixed an issue where the users when attempting to initiate the deployment, were failing with the "Failed to initiate deployment request" error (#40620).
Fixed an issue where the users were unable to perform the branching baseline operation (#41622).
Fixed an issue where the users were not able to configure the approver's lists on the New Merge Request screen (#41844).
Fixed an issue where the users trying to revert a commit for a commit label was getting failed (#39613).
Fixed an issue where the users were unable to update any changes in the permission section.
Fixed an issue where the non-licensed users were receiving the deployment email failure notification for the unsuccessful deployment (#41705).
Fixed an issue where the users were unable to use the nCino feature after the ARM was upgraded to v21.6 (#41108).
Fixed an issue where the users were not able to create a new ALM project for the Azure repository (#41554, #41630).
Fixed an issue where the users having difficulty with the datamigration.properties file while creating a new instance (#41510).
Fixed an issue where the users when trying to start a deployment, it was getting failed with the "Failed to start deployment request error" (#40620).
Fixed an issue where the users were unable to revert the commits using AutoRABIT (#39957).
Fixed an issue where the users were not able to use the "Files Changed" functionality on the Merge Request History page (#41456).
Fixed an issue where the users were unable to delete the changes made in the version control branch via AutoRABIT (#39130).
Fixed a bug that prevented users from performing commit and merge operations in AutoRABIT (#39129).
Fixed an issue where the external objects with lookup relationships were not getting displayed under the child objects in the Dataloader Pro (#41084).
Fixed an issue where the users were unable to update the "Validation checks" status from the in-progress state to the completed state.
Fixed an issue where changes from multiple package directories were not being retrieved without selecting a package directory.
Fixed an issue where the users were unable to attach the CSV file while carrying out the CI deployment.
Fixed an issue that caused users to receive an invalid session error when changing their password.
There was an AutoRABIT performance issue that caused searching for revisions, validations, and commits to taking a long time. It has now been fixed (#39129).
Fixed an issue where users were not able to commit their changes to the branch (#39269).
When users attempted to update changes in the target org using the profile manager, the deployment getting failed. It has now been fixed (#40599).
Fixed an issue where users were unable to switch from a credential-based login to an SSO-based login (#40871).
AutoRABIT instances were not supporting the Salesforce API 54 version. It has now been fixed. (#40921).
When a user performs a pre-validation commit on the Azure repository branches, it creates a duplicate external commit with the same revision ID. This issue has now been fixed (#39287).
Fixed a bug where the users were facing challenges while merging the entire branch changes to the target environment (#39451).
Fixed an issue where the File Diff shows full component (especially Aura, LWC components) as a change instead of delta changes (#39351).
Fixed a bug where the sub-users without admin privileges were able to export and download the org users' data from Admin > Users section.
Fixed an issue where the data loader pro throws the error "Error creating output directory: configs" while uploading data from one environment to another (#40832).
Fixed an issue where the external object-related lookups were unable to verify the relationship associated with the external objects in the destination org (#41084).
Fixed a minor user-interface bug where the users were unable to find the Resolve Conflict button to resolve the merges conflict. This is now resolved.
Fixed an issue where the admin was unable to assign permissions to its sub-users. This is now working as expected (#40017).
Fixed an issue where the data loader pro job is not able to load data for objects with fields exceeding limits(#38790).
Fixed an issue where the users were unable to register the existing branches to AutoRABIT (#40894).
Fixed an issue where the EZ-Merge was showing status as failed in the AutoRABIT application however, in the Salesforce environment the status shows as success (#40673).
Fixed a bug where the users were unable to register a dev hub on the SDFX > Hub Management page.
Fixed a bug where the access token is being printed along with the URL in the Merge Log report (#39546).
Fixed an issue where when users expanded the metadata types on the Profile Manager screen, they were able to spot duplicate child components.
Fixed an issue where the lookup field values were not picked up while creating the nCino feature migrating template (#38868).
Fixed a bug that displays the nCino-related CI Jobs on the ARM CI Jobs Results page.
Fixed a bug where the parallel CI jobs are not working as expected (#38803).
Fixed a bug where the users were unable to generate the code coverage log report from the Report module (#38673).
Fixed a bug where the search box doesn't work well with uppercase and lowercase in the commit label unlike the search in the dropdowns on the Commit History page (#39286).
Fixed an issue where the metadata types "NavigationMenu" and "IframeWhiteListUrlSettings" were included in the build view changes for both DX and non-DX CI Jobs, despite being excluded.
Fixed a bug where the user was unable to deploy the Email Template on their target environment (#40241).
Fixed an issue where users were unable to upload/migrate the knowledge articles from one sandbox to another sandbox (#37922).
Fixed an issue where the users were facing the "Null Pointer Exception" error during the merge prevalidation process.
Fixed an issue where If the users picked all the conflicted files during a merge request, they would receive an error message saying "Please click on any conflicted file."
Fixed an issue where the users were unable to find the log report for the newly created branch in AutoRABIT.
Fixed an issue where the users were unable to find out the work item statuses during the deployment process for the unlocked packages.
ALM Enhancements:
Added a new section called "ALM Management" to the Admin module for merge requests
Detailed information on all of your ALM's active and inactive sprints.
Smart commits to reading the comment in a revision associated with your ALM story.
We have introduced the ALM Details section that lists the work items linked with the commits along with the existing and post-merge status.
Ability to keep the work item status without a change or update it during EZ-Commit.
You may now configure the job to pick up revisions based on your work item status while deploying from version control to a Salesforce org, allowing you to adjust the status even after a successful rollback.
Fixed a bug where the parallel CI jobs are not working as expected (#38803).
Fixed a bug where the users were unable to generate the code coverage log report from the Report module (#38673).
Fixed a bug where the search box doesn't work well with uppercase and lowercase in the commit label unlike the search in the dropdowns on the Commit History page (#39286).
Fixed an issue where the metadata types "NavigationMenu" and "IframeWhiteListUrlSettings" were included in the build view changes for both DX and non-DX CI Jobs, despite being excluded.
Fixed a bug where the access token is being printed along with the URL in the Merge Log report (#39546).
Fixed an issue where when users expanded the metadata types on the Profile Manager screen, they were able to spot duplicate child components.
Fixed an issue where the lookup field values were not picked up while creating the nCino feature migrating template (#38868).
Fixed a bug that displays the nCino-related CI Jobs on the ARM CI Jobs Results page.
Fixed a bug where the super administrator was getting an empty popup screen when navigating to the Process Summary page.
Fixed an issue where the users were able to find the Abort option even when the CI Job had been completed successfully (#38177).
Fixed a bug where the access token is being printed along with the URL in the Merge Log report (#39546).
Fixed an issue where when users expanded the metadata types on the Profile Manager screen, they were able to spot duplicate child components.
Fixed an issue where the lookup field values were not picked up while creating the nCino feature migrating template (#38868).
Fixed a bug that displays the nCino-related CI Jobs on the ARM CI Jobs Results page.
Fixed a bug where the parallel CI jobs are not working as expected (#38803).
Fixed a bug where the users were unable to generate the code coverage log report from the Report module (#38673).
Fixed a bug where the search box doesn't work well with uppercase and lowercase in the commit label unlike the search in the dropdowns on the Commit History page (#39286).
Fixed an issue where the metadata types "NavigationMenu" and "IframeWhiteListUrlSettings" were included in the build view changes for both DX and non-DX CI Jobs, despite being excluded.
Fixed a bug where a null pointer exception was thrown while loading in Dataloader Pro (#38286).
Fixed an issue where the entitlement process is getting removed from Package.xml (#39097).
Fixed an issue where the external commits did not show up on the release label (#38822).
Fixed an issue where the code coverage percent is not available in the case of SFDX merge operation.
Fixed an issue where the data loader pro jobs were not able to load data for objects with fields exceeding 800 (#38790).
Fixed an issue where the code coverage percentage shows as 0 in the UI logs even after deployment validation is passed.
Fixed a bug where the changes are being committed even after a failed validation.
Fixed an issue where the package directory filter in the release labels is not working as expected.
Fixed an issue where users were unable to run SCA within the reports module due to an error stating "Invalid mapping credentials." In addition, the number of issues indicated in the Ez-commit process does not match the CodeScan analysis (#38917).
Fixed a bug where single data loader jobs couldn't be edited and there was a mapped field cache issue (#38753).
Fixed an issue where the alm mapping details for the scratch org with alm configuration could not be found.
While executing scratch org alm commit with skip mapping set to false, the current ALM work item status was reporting "empty" results. This is now fixed.
Fixed a bug that allowed users to save multiple criteria rows with the same priorities for ApexPMD.
Fixed an issue where the repository filter on the Commit History screen was reset to default after resolving a conflict.
Fixed a bug where the failed component count position is wrong when the window is scrolled.
Fixed an issue where the pull request support with BitBucket was not working properly. This is now fixed (#38644).
Fixed an issue where the org administrator was unable to assign hub level permissions to its sub-users (#38898).
Fixed wrong metadata identification for deletion issue (#37703).
Fixed an issue where the user was unable to update "Configuration For recordTypes picklistValues" (#38901).
Fixed API version error in the CI Job screen (#36550).
Fixed CI build failing issue (#38630).
Fixed an issue where duplicate entries were seen while creating release labels (#37300).
Fixed a bug where the user was unable to click on the OK button on the Merge Request History screen (#38781).
Fixed an issue where the "include delete records" checkbox is de-selected automatically during editing the data loader extract job.
Fixed an issue where the scratch org permissions are not visible on "hub level permissions" and "scratch org permissions" screens.
Fixed Ez-commit issue where a sub user with only one repository registered with AutoRABIT, is not able to find/select his repository in the EZ-Commit screen.
Fixed an issue where the repository filter is reset to default during the conflict resolve flow.
Fixed registering the branch issue when the branch registration crossed 100 limits in AutoRABIT.
Fixed a bug where the parent checkbox in the download zip for CI Job is not working as expected.
Fixed wave-dependent missing files from the package during the prevalidation merge operation.
Fixed an issue where the non-SFDX CI job for WaveTemplates is showing no modifications when triggered.
Fixed single data loader and data loader pro filter issues while carrying out the edit functionality.
Fixed an issue where the pull request support for BitBucket was not working properly as expected (#38644).
Fixed an issue where the user was not able to retrieve the metadata to deploy the changes using AutoRABIT's deployment feature.
Fixed data loader pro issue which was throwing unknown error while migrating the data objects (#38566).
Customize CI jobs for desired Salesforce API versions: To support different Salesforce API versions for distinct Salesforce orgs instead of a global setup, we've added a new checkbox named Salesforce API version across the CI Job module. This will offer a granular facility in a CI job to select the required Salesforce API version.
Improved Audit Trail Report: Additional data was added to the reports to support improved report analysis.
Performance Improvement: Waiting is always boring- we have reduced that wait for you.
Salesforce CLI Upgrade- Salesforce CLI upgraded to the latest stable 7.112 version.
Fixed an issue where the salesforce deployment from GIT to SFDC was not working (#38558)
Fixed a bug where the deployment CI Job occurs multiple times (#37454).
Fixed the search and substitute deletion rule issue (#38410).
Fixed SFDX parent and child job triggered the issue.
Fixed an issue where the review artifact with AutoDraft functionality was not working properly in the EZ-commit screen.
Fixed an issue where the wave template related dependent files were missing from the package [CI, Deployment, VC].
Fixed an issue where all existing credentials for version control mappings that were created using the Profile screen were reset.
Fixed a commit label issue (#38275).
Fixed an issue with SSO where users had to log in twice before being able to use the AutoRABIT application (#36634).
The issue with the SSO domain has been fixed (#37232).
Fixed data loader audit logs issue (#37688).
Fixed an issue where the users were unable to exclude EmbeddedServiceLiveAgent from CI Job (#38261).
Fixed an issue where the user couldn't delete a job with special characters in its name (#38332).
Fixed an issue where users were unable to compare profiles using the Profile Manager feature in the Deployment module (#36978).
In CI Jobs, a bug with the "Group By" filter was fixed (#38132).
Fixed an issue where the community site was not getting deployed (#38226).
Fixed a bug that caused metadata retrieval to fail with a Null error during revision range deployment.
[Profile Manager] Fixed an issue where the org compare feature would not work when three orgs were configured, resulting in a "Empty screen" error.
[Profile manager] Fixed an issue where after comparison, duplicate metadata entries and empty popups were displayed.
[nCino CI Jobs] Fixed an issue where the unwanted objects are displayed on editing the cloned CI Job.
Agentforce Metadata Type
Supported
Verified
GenAiPromptTemplate
Yes
No
GenAiPromptTemplateActv
Yes
No
GenAiPlugin
Yes
Yes
GenAiFunction
Yes
Yes
Metadata Type
Supported
Verified
LightningOutApp
Yes
Yes
InvocableActionExtension
Yes
Yes
PresenceDeclineReason
Yes
Yes
PresenceUserConfig
Yes
Yes
Version Control
Commits for Fields on Objects are Removing Lines from related Object XML
QA Passed
23.1
Code fix
Configuration
Version Control
Implemented an option to add Reviewers when Creating an External Pull Request
QA Passed
Deployments
Getting error on deployments
QA Passed
23.1
Code fix
Use case
CI Jobs
Skip member is not working
QA Passed
Version Control
EZ-merges: Successful validations were auto-rejected on 'validate deploy' step
Code fix
Use case
Version Control
Release Label: Package is not preparing
Code fix
Use case
Reports
Weekly Reports tab error
Code fix
Deployments
Org Sync issue with case components
QA Passed
23.1
Code fix
Use case
Deployments
B2C Org sync diff mail notification issue
QA Passed
Reports, CI Jobs, Deployments, Version Control
ARM overwrites any exclusions set up in CodeScan UI * Requires documentation.
Code Fix
Change Request
Deployments
Single revision deployment taking longer time to retrieve revision
Code Fix
Use Case
Version Control
Org registration issue – resolved by displaying in Logs the exact Salesforce error
Code Fix
Deployments
Org Sync question on Moderation Rule difference
QA Passed
23.1
23.1
Code Fix
Use Case
Version Control
CI Jobs
nCino CI jobs created are not visible for CI job on successful deployment
QA Passed
23.1
Code Fix
Use Case
Version Control
Regarding unable to approve commit request
QA Passed
Deployments
Profile Comparer was taking too long to deploy
23.1
Code Fix
Use Case
CI Jobs
When the agent is external, DevHub authentication was not properly validated in CI Jobs for DX unlock and install-type CI job
23.1
Code Fix
Use Case
ARM
Not fetching merges when trying to create a release label for Vlocity components.
23.1
Code Fix
Use Case
Deployments
Org Sync issue
23.1
Code Fix
Use Case
Admin
Login Error
Code Fix
Use Case
Ci Jobs
CI Jobs build date sorting is not functioning as expected for non-Admin users
Code Fix
Use Case
VS Code extension Version Control
Cannot set up VS Code Extension
Code Fix
Use Case
Ci Jobs
CI Job and code coverage not running at correct times
Code Fix
Use Case
Version Control
EZ-Commit & EZ-Merge SCA validation issue
Code Fix
Deployments
Upgrade to 23.1.16 + Ubuntu OS Upgrade
QA Passed
23.1
Code Fix
Use Case
NO
Administration
Jira On-prem SSO Cooperation
QA Passed
23.1
Code Fix
Use Case
Version Control
Random Error Message
QA Passed
Version Control
Email communication error in EZ-Commit * Requires documentation.
QA Passed
23.1
Code Fix
Change Request
Version Control
Version Control
EZ-Merge 'Reviewer Comments' section not displaying comments entered by reviewer.
QA Passed
23.1
Code Fix
Use Case
Deployments
MODULE
SUMMARY
FIX VERSION
RESOLUTION
CAUSE
Version Control
Internal - Default SCA branch not reflected while merging
23.1
Code Fix
Use Case
Version Control
EZ-Merge request with apex class metadata files failed to identify related test classes and auto-rejected with validation failure
23.1
Code Fix
Admin
Client unable to create New Branching Baseline showing loading icon
23.1
Code fix
Use Case
CI jobs
Request to increase the build label size to 150-200 characters
23.1
Deployment
Profile/Permission Set Manager Report not loading
23.1
Code Fix
Use Case
Version Control
ARM and CodeScan integration EZ- Commit validation issue. Feature Flag: USE_MASTER_ANALYSIS_PACKAGE_DIRECTORY
23.1
All Modules
SF CLI Version upgrade to 2.19.8
23.1
No Code Fix
Configuration Change request
Deployment
Experience bundle not properly generated when deploying using release label
23.1
Admin
Issue adding user mapping
22.3, 23.1
Code Fix
Use Case
Deployments
Full org:org deployment failing with no proper reason
23.1
Admin
Branching baseline issue
23.1
Code Fix
Use Case
CI Jobs
The new feature of merging only revision in the CI job build is not working
23.1
Version Control
Branch Protection Policy enforced and behavior of EZ- merge
23.1
Code Fix
Use Case
NO
Deployments
Deployment tab - Redeploy/Promote issue
22.3, 23.1
Added Loggers
Data
Dataloader
Optimize the Dataloader Pro job logs in the rabit cs log
23.1
CI Jobs
CI Job is not picking up changes committed on the branch, indicating "No modifications made."
23.1
Code Fix
Use Case
Deployments
Org Synchronization – constructive & destructive changes are not working together
23.1
Deployments
During Org Sync, file names are being repeated as part of the deployment results.
23.1
Code Fix
Use Case
Deployments
User is unable to see the Deployment History.
23.1
All Modules
SF CLI version upgrade to 2.14.6
23.1
Code Fix
Enhancement
Environment Provisioning
View environment provisioning templates
22.3 & 23.1
Version Control
Merges are not being fetched when trying to create a release label for Vlocity components.
22.3
Code Fix
Use Case
Version Control
Unable to Commit the Action Overrides in Service Appointment Object
22.3
Code Fix
Use Case
Deployment
Vlocity Deployment issue
QA Passed
22.3, 23.1
Code Fix
Use Case
Version Control
Dataloader Pro
Issue while deploying promotions from QAT to PRD the rule set criteria is compressing the value while deploying it to RD
QA Passed
22.3 23.1
Code Fix
Use Case
Dataloader Pro
MODULE
SUMMARY
FIXVERSION
RESOLUTION
CAUSE
Admin
After baselining the branch, it did not pull all metadata for development.
22.3
Code Fix
Use Case
Deployments
Deployment status failed when deploying Vlocity components
22.3 23.1
Code Fix
nCino
User is unable to do nCino Feature Deployments * Requires documentation
23.1, 22.3
Code Fix
Use Case
Admin
Getting ‘null parameters’ error when clicking on save in the user’s section.
23.1, 22.3
Admin
Issue adding user mapping
22.3, 23.1
Code Fix
Use Case
Admin
nCino View Object Failing
NA
CI Jobs
Post activities, particular job status showing as FAILED in ARM even job execution completed with succeed
22.3
Code Fix
Use Case
Admin
Getting empty Configuration under "Configure Default SCA Baseline Branches"
22.3
Deployments
In sub-user, unable to get the branch in Salesforce Org Mappings section in SF Org Management screen if Admin user given only admin module permission.
22.3
Code Fix
Use Case
Deployments
Deployment tab - Redeploy/Promote issue
22.3, 23.1
Deployments
Page unresponsive in new deployment for "previous deployment" as source type
22.3
Code Fix
Use Case
nCino
User is unable to create Feature Migration Template on Debt Schedule object.
22.3, 23.1
Code Fix
Use Case
All Modules
New User Creation
22.3
Code Fix
Change Request
Environment Provisioning
View environment provisioning templates
22.3 & 23.1
Apex Triggers
Apex Classes
Aura Definition Bundles
Lightning Component Bundles (LWC)
Visualforce Pages
Custom Object
Settings
Flows
Workflows
Profiles
Sharing Rules
Sharing Criteria Rules
Sharing Owner Rules

GenAiPlanner (API 60 to 63)
QueueRoutingConfig
23.1
23.1
Use case
23.1
Use Case
Unable to create EZ-Commit for the new user
23.1
Admin
Admin
ARM
Use Case
NO
23.1
Finding WaveDataflow components for commit
Profiles Sync Issue-CustomSettings issue
Use Case
Code fix
Code Fix
Code fix
Code Fix
Code Fix
GIT_LOGGEDIN_USER_AS_COMMIT_USER
Code Fix
Code Fix
Code Fix
Code Fix
Not fetching merges when trying to create a release label for Vlocity components
Issue on Feature Deployments
Use Case
Code Fix
No Code Fix - Added Loggers
Code Fix
Added Loggers
Code Fix
Sharing Territory Rules